By Diego Patrik
According to the United States Computer Emergency Readiness Team (US-CERT), in 2020 alone, 17,447 new vulnerabilities were reported, representing a record number of published security flaws for the fourth year in a row.
With this scenario, and the lack of professionals specialized in cybersecurity, the organizations face a great challenge in finding countless vulnerabilities to be fixed. Solving this challenge is part of a vulnerability management program, part of which is deciding which ones are the most important.
Image 1: “Being the worst makes you the first.” – Sign in a hospital emergency room

Vulnerability management aims to prioritize risks
Vulnerability management involves knowing the vulnerabilities in an environment, with the intention of subsequently correcting or mitigating them to enhance security.
As per Magnusson (2020, p. 22, author’s interpretation) “Vulnerability management looks at the problem with a risk management view”. Unlike Patch Management, which aims to apply all available patches, vulnerability management is a continuous process of identifying, prioritizing, recommending, and implementing the recommendation, which involves correction or mitigation.
Image 2: Vulnerability management cycle
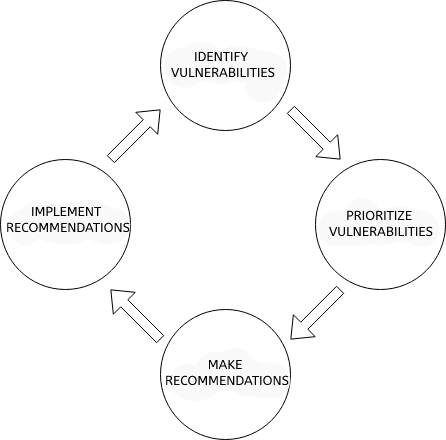
The vulnerability prioritization phase is critical to the process, since time and resources are limited and the threat environment is always changing, making it difficult to correct all the vulnerabilities discovered.
The strategy, then, becomes to prioritize the correction of vulnerabilities according to their risk to the organization. To understand the risks associated with each one, several factors can be taken into consideration, such as:
- Asset information:
Obtaining a list of all hosts is essential to a vulnerability management program. Additional details to determine which assets are most important, such as: Internet exposure, device type, and functionality; are internal company information that can help prioritize the remediation of vulnerabilities related to such assets.
- Vulnerability Information:
Using information from outside the organization may include public details of vulnerabilities, from Common Vulnerabilities and Exposures (CVE) data, public exploit information from Metasploit, and Common Vulnerability Scoring System (CVSS) points that indicate severity.
Is the traditional approach good enough?
In a traditional approach, the main focus of prioritization of the vulnerabilities to be fixed is using the severity determined by the CVSS score. The CVSS is important in order to, among other things, know what the impact could be if the vulnerability is exploited, taking into account confidentiality, integrity and availability. But, not all vulnerabilities receive a CVSS score when they are published, it’s usually assigned within two weeks, and the base score of the vast majority is never updated after that.
With the constant threat landscape, this score becomes outdated. Also, taking into account only the severity from the CVE/CVSS is like having a prescribed risk calculation, so the vulnerabilities that seem to be of low severity for all organizations, but of urgent risk for a specific organization, are not fixed for a long time.
Therefore, it’s ideal to use CVSS with a greater degree of context, in conjunction with internal information about asset criticality, the existence of public exploits, and intelligence data.
Intelligence data allows you to update priorities as the threat scenario changes and understand the risks that apply to a specific organization.
Threat Intelligence
To many people the term Threat Intelligence sounds very confusing. In order to define Threat Intelligence, we can separate the two words to make the explanation more explanatory:
- Threat: refers to the act of a person (or group of people) causing something that is only a risk to become a reality.
- Intelligence: refers to the collection of information and activities that may indicate that a risk has become a real threat.
It’s also worth mentioning that part of the activities of Threat Intelligence professionals is to collect security data from multiple logs and other data sources, such as unusual activities, malicious domains, and IP addresses. Then, these analysts are able to process and extract from this raw threat data, the intelligence information for the creation of reports that will compose the so-called Intelligence Information Sources. These sources have information about:
- Honeypots and honeynets
- Cybersecurity websites or blogs
- Social networks
- Code repositories
- Websites such as Pastebin or Ghostbin
- Dark web
- Discussion forums
As already mentioned, to understand the real risk of a vulnerability it’s necessary to have a high degree of contextualization, in an updated way. Based on these sources it’s possible to identify new vulnerabilities released well before they are published in databases such as NVD, exploit codes which aren’t yet public knowledge being shared, and reports of vulnerabilities that are being widely exploited. Having the correlation between vulnerabilities found and threats in real time saves time and saves resources.
Image 3: The biggest risks are in the vulnerabilities present in the environment and which are currently being exploited.
