By Gabriel Siqueira de Oliveira
As the technology continues to advance and cryptocurrencies become more widespread, a phenomenon has emerged behind the scenes of the digital revolution: cryptojacking. This malicious practice is becoming more and more common, affecting companies and individuals all over the world by exploiting their computing resources for illegitimate gain.
Cryptojacking is an insidious technique in which hackers take control of the processing power of other people’s devices, such as personal computers, smartphones and servers, in order to mine cryptocurrencies without the owners’ knowledge or consent.
This article explores the main points of the cryptojacking phenomenon, presenting its origins, operation and consequences for individuals and organizations. In addition, we’ll analyze the main methods of infection, the types of cryptocurrencies most targeted by criminals and the tactics they use to hide in the shadows of the Internet.
The rise of cryptojacking has caught the attention of cybersecurity experts, governments and companies, who are looking for effective solutions to combat this threat. Throughout this article, we’re also going to cover the preventive measures that can be adopted to protect against this malicious practice and how public awareness is essential to mitigate the risks associated with cryptojacking.
What is Cryptojacking?
Before we get a literal definition of what cryptojacking is, it’s interesting to know the origin of its name. In the market, the most common definition of the word “Crypto” is cryptocurrency. “Jacking”, on the other hand, can mean the act of obtaining something illegally or irregularly.
Cryptocurrency is digital or virtual money, which takes the form of tokens or “coins”. The most famous is Bitcoin, but there are approximately 3,000 other forms of cryptocurrency.
Cryptojacking is a form of cybercrime malware in which the criminal illegally uses the victim’s device, such as a computer or cell phone, stealing processing power to generate cryptocurrencies.
Cryptocurrency mining is not illegal, as long as it is done correctly without harming people or companies. As soon as an individual uses the processing power of a device without the authorization of its owner, the act of mining becomes a cybercrime known as cryptojacking.
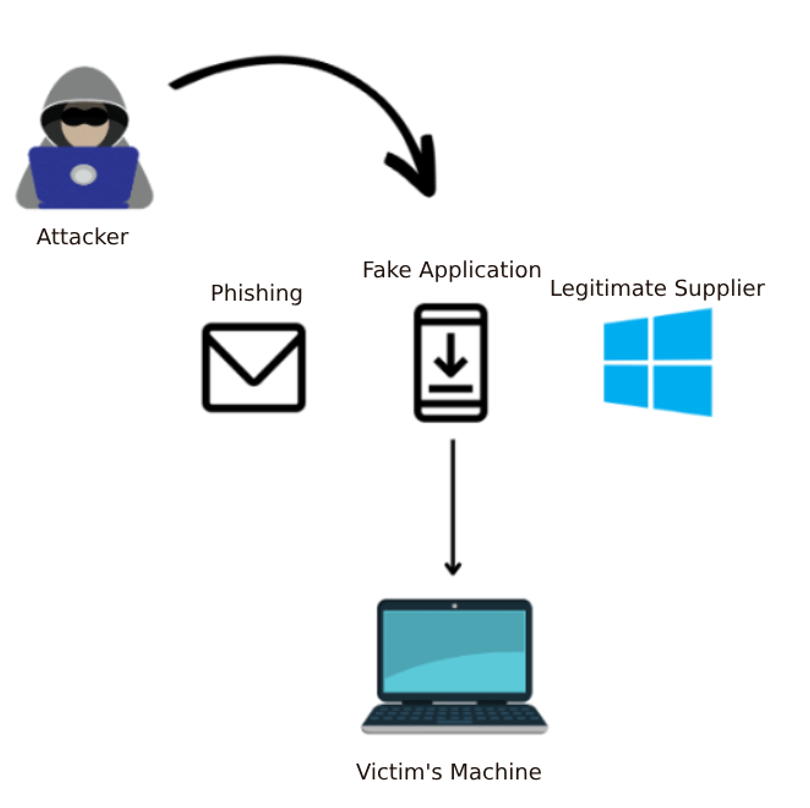
The crime involves two channels: host or browser.
