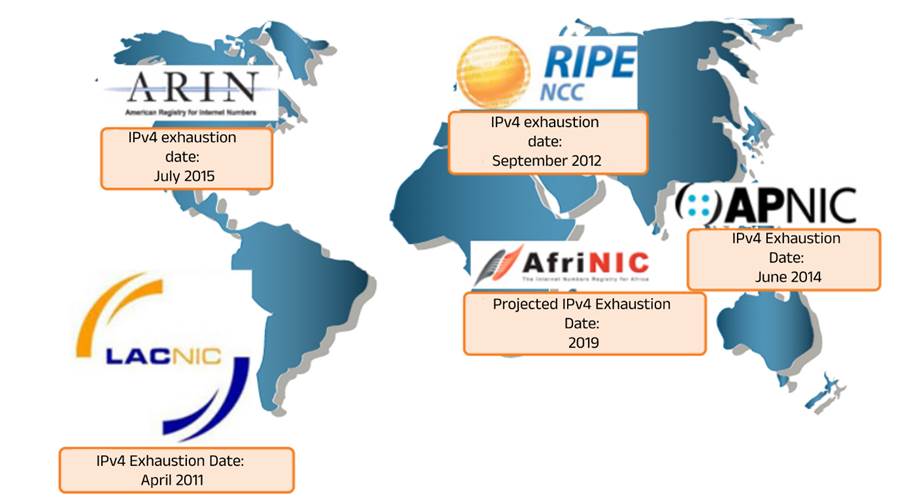
he IPv4 addressing protocol was created by the Internet Engineering Task Force (IETF) in 1981 to connect 232 devices to the World Wide Web. However, all Regional Internet Registries (RIRs) have limited supplies or have exhausted the available IPv4 addresses in 2019[1].
To circumvent IPv4 address exhaustion, a solution called NAT (Network Address Translator) was created. However, NAT is problematic for many applications because it creates latency and has limitations that severely impede point-to-point communications[2]. In addition, with the rise of the mobile internet and the emergence of IoT devices the need for public IP addresses has increased exponentially. Consequently, the IETF needed to create a new protocol with greater addressing capacity: that’s how IPv6 was born, with the capacity to connect 2¹²⁸ devices.
With new technology comes new vulnerabilities. It’s common to find firewall and security configurations, in general, geared towards the IPv4 protocol, which is still the most used network layer protocol on the Internet. However, the use of IPv6 addresses is expanding, as they are being distributed by ISPs (Internet Service Providers), leading to an additional concern about the security of the networks that already use the protocol.
The purpose of this blog post is to briefly explain how the IPv6 protocol works and then raise awareness about the existing risks – in case of negligence in its configuration in firewalls, ACLs, etc. The main idea is to corroborate the argument that a good configuration of firewall rules for the IPv6 protocol is essential for the security of an organization.
What are the differences between the IPv4 and IPv6 protocols?
To begin with, it’s important to note the differences between the two protocols. The following table compares both protocols, explaining these distinctions:
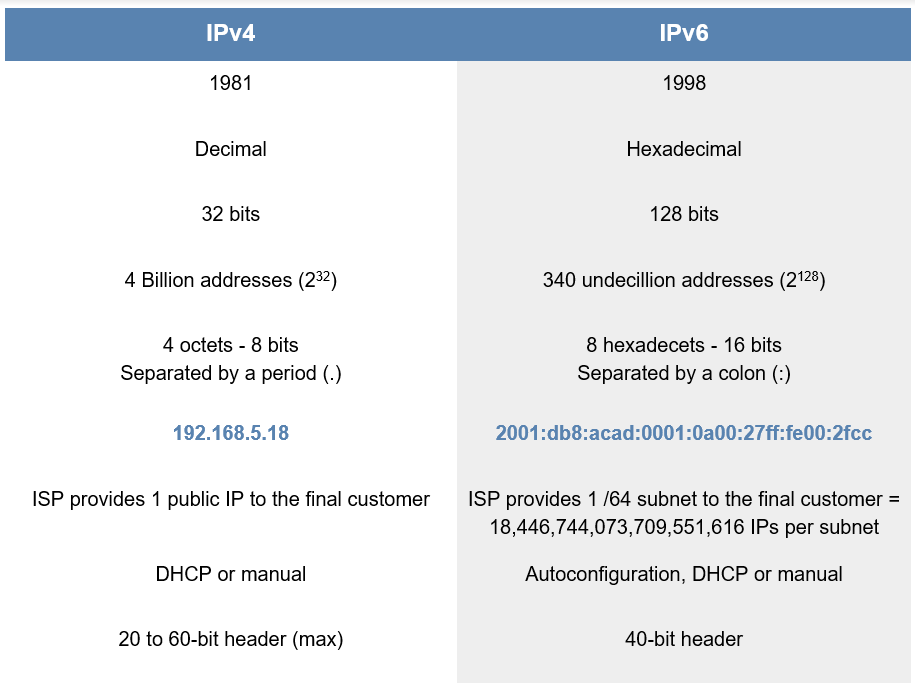
Nevertheless, both protocols operate at layer 3 of the OSI model – the network layer – as do other protocols such as ICMP, ARP, IPsec, MPLS. The IPv4 and IPv6 protocols may have certain differences, but they perform the same function.
Representation of IPv6 addresses
An IPv6 address is much longer than an IPv4 address. It’s common to see abbreviations of these addresses in literature and on devices. For example, it’s common practice to omit leading zeros from hexadecatets:
2001:0db8:0000:0000:0000:0000:0000:0001
2001:db8:0:0:0:0:0:1
In addition, abbreviation of continuous zeros is common:
2001:db8:0:0:0:0:0:1
2001:db8::1
However, this abbreviation can only be done once, in the longest string of zeros.
