By Threat Intelligence Team
Executive Summary
- Stealer-type malware are the primary means of obtaining data, used by data sales stores in cybercrime (underground marketplaces) and initial access sellers (Initial access brokers);
- the purchase of data on marketplaces, such as, “Genesis Store” and “2easy Shop”, can be used by cybercriminals to obtain valid credentials and thus gain initial access by performing the intrusion to the victim’s infrastructure;
- the use of “digital identities” (fingerprints) provided by some stealers or the purchase of fingerprints on underground marketplaces, are also a way to gain access to remote systems and services;
- Anti-detection tools such as Linken Sphere, Genesium and Che Browser can be used as a way to bypass anti-fraud mechanisms commonly found in internet banking and other technologies;
- the use of stealers and buying data on underground marketplaces are means used by ransomware groups to gain initial access to companies’ infrastructure;
- The sale of credentials, initial access, as well as the sale of products such as stealers and Malware-as-a-Service services are some of the various forms of monetization in cybercrime, allowing cybercriminals to have more resources to improve infrastructure used in attacks, hire pentesters, etc.
Supply chain and business models
Similar to the supply chain concept established in the commercial sphere, over the years cybercrime has evolved and proven to have organizational systems and business models that are as mature and well-structured as those seen in the corporate world, going through the stages of planning and targeting, teaming up and using suppliers, developing their capabilities (malware, phishing, etc.), distributing and advertising their campaigns and products in media such as underground forums, and even financial control and money laundering. Recently, leaked data about the Conti ransomware group revealed that the group’s operation would function similarly to a regular company, even containing paid employees.
Analogous to cloud solutions such as IaaS, SaaS and PaaS, in cybercrime we find services ranging from Access-as-a-Service, Malware-as-a-Service to the more well-known Ransomware-as-a-Service, demonstrating that product-service servitization is a trend. This complex ecosystem made up of different business models ranging from selling initial access to deploying ransomware and extortion, nurtures the supply chain necessary for malicious activity to continue in the digital world.
Although incidents arising from such activities happen mostly in the computational universe, their impacts are not restricted to the digital world, and can affect people, institutions, cities, or even countries. Thus, besides financial gain, cybercrime can and has been used as a tool for political maneuvering, as observed in state-sponsored threat actors, such as APT38 and APT28, both supported by North Korea and Russia, respectively.
Ransomware Supply Chain
Ransomware groups can operate independently or in the Ransomware-as-a-Service (RaaS) model. However, in both cases there is a supply chain, in which different parties involved in this process provide different types of resources, such as malware development, pentesting services, and initial access needed to carry out an attack. Ransomware is one of the main current threats against which security teams must plan and adapt their systems to defend against possible attacks. However, to do this, it is necessary to go beyond ransomware and understand various stages of this type of threat.
This report will cover the use of stealers and Malware-as-a-Service as data providers for marketplaces operating in the Access-as-a-Service model; the use of stealers and marketplaces as access providers for Initial access brokers; the sale of initial access as one way to gain access to corporate networks for ransomware deployment, among other points that are part of the supply chain of a ransomware attack and are essential to the continuity of malicious activity in cybercrime.
Stealer e Logs
Among various types of tools used by cybercriminals, information stealer is a form of malware used essentially to retrieve data such as credentials and card data saved in browsers, cryptocurrency wallet data, and auto-fill and web form data via web inject. This type of malware has been widely used as one of the ways to gain initial access to companies’ infrastructure, as most stealers collect credentials from services such as AWS, SSH, VPN, RDP and Citrix; in addition, this type of malware plays an important role in the cybercrime ecosystem by providing data that fuels the “stocks” of marketplaces such as Genesis Store.
While there are other methods such as exploiting vulnerabilities in exposed Internet services, using stealers can decrease the costs and time of the operation since, in possession of valid credentials, there is no need to recruit pentesters to gain initial access; moreover, access through valid credentials decreases the chances of detection in perimeter protection systems.
Below is the sale of initial access made by the user subcomandantevpn on the Russian ExploitIN forum. In the announcement, the user claims that the accesses sold were extracted from logs:
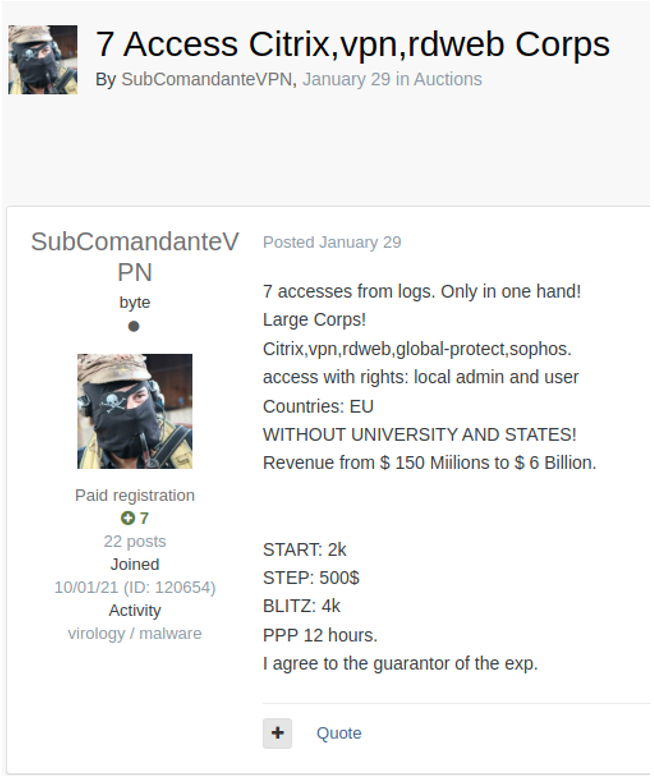
The logs mentioned by the user in his ad, however, can be obtained not only by using a stealer, but also by purchasing logs offered in forums such as XSS, ExploitIN and BreachForums. It is also common to share these logs, however, the information contained in freely available logs is often old and is usually of poor data quality. Among the most used stealers in the logs shared and sold in the underground, Redline appears as one of the main sources.
