A research conducted by Tempest’s Threat Intelligence team to investigate possible fraud involving the manipulation of emailed files has led to the identification of a tool used by criminals to automate the collection of traffic information in electronic mail.
This investigation involved communication between two companies that periodically carried out financial transactions by using billing slips sent by email. In one of these exchanges, one of the companies noted that the bank logo printed on the slip did not correspond to the financial institution normally used to charge the creditor company; however, after contacting employees from both companies, it was discovered that the billing that had originally been sent contained the correct logo, which led to the hypothesis that someone used a message tampering tool.
It is well known that, in order to optimize their work and increase their illicit earnings, criminals use automated tools such as login testers, which are programs designed to perform dictionary attacks on authentication pages of a variety of web systems. Another example are information exfiltration tools, which collect information of interest to the attacker. Its function is to extract predefined information from a web system in a similar way to another type of software widely used by criminals in e-commerce stores, especially at the beginning of this decade, to extract payment cards information.
Recently, a new concept has emerged in the fraud environment focused on webmail inboxes from various providers. This tool, benefits from leaked access credentials to automatically search for keywords within victims’ mailbox.
A tool for testing, collecting, and modifying email attachments
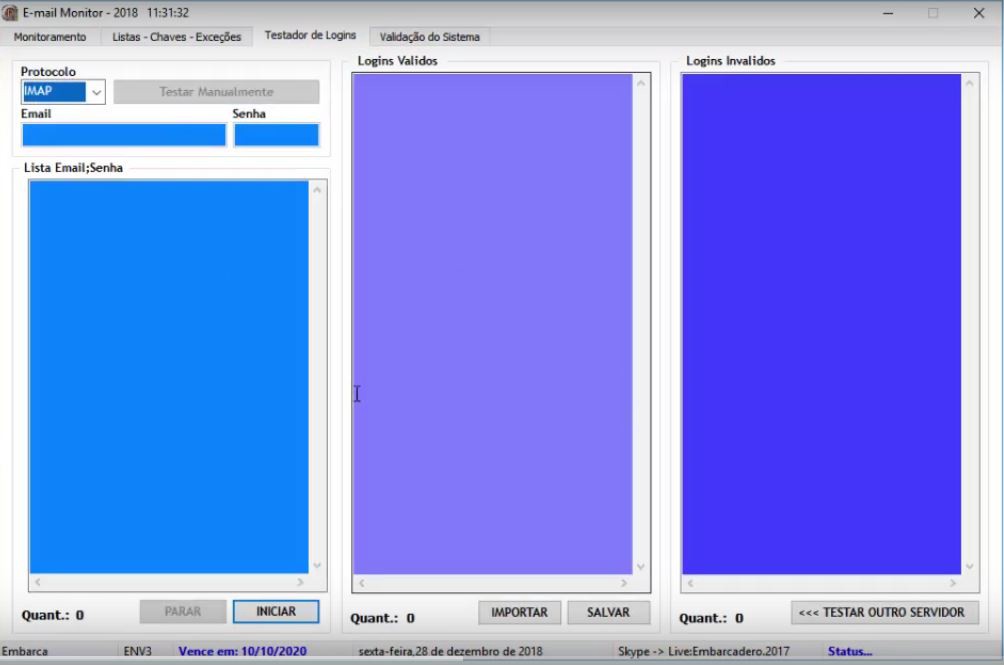
The research has led to the discovery of a tool that allows, from a list of emails and passwords (obtained through leaks, for example), to test valid credentials and, once the access to these accounts is obtained, it performs the extraction of email messages, offering the option to filter keywords of interest and allows for the modification of email attachments.
The tool abuses a feature of the IMAP protocol which allows to synchronously retrieve emails between client and server — that is, any modification (such as changing the message status from read to unread, deleting or retrieving a message) made in an email client using such protocol reflects on the server and vice versa. IMAP, as we have already pointed out, is supported by most email providers and, because of its flexibility, is widely used in cases where the same email account needs to be accessed by email clients installed on different computers (ex: a finance department where two or more employees need to access the same email account).
The operation of the tool offered by the fraudster is simple. Initially, the operator loads the list of emails and passwords for credential validation (image 1).
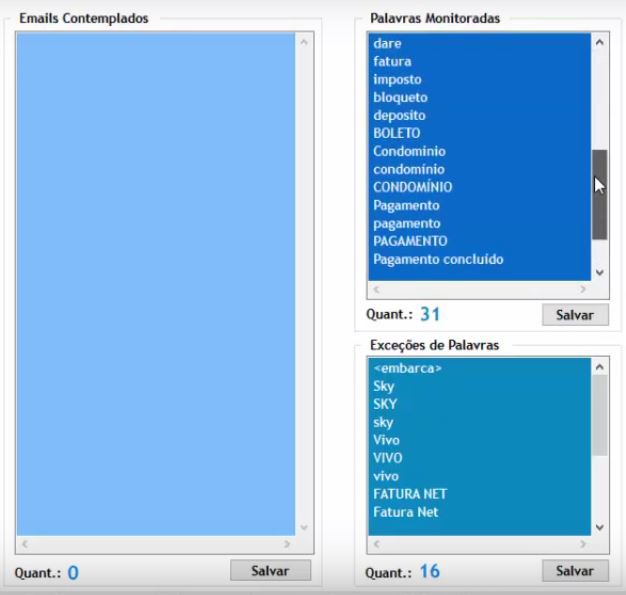
After the credential validation, the operator can create a selection of email accounts to be tracked down based on keywords. It is also possible to exclude emails based on word exceptions. The result of this selection is displayed in the “Emails Contemplados” (contemplated emails) column (image 2).
