As a result of research efforts and content generation, which are also part of the activities of the AllowMe Digital Engineering team (a Tempest company that helps organizations protect the digital identities of their legitimate customers through a complete fraud prevention platform), an e-book was developed that shows the panorama of the Brazilian market in the e-commerce environment.
In this study, Gabriel Glisson, Information Security Analyst at AllowMe, brings the main types of fraud that occur in e-commerce and explains how to apply the so-called Fraud Prevention Triad – Detection, Learning, Prevention – so important to define strategies that will be used in the business world.
A brief summary about e-commerce in Brazil
In the early 90s, with the popularization of the Internet at full speed in the USA, the first e-commerce (electronic commerce) companies in the world emerged. Two of them, Amazon and eBay, went further and proposed a new experience uniting the physical and digital worlds. These companies aim to put the consumer in the spotlight, no longer requiring him to go to a physical store to purchase a product, i. e., the merchandise, through e-commerce, will be sent to the customer, thus spreading a new shopping experience for the user.
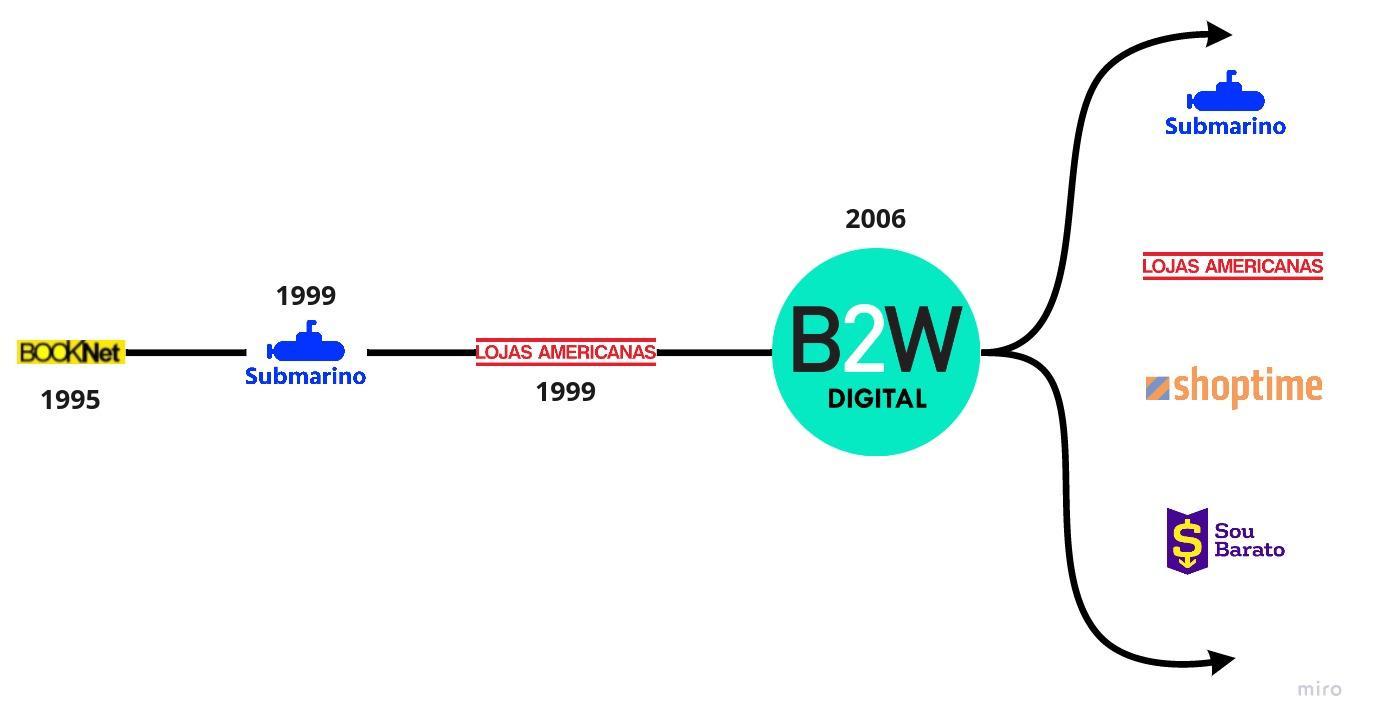
In Brazil, one of the first reports of e-commerce (electronic commerce) was Booknet. Founded by Jack London in 1995, its main activity was the sale of books, with guaranteed delivery within 72 hours and the possibility of payment on delivery. In 1999 it was acquired by Submarino, which today is part of the B2W (Business To World) group, leader in the Brazilian market share.