Below we can see the sale of 2.2TB of data from several countries in Redline Stealer logs offered by user BradMax on the newly created BreachForums:
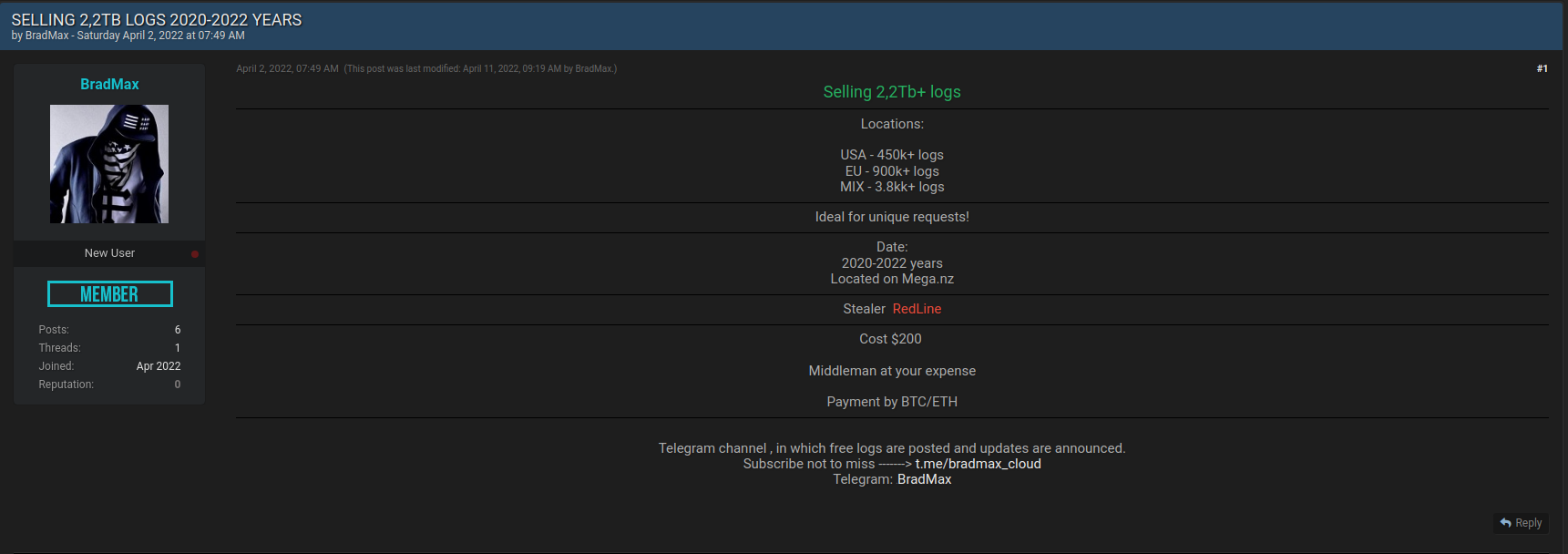
Recently, we identified between the months of March and April, about 27 log sharing posts on BreachForums, with Addka72424 (15) and Ura (4) being the most active users identified. In some cases, we detected files over 10GB containing logs from various countries and different types of data. Although in most of these cases Redline was used, we reiterate that there are several other stealers offered in cybercrime.
While we have observed the sale and sharing of logs on XSS and exploitIN, we have identified a higher volume of this type of activity on BreachForums, a forum commonly used for selling and sharing data leaks.
Given the wide variety of info stealers detected in different forums, we’ll emphasize the most commonly used ones, since they present a higher risk.
In the period of one year, between April 2021 and 2022, we identified in the XSS forum four posts related to selling stealers. The malware has different characteristics and is offered in the product (nonresident) or service (Malware-as-a-Service) model. Among the stealers identified in the forum are BlackGuard, Mars Stealer, Eternity Stealer, and most recently Rust Native Grabber. Their prices range from $100 to $700 dollars.
Besides features common to all stealers, some features such as AntiVM – AntiDebugger, Sandbox Web panel and use of encryption algorithms demonstrate the constant evolution and robustness of these malware. Below we list the main features of stealers identified in the XSS forum:
- Browser collection (Passwords, Credit Cards, Cookies, AutoFill, Tokens, History, Favorites): Email clients (Thunderbird, Outlook, FoxMail.), Messengers (Telegram, Discord, WhatsApp, Signal, Pidgin, RamBox.);
- VPN Collection Clients: WindscribeVPN, NordVPN, EarthVPN, ProtonVPN, OpenVPN, AzireVPN;
- Credentials collection: WinSCP, Credman passwords, Vault passwords, network passwords);
- List of 2FA plugins: Authenticator, Authy, EOS Authenticator, GAuth Authenticator, Trezor Password Manager.
- Machine fingerprint collection based on:
- IP and country
- Working path to the Mars EXE file during operation
- Local time on the PC and time zone
- System language
- Language keyboard layouts
- Laptop/Desktop
- Processor model
- Installed RAM size
- Operating system version system and its bit depth
- Video card model
- Computer
- Support for browsers such as Chrome, Firefox, Edge, Opera, Chromium, Vivaldi, IE.
The malware is developed in different languages, the most common being C++. However, the Rust Native Grabber stealer, as the name suggests, was developed in Rust, a language also used by the ALPHV/Blackcat ransomware group. According to forum discussions, languages such as Go and Rust make the malware development process faster, more reliable, and more difficult to reverse engineer.
