The perimeter concept and architecture used by many companies, with on-premises services, giant data center structures, protected by different security tools and hosts allocated on company premises, have given way to cloud services. According to a player available on the market, today, companies use approximately more than 800 SaaS – software-as-a-service – applications. Cloud computing (cloud archiving) has brought with it many benefits such as speed and efficiency, the ability to allocate more computing resources on an as-needed or timed basis, and to decommission when necessary, thus eliminating fixed costs with large computing structures. Therefore, it’s possible to obtain significant cost savings compared to the acquisition and maintenance of physical environments. Cloud computing presents several benefits, be they economic, technical, architectural, and ecological. Adding a potential improvement in security and resiliency.
In the market, it’s estimated that 97% of these cloud applications are considered Shadow-IT, i.e., they are not being managed, making the visibility of these applications difficult for security teams (If you want to understand a little more about the concept of Shadow IT, read the article “The dangers of Shadow IT” available at https://sidechannel.blog/en/the-dangers-of-shadow-it-and-casbs-role-in-protecting-the-environment/). In this sense, cloud computing also brought the challenge of how to ensure the security of information, people, and all the applications available in the cloud. Security had to become intelligent, adapting to situations that were not routine, such as remote work, leading employees to work in different environments outside the company or even the use of private equipment, such as BYOD (bring your own device), which increases the surface subject to incidents. In this sense, CASB tools are essential, helping in the visibility and organization of cloud applications, significantly reducing the Shadow-IT problem, and improving the security of the environment.
To ensure security in the SaaS environment it’s suggested that the following key ideas should be considered: SASE, SSE, Context, Zero Trust.
The first idea is related to the concept of SASE – Secure Access Service Edge, this is an emerging cybersecurity concept, presented in 2019 for the first time by Gartner. Looking back, it can be seen that the network approaches and technologies used so far do not effectively provide the security that corporations need today. Companies need their employees to have immediate and uninterrupted access to information. With many staff working remotely, data has been migrating from data centers to cloud services. In addition, more traffic going to the cloud than coming back to data centers has demanded a new approach to network security. SASE resources are based on entity identification and can be associated with people, groups of people, devices, and IoT systems. Furthermore, they are based on real-time context services, a secure environment in compliance with policies, and continuous risk assessment.
SSE – Security Service Edge, in turn, is a term used by Gartner to describe part of a new concept, i.e. a subset of SASE. It promotes secure access to the web, software as a service, and private applications, keeping attackers away from sensitive data and information. SSE is demonstrating great value by integrating several services, which work well together, into a single platform, e.g. Secure Web Gateway, CASB or Zero Trust. Security Service Edge transcends traditional firewalls, allowing details of what, how and why certain data was accessed. This makes it much easier to make security decisions, and better, in real time. In summary, an SSE solution brings several benefits such as security and trust regardless of where people are working, unifying functionality and strategy, evolution in user experience, flexibility, and cost reduction.
Context will determine how SSE capabilities will be controlled to keep data, applications, and people safe. This requires a deep understanding of who the person is, what they are accessing or trying to do, and when and how they are doing certain actions. Thus providing the opportunity for real-time risk mitigation.
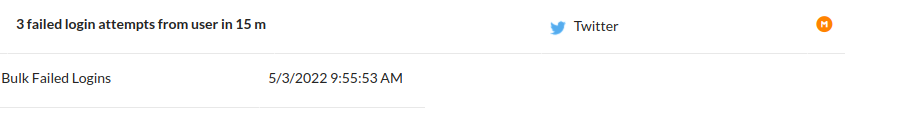
In Image 1, we can observe that there was a repeated login attempt action. Three access attempts were made, within fifteen minutes, in the account of a certain user, whose credentials were hidden for ethical and security reasons. In this situation, an alert was generated because several unsuccessful login attempts were identified. In this case, the tool provides additional information to help analyze the event, such as: source and destination, user and application information, event severity, among other information.
Zero Trust is a security paradigm that combines strict identity verification and explicit permission for every person or entity attempting to access or use network resources, regardless of whether the person or entity is “inside” an enterprise’s network perimeter or accessing the network remotely. So the goal is not just to control the access and identification of each person, but rather the activities that a person does according to the level of trust derived from a real-time assessment. Thus, obtaining insights into what happens at the login, such as environmental signals, the history of behavior, as well as the characteristics of the data itself.
