By Threat Intelligence Team
Executive Summary
- Between the months of November 2022 and January 2023, we observed a significant increase in the use of Google Ads and SEO Poisoning for the dissemination of stealers, loaders and Remote Access Trojans (RAT));
- The techniques were mainly employed in the dissemination of the stealers Rhadamanthys, Vidar, Raccoon, and RedLine, as well as the malware Gootkit Loader, Batloader, Zloader, and IcedID, and others;
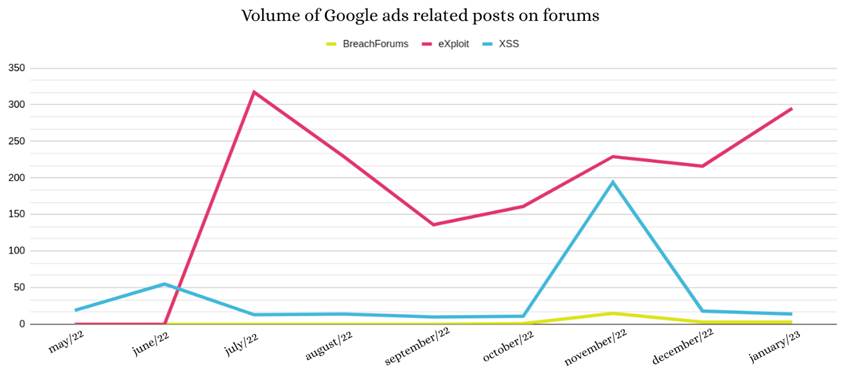
- We also identified an increase in Google Ads related posts in underground forums, especially on eXploit;
- In areport from November 17, 2022 published by Microsoft, threat actor DEV-0569 was identified using Google Ads for spreading BatLoader malware and deploying Royal ransomware;
- Webshells and web server credentials using WordPress, Joomla and cPanel are commonly traded on underground forums for use in SEO Poisoning campaigns;
- One of the ways adversaries use to circumvent Google’s security mechanisms is to register non-malicious pages whose sole function is to redirect the user to the malicious site. The redirection only occurs when the user clicks on the ad, preventing Google from associating the malicious activity with the registered page;
- Platforms such as Telegram, Steam, Discord and TikTok are used as Dead Drop Resolver (T1102.001), storing IP address information from the criminals’ infrastructure servers;
Introduction
This article discusses the use of digital marketing strategies to spread malware by promoting malicious websites using ads on search engines such as Google and Bing, and by employing SEO Poisoning techniques.
The information collected is a result of our monitoring of underground forums and multiple intelligence sources and can benefit defense teams as well as different user profiles.
During 2022 we observed the use of Search Engine Optimization (SEO) and Search Engine Advertising (SEA) strategies to spread threats through the promotion of malicious links, as an alternative to other user-focused techniques such as email phishing and smishing. This activity has been on the rise since July 2022 and showed a significant increase between the months of November and January.
Although this approach is relatively old, we have observed an increase in supply and demand for Google and Bing Ads related advertising services in underground forums, most notably the eXploit forum.
Additionally, the most recent update to the MITRE ATT&CK framework included the SEO Poisoning technique (T1609.006) to the Stage Capabilities tactic. Furthermore, in December the FBI warned about cybercriminals abusing search engine advertisements for malicious purposes.
Malware Dissemination
The main malware families spread via malicious links promoted with Google Ads and the SEO Poisoning method are the stealers Vidar, Raccoon, MarsStealer, RedLine and Rhadamanthys and the malware Gootkit Loader, Batloader, Zloader, IcedID.
In an analysis published in September 2021 by SentinelOne, the company observed a campaign in which the Zloader malware was being spread through Google Ads. According to the report, after infection with the loader, the Egregor and Ryuk ransomware was deployed on the compromised computers.
In the Microsoft report of November 17, 2022, researchers identified a threat actor, cataloged as DEV-0569, using Google Ads to spread the BatLoader malware, in which, after its execution, the Royal ransomware was implemented. On January 21, 2023, in a post on Twitter, researcher Germán Fernández identified the dissemination of a malicious artifact where the Gozi, RedLine and Royal ransomware malware are observed at different stages of the infection chain after the execution of the artifact.
