What is Shadow IT and why it is bad for your business
Have you, as an IT employee, ever found yourself in an emergency where you needed to separate a single PDF into several different PDF files? And when you googled for a quick and easy tool for the situation, you came across that beautiful online website where your only job would be to drop the files into the cloud and a few seconds later your single PDF would come back to you in several separate and well-organized pages. How cool are these cloud tools, aren’t they? What if I told you that by using cloud tools similar to this one, you may be offering your PDF document in the cloud from entities that often have low security on their platform and false promises to “delete your file after use”?
This practice, often driven by the desire of the professional to want to contribute to your company, aiming to optimize a process and make the work environment more dynamic, may end up contributing to information leakage or compromise of the environment, bringing serious problems for the organization.
In the article Shadow IT evaluation model presented at the Federated Conference on Computer Science and Information Systems (FedCSIS) in 2012 by the authors C. Rentrop and S. Zimmermann, we can define Shadow IT as an unofficial IT infrastructure that ends up existing in several companies, acting in a hidden way, in conjunction with the “official” IT infrastructure that is in fact developed, managed and controlled by the IT department. Several other departments have a wide variety of IT hardware, software and employees that are often unknown, unsupported and unapproved by the IT department. This results in independent systems, processes and organizational units that are developed and supplied by the very department that brought them in.
Using unapproved software is bad, but is it really that bad?
Absolutely! Let’s imagine we are in the work environment of a fictitious company and this person is part of the financial sector: The production control system that is used by the company takes a long time to open on this employee’s computer, it is a bit complex to use and he was already used to another tool. This employee then installs this other tool, unknown to the company, and starts using it for his production control. Only in this change, the company ends up losing all the production control of that specific employee, besides the visibility of the work done by him.
Let’s further say that the software he downloaded does not have an Open Source version (Open Source and available for free use and redistribution) and he downloads an ‘alternative’ version. After several months using this unlicensed tool, the employee has forgotten where it came from and your company has an audit scheduled. During the audit, for using unlicensed software, the company will be fined and penalized for this mistake.
What if this program used by the employee connects to the Internet and does not have all the required security measures? If the unknown software has loopholes, the company can be targeted by attackers who can steal data through this vulnerability.
In another scenario, imagine the program crashes and all the important data the employee has been storing all this time is lost: IT employees will have to try to recover the lost data from the unknown software and there is a good chance that they won’t succeed.
Finally, imagine an employee who prefers to use his personal computer instead of the one offered by the company: By connecting his computer to the organization’s environment, he is exposing a breach through a device that may not have all the security measures that the company offers such as endpoints, agents, antivirus and several other software that prevent the breaches that exist in the operating system itself and/or viruses already existing in the personal machine.
As we can see, a simple action of using a software or device that has not been approved and authorized by the company can lead to a series of problems, from the lack of visibility of the work done by the employee to the loss of important data for the company. These fictitious situations were created thinking of just one employee, now imagine a real business environment, with hundreds, or thousands of employees working in the same company and using the same environment, with hundreds of unknown software for the organization on the machines of all these people?
But then how do we combat Shadow IT if we can’t see it?
There was a time when people considered that data would always be safe behind applications, which were considered to be heavily protected. However, with the continuous development of technology and digital media, this perimeter, once considered secure, is now spread out in the cloud, on our smartphones, laptops, and other multiple devices. Being secure today means keeping up with the evolution of digital media and keeping a continuous watch on applications, users, data, and cloud connectivity. And that’s where the goal of this article comes into play: The dangers arising from Shadow IT and how to ensure a secure perimeter in your organization using specialized detection and control tools, focusing on this highly targeted area by cybercriminals, but little feared by users: The cloud.
To combat Shadow IT it is necessary to implement management control routines, using specialized tools to identify software and devices hidden in the company’s system and monitor them. Through management control routines, it is possible to create more efficient communication between the organization and employees, listening to the problems the staff is experiencing with software, for example. At the same time that the organization learns from the employee which tools would do the job more efficiently, the employee also learns from the organization the problems they can bring by using software and devices beyond the company’s knowledge. This exchange of information would discourage unapproved actions and encourage the search for specialized communication channels before trying new solutions, as well as demonstrate to the organization that the employee is looking for ways to improve the work environment and make it more productive and efficient.
In addition to the management control routines, which would help teach the employee not to try possibly dangerous approaches to the organization, one should implement the use of tools to monitor this type of activity and create restrictions in the system that only allow the use of authorized tools cataloged by the company, in addition to well-defined BYOD (Bring Your Own Device) policies.
Speaking of tools… let’s get to CASB
Cloud Access Security Brokers (CASB), in short, are security applications that help organizations protect and manage their data stored in the cloud. Acting both as a filter, proxy, and firewall, CASB can detect unapproved cloud applications, such as shadow IT, as well as the ability to intercept sensitive data being transmitted or block dangerous websites and content. Another great feature of CASB is also the encryption of data traveling between the organization and the cloud.
