By Threat Intelligence Team
Tempest’s Threat Intelligence team recently identified a new banking trojan that targets customers of financial institutions operating in Brazil. The malware has characteristics that classify it as a Remote Access Trojan (RAT) and uses the screen overlay mode to capture the victims’ financial information.
Named as SLKRat by Tempest and as “Janeleiro”, in the survey released by ESET on April 6, the trojan is operated by the self-titled group “The Money Team”, which has supposed origin in Brazil. It’s worth mentioning that this group is recent in the scenario of cybercrime and has no apparent connections with the homonymous actor of Russian origin, whose performance is directed at the forgery of documents.
SLKRat is developed with the .NET framework and among its main features is the monitoring of active browser windows to identify accesses to Internet Banking, aiming at the overlapping of screens to capture sensitive information. The trojan is also capable of replacing Bitcoin wallet addresses copied to the Windows clipboard, these being some of the most common features found in banking trojans that affect Latin America. In the analysis conducted by our experts, about 30 financial institutions were identified on the threat target list, including national banks and fintechs.
PS: This, and future articles, that will be produced by the Threat Intelligence team will be structured based on the Cyber Kill Chain cybersecurity model developed by Lockheed Martin’s CSIRT team.
Weaponization
In the last weeks, Tempest’s detection mechanisms have identified the distribution of two versions of the SLKRat trojan. The versions differ only in the target list and in the string decryption algorithm that are necessary for communication with the command-and-control server (C2). The first version (0.0.1) uses an algorithm based on two RSA keys to encrypt and decrypt strings, while the second (0.0.4) uses the Rijndael library, which is based on the Advanced Encryption Standard (AES) algorithm.
Delivery
The threat is distributed exclusively by malicious links that are embedded in e-mail messages designed with different approaches for each version of the trojan. The first version is distributed with the theme of an overdue invoice, and the second, with the motto of vaccination against Covid-19.

Exploitation
Despite using different themes, the main objective of the campaigns is to exploit the user’s curiosity by convincing him to click on the link provided in the body of the email, in order to download and execute a malicious ZIP file containing the main payload of the threat in MSI format. Unlike other known Trojans, SLKRat does not download an additional toolkit, having all the necessary artifacts for its execution and installation within the installation file.
Installation
When executed, the MSI starts the infection process by sending a request to the address checkip.dyndns.org (legitimate service from dyn.com) to verify that the external IP address of the victim network is located in Brazil. If so, the malware communicates with the control panel to register the new infection, otherwise, the execution on the target machine is terminated. Then, the MSI file sets up persistence on the target by creating a shortcut (LNK) in the Windows Startup folder. When executed, this shortcut starts the legitimate Windows process rundll.exe, using as an argument the malicious SLKRat DLL stored among the MSI artifacts.
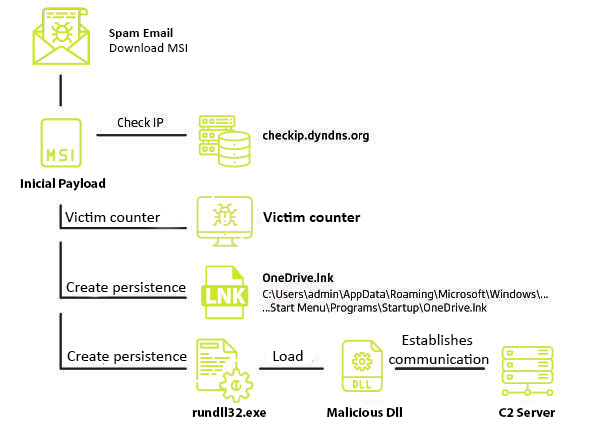
Command and Control
Similar to other Latin trojans, SLKRat abuses cloud services and hosting platforms, such as GitHub, to host the IP address used to establish encrypted communication between the infected computer and the server. Operators use a standard nomenclature, based on the SLK%d%m%y format, to name repositories and files in which connection strings are stored. In this standard mode, the term SLK is a fixed string and %d%m%y is the variable part that corresponds to day, month and year in numeric format.
Two distinct IP addresses were identified in the repositories controlled by the attackers, however, the ports used to establish the connection were changed daily.
Actions and Objectives
After configuring the persistence, the malware remains active waiting for the victim to access the Internet Banking of some financial institution in the target list. When this access is identified, a notification is sent to the control panel so that the operators of the threat can, in due time, send commands to the infected machine and display fake screens from the target institution overlapping the originals accessed by the victim. One of these commands identified by Tempest was startcapture, which makes it possible to send a screenshot of the infected machine to the C2 server.
The malware also has the ability to monitor and manipulate the data that travels on the Windows clipboard. This functionality is performed through the open-source library known as Sharpclipboard combined with a regular expression (regex) that aims to recognize addresses of bitcoin wallets. When the requirements of the regex are met, the malware replaces the found string with one of the bitcoin wallet addresses controlled by the operators.