The malicious campaigns consist of web pages that mimic the appearance of legitimate websites that provide the download of popular software such as Notepad++, Anydesk, TeamViewer, Zoom, Adobe, Libre Office, VLC Media Player, 7zip and Slack in an attempt to convince users to download a malicious artifact.
The main criteria for choosing the themes of the campaigns are usually popular software and systems. However, although there is no conclusive evidence, we have observed in some cases a tenuous relationship between the social engineering motto used in the campaign and the interest of the actor. Meaning, adversaries interested in abusing computing resources to mine crypto-actives may create, for example, fake pages with themes related to graphics cards or Afterburner software, used for video card control; while gangs of ransomware e Initial Access Brokers (IAB) with the intention of obtaining credentials from victims may create pages related to remote access services or software, such as Fortinet, Citrix, TeamViewer, among others.
Malicious use of marketing strategies
SEM (Search Engine Marketing) is a set of digital marketing practices used with the aim of promoting content on different search engines. Among the most common practices are:
- Search Engine Advertising (SEA): uses paid ads on search engines such as Google, Bing, and Yahoo! to promote websites. This type of advertising is usually targeted at users interested in a specific product and works in the form of Pay per click (PPC);
- Search Engine Optimization (SEO): are optimizations made on the website in order to raise its ranking in search engines, so as to increase organic traffic, i.e., direct visits to the page without the intermediation of paid resources such as Google Ads and similar;
- Social Media Optimization (SMO): aims to promote content on social media such as Facebook, YouTube and Instagram.
Although malicious campaigns can use any of the three techniques, we noticed that the use of Search Engine Advertising with Google Ads has been the most used way for malware dissemination, with the Rhadamanthys stealer in January this year.
SEO Poisoning
One of the factors used to evaluate websites indexed by search engines are related to the content and structure of the page and the domain, such as: words used, Top-level domain (TLD), registration time, domain history, among other information. In this way, criminals turn to compromised sites to host malicious content in order to, among other things, benefit from their reputation, credibility, and legitimacy. As an alternative to this practice, criminals register domains similar to those of popular websites – typosquatting technique – in order to deceive inattentive users.
Another approach used by criminals in SEO Poisoning campaigns is to buy web shells and credentials from compromised web servers using WordPress, Joomla and cPanel in underground forums. These mechanisms allow an adversary to gain access to specific settings, such as DNS zones, making it possible to create subdomains and new domains and edit the source code of other sites hosted on the compromised server.
With these privileges, the adversary can include keywords in the configuration of ads related to the theme of a malicious campaign, insert links (Link Farming) reference, configure redirects and various other modifications with the aim of raising the ranking of the website in search engines and reach as many users as possible. In some cases, tools such as SEO Autopilot can be used to optimize websites.
Among the threats observed being spread via SEO Poisoning are Gootkit Loader, BatLoader, VagusRAT, SolarMarker RAT and Atera Agent.
Google Ads
Google offers a robust ad platform, through which it is possible to determine, among other settings, the language, the geolocation in which the ad will be displayed, as well as to check via Google Planner keywords related to the registered keywords. The visibility level of an ad is directly related to the keywords registered on the platform. Therefore, native tools of Google Ads and Google Trends allow the adversary to have a view of what is being searched in the search engine and thus ensure that your ad reaches a greater number of users.
The platform allows the creation of different types of ads, however, we have observed that the vast majority of malware has been disseminated using Search Networks, i.e. ads displayed in search results on Google.
In one of the ad configuration steps it’s necessary to enter the following information:
- Displaying Path: URL presented in the ad;
- End URL: URL where the user will be redirected to after clicking on the ad;
- Ad URL Options: Alternative URLs, such as specific pages for mobile devices, for example;
- Title: title that will be displayed in the ad.
