By Threat Intelligence Team
Researchers at Tempest have identified a new command and control server through which fraudsters administer infected targets with a variant of HydraPOS, malware that was initially developed to steal credit and debit cards, as well as food tickets and meal ticket card data from Brazilian merchants, but which, over the years, has gained new functionalities by collecting e-commerce store access credentials and banking data.
The threat was originally described by Tempest in October 2017 and, at that time, was composed of several malware with hundreds of different versions, in addition to dozens of tools developed by HydraPOS operators and by third-party. Its infection process can be made by phishing techniques, but it also includes the search for open ports associated with remote access services, such as VNC, RDP, Radmin and SSH. Through these ports, the attacker attempts to exploit vulnerabilities or execute brute-force attacks to access the victim’s network, reach payment systems, and infect the cashier’s computer. There is also the possibility of infecting devices locally, either by stealthy and by social engineering attacks or by luring merchant’s employees.
The command and control servers identified in 2017 had an arsenal of tools, which were accumulated to meet the various conditions present in the targets. “Several versions of other artefacts have been identified, covering various distributions of legitimate use tools (such as those used for remote administration), brute-force attack mechanisms, and tools for collecting email addresses.”
Through the analysis of the server identified few weeks ago, it was possible to obtain access to the binary of the control panel that is located on the same computer that also stores the card data. Similar to what we reported in 2017, access control to the server is done by means of a user and password that are stored in plain text in the source code.
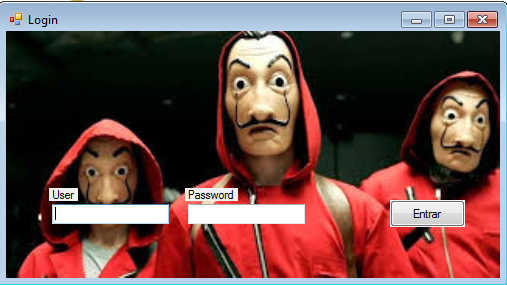
The application has some particularities which, although simple, were recently developed to facilitate the work of the fraudster, such as the segregation in the storage of data, separating the tracks that have the security code from those that do not, and maintaining a specific area for international cards.
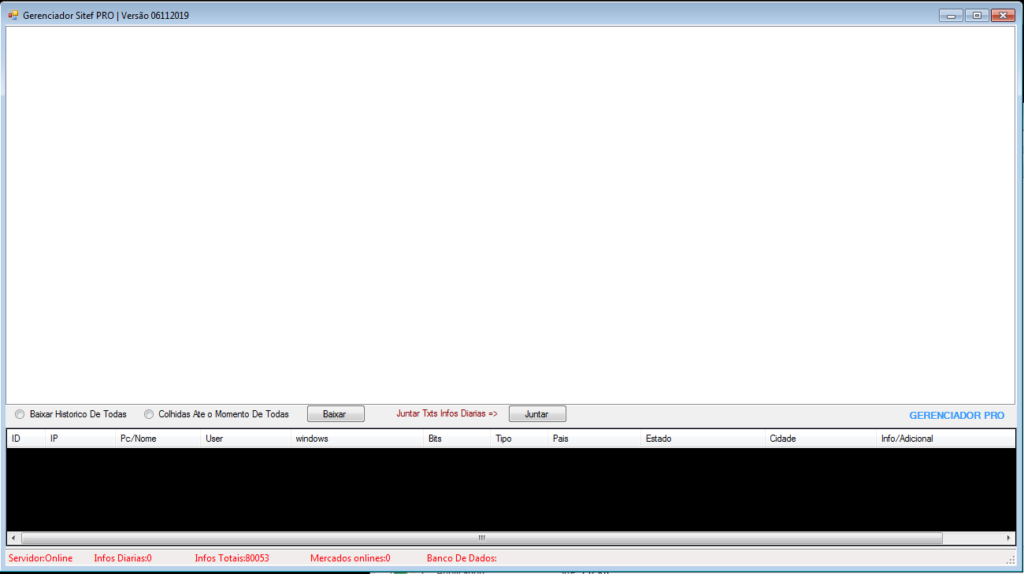
During execution, the control panel opens the 1/TCP port through which it waits from infected machines communication, which are identified by their hostname, username, and IP address. It was possible to identify, at least 65 computers infected by the malware. Among them, some have the hostname referring to merchants with a high volume of transactions, such as restaurants in airports.
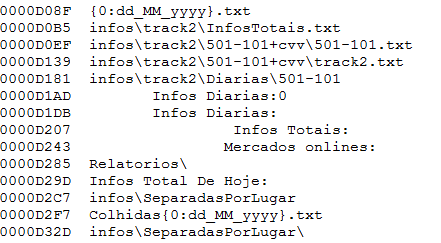
The information collected on each target is found in the root directory of the control panel and, until we close this article, there were already more than 100 thousand track data, but with thousands of new data added each day, which are separated in files whose nomenclature follows the following pattern:
IPADDRES-HOSTNAME-USER-MalwareName.txt.
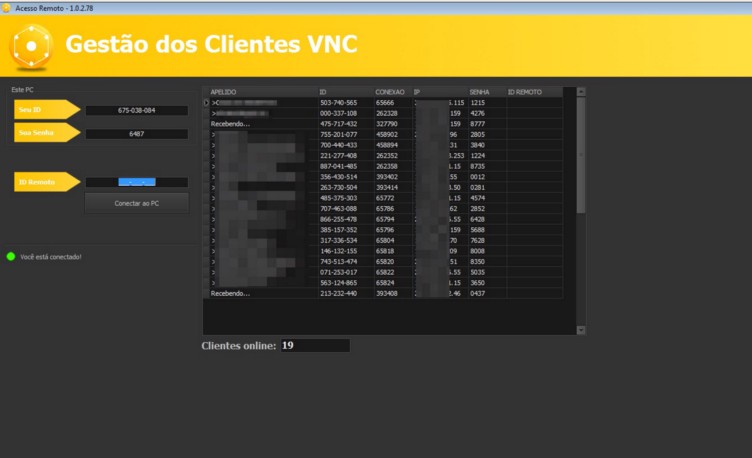
The use of a remote access tool used by fraudsters to manage a small set of targets was also identified on this server. Like a traditional RAT, fraudsters use this system to monitor what happens on the target’s screen and take control of the victim’s mouse and keyboard.
To reduce the risk of attack with HydraPOS it is important to physically protect computers in the cashier, preventing unauthorised access to USB ports or to operating system with administrative priviledges. In addition, it is recommended that essential measures for businesses of any size are implemented, such as adopting configuration standards that determine a strong authentication policy, implementing endpoint protection systems and security settings for computers and network, as well as a patch management process”.
IOCs
Filename: Gerenciador.exe
MD5: 9b3cf8b8d767bb95dfaec0547ee1ae6b
SHA1: 41ababf394ffbec19503238871905c956db31dc1
SHA256: 2b7805ce22e19d74d975adb9acee8f110dbd713fad257b6bcd3e26966cb1d0b9
SHA512: 347c06b3991fd362c4f57cee211924e725254bcb644fdd283a215e1ebf20933a7c08d16da1b76eef28a5e29562739bd6d47ae9885653a03a6ccb4d70cb616f76