Through the host, the malware is distributed, which can be installed in a variety of ways, the 3 most popular being:
- Phishing:sending the victim a malicious e-mail attachment
- Fake application: using a fake application (e.g. game) that contains the malware
- Legitimate software: compromising the supply chain of a legitimate software vendor by inserting the malware into the software.
According to the RSA Conference website, phishing is the most frequent source of threats, which makes it even more important to be careful when dealing with links and attachments in any type of communication.
In the case of browser-based attacks, which are the most common, hidden codes are used on websites to exploit the processing capacity of equipment and can take advantage of any device connected to the Internet. This fits in with the concept of fileless malware, which uses the operating system’s own tools and processes through a technique known as “Living off the Land”, which allows malicious activities to be carried out using pre-installed elements and without installing additional executables on the victim’s system.
According to the SentinelOne website, the most common way of contracting fileless malware is when the victim clicks on a spam link in a fraudulent email or website.
Why is this a concern?
Cryptojacking may seem like a harmless crime, since the only thing “stolen” is the power of the victim’s computer, to the benefit of the criminal who is illicitly creating coins. As a large number of infected devices generate a huge amount of cryptocurrency, cybercriminals see this as a lucrative crime.
According to an article in Exame magazine, the perpetrator can make a profit of up to 40,000 dollars a month.
The main impact of cryptojacking is related to the performance of the device, which can cause overheating and hardware damage (loss of components due to overheating). Given this, attention must also be paid to the costs for the individuals and companies affected because the generation of coins uses high levels of electricity and computing power. In addition, the increase in expenses related to higher energy consumption is also a relevant factor.
In the scenario where cryptojacking is installed on a mobile device, the main “symptom” is battery drain, because even if you keep a browser tab on your phone in the background, the script installed in the website’s code is consuming the device’s resources.
Imagine a scenario where the cybercriminal wants to use 100 machines to generate cryptocurrencies. He might try to attack corporate machines, where crime detection generally tends to be quick. But what if the attacker targets home devices where the user will only notice the slowness of their machine?
The crime could go on for hundreds of days and the victim would never know. The scalability of this crime is immense, given the stealth with which it takes place.
Cryptojacking in real-life
As cybercrime grows, the law needs to catch up and quickly combat harmful incidents. One of the countries that has taken firm action in these cases is Japan.
A criminal was tried for embedding a malicious library inside a gaming tool that was made available for download, and according to the authorities, consumed by around 90 people, resulting in the criminal being fined approximately 45 dollars and sent to prison for a year, according to the report.
Cryptojacking by industry
According to the “2022 SonicWall Cyber Threat Report” by cybersecurity company SonicWall, cryptojacking attacks in the government sector increased by 709% up until the end of 2021, around three times more than cyberattacks targeting the health sector.
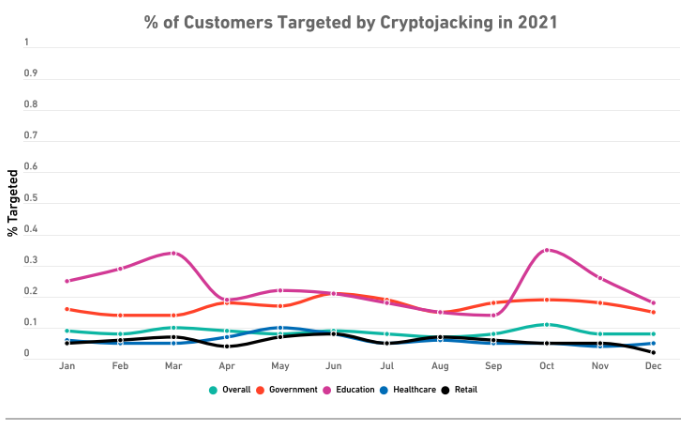
SonicWall researchers observed that even with the intense drop in prices in January 2022, cryptojacking cases continued to rise, showing that incidents continue regardless of price fluctuations.
The researchers pointed out that the increase in cases is related to the strong campaign to suppress ransomware attacks, causing some cybercriminals who used to employ those attacks to switch to cryptojacking, where the invasion is silent and the profit remains the same.