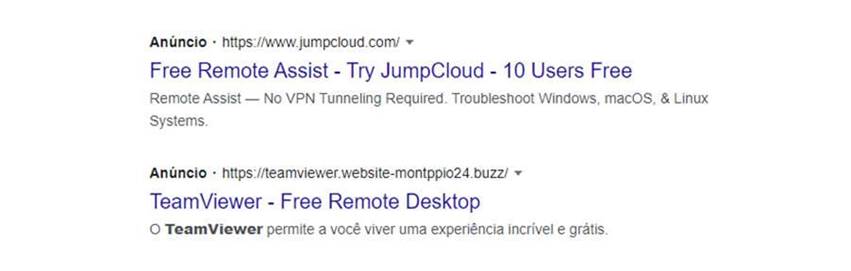
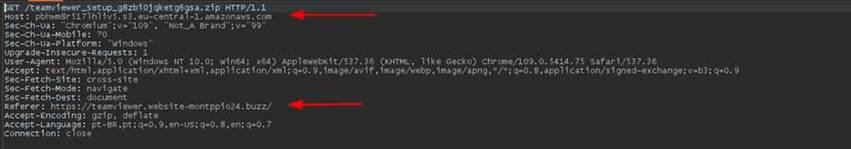
To promote malicious campaigns, cybercriminals abuse these features by registering keywords related to widely used systems and free software with large download volume compatible with the Windows operating system. In the example below, the ad title and URL use keywords related to the remote access software “Team Viewer”.
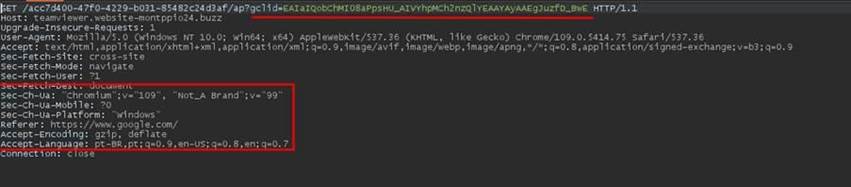
Adversaries can manipulate the behavior of ads with specific settings, mostly aimed at circumventing Google’s security policies. Some of these strategies involve redirection at the server level rather than directly via Google Ads. In other words, a page is registered in the ad only with the functionality of redirecting the user to the malicious page.
This redirection occurs only if the HTTP request contains the gclid parameter, indicating that the user clicked on the ad. However, if accessed directly, without clicking on the ad, the redirection doesn’t occur due to the absence of the “gclid” parameter in the request and therefore no malicious behavior is identified. This configuration makes detection by search engine defense mechanisms difficult.
In some cases, after clicking on the ad, the user is redirected to a page unrelated to the searched product, which redirects the user again to a page containing a URL to download some threat. Usually, the file downloaded by the user is in ZIP format and contains the malware’s executable file larger than 500 MB, so that the artifact cannot be detected by antivirus software and uploaded to automated analysis tools such as Anyrun.
After running on victims’ devices, some threats such as Vidar stealer use legitimate platforms such as Telegram, Steam, Discord, and Tiktok to retrieve information (T1102.001) from IP addresses of the servers that make up the adversaries’ infrastructure.
Based on our monitoring, we identified a user on the eXploit forum whose account was created on May 4, 2022, as being a major provider of Google Ads-related services. The account has a history of activity with several posts related to auditing, training, and search engine ad services. In addition, the user interacts with other forum members by answering questions about Google Ads.