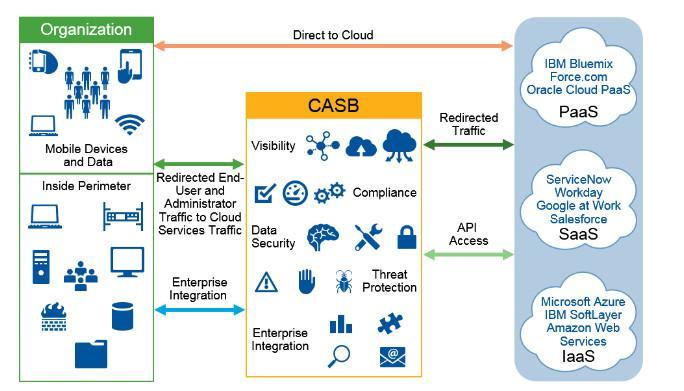
There are several CASB tools, each with a different direction depending on the cloud provider the organization uses, and there may be a need to hire different CASB tools for different providers used. An example would be a company that uses Salesforce, it will need a CASB tool that supports the Salesforce APIs as well as having functionality made to secure the traffic exchanged between the company and Salesforce, and not all CASB solutions provide this functionality. Although each CASB works with certain cloud computing vendors, all of them, without exception, follow these four principles:
1) Visibility:
CASB analyzes each and every piece of information traveling between the organization and its cloud provider. Through this analysis it is possible to discover all the systems, applications, and programs, sanctioned or not, that employees use. With this information in hand, you can help your users migrate to secure solutions.
2) Integrity:
As technology evolves, so do the problems added to it, such as new viruses and other threats, new social engineering techniques, and various activities that harm people who are more clueless about digital security. However, at the same time that criminal activities grow, laws are also created to combat them, a current example being the new Brazilian General Law for Data Protection (LGPD). And we can expect many more data laws and regulations to be created in the future. But how can you keep track of and keep up with all the data laws and regulations? CASB has functions that classify data exchanged between the organization and the cloud provider, providing the support to assist compliance programs that control this data.
3) Data security:
One of CASB’s capabilities is to detect sensitive data being trafficked, encrypt or “tokenizing” data (the act of encrypting the data and it can only be accessed with a specific key/key) and controlling access to it. With some exceptions, most CASB solutions don’t edit data, but only analyze it as it travels between the organization and the cloud. Since CASB acts as both a proxy and a firewall, access to dangerous sites and sensitive data can be blocked while it is being sent. At the same time, data that should be encrypted, but is not originally encrypted, will be encrypted by the CASB through keys that you control, using encryption algorithms of your choice (which may vary depending on the CASB being used).
4) Threat Protection:
CASB has UEBA (User Entity Behavior Analytics) capabilities that detect insider threats and compromised accounts. It blocks unauthorized access attempts and prevents security flaws caused by the user himself. These failures are often caused by carelessness, such as creating a test rule in the firewall of a cloud server and not deleting it, and another team accidentally activating it: An error like this can be exploited by malicious agents and customer data can be leaked. This may seem like a very extreme example, but one of the biggest security breach problems within cloud providers is misconfigurations by technicians, almost always through lack of attention, which can lead to very serious errors and leaks. CASB has tools that detect this type of problem within cloud providers and generate an alert for the administrator. In addition, CASB also has antivirus capabilities, i.e. if there is malware circulating in the environment, or in the cloud, it will be detected and, depending on the rules created by administrators, may be moved to quarantine for further analysis, and then be deleted from the cloud if its dangerousness is confirmed.
Depending on your cloud provider…
There are four possible categories of CASB implementation in your corporate system. And it is super important to choose the right CASB architecture for each case, since it’s the architecture that will dictate which CASB resources can be used, by which people, devices, services, and under which conditions. The four possible implementation types are:
- Log Collection: In this type of implementation, the CASB collects the event logs generated by the infrastructure present in the organization, such as firewalls and web gateways (proxies). These logs usually record the activities of users, but this method does not allow the analysis of the content of these activities.
- APIs: This CASB implementation is more oriented toward enterprise-level cloud services that offer APIs (Application Programming Interface), allowing visibility and the ability to enforce policies through CASB. The API capabilities provided by cloud services vary by their vendors. These features are: user activity audit trails, content inspection, privilege checking, sharing permissions on files and folders, and finally application security settings.
- Forward Proxy: There are two distinct ways to implement a CASB using Forward Proxy and they depend exclusively on the organization’s network settings. If the organization has a web gateway, you can configure proxy chaining to the higher CASB forward proxy. In other words, the CASB in this case will look through all proxy traffic that is sent to it. In another case, if the organization does not have a secure web gateway, but has endpoint agents installed on every machine in the company, this agent will take care of routing the cloud traffic through the proxy to the CASB.
