Tempest researcher, Filipe Xavier, identified, at the beginning of this year, an elementary vulnerability in the parameterization of access permissions in the industrial system Rapid SCADA. If exploited, the flaw allows the system to become a bridge to access critical infrastructures, being a key element for more elaborate attacks.
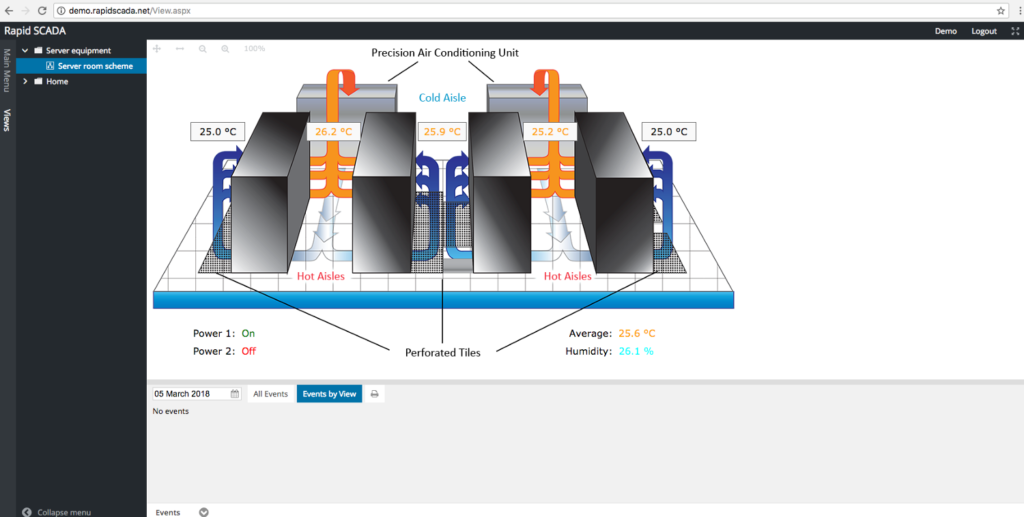
By definition, SCADA systems — Supervisory Control and Data Acquisition — are industrial software with the function of monitoring and controlling the most varied types of equipment, from air conditioning structures in factories to controllers of centrifuges in nuclear power plants.
There are many such systems, and Rapid SCADA, developed by the Russian company Rapid Software, has features similar to those of other platforms, but it is a free and open source alternative. The company charges for training and supporting services in the tool, as well as marketing additional software modules.
On Windows systems, the installation includes, in addition to Rapid SCADA, a version of SQL Compact, the .NET Framework, and IIS. The system has an administration interface in the client/server model and another one in the web format.
During the installation process, Rapid SCADA creates the C:\SCADA folder on the computer and drops all its components into it. In the documentation, the manufacturer recommends maintaining this default folder configuration in order to simplify the system configuration as a whole.
By default, when the folder is created in the operating system, full access to the administrator of the computer (and the domain) and to the System user is granted. However, access to read and execute is also granted to any user created by default in the Windows installation, as well as modification access (creation, removal, reading, and writing) to any user authenticated on the computer.
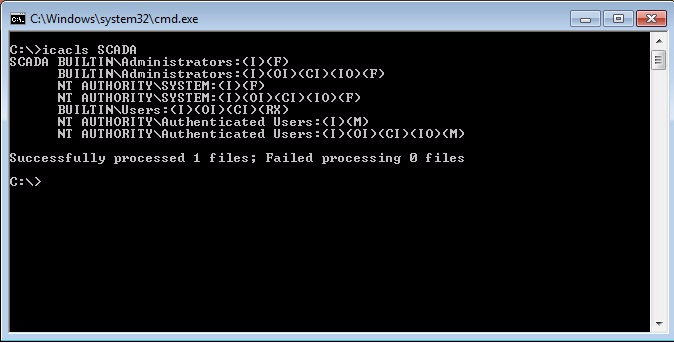
Here is the flaw found by Xavier. It is elementary, but it can cause catastrophic results in industrial environments where administrators rely on misconfigured software.
To be clearer, as permissions to the folder are configured at the installation, it is possible for any authenticated user to modify content (create, remove, read, and write) in the Rapid SCADA folder. Default operating system users, such as the IIS guest user, can also read the contents of the folder and run programs within it.
This type of configuration facilitates the execution of system sabotage attacks by removing files or more elaborate attacks based on Rapid SCADA components exchange; for example by injecting malicious components into one of two system services, to spy on environments or to create a bridge and access other networks connected to the product. The condition may be even more critical if the system administrator exposes the product’s web interface to the Internet.
Critical infrastructure environments, especially power plants, are a target of interest to terrorist groups or other political opponents. This type of environment uses SCADA systems and it is common that, when installing software, administrators maintain the default permissions to avoid unavailability in the system, especially when the system documentation does not specify whether the permissions configuration needs to be maintained or can be changed, as is the case with the Rapid SCADA documentation. In tests, it has been proven that a safer configuration, which removes the exaggeration in the access granting, does not affect the operation of the system.
Felipe Xavier informed Rapid Software about it on 9th January; and, on the 15th of that same month, it was notified by the manufacturer that the company will not focus on this flaw at the moment. The vulnerability was cataloged as CVE-2018–5313.