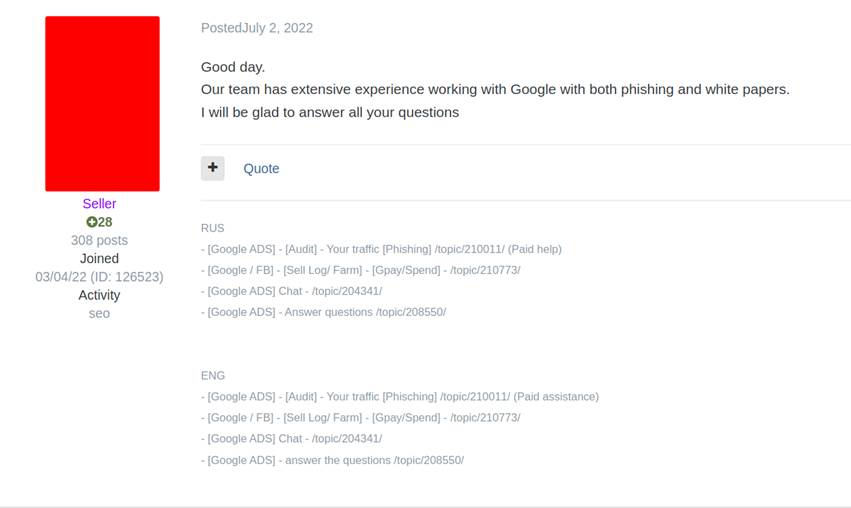
The main threats identified being spread through Google Ads are Vidar stealer, Raccoon stealer, Redline stealer, Rhadamanthys stealer, MarsStealer, IcedID, Gootkit Loader, Batloader, Zloader and Royal ransomware, among others.
Conclusion
The use of marketing strategies, especially Google Ads, allows an adversary to reach a large number of users through very customizable malicious campaigns. Because ads are presented under specific conditions (language, geolocation, browser, device type, etc.) to users with an interest in a particular product, it’s possible to achieve greater assertiveness in malicious campaigns. In addition, due to the platforms’ charging method (Pay per click) and the absence of an infrastructure for malware dissemination, it’s possible that there may be a decrease in operation costs, making the use of this technique more attractive to cybercriminals.
Additionally, we infer that the defense mechanisms currently used to mitigate malicious campaigns disseminated through search engine ads are inferior to the resources available to combat threats delivered via Phishing emails. Thus, although the use of Proxy servers is common in the corporate environment, ad blocking is usually done through browser extensions known as ad-blockers. So, in the absence of this type of resource and technologies such as DNS sinkhole (Pi-Hole), the user may have access to malicious content available in ads. The risks can be even higher when dealing with users working remotely since the home environment is outside the control of the company.
Among the many techniques used by adversaries to steal data or gain access to corporate networks is the exploitation of vulnerabilities in human assets, called Social Engineering. These strategies facilitate the intrusion process since an error or lack of attention from the user can allow the intrusion of an attacker without the need to exploit a vulnerability in systems. In addition, the use of valid accounts obtained in social engineering attacks enables post-exploitation actions such as lateral movement and privilege escalation.
Thus, we reiterate the importance of raising users’ awareness of the risks and threats inherent in the use of the Internet and computer systems as part of the defense and mitigation strategy against cyber threats.
How to protect yourself?
- Promote user training and awareness of new social engineering techniques in order to reduce the risks inherent to the use of the Internet;
- Review defense strategies and identify possible “gaps” related to the techniques of dissemination and evasion of defense mechanisms used by the malware families mentioned in this article;
- Improve proxy rules and other perimeter protection systems in order to audit and block access to suspicious sites and the download of software not used by the company;
- Monitor anomalous network traffic related to legitimate platforms such as Discord, Tik Tok, Steam, and others.
IoCs
Below are the IoCs (Indicators of Compromise) used in some campaigns identified by Tempest’s Threat Intelligence team. This data can be used to create rules in detection systems, as well as to investigate possible access to the corporate network infrastructure.