The representation of IPv6 addresses in URLs is done in square brackets so that there is no ambiguity if it is necessary to indicate a port number
https://[2001:db8:0:2::53]/index.html
https://[2001:db8:0:2::53]:8080
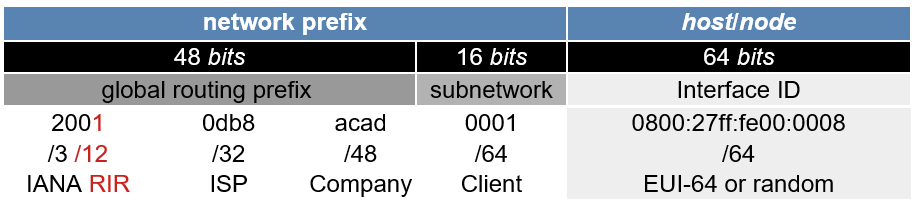
IPv6 addresses are divided into two main portions: the network prefix and the interface identifier. Each portion is assigned by default a /64 in CIDR (Classless Inter-Domain Routing) notation:
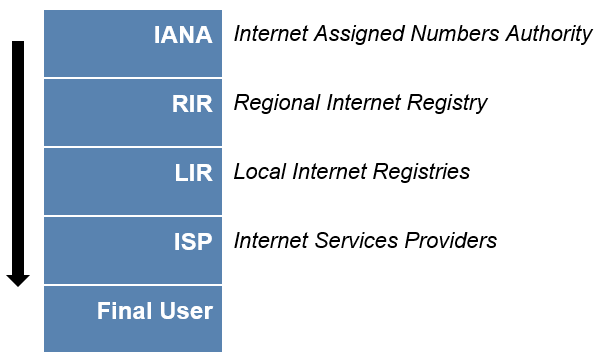
The order of IP address distribution is as follows: IANA distributes addresses to the RIRs, which distribute addresses to the LIRs, which then distribute the addresses to the ISPs, the latter distributing them to the end users, whether they are companies or individuals:
IPv6 Address Types
There are three types of addressing in the IPv6 protocol: Anycast, Multicast and Unicast.
An Anycast address is used for mirroring hosts. Root DNS servers – there are 11 in total – which have the same IP address. This is only possible because machine mirroring is done: when one server stops, another takes over. NTP servers also work this way; these servers have the same IP address and respond to several different clients.
A Multicast address is an identifier for a set of interfaces that usually belong to different nodes. A packet sent to a multicast address is delivered to all interfaces identified by that address. If you block a multicast address on a firewall, nothing else on your network will work, so it should be handled carefully. Multicast addresses have a default prefix of FF00::/. Some examples of multicast addresses are:

A Unicast address can be divided into three categories: Global, Unique Local, and Link-Local.
A Global Unicast Address (GUA) is the same as a public IPv4. This 2000::/3 range is the subnet of the total IPv6 for the entire world, which is 13% of the total possible addresses (released by the IANA, which we use today). A GUA is routable on the Internet, and its range is between 2000::/3 and 3FFF:FFFF:FFFF:FFFF:FFFF:FFFF:FFFF:FFFF.
A Unique Local Address (ULA) is the same as a class A, B and C private IPv4 (10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16), and can be used if you need to create an internal network to connect your printer, local servers, etc. It can be routed in an internal network or VPN, but not on the Internet. The prefix is FC00::/7.
A Link-Local Address (LLA) is the same as a private IP that is automatically created on your interface; for example, the address 169.254.0.0/16 in IPv4 – when there is no dynamic address assignment (DHCP). LLA is meant to be the Automatic Private IP Addressing (APIPA) of IPv6.
In IPv4, when you get a fixed IP or via DHCP, it “kills” the 169.254.0.0/16. In IPv6, it remains as an automatically created, nonroutable, local private interface IP address used on a single network segment. Its range is FE80::/64, where the other /64 interfaces will be configured by the EUI-64 process (explained later).
In IPv6, some addresses or address ranges have unique uses such as:

IPv4 and IPv6 Coexistence
The IETF has created several protocols and tools to help network administrators migrate networks to IPv6[3]:
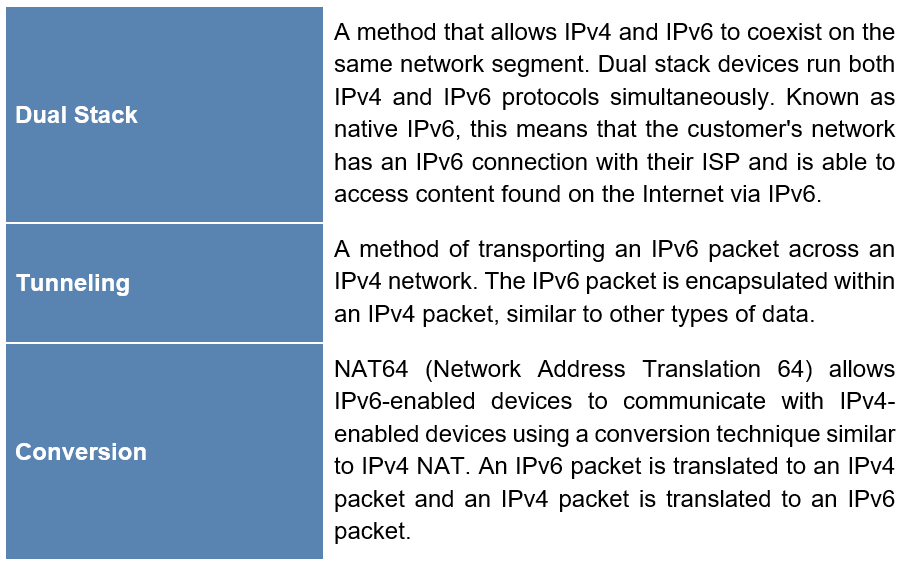
Dynamic addressing for IPv6 GUAs
If you do not want to configure IPv6 addresses manually, it can be configured dynamically by ICMPv6 router solicitation (RS) and router advertisement (RA) packets. RA is used for a device to obtain a global unicast IPv6 address and includes:
- network prefix and prefix length
- the default gateway address (an IPv6 LLA address, which is the source of the RA message)
- DNS address and domain name
IPv6 routers send ICMPv6 RA messages every 200 seconds to all IPv6-enabled devices in the network, and also send RA messages in response to RS messages.