- Reverse Proxy: In this last implementation, the CASB will act as the central proxy for all traffic passing through it from the cloud. So, unlike a conventional proxy, neither the endpoint nor the network needs to be managed. This management is handled by an IDM (Identity and Access Management) solution that will route this traffic after the authentication of the CASB in the IDM.
What we can learn from all of this
Several studies have proven that with the COVID-19 pandemic, attacks on companies aimed at exploiting vulnerabilities have increased exponentially. When looking for cases of ransomware attacks in the media, we can see successful cases against large companies on a daily basis. According to data from ISH Tecnologia, ransomware occurrences in Brazil grew 85% in the first half of 2021. The study also points out that the monthly average of attacks against companies was around 13,000 incidents, an extremely high number. Out of these cyber-attacks, 57% were identified as ransomware. Brazil leads the ranking of attempted cyber-attacks in Latin America and is in fifth place in the global ranking of data hijackings. As you can see, you can’t save money on security, because there is a lot to lose. Therefore, if your company does not have a strong security policy, invest in one, since it will only do you good.
In conclusion, it’s important to understand that CASB is just another layer of protection, more specifically for the cloud: it’s an essential and extremely important layer for your organization, especially if it has cloud applications. And although CASB includes features such as threat detection, discovery, encryption of data exchanged between the organization and the cloud, and other several functions that vary between different CASBs, we can’t fool ourselves with the false sense of security that having all these functions can give us. These functions only work for cloud applications offered by CASB, which operates only in this security niche.
You should also, if you don’t have one, even before implementing a CASB in your system, look for the complete security set: Antivirus, proxy, firewall, policies and rules for the treatment of information leakage, EDR tools for endpoint monitoring and security, implementation of DLP (Data Loss Prevention) tools, among several other measures to be taken, which are priorities.
References
BROADCOM. Endpoint Security. Available at: https://www.broadcom.com/products/cyber-security/endpoint. Acessed: 23 jul. 2021.
BUCKBEE, Michael. What is CASB? All About Cloud Access Security Brokers. [\{_}S. l.\{_}], 2020. Available at: https://www.varonis.com/blog/what-is-casb. Acessed: 29 jul. 2021.
C. Rentrop and S. Zimmermann, “Shadow IT evaluation model,” 2012 Federated Conference on Computer Science and Information Systems (FedCSIS), 2012, pp. 1023-1027. Available at: https://annals-csis.org/proceedings/2012/pliks/394.pdf. Acessed: 31 aug. 2022.
FALANDO DE SHADOW IT. Direção: Luiz Medina. Brasil: Youtube, 2021. Available at: https://www.youtube.com/watch?v=VEyI5MljB_Q. Acessed: 26 jul. 2021.
GRUPO BINÁRIO. CASB: Conheça a Definição e Funcionalidades. [\{_}S. l.\{_}], 2020. Available at: https://www.binarionet.com.br/casb-conheca-a-definicao-e-funcionalidades-deste-recurso/. Acessed: 29 jul. 2021.
HEISER, Jay et al. Technology Overview for Cloud Access Security Broker. [\{_}S. l.\{_}], 2015. Available at: https://www.gartner.com/en/documents/3057118. Acessed: 13 aug. 2021.
JULIO, Clara. Ocorrências de ransomware subiram 85% no 1º semestre do ano. [\{_}S. l.\{_}], 2021. Available at: https://backupgarantido.com.br/blog/ocorrencias-de-ransomware-subiram-85-no-1o-semestre-do-ano/. Acessed: 31 aug. 2021.
MARQUES, José Roberto. ENTENDA O QUE É GERENCIAMENTO DE ROTINA E COMO IMPLEMENTAR O CONCEITO NA SUA GESTÃO. [\{_}S. l.\{_}], 2019. Available at: https://www.ibccoaching.com.br/portal/empreendedorismo/entenda-o-que-e-gerenciamento-de-rotina-e-como-implementar-o-conceito-na-sua-gestao/. Acessed: 13 aug. 2021.
NETSKOPE. Why Netskope? Available at: https://www.netskope.com/why-netskope. Acessed: 23 jul. 2021.
SANTOS, Alfredo. Segurança em nuvem: como definir a arquitetura CASB? [\{_}S. l.\{_}], 2019. Available at: https://www.sec4u.com.br/blog-seguranca-nuvem-casb. Acessed: 29 jul. 2021.
WATSON, Kyle. Cloud App Encryption and CASB. [\{_}S. l.\{_}], 2018. Available at: https://cloudsecurityalliance.org/blog/2018/01/19/cloud-app-encryption-casb/. Acessed: 3 sep. 2021.