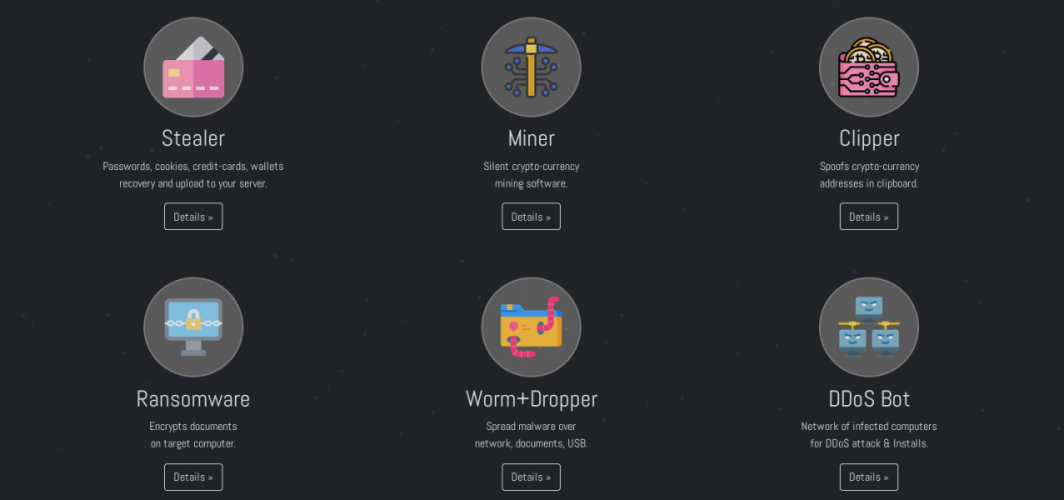
The malwares are commonly advertised on different platforms and forums such as RuTor, Telegram or even sites on the Tor network. Below is the Eternity Stealer site on the Tor network; among other services, ransomware and DDoS bot are offered:
During the investigation, we identified that the XSS user MarsTeam, used by members of Mars Stealer, was banned from the forum under allegation of scam (scammer/fraudster). The user had been active since May 2021 and had his account banned by the forum administrator on April 16.
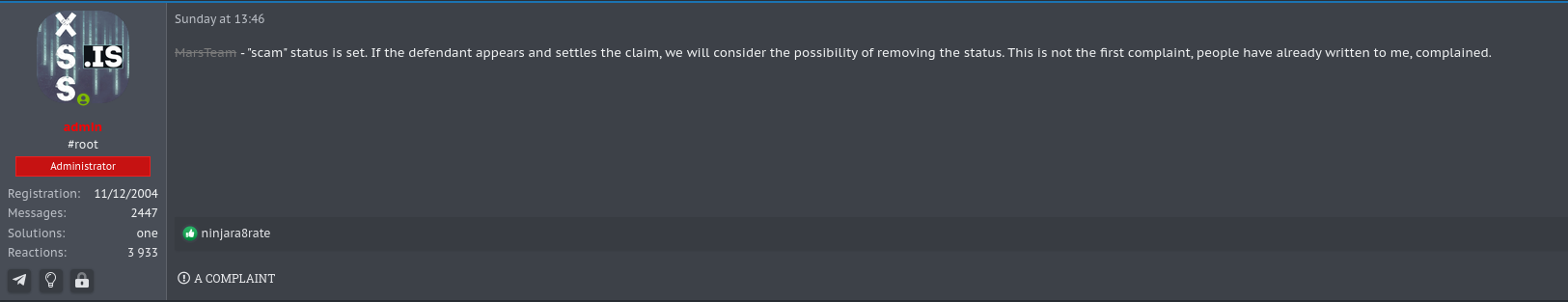
Also regarding the operation of stealers, we identified on April 16th a comment on the ExploitIN forum about the suspension of Raccoon Stealer’s activities due to the war in Ukraine and the death of one of its members. Raccoon Stealer started its activities around April 2019. Although user MarsTeam was banned in the XSS forum and threads related to the sale of Raccoon Stealer were closed by moderators of the ExploitIN forum, such events do not mean the end of the operation of these groups.
While analyzing some marketplaces such as Genesis, 2easy and Russian Market, we observed mentions of Vidar as being one of the main data sources on these platforms, right after Redline. Developed in C++, its activity started in November 2018, with its first announcement on the ExploitIN forum. The stealer operates on the Malware-as-a-Service model and has proven to be a reliable malware, as it has a good reputation and no negative reviews, and is mature among forum members. Within its functions are:
- Collect data from commonly used browsers (Passwords, cookies, history, Crypto wallet collection (All according to the wallet.dat template, as well as unique wallets according to the rules);
- CC – Card data, except *** (*** does not save the browser itself);
- File collection according to user established configuration;
- Telegram authorization (Windows version);
- FTP, WINSCP, MAIL collection (Correctly collects data, with correctly specified ports);
Vidar is represented by user Loadbaks on ExploitIN and has a good reputation on the forum (7). Besides the functions mentioned above, the stealer supports multiple accounts giving the operator the possibility to create different access profiles to the platform and daily updates in case of antivirus detection.
Marketplaces
Since the latest attacks by the extortion group LAPSUS$ against large companies such as Okta and Microsoft, suspicions have been growing that the group is buying access to platforms such as the Genesis Store and Russian Market. This argument, in a way, would justify the accesses made by the group with valid accounts to the infrastructure of its victims. Although in some incidents the group claimed to have gained access through credentials available on platforms such as Github from some victims, buying access on marketplaces is a common practice by cybercriminals. We have noticed that after the publication of Microsoft’s report on the group’s TTPs, the demand for invitations and accounts on the Genesis Store and 2easy marketplaces has grown significantly on forums such as XSS and ExploitIN.
Just like in the corporate world, cybercrime has been looking for ways to innovate, aiming for higher profits and new ways to establish different business models. Among some of these changes, marketplaces represent an almost inexhaustible source of data, offering attackers the opportunity to gain access to systems by purchasing data such as cookies, system credentials, and remote access services. Such stores, operating on the Access-as-a-Service model, give adversaries greater exposure of the data sold, greater agility in their sales (since the whole process is automated), and greater reliability, since transactions are intermediated by the platform acting as a broker for cybercrime. Consequently, such ease in buying and selling data implies greater risks.
Marketplaces, however, aren’t new. Created in 2014, the Ukrainian marketplace xDedic, which specializes in RDP access sales, made available approximately 176.000 compromised servers on its platform between October 2014 and February 2016. Later, on January 24, 2019, the store shut down its activities after an operation by the FBI and European authorities.
Due to the wide variety of marketplaces, this report will present an overview of the most commonly used stores.
MagBo
In 2018 MagBo emerges, a store with a greater variety, volume and quality of data (exclusively first-party, functional and non-reused data). According to Israeli cyber security firm Ke-La, in addition to FTP credentials, SSH and CMS panels, MagBo relies on MagBo Backdoor (MBD), a tool installed on compromised machines with the goal of giving the attacker the ability to use a web shell with integration to the store. Although the user mrbo (used for store ads on ExploitIN), was banned in May 2019 after several forum reviews, the platform is still online.