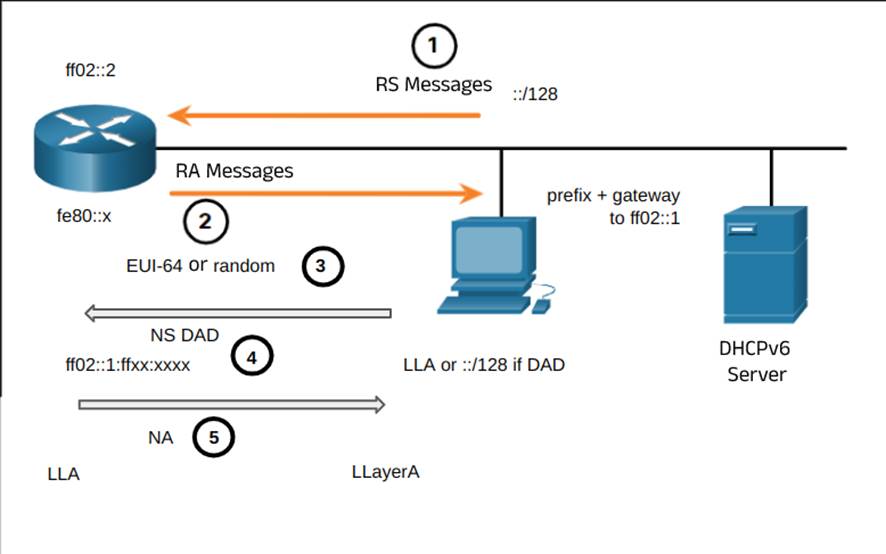
There are three methods for RA messaging:

When the router advertisement message is submitted via SLAAC or SLAAC with stateless DHCPv6, the client must generate its own interface ID, and this can be done either with a random 64-bit number or by the EUI-64 (Extended Unique Identifier) process.
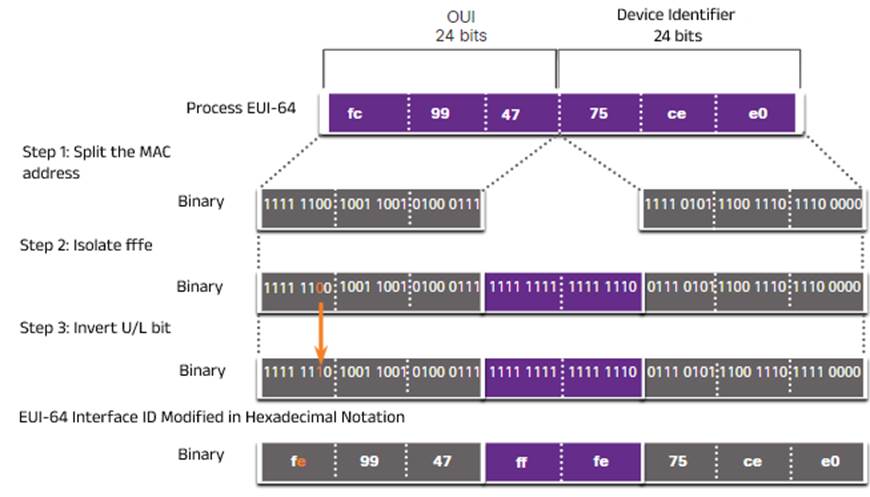
This process is simple: it takes the 48-bit Ethernet MAC address of the machine – consisting of 24 bits of Organizationally unique identifier (OUI) – which is the vendor code, and 24 bits of Device identifier (ID) – a unique value with an OUI in common, inverts the 7th bit of the OUI, and inserts an FFFE value between the OUI and the ID:
EUI-64: MAC OUI (24 bits) with 7th bit reversed + FFFE (16 bits) + MAC ID (24 bits) = 64-bit interface ID:
Security issues of the IPv6 protocol
Now that we understand how the IPv6 protocol works, let’s understand some of the problems associated with it. There are some vulnerabilities similar to those of the IPv4 protocol, but some are new and inherent to the operation of the IPv6 protocol.