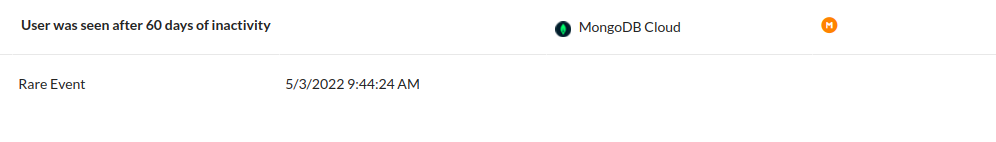
The tool performs a behavioral analysis of the user, checking the habitualness in which he logs in, which applications he has accessed, his downloads and uploads, as well as actions that it understands as suspicious and that are outside the user’s behavior. In Image 2, a certain user, whose credentials were hidden for ethical and security reasons, generated an alert in the tool, because he presented a behavior considered rare. He had not logged in for over 60 days and when accessing his account, he downloaded an application considered to be different from those normally used by this user. In addition, it’s possible to obtain more information such as date and time of the event, application details, user details such as IP, device, operating system, browser, among others.
With the help of a CASB tool, as presented above, it’s possible to make more assertive decisions based on all the available data, in real time. With this apparatus of information, it’s possible to find out if in fact the user made a mistake or forgot his password, or even if there was an attempt to compromise his credentials, as well as if the application used by a user is reliable, or if his actions are being those expected to his function, for example.
Best practices for implementing cloud security.
Considering the importance of all the concepts presented above, what are the topics to be observed by companies planning for the future of their business security? Some points need to be considered during this process:
First, the network must be structured to move data between all points covered, from cloud services to the data center. Ensure that consistent protocols and policies are applied across the network. Traffic should be routed through a network that is built to support SSE, i.e. consists of globally distributed points. So that employees at home, in the office, or in the cafeteria are using their devices properly secured and performing their activities at a high level, while the company’s data remains secure.
You need to know how sensitive certain information is and how important it is to the corporation. And what impact it would have on the organization if this information were available to unauthorized parties. In this case, information classification would help ensure that the information is made available correctly and securely.
Security services should be fully integrated. By reducing the number of individual tools, management and administration is made easier, ensuring consistent policy enforcement, efficient traffic and processing, and decisions are made efficiently, supporting and securing the cloud strategy.
It’s also necessary to know the flow of information, where certain information will transit. As well as ensuring that this flow is inspected, assuring that the information is accessed in a secure manner. By using control configurations during data traffic such as encryption, tokens, and identity management, among others.
It’s crucial to define what each user can access, meaning who will be allowed to access what, considering what resources each employee needs to perform his or her job. Making sure that users do not have inappropriate or excessive levels of access is essential. When you ensure “least access” as part of your access strategy, you can minimize the impact if any accounts are compromised, because they will only have access to an isolated subset of corporate assets.
Finally, it’s worth emphasizing that more than ever Cybersecurity needs a strategic look when it comes to mitigating the impacts of Shadow-IT. With the growing number of attacks worldwide, coupled with all this technological diversity that we have available, as well as the changes in the ways we work, especially as a result of the Covid-19 Pandemic, many companies that have not yet considered cybersecurity as part of their organizational strategy have stopped to re-evaluate their processes or even migrate their services to a cloud environment and thus keep their environments safe. Considering the scenario exposed, the Cloud service brings with it several benefits, efficiency and agility without leaving aside the guarantee of cyber and information security.
References
Estudo de caso da GE Oil & Gas. Available at: <https://aws.amazon.com/pt/solutions/case-studies/ge-oil-gas/>. Acessed: 4 Aug. 2022.
Expedia Case Study. Available at: <https://aws.amazon.com/pt/solutions/case-studies/expedia/>. Acessed: 3 Aug. 2022.
GLOBAL Cybersecurity Leader. [S. l.], 1 Aug. 2022. Available at: <https://www.paloaltonetworks.com>. Acessed: 2 Aug. 2022.
Learning Articles Archive. Available at: <https://www.skyhighsecurity.com/en-us/cybersecurity-defined>. Acessed: 3 Aug. 2022.
Netskope. Available at: <https://www.netskope.com>. Acesso em: 3 ago. 2022..
What is SSE? Available at: <https://www.forcepoint.com/pt-br/cyber-edu/security-service-edge-sse>. Acessed: 2 Aug. 2022.