Images regarding MagBo marketplace:
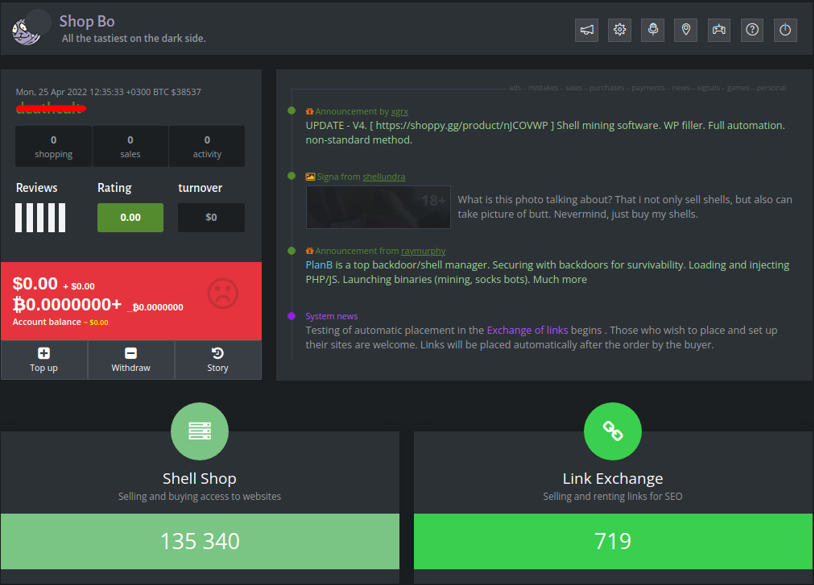
Among the sections of MagBo shown in the images, we highlight:
- Shell Shop: accessible only upon a payment of $50 dollars;
- Link Exchange: contains SEO (Search Engine Optimization) links;
- Scan Store: contains documents such as passports, military and civil identity among others (during analysis, we identified the sale of selfies and documents of Brazilians for $5 dollars by the user kyoto – @kyoto12);
- Flea Market: free section containing remote access, logs, emails, exploits, database, documents etc;
Odin Shop
With an interface similar to xLeet, Odin Shop appeared in April 2020 on the XSS forum, with its first announcement made by user OdinShop. Another account using the same nickname (odinshop) was registered on the ExploitIN forum in September of the same year, however, there is no record in its activity history. Despite this, at the time of analysis we identified that the user had logged into ExploitIN 8 hours earlier, demonstrating that the account is still in use. One hypothesis is that the user odinshop communicates directly with vendors via private messages on the ExploitIN forum.
Among the services and products offered in the marketplace are:
- Hosts: RDP, Shell, cPanel e SSH/WHM;
- Send: Mailers e SMTP;
- Leads: E-mail Only, Combo email:password, Combo username:password, E-mail access, Phone Number Only, Combo phone:password, Full data, social media data;
- Business: cPanel webmail, GoDaddy webmail, Office 365 webmail;
- Accounts: Marketing, Hosting/Domain, Games, VPN/ Socks Proxy (e-mail access), Shopping, Programs, Stream, Dating, Learning, Torrent/File host, VoIP/SIP, Other
- Social: Likes, followers, Views, Comments, Accounts, Coupons, Methods;
Below are URLs regarding Odin Shop and statistics of hits sold on Odin Shop and xLeet, respectively, extracted from the platform itself on April 24, 2022:
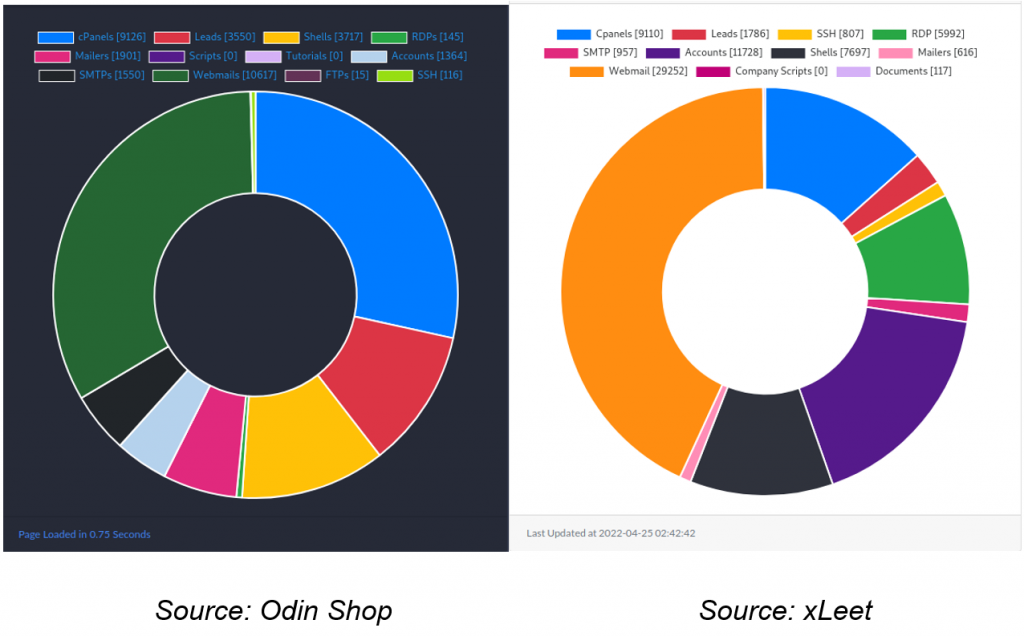
xLeet and Odin Shop are marketplaces that use the same technology on their websites and therefore sell very similar data.
Russian Market
We haven’t identified any announcements or recommendations related to Russian Market in any of the main underground forums: XSS, ExploitIN and RAMP. However, according to the registration date of the store’s main domain, we believe that the marketplace exists since 2019. Despite little information about Russian Market, the marketplace is mentioned in a tweet by cybersecurity researcher Brian Krebs as one of the sources used by LAPSUS$ to purchase access. In a post on the XSS forum, Russian Market is pointed to as a possible alternative to the Genesis Store. Despite this, we have identified some criticism of the store under claims that the logs provided are not first hand.