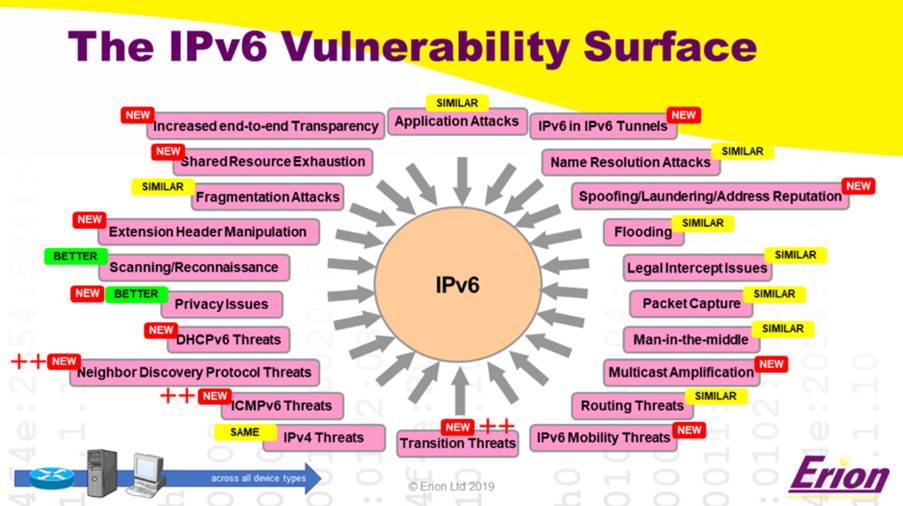
The security challenges and problems inherent to the operation of the protocol create room for the existence of vulnerabilities in devices. The United States National Security Agency released a paper in January 2023, on IPv6 security concerns and recommendations. It can be seen that these concerns and challenges are interconnected in some way:
ICMP and Multicast
É comum bloquearmos pacotes ICMP no IPv4 como medida de segurança. Contudo, o funcionamento do IPv6 depende do ICMPv6 para mensagens de erro, descoberta de unidade de transmissão máxima (maximum transmission unit – MTU) de caminho, gerenciamento de grupo multicast e descoberta de vizinhos. A maneira como o multicast funciona é um desafio para firewalls, detecção de intrusão e ACLs.
It is common for us to block ICMP packets in IPv4 as a security measure. However, IPv6 operation depends on ICMPv6 for error messages, maximum transmission unit (MTU) path discovery, multicast group management, and neighbor discovery. The way multicast works is a challenge for firewalls, intrusion detection, and ACLs.
Dual Stack
Dual stack means the coexistence of IPv4 and IPv6 protocols. It is one of the essential transition methods to IPv6 and the most widely used in the world today. However, this means that security must be maintained for both, which increases the costs of time and effort, causing organizations like Facebook to adopt IPv6 in their internal networks and use conversion techniques at the edges of the network.
Automatic Tunneling
Tunneling means that the packets of one protocol are encapsulated by another. Tunneling is also an essential IPv6 transition technique. However, some off-the-shelf operating systems will automatically establish an IPv6 network when a client is connected to a server, for example, various versions of Windows. Potentially unwanted new paths to hosts may be configured and firewalls may not be prepared.
Autoconfiguration
This is an efficient and cost-effective process, it tends to produce the existence of vulnerabilities. When SLAAC uses the EUI-64 process, it exposes the MAC address of the client, which may allow the host to be identified via the interface ID, NIC manufacturer, or host vendor. Addresses generated by random, temporary, or cryptographic means are the best option. Another solution is to use a DHCPv6.
Multi-addressed Hosts
It is common for a host to have multiple addresses in IPv6 as a result of SLAAC, temporary DHCPv6, LLA addresses, multiple prefixes, overlapping lifetimes, in addition to IPv4 addresses. Administrators should be aware of all possible interface addresses.
IPv6 scans
Sequential scans on a /64 subnet are useless. It would take 500,000 years to scan a single /64 at one million probes per second. However, the suggested scanning (using other sources for address range information) may still be possible. This can be done, for example, with the help of public hitlists such as: Alexa domains and Cisco Umbrella, NDP, routing table, whois or reverse DNS, SLAAC + EUI-64 + invader with enough previous information. For example, in a static/manual configuration or with stateful DHCPv6, IPv6 network addresses may have a known structure (organizations that number their hosts sequentially), such as:
::3, ::4
::aaaa, ::bbbb
::1:80, ::2:22, ::3:443 etc (portas IPv4)
::1000-2000, ::100-200, ::1:0-1000, ::1:1000-2000
IPv6 protocol misconfiguration and its consequences
Now that we understand how the protocol works, how it’s represented, their types and how they are configured, we can reach some conclusions:
- The fact that the dual stack exists and most ISPs distribute GUA addresses to their clients makes the inference plausible that a large number of devices have more than one active IP address.
- In general, standard router protections and firewall rules come with basic security measures. If someone knows the GUA address of your device, it can be accessed directly from anywhere in the world and thus exploited.
- An attacker using network reconnaissance techniques could access servers and personal files simply because there is no security configuration established for the IPv6 protocol.
As a demonstration of how this could happen, we can take RFC 7707 as a reference, in which network reconnaissance techniques within the IPv6 scope are described that can be used to exploit a misconfiguration of system security. Therefore, these techniques can help an attacker access machines and exploit them.
To demonstrate the hazards of misconfiguration – or negligence in configuration – of the IPv6 protocol, a lab was set up with the following topology:
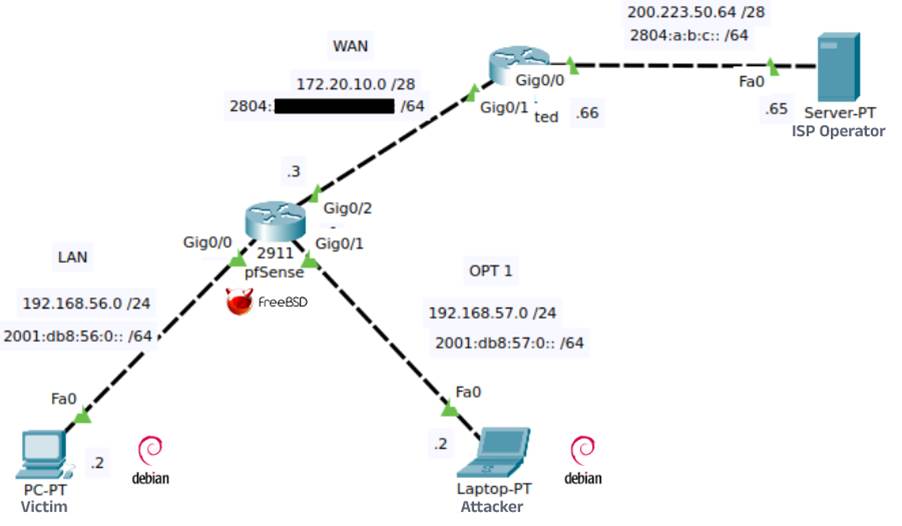
In this lab, machines have been configured in a way that simulates a stateful DHCPv6, in which devices receive addressing in a low-byte sequential manner.