Getting down to numbers
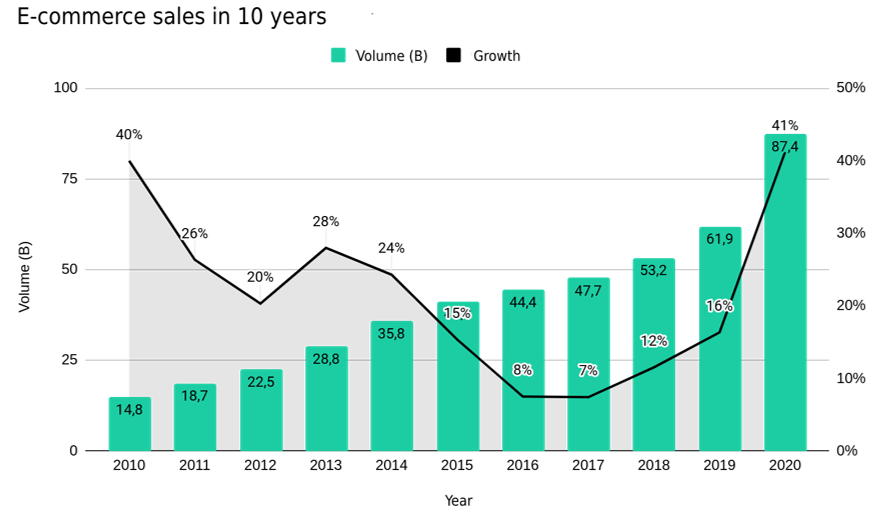
The pandemic stimulated the creation of new habits, mainly due to the social distance and the need for Home Office and EAD. Thus, the need to adapt the living environment to an environment that made it possible to perform these tasks, generated a high demand for utensils, examples: tables, chairs, and computers. However, the impossibility of going to a physical store helped e-commerce (electronic commerce) in Brazil to reach the historic mark of more than R$ 87 billion in sales in 2020. This represents a growth of more than 41% compared to 2019 and 490% compared to 2010.
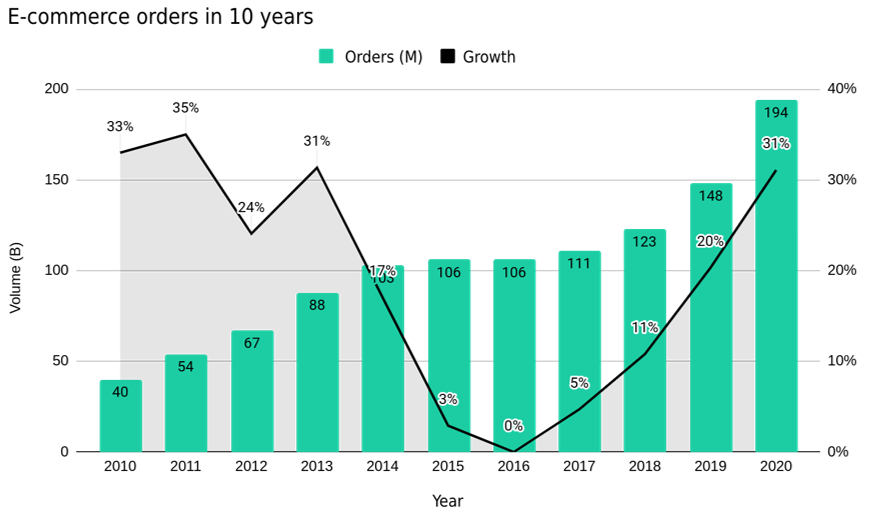
The increase in orders was precisely one of the main reasons for the rise. In 2020 alone there were 194 million orders placed. A growth of 31% compared to 2019 and 385% compared to 2010.