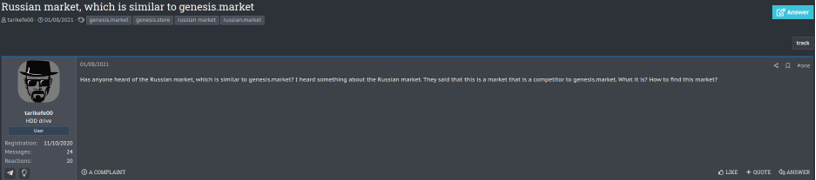
Access to the marketplace happens with a simple registration. However, a $50 payment is required to activate and keep the account active.
Below are screenshots of the most relevant sections observed in the store:
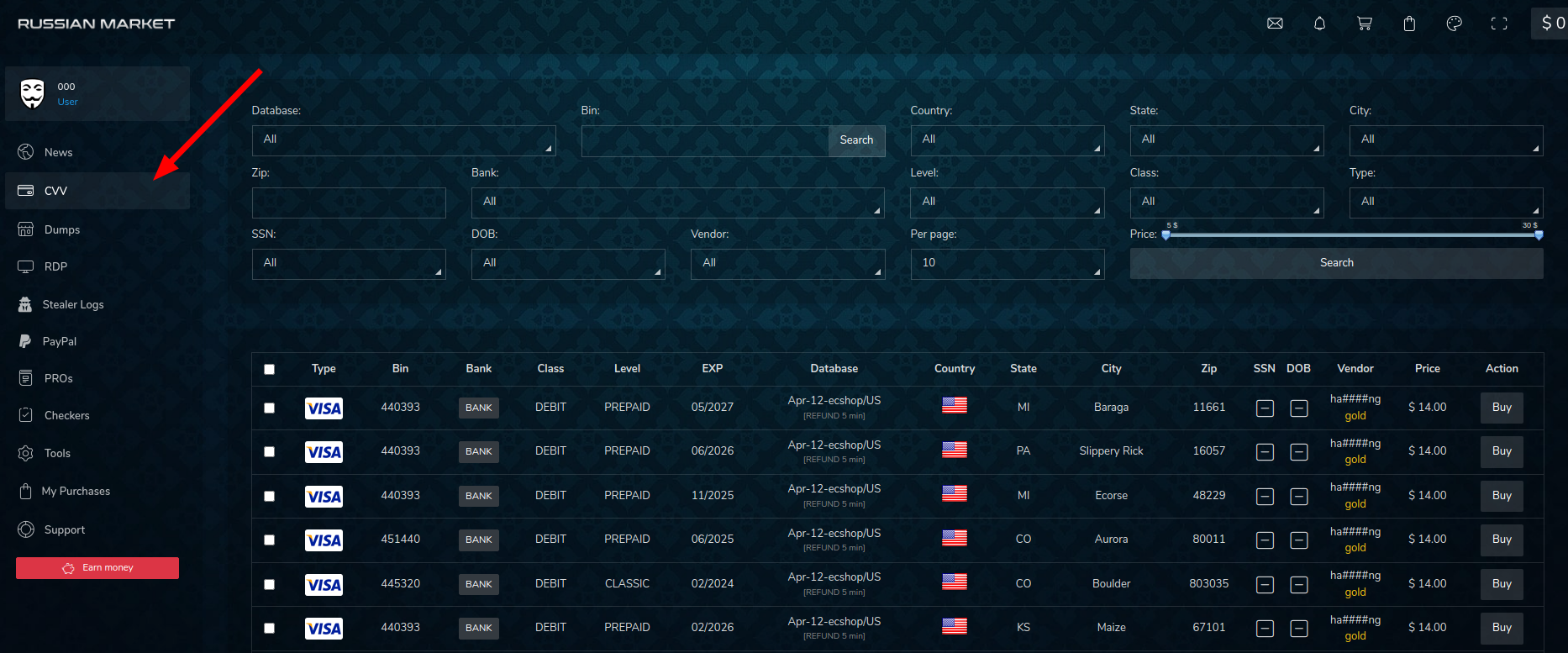
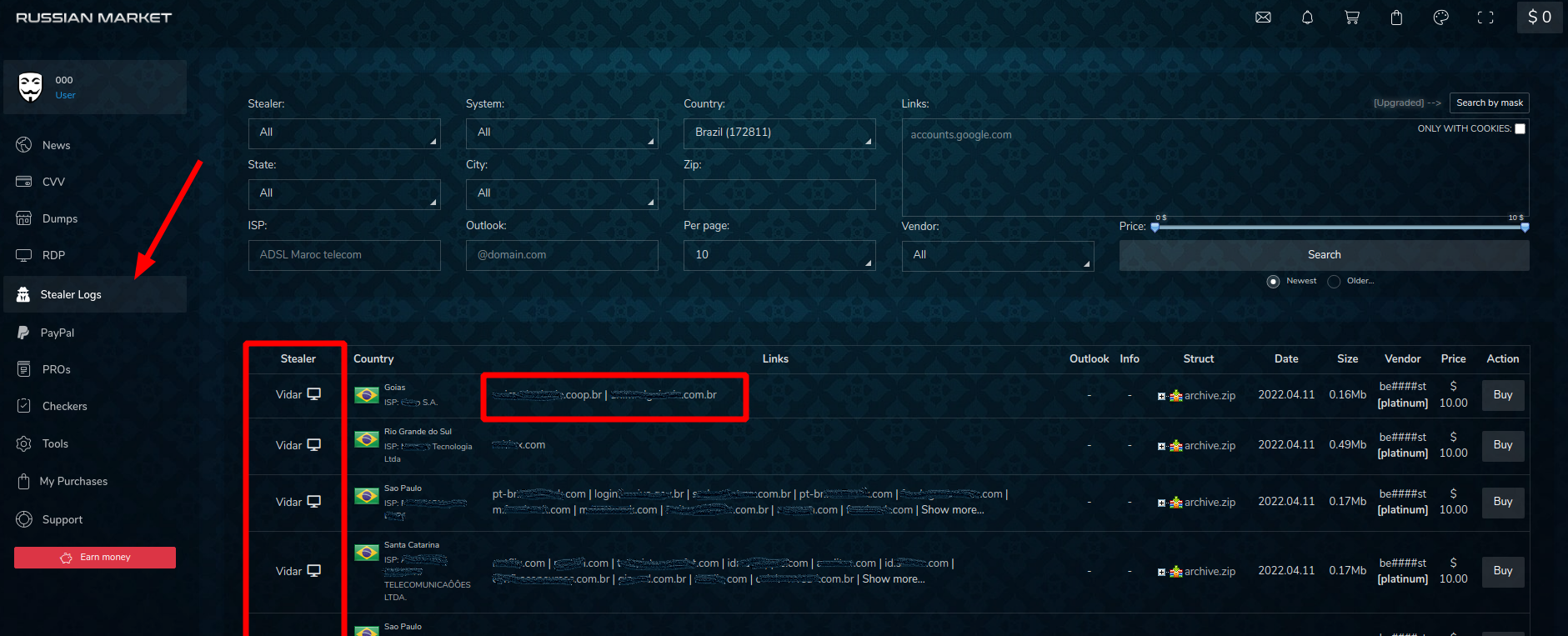
Among the analyzed marketplaces, Russian Market is the only one that displays the stealer used in the sold logs. In its list Redline is the main source of the data, followed by Vidar Stealer, Raccoon Stealer, Taurus and Azorult.