Dissemination of Raccoon Stealer using a fake AIDA64 website
HASH:
58ae566c0ae9185f68b9c933e436e8ed1c7eba42f6211fc9a396ec3d368a6ed6
15fc99e3ee6d887a59ec48fa9c5dd85e6fd7ae05
6235757f9facda9b16f498aa0f24e2a0
11488f740fdeaa4ccf9df6bdffc679917107674f1d3d287fefe8eba4207cde0e
96cbed9b2526c00015e99f4b4fc52a6bc74f2207
687df041439f81ed8688a55c017e1b2c
IP:
135[.]181[.]68[.]23
135[.]181[.]241[.]165
URL:
hxxps://aida64extreme[.]com/
hxxps://alda64[.]com
Dissemination of Vidar Stealer using a fake Cpu-Z website
HASH:
72d25540d3919e2ea7226deb8434c997f6044004a389b220748659a09a7f296e
c83182954915d4126dbd702e3cdcbcaa66999184
091693913d3cba2023dd37fbdb9e8e36
ec2b89af1752b287772865418598ae3e4852e68ed72958d4715c2561b63e9226
e1cc2ad8a6f156674b478ec1cd9c4eda65429153
712e6b917b5099bde85de13402961f7e
b57189fde7041711ada83cced49bc49a5cc098e9422da4815d7b6cbcd55dadcd
0c46a2674f5c4362830333cfbdbc11f6c7d75300
7b0fe7a7c970eb558ec45731a5f47918
URL:
hxxps://steamcommunity[.]com/profiles/76561199474840123
hxxps://t[.]me/mantarlars
hxxps://cpu-z[.]sofltware[.]com/
hxxps://steamcommunity[.]com/profiles/76561199476091435
hxxps://cpu-z[.]rsysweb[.]com/
hxxps://cpu-z[.]freewarei[.]com/
hxxps://cpu-z[.]gbitl[.]com/zodsnload[.]php
hxxps://cpu-z[.]cpuides[.]com/
IP:
65[.]109[.]7[.]48
94[.]130[.]75[.]1
65[.]109[.]168[.]175
23[.]88[.]36[.]149
Dissemination of Raccoon Stealer using a fake Notepad++ website
IP:
5[.]254[.]118[.]254
91[.]234[.]254[.]216
HASH:
9dcc2579e5e6232f116e2ae1cb572040f03ce1cbc4960e5df32152a874d7b66e
efbdcc5e9e798a277ad034c22927ecee53d7ce94
9839dafcdf536ca3949c7352ccf8bfcb
URL:
hxxps://muhammadowaismemon[.]com/
Dissemination of Aurora Stealer using a fake Nvidia drivers’ website
HASH:
fb32b33b4df698be55a3cf09aa9f082ef78e0299
de494d8b0ba94e604707fe20bee57aa7f5e19cc7
4409ceb5b33e19bb7923913429a74a6d1a1af8af
8de8fa8f9ada313ee7413f401efad8fad3b452b8b7002c27865f7c64f6a4ef68
0d341dc0fc16e1d8d134a091ae91fada5f75fcf96b3afb0b3fc806d937856bae
ed21de8db10f9d54777ababb908417b3fa4dc1d6dfd821c4aee312ef35e65687
6676e94c927ef3debc9e6c2bb4aa471c
3c3dc9048f03d1d873d607ce933807c0
1958b167c0de05e60c48f35529032ff2
URL:
hxxp://nvidio-geforce[.]site/
hxxp://constructiiunu[.]ro/downloads/setup_win64[.]exe
hxxp://constructiiunu[.]ro/downloads/install_win64[.]exe
hxxp://constructiiunu[.]ro/downloads/install_win64-32[.]exe
IP:
45[.]15[.]156[.]210
Dissemination of Rhadamanthys Stealer using a fake Notepad++ website
HASH:
80ea73d6b765fb4fc577c37f6c51d3b6deb99560b61d3f1bef1af75017fd1670
b478b49f7d108d5d2845d782264f3e30c69bb3e5
fdeab7167319131a713ec90504eb8d9b
URL:
hxxp://144[.]76[.]33[.]241/logimamonta/LEND[.]api
hxxps://github[.]com/S1lentHash/file_to_dwnld/raw/main/WinRing0x64[.]sys
hxxps://github[.]com/S1lentHash/xmrig/raw/main/xmrig[.]exe
hxxps://github[.]com/S1lentHash/lolminer/raw/main/lolMiner[.]exe
hxxps://github[.]com/S1lentHash/newwatch/raw/main/NewNewWatch[.]exe
hxxps://pastebin[.]com/raw/PTNbBX9V
hxxps://notepad-plusplus[.]donyadigital[.]com/
IP:
79[.]137[.]199[.]252