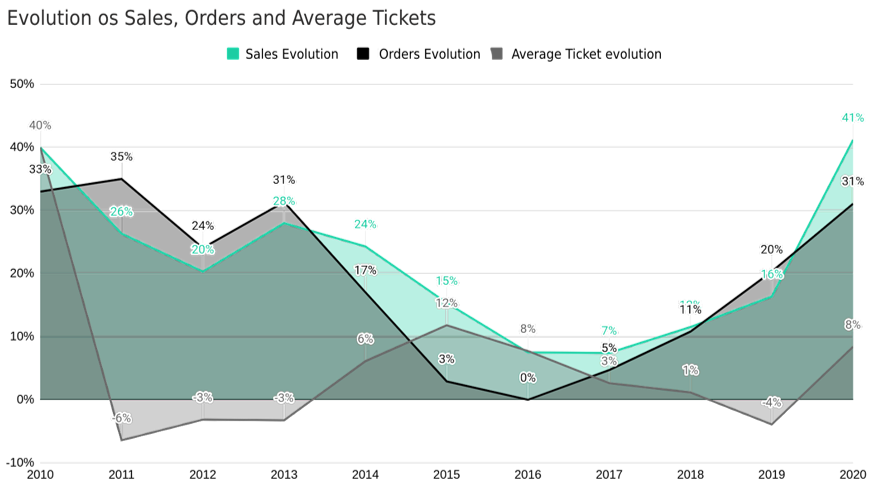
Not only the orders helped this growth, but the average ticket also increased compared to previous years and reached the record of $ 452.00.
It can be seen that the upward behavior of these two variables is unprecedented in the last 10 years:
The segments with the highest growth in revenues are:
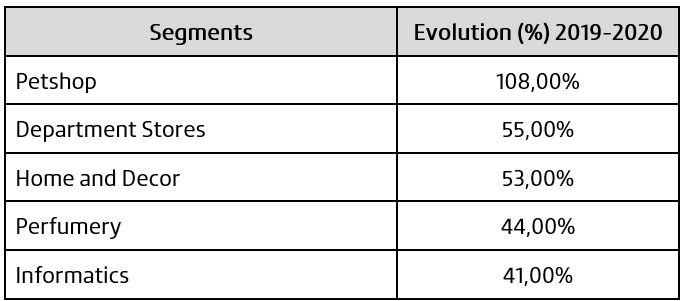
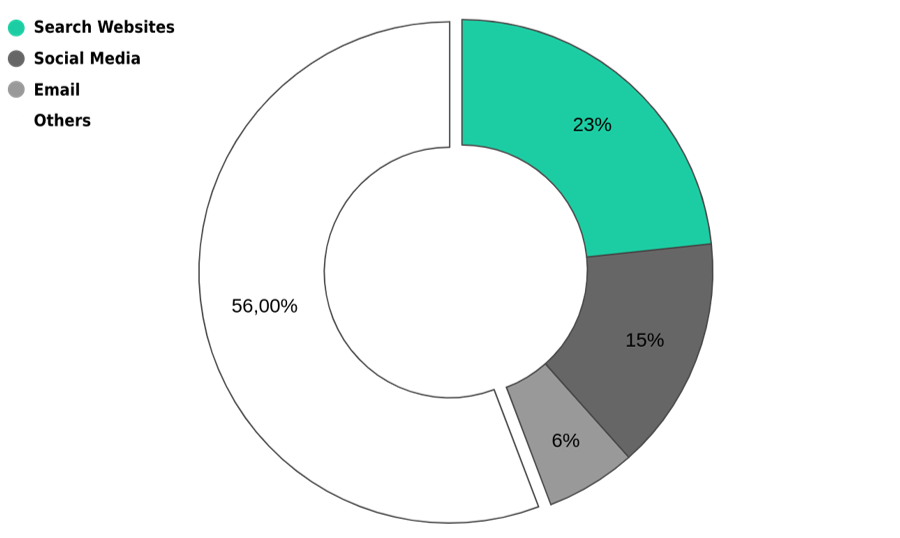
Knowing how the user gets to the segment stores is an important step to plan the amount of effort needed to avoid “fake” support accounts, in which fraudsters are creating accounts pretending to be employees of the companies. This is an example of fraud that is very active in the market and is creating a lot of victims. Possibly, one of the reasons for the “success” of this type of fraud is the decentralization of service channels. Today, about 15% of the customers use social networks to reach the stores, and 6% use e-mail mkt (the use of e-mail as a direct marketing tool). If we do the sum between social network + e-mail mkt we reach 21%, very close to the search engine, which is around 23%. This theme will be addressed later on.