The detection of this new trojan denotes the activity of cybercriminals, possibly Brazilians, who continue to take advantage of the Covid-19 theme to boost their malicious campaigns. As we have detailed in this article, The Money Team is a new group in the Latin cybercrime scene, and its appearance is further evidence of the new malicious groups and malware families that have been detected by Tempest in the last months.
As for SLKRat’s modus operandi, Tempest believes that operators can carry out financial transactions in the background while displaying the fake screens of financial institutions to victims, interactively requesting complementary information if necessary. This type of real-time operation has been previously detected in campaigns of other threats of the same nature.
Detection and Investigation
Network
- Communication with the address dyndns.org to check the external IP address of the infected machine.
- The exe process communicates with the legitimate address raw.githubusercontent.com to query the IP address of the C2 server. The created repositories follow the format SLK%d%m%y, for example “SLK23022021”.
Endpoint
- Creating a shortcut in the Windows Startup folder named OneDrive.lnk.
Example:
C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\OneDrive.lnk
- Creating a file in the %AppData%/Roaming/.
- The process executed by rundll.exe is used to load the malicious DLL.
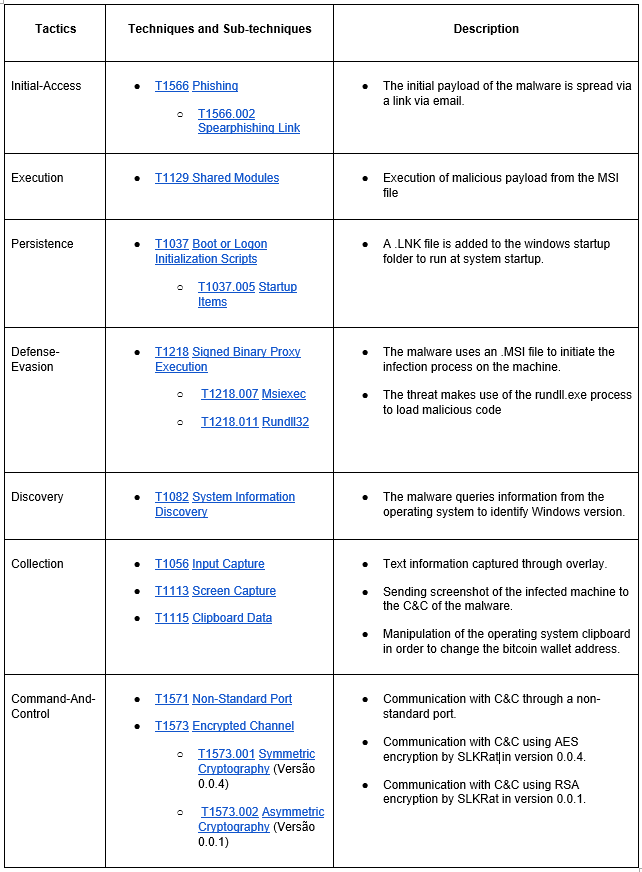
MITRE ATT&CK Techniques
Click on the technique ID for more details or click on the description for the Atomic Red Team detection test.
IOCs
SLKRat version_0.0.1(23/02/2021)
Subject
Attached is a copy of the pending invoice!
URL
https://invoicetracking[.]s3-sa-east-1[.]amazonaws[.]com/pendinginvoice[.]html
Hashs
Filename: Invoice-5934856[.]zip
MD5: e032ff312f20f3d7af68da54383e2b24
SHA1: 430687d1f8e42d9ab51baf90e63ef52f20f5dec1
SHA256: 3a48962ca6c24fccf99d30af3d545dbf490a762a7b99a75ce6cac160c2a77653
Filename: Group Consorcio-0881657[.]msi
MD5: acceae669bef71ac49dc18332eb31340
SHA1: 3a3a774fd04f151f0c0f21842e9abbbfe6f68303
SHA256: 762b4b3445080612cbf4f5d75a9f7e021c6278111a35694eade9c4c6af5072e0
SLKRat version_0.0.4 (10/03/2021)
Subject
Scheduling for COVID-19 Vaccination
Domain
regulation-scheduling[.]brazilsouth[.]cloudapp[.]azure[.]com
Hashs
Filename: nsouza-81697[.]zip
MD5: edf92ff3dc5799b66d21115432b68c22
SHA1: c48a30f66e6e9915541a9a51e72ff2280b6d1d89
SHA256: 55b88665657f9b883e93297632d806dfa6ba7ad5360d37ac07a0e5a0bcecc4c7
Filename: nsouza-81697[.]msi
MD5: 4b6934fb6e1744b04fbfaa1e7090c46f
SHA1: 455faf2a741c28ba1efce8635ac0fce935c080ff
SHA256: a13d2b12dfa4922a84b2783752d184a6850e9efe6fcea32fa3e50d04854746b0