We can notice that there are two LANs directly connected (administrative distance 0) to a pfSense firewall; and that both LANs have been assigned an IPv4 addressing and an IPv6 addressing. In this lab, the attacker is running a Debian on LAN OPT1, while the victim is running a Debian on LAN OPT0.
PfSense has its interfaces configured as follows:
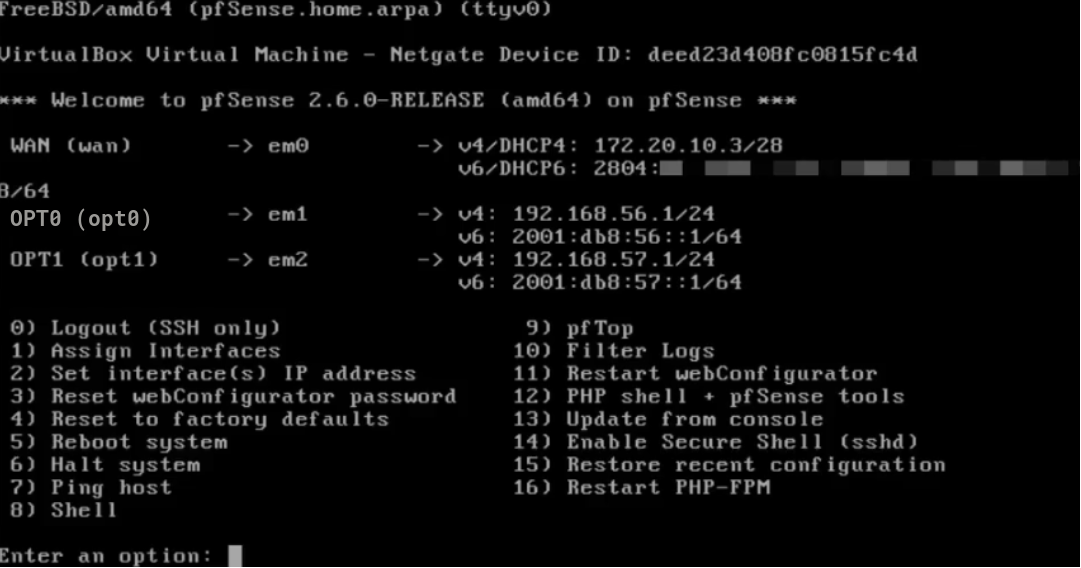
Furthermore, we can notice that the pfSense firewall rules are configured to block ICMPv4, TCPv4, and UDPv4 packets coming from lan OPT1, while IPv6 protocol packets are not configured:
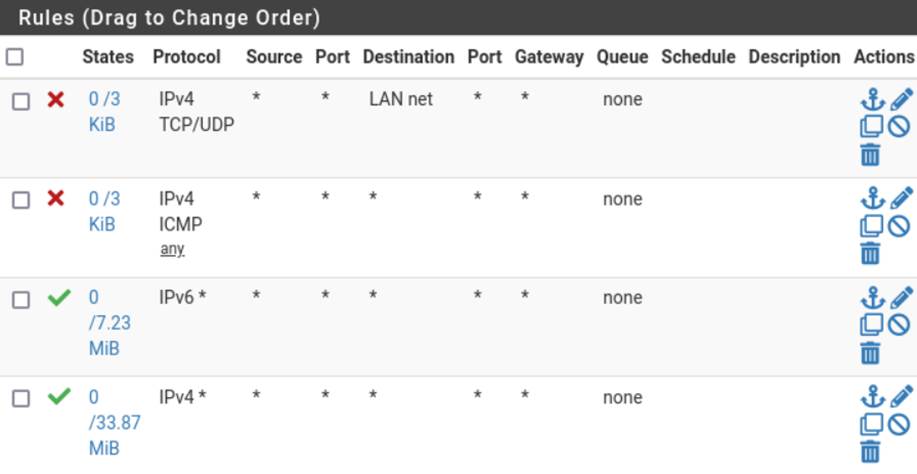
In addition to the pfSense firewall, the victim has on his device an IPTables firewall configured with the DROP policy for ICMPv4, TCPv4 and UDPv4, releasing only ports for internet, DNS, traceroute and loopback operation:
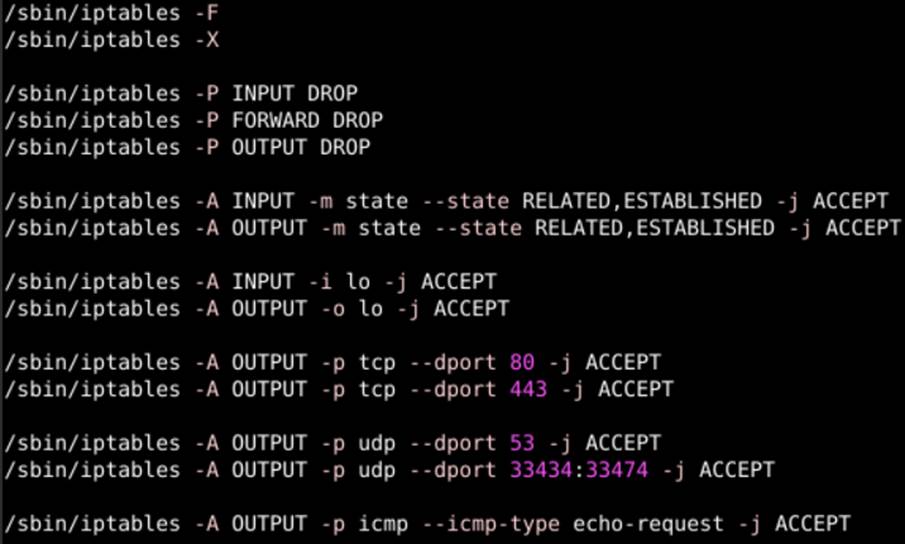
We can notice that, in theory, no ICMP packets or TCP/UDP segments coming from LAN OPT1 will reach LAN OPT0. To demonstrate that both firewalls are active and functional, the ping and traceroute tools were used from the attacker’s machine to the victim’s machine and vice versa:
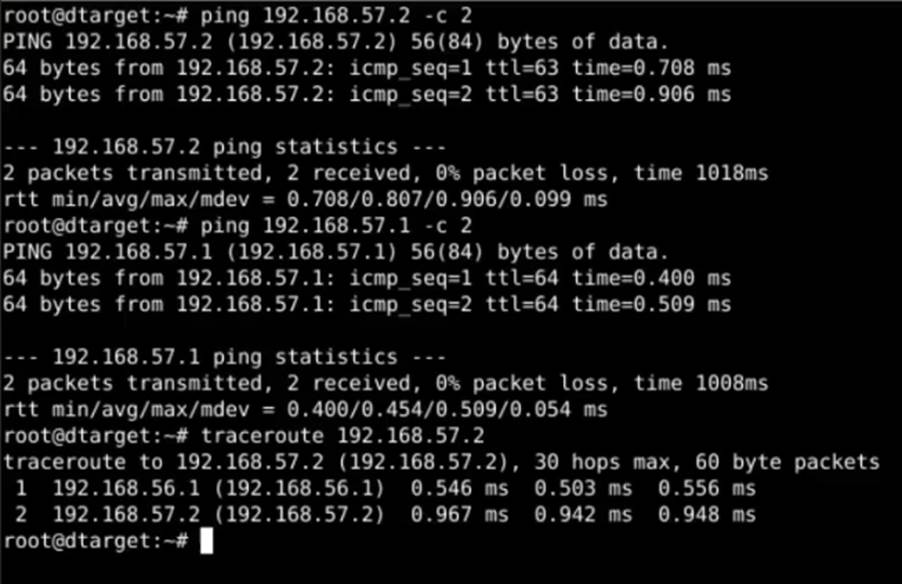
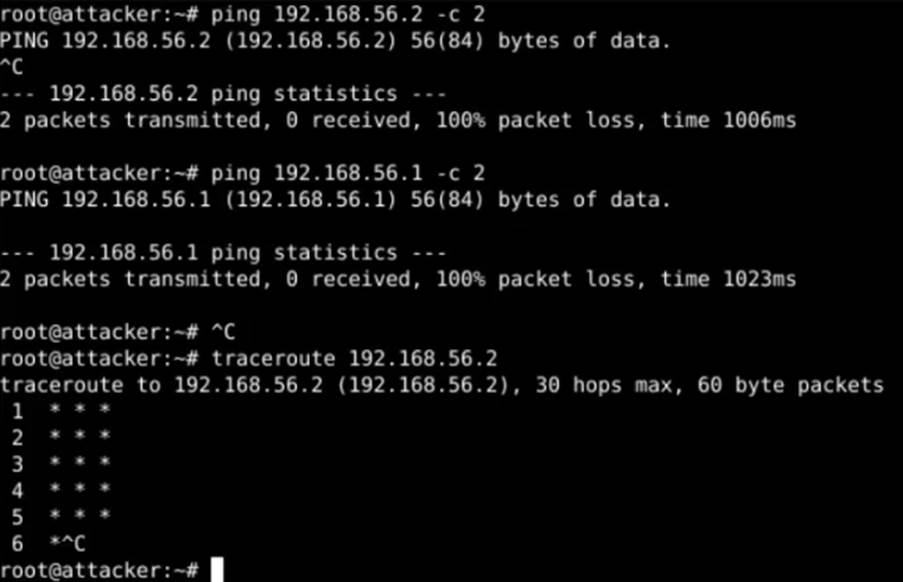
Using nMAP, we can see that there are no active hosts returning on the victim’s LAN, or that ICMP packets are being blocked:
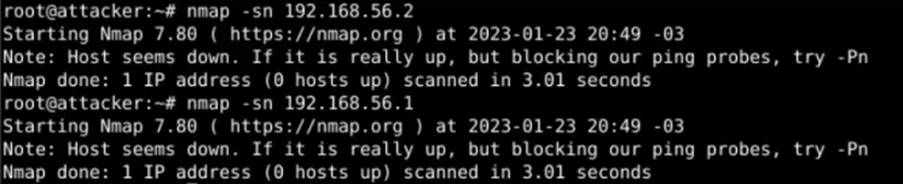
So we can conclude that the victim’s network is protected… or can we really say that?