I’ve been infected – now what?
Don’t panic! The first step is to disconnect the hardware from the network and Internet so that mining activity is interrupted and there is no risk of spreading the malware to other devices. Once this is done, the focus is on removing the artifact from the machine.
As mentioned earlier, cryptojacking can also be carried out through browsers, so part of the removal process is to uninstall or disable extensions used in browsers or not to access certain pages with malicious scripts.
Installing an antivirus focused on malware protection is crucial in order to identify all system and registry files to find the root of the malware and clean it out of memory. In addition, the antivirus can act proactively to stop malicious code from infecting the machine through behavioral detections and web traffic analysis.
Last but not least, installing an ad-blocker or anti-cryptomining is essential for combating malware. The extension will stop one of the cybercriminals’ main attack channels, ads on web pages.
For more information on how to protect your privacy and defend yourself against certain cyber attacks, I recommend reading the article Cryptography: Applications to ensure your privacy.
Conclusion
The idea that major cybercrime losses are primarily linked to ransomware attacks is outdated. The study “Vulnerability and Threat Trends”, conducted by Skybox Security, showed that illicit cryptocurrency mining already accounts for 32% of cyberattacks, while ransomware threats account for only 8%.
Considering all the above and the growing number of cases, the cybersecurity community needs to start looking at this as a potential risk and not just a low-impact incident, making the corporate and personal environment safer.
In other words, as well as investing in security, companies must educate their employees to take advantage of best practices, through training and lectures, so that they avoid becoming victims of the attack. Informed employees can pass on their knowledge to acquaintances and family members, raising mass awareness so that ordinary users don’t suffer the same crime.
References
Ataques em computadores para minerar criptomoedas subiram 200%, diz estudo. Available at: <https://exame.com/future-of-money/ataques-em-computadores-para-minerar-criptomoedas-subiram-200-diz-estudo/>.
Cryptojacking. Available at: <https://www.interpol.int/en/Crimes/Cybercrime/Cryptojacking>.
Cryptojacking: como detectar e evitar – HF Tecnologia. Available at: <https://hftecnologia.com.br/cryptojacking-como-detectar-e-evitar/>.
Cryptojacking: Impact, Attack Examples, and Defensive Measures. Available at: <https://www.aquasec.com/cloud-native-academy/cloud%20attacks/cryptojacking/>.
Internet Security Threat Report ISTR Cryptojacking: A Modern Cash Cow An ISTR Special Report |. [s.l: s.n.]. Available at: <https://docs.broadcom.com/doc/istr-cryptojacking-modern-cash-cow-en>.
KASPERSKY. What is Cryptojacking? – Definition and Explanation. Available at: <https://www.kaspersky.com/resource-center/definitions/what-is-cryptojacking>.
NASCIMENTO, D. P. DO. Como identificar “cryptojacking” e evitar que minerem cripto pelo seu computador. Available at: <https://www.moneytimes.com.br/como-identificar-cryptojacking-e-evitar-que-minerem-cripto-pelo-seu-computador/>.
O impacto na segurança do aumento dos preços das criptomoedas. Available at: <https://www.rsaconference.com/library/blog/the-security-impact-of-rising-cryptocurrency-prices>.
OSBORNE, C. Japan issues first-ever prison sentence in cryptojacking case. Available at: <https://www.zdnet.com/article/for-the-first-time-remote-cryptojacker-sentenced-for-exploiting-coinhive/>.
What enterprises need to know about cryptojacking. Available at: <https://www.perle.com/articles/what-enterprises-need-to-know-about-cryptojacking-40184800.shtml>.
What is Fileless Malware. Available at: <https://www.sentinelone.com/cybersecurity-101/fileless-malware/>.
What is malware? Everything you need to know. Available at: <https://www.sentinelone.com/cybersecurity-101/what-is-malware-everything-you-need-to-know/>.
2022 SonicWall Cyber Threat Report. Available at: <https://www.sonicwall.com/resources/white-papers/2022-sonicwall-cyber-threat-report/>.