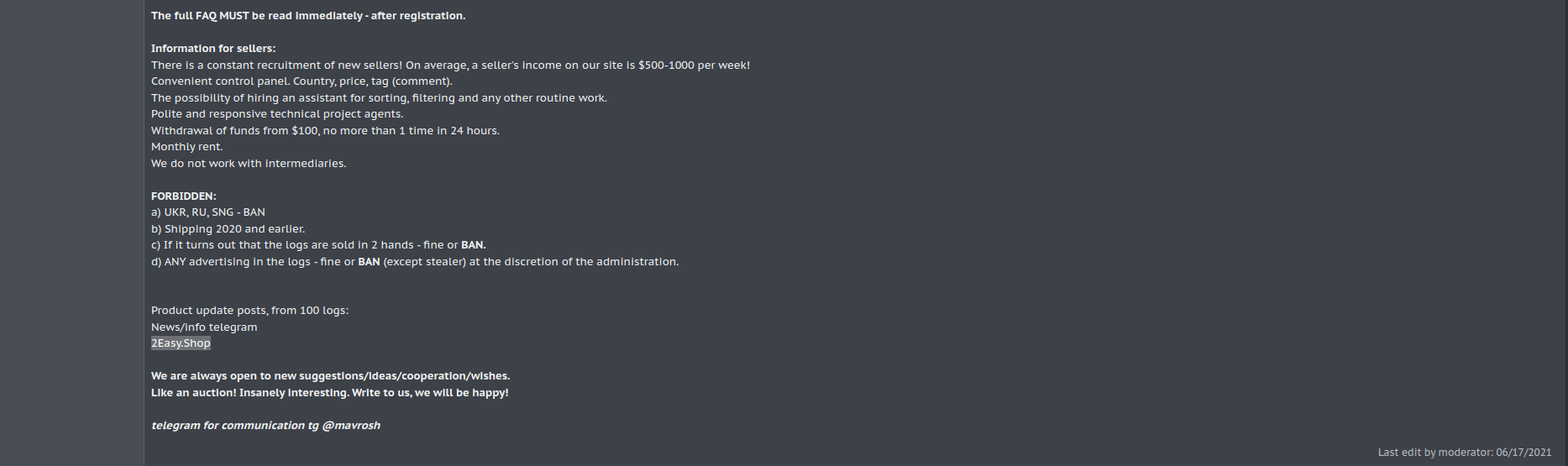
2easy Shop
2easy is currently seen as the main alternative to the Genesis Store. According to data from December 2021, the marketplace would have exposed around 600,000 infected devices on its platform. The store operates on a bot scheme, which is basically a set of data collected from a compromised machine, offering a wide variety of data at low prices, with some bots costing as little as $5.
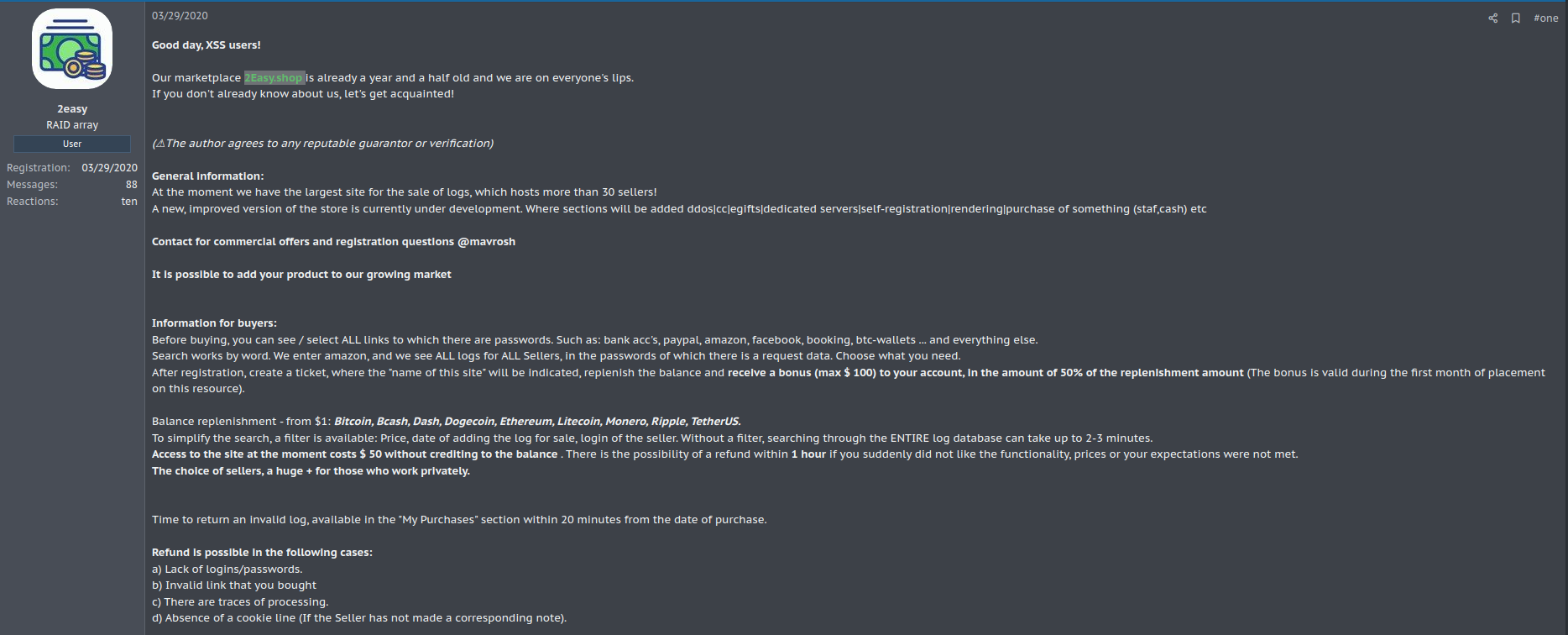
Based on user 2easy’s registration and announcement on the XSS forum, the marketplace was supposed to begin operation in March 2020; later, in June 2021, user 2easyshop announced the store on the ExploitIN forum. However, user 2easy reports in his XSS announcement that the store had been active for at least a year; we identified that the domain 2easy[.]shop was registered in December 2019, the year in which the user reports starting its operation.