As we saw earlier, there is no configuration in pfSense or IPTables for the IPv6 protocol. We can try a suggested scan of the victim’s LAN to discover active hosts with the -sn flag of nMAP:
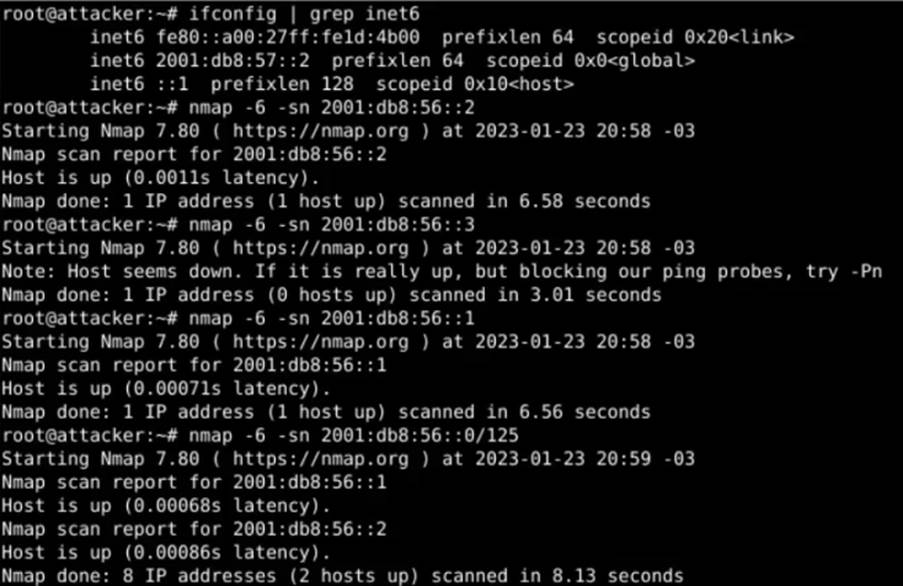
In the example above, we can see that there are two active hosts on the network 2001:db8:56::0/64. Using the -sV flag of nMAP, we can get more information about these active hosts:
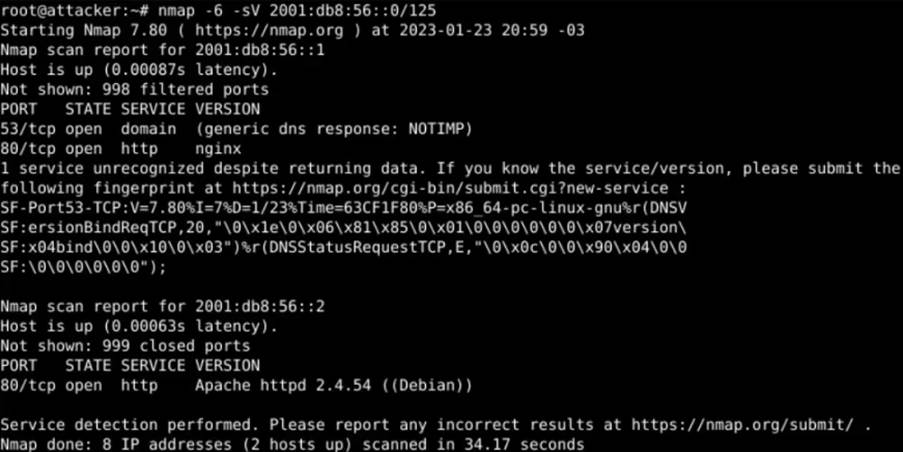
You can see that there are servers running on port 80 on both active hosts: a NGINX and an Apache. We can even see the version of the Apache server and the operating system on which it is running. Since we know that there is a web server running on each host, we can try to access this server through the browser:
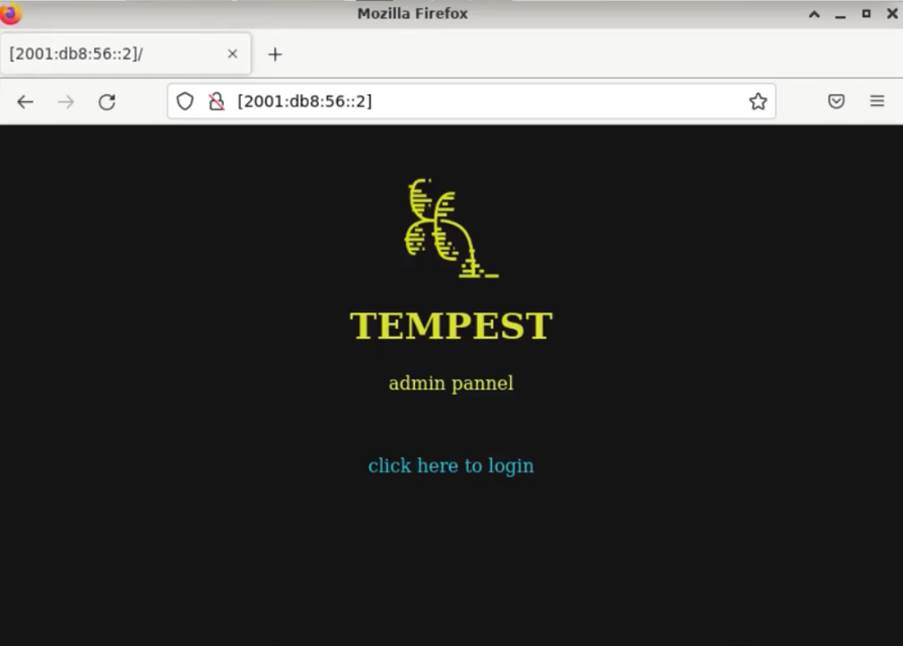
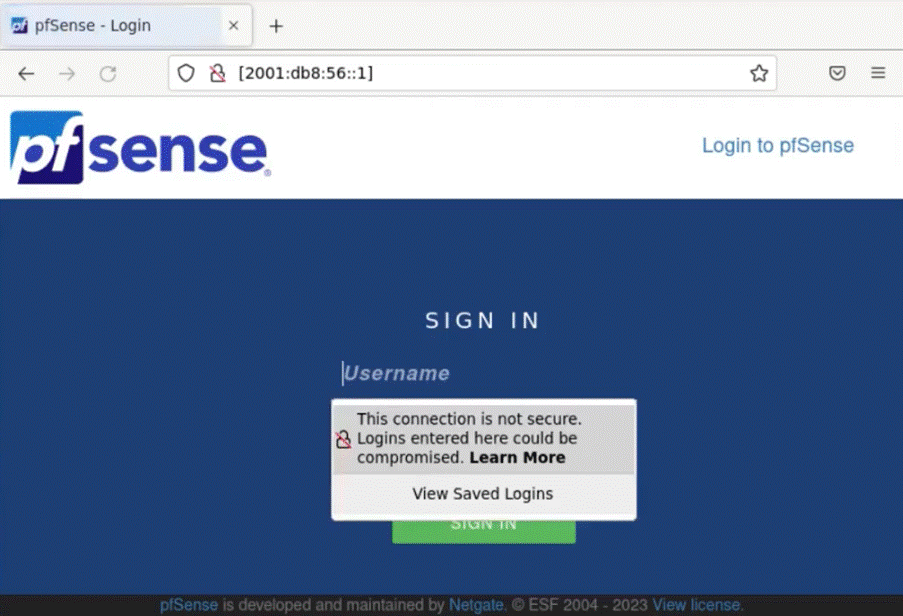
We can notice that the misconfiguration of the IPv6 protocol in both firewalls provided us with access to pfSense and to an internal page of the company, even with all access being restricted by the IPv4 protocol.