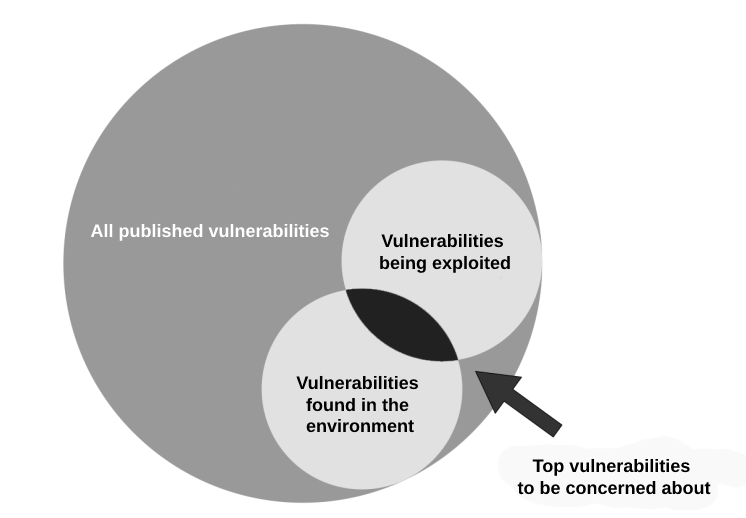
By helping to identify specific vulnerabilities that actually pose a risk to the organization and providing visibility into the likelihood of exploitation, intelligence data enables vulnerability management to target fewer high-risk CVEs, generating less demand and thus enabling the prioritization of immediate remediation of the highest priority vulnerabilities based on actual risk applied to the specific organization.
Having several possible sources of intelligence, an automated solution allows the cybersecurity team to centralize and combine the data before it is used in other security systems or accessed by analysts. Some examples of solutions that allow you to automate the process of relating vulnerability information to intelligence data for the purpose of prioritization, are:
- Qualys Threat Protection
- Tenable Predictive Prioritization
- Recorded Future Vulnerability Intelligence
CONCLUSION
Taking into account the aspects taken into account, it’s necessary to combine the organization’s internal information, details from CVEs, CVSS and external threat intelligence data to have an effective model for prioritizing vulnerabilities to be fixed in a vulnerability management program.
Having this approach, which ties together information from multiple sources, results in being able to understand the risks that apply specifically to an organization and keep up with the ever-changing threat environment. It also reduces the demand for critical patches to be applied and avoids wasting time and resources on vulnerabilities that are not important.
REFERENCES
AHLBERG, Christopher. The Security Intelligence Handbook. Third Edition. Local, 2020.
GESTÃO DE VULNERABILIDADE: como priorizar riscos. Blockbit. Available in: https://www.blockbit.com/pt/blog/gestao-de-vulnerabilidade-como-priorizar-riscos/
Accessed in: 02/09/21.
LIVSHIZ, Alex, When it comes to vulnerability triage, ditch CVSS and prioritize exploitability. Available in:
https://www.helpnetsecurity.com/2021/02/10/vulnerability-triage/
Accessed in: 02/13/21.
MAGNUSSON, Andrew. Practical Vulnerability Management – A Strategic Approach to Managing Cyber Risk. Local, 2020
SHERIDAN, Kelly. US-CERT Reports 17,447 Vulnerabilities Recorded in 2020.
Available in: https://www.darkreading.com/threat-intelligence/us-cert-reports-17447-vulnerabilities-recorded-in-2020/d/d-id/1339741
Accessed in: 02/13/21.
THE FUTURE OF VULNERABILITY MANAGEMENT IS RISK-BASED. Kenna Security. Available in: https://www.gartner.com/technology/media-products/newsletters/kenna-security/1-1XV6PUGR/gartner2.html
Accessed in: 02/04/21.
THE ROLE OF THREAT INTELLIGENCE IN VULNERABILITY MANAGEMENT. Nopsec. Available in:
https://www.nopsec.com/the-role-of-threat-intelligence-in-vulnerability-management/
Accessed in: 01/13/21.
WHAT IS PATCH MANAGEMENT? [REF-09]. Rapid7. Available in: https://www.rapid7.com/fundamentals/patch-management/
Accessed in: 02/09/21.
WHAT IS RISK-BASED VULNERABILITY MANAGEMENT? Kenna Security. Available in:
https://www.kennasecurity.com/blog/what-is-risk-based-vulnerability-management/
Accessed in: 02/04/21.
WHY THREAT INTELLIGENCE IS CENTRAL TO EFFECTIVE VULNERABILITY PRIORITIZATION. Blueliv. Available in:
https://www.blueliv.com/cyber-security-and-cyber-threat-intelligence-blog-blueliv/why-threat-intelligence-is-central-to-effective-vulnerability-prioritization/
Accessed in: 01/13/21.