Below, we display images of the ad in the XSS forum:
In a report by cyber security firm Ke-La from 2021, it’s mentioned that the incident involving Eletronic Arts allegedly occurred through the purchase of initial access to the company’s Slack platform. It’s worth remembering that the user 4c3 from the ExploitIN forum, announced in a post to be the author of the attack on EA. This same user was identified by Tempest’s Cyber Threat Intelligence team as the threat actor “oklaqq”, one of the members of the LAPSUS group.
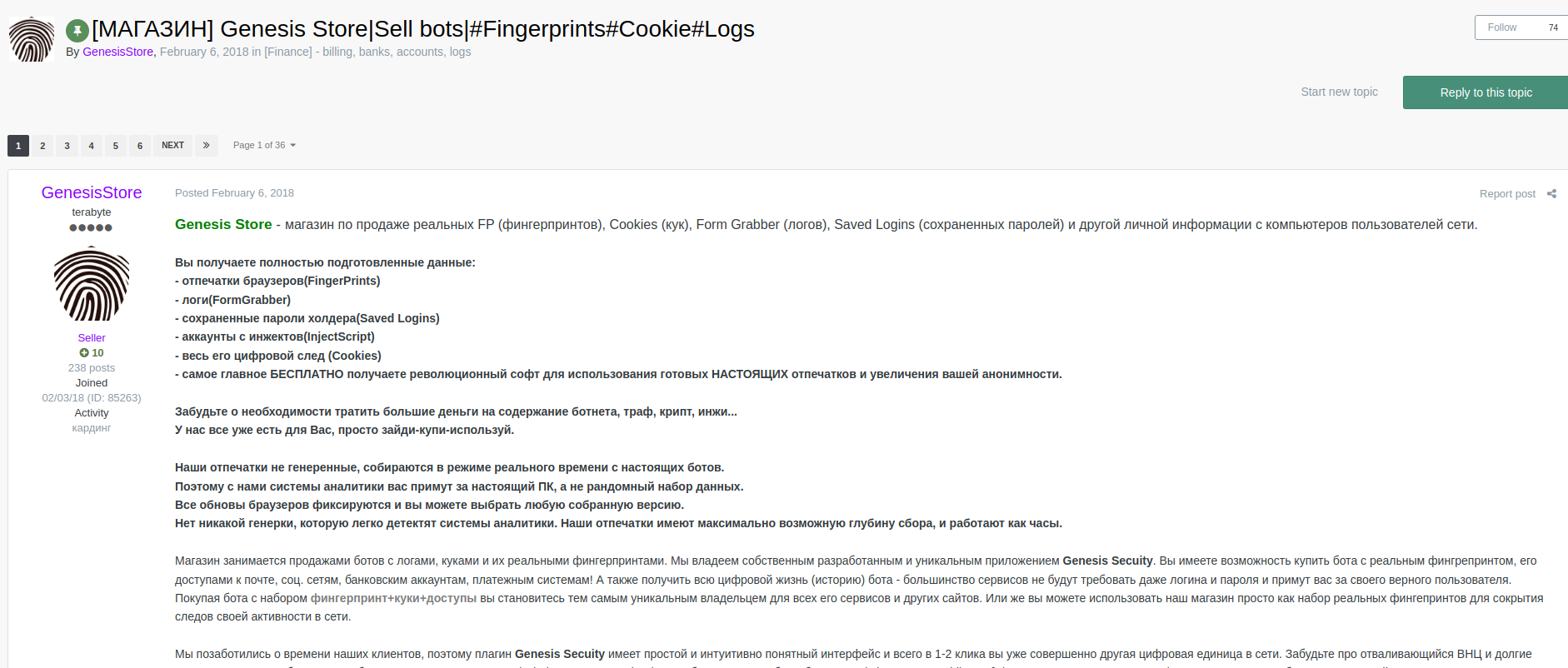
Genesis Store
Similar to other platforms, Genesis Store offers a large variety and volume of information. However, some features of this store make it the most used and prominent marketplace today. In February 2018, Genesis Store was announced on ExploitIN by user genesisstore. With only one post in its activity history, the account holds a good reputation (10) on the Russian forum. With no accounts or ads on XSS, the marketplace was first mentioned on the forum in April 2019. The domain genesis[.]market, on the other hand, was registered in November 2017.
Among the available features are:
- Browser fingerprints (FingerPrints);
- Logs (FormGrabber);
- Saved holder passwords (Saved Logins);
- Accounts from injections (InjectScript);
- Entire digital footprint (Cookies)
Post ad
Initial Access Broker (IAB)
In a double extortion attack the encryption and exfiltration of data is one of several steps in a ransomware incident. However, to mitigate this type of threat, it’s necessary to go beyond ransomware and consider as a defense strategy each of the points presented, in this report, that make up the supply chain of this type of attack. As shown, stealers and marketplaces are means of providing ransomware groups and IABs with data that enables intrusion through access with valid credentials and ensures the execution of the next stages of the attack.
In this ecosystem, the Initial access broker (IAB) plays an important role in providing initial access for a subsequent ransomware deployment. Thus, buying credentials on platforms like Genesis and using stealers exposes the IAB to a universe with greater possibilities for access, lower cost, and less risk. On the other hand, the risks increase for those seeking to defend themselves from these threats. For groups operating in the Ransomware-as-a-Service (RaaS) model, the IAB can play the role of an affiliate, providing access to companies’ infrastructure in exchange for ransomware use and profit sharing.