The operator then monitors the contemplated email accounts searching for messages that contain information of interest. Image 3 shows the screen dedicated to this function. On this screen, it is possible to set the number of messages to be monitored (the 10 most recent messages, for example), use keyword filters in the subject line or message body, delete messages selected by the tool from the email server (to avoid that the victim pre-reads these messages), and ignore emails that have already been read in order to avoid arousing the victim’s attention.
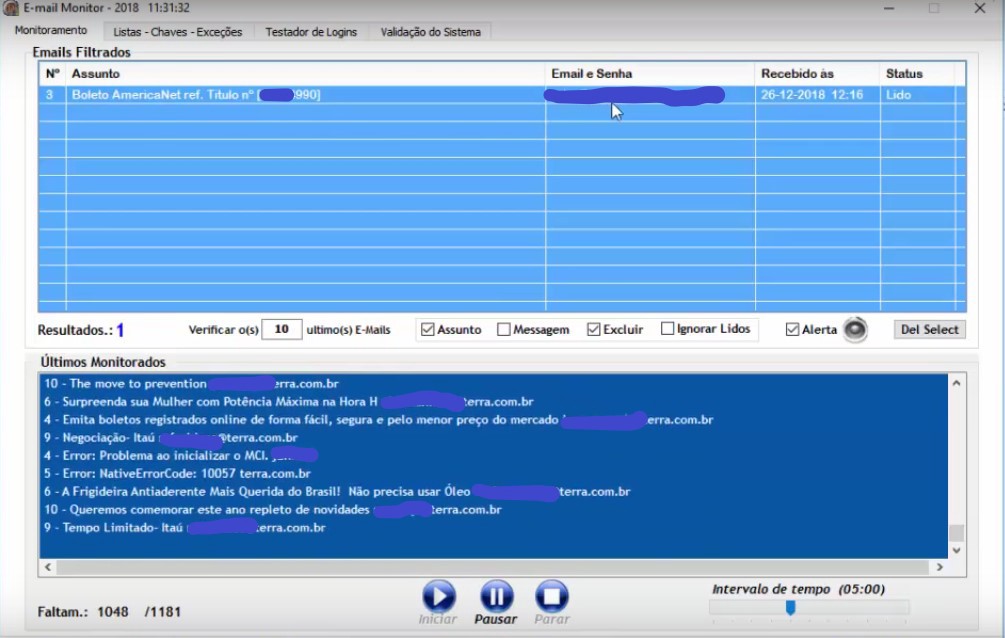
Emails filtered by the tool are saved in the operator’s computer in txt and mbox formats (extension used by the email client Mozilla Thunderbird) so that the operator can download attachments, modify them as they wish (using simple tools for editing PDFs in the case of the billings), and then restore the email to the victim’s inbox.
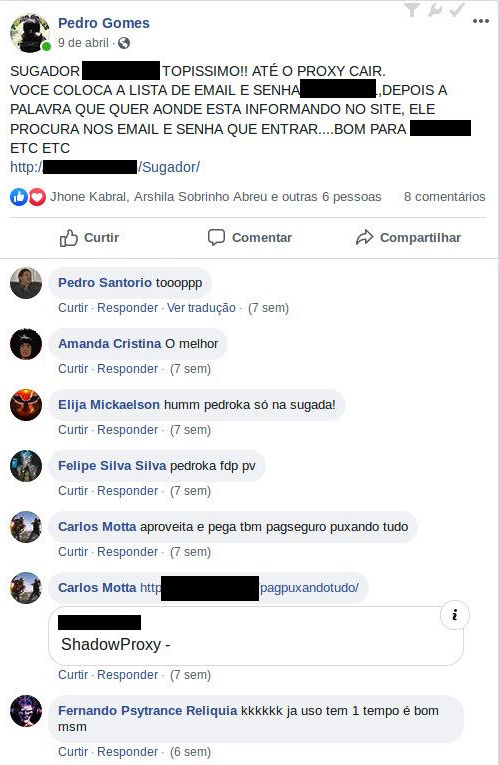
Tool is offered on social networks
On social networks it was possible to identify at least one ad advertising a similar tool, containing a trial URL for, as shown below.
The successful use of systems such as the this tool by an attacker depends on some factors. First, credential leaks enable access to a variety of mailboxes, both from businesses and from citizens.
These credentials can be tested in a large scale by login-testing programs and can be incorporated into tools such as the email sucker to automate access to mailboxes, searching for keywords of interest and manipulating the content of emails that contain financial information and documents, such as bank billings.
Because it involves several steps, the cost of this attack is apparently higher than a traditional phishing. However, when handling company-paid billings, the chances of success are greater, which may be the great incentive of this scheme.
The last line of defense against these threats is the email recipient, the person who operates the mailbox, who may or may not suspect the changes.
References:
INTERNET MESSAGE ACCESS PROTOCOL — VERSION 4rev1. March 2013
Save attachment changes with original message. MSOutlook.info. 30 May 2018