Conclusions and recommendations
Misconfiguration is always a big problem for companies. We can observe that it is clearly more difficult to perform a scan on IPv6 addresses when we consider, as a reference, the IPv4 model, but a suggested scan is still quite possible. If there is no well-defined configuration in firewalls, ACLs, etc., and a scan of this type is effective, i.e. active hosts are found, exploits become plausible.
The purpose of this post was to serve as a whitepaper to raise awareness that both IPv4 and IPv6 protocols must be configured taking into consideration doctrinal concepts of information security. Thus, having established the relevance of this premise, some recommendations are listed below:
- Regarding the dual stack context: security mechanisms must be implemented in both IP protocols with the aim of protecting the network;
- IPv6 address configuration using a standardized structure (SLAAC with EUI-64 (RFC 4941), tunneling and NAT64) should be avoided;
- Change the mindset of security by obscurity, i.e., just because it’s harder to discover an IPv6 address doesn’t mean you are secure purely because of that;
- Filter IPv6 traffic: RFC 4890 shows how to do this for ICMPv6;
- Beware of misconfiguration: RFC 9099;
- Configuring your firewall for IPv6.
Once again, the lab set up in this research had the specific goal of demonstrating how a security flaw involving misconfiguration of the IPv6 protocol can leave your device vulnerable. However, further tests could be done with other operating systems, IoT and mobile, simulating different infrastructure configurations, topology and administrative distances, as well as testing all types of dynamic addressing and other migration protocols.
References
ANBAR, Mohammed; BELATON, Bahari; ELEJLA, Omar. ICMPv6-Based DoS and DDoS Attacks and Defense Mechanisms: Review. IETE Technical Review, v. 34, p. 1-18, 2016. Available at: https://www.tandfonline.com/doi/abs/10.1080/02564602.2016.1192964. Accessed on: Jan. 2023.
APNIC BLOG. Available at: https://blog.apnic.net.
[1] APNIC. Gerenciamento de IP – Esgotamento do IPv4. Disponível em: https://www.apnic.net/manage-ip/ipv4-exhaustion/#globalipv4-run-out.
CAICEDO, Carlos et al. Study of IPv6 Security Vulnerabilities. 2014. Available at: https://www.researchgate.net/publication/276818459_Study_of_IPv6_Security_Vulnerabilities. Accessed on: Jan. 2023.
[2] CISCO NETWORKING ACADEMY. CCNA1.
[3] CISCO NETWORKING ACADEMY. CCNA1 – Introdução a redes. São Paulo: Cisco
GOODIN, Dan. Using IPv6 with Linux? You’ve likely been visited by Shodan and other scanners. Ars Technica, 1 feb. 2016. Available at: https://arstechnica.com/information-technology/2016/02/using-ipv6-with-linux-youve-likely-been-visited-by-shodan-and-other-scanners/. Accessed on: Jan. 2023.
IPV6.BR. Available at: https://ipv6.br. Accessed on: Jan. 2023.
NATIONAL SECURITY AGENCY (NSA). IPv6 Security Guidance. 2015. Available at: https://media.defense.gov/2023/Jan/18/2003145994/-1/-1/0/CSI_IPV6_SECURITY_GUIDANCE.PDF. Accessed on: Jan. 2023.
ROHRER, JUSTIN P. Ph.D. TaNCAD, NPS, Monterey, CA. Hacking IPv6: Security and Attacks vs IPv4 | Network Traffic Analysis Ep. 11 | CS4558. 2015. Available at: https://www.youtube.com/watch?v=aEYeWy4Zf68. Accessed on: Jan. 2023.
RFC 2373. IP Version 6 Addressing Architecture. 1998.
RFC 4443. Internet Control Message Protocol (ICMPv6) for the Internet Protocol Version 6 (IPv6) Specification. 2006.
RFC 4890. Recommendations for Filtering ICMPv6 Messages in Firewalls. 2007.
RFC 7123. Security Implications of IPv6 on IPv4 Networks. 2014.
[4] RFC 7707. Network Reconnaissance in IPv6 Networks. 2015.
RFC 7721. Security and Privacy Considerations for IPv6 Address Generation Mechanisms. 2016.
ULLRICH, Johannes. Targeted IPv6 Scans Using Pool.ntp.org. SANS Internet Storm Center, 2016. Available at: https://isc.sans.edu/diary/Targeted+IPv6+Scans+Using+poolntporg/20681. Accessed on: Jan. 2023.
ULLRICH, Johanna et al. IPv6 Security: Attacks and Countermeasures in a Nutshell. 2014. Available at: https://www.sba-research.org/wp-content/uploads/publications/IPv6Sec-INutshell.pdf. Accessed on: Jan. 2023.