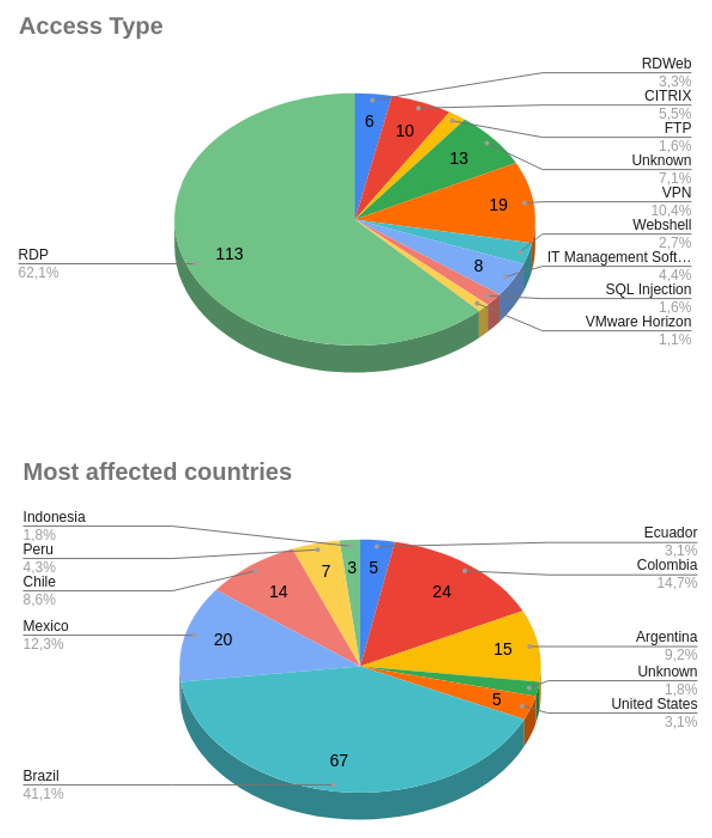
Between the months of January and June, we detected around 180 initial access sales in Latin America, with Brazil, Mexico, and Colombia being the most affected countries.
Below are the top-selling access types and most affected countries between January and June 2022:
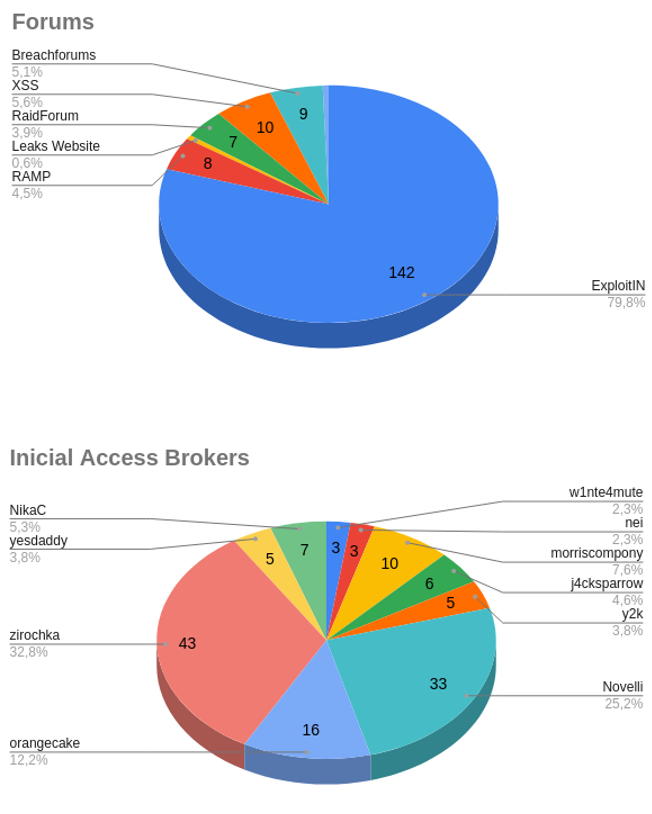
Below are the most used forums and IABs with the highest activity, between January and April 2022.
We believe that the intelligence coming from our monitoring of underground forums can help in decision making, specifically in identifying initial access sales. Because, even if the environment has been compromised, it’s possible to identify improper accesses before they become major incidents. However, the public exposure of data in forums and marketplaces significantly increases the risks, since such information is openly accessible and can be bought by any type of adversary.
Analyst Commentary
Having visibility into the activities presented in this report is crucial for a better understanding of cybercrime, especially a threat scenario related to ransomware attacks. Thus, monitoring marketplaces such as Genesis Store and 2easy Shop allows defense teams to use IP and domain data available on the platforms and register them in perimeter protection systems, since the bots sold on these stores are compromised machines that can be controlled by any type of threat actor, thus representing a potential threat to companies that may have a direct or indirect relationship with the victim. Monitoring these stores also allows the detection of data sales from compromised machines before this data becomes raw material for IABs, resulting in a major incident, such as a double extortion attack or data leak.
However, we emphasize that the success of data collection by stealers and the exposure of data in the marketplace for buying and selling access is the effect caused by the failure to mitigate attacks prior to these events, such as opening phishing email attachments, accessing malicious websites, and social engineering attacks. The implementation of MFA, password policies, and several other measures to increase the security of the computing environment is undoubtedly essential, however, it’s important that in addition to the measures taken to protect such assets, the awareness of risks and threats by those who use the computational resources in a corporate environment, is crucial to mitigate attacks that exploit vulnerabilities in the human asset.
It’s worth noting that using the techniques presented in this report is not the only way to gain initial access, and exploiting vulnerabilities in systems publicly exposed to the internet is also a common practice especially among ransomware groups. Thus, we draw attention to a broader view of cybersecurity incidents, where each party involved in this and other supply chains are interdependent and therefore do not exist in isolation.
Finally, we emphasize that the presence of marketplaces such as Genesis Store represents a major risk due to the ease of obtaining and using valid credential data to gain access to companies’ infrastructure, as already demonstrated by the extortion group LAPSUS$.