Type of authors and their goals
The numbers speak for themselves, sales success is already a reality, the trend is to maintain this positive exponential growth. Unfortunately, fraud attempts are usually directly proportional to this development. I emphasize that I am talking about attempts, since their effectiveness depends on each one of us, both people who work to prevent and users of e-commerces (electronic commerce), and this last group includes all of us.
Making a parallel with the present times, the population has been asked to take several actions in order to avoid an over demand for ICU beds in hospitals. Here are some examples: social isolation, hand washing, cleaning objects, and the use of masks, among others. This is all called Prevention. These are simple tasks, but they have proven to be very effective in fighting COVID-19.
Taking this example into account, it’s extremely important to communicate and educate users, providing information on how to prevent fraud, and having a direct service channel for this type of issue. We cannot be afraid to “scare” users with this, on the contrary, users feel safer when a platform cares about their security. The lack of action may be considered as omission and “tarnish” the image of the platform, worse damage than just a chargeback.
But after all, what is fraud? To put it literally, fraud is any cunning, deceptive act, in bad faith, with the intent to injure or deceive others. It can also be summarized as follows: obtaining an advantage over a victim, and may use various artifacts to achieve success.
Below we list the main types of fraud that occur in e-commerce:
-
Card fraud
One of the most common and oldest scams. Credit card credentials are bought on the Deep Web (an area of the Internet that has little regulation) and the products are sent to freight forwarders, making it difficult to identify the buyer of the product in question.
In some cases, Internet proxies are used to mask the IP internationally and hide the origin of this type of action. A proxy is a server that acts as an intermediary between customers and other servers and is useful for the fraudster to maintain his anonymity.
-
Account takeover (ATO)
In this case, the scam occurs when fraudsters get hold of a legitimate customer’s login credentials and take advantage of stored credit cards to make purchases. Usually, registration data is changed, soon after the fraudster successfully logs in, either by changing the phone number, in order to avoid alarming the account owner, or the delivery address of the products.
-
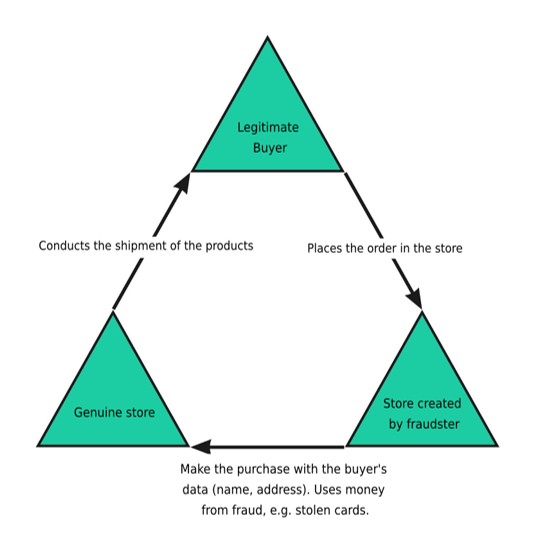
Figure 7: Triangulation mode fraud | author source Triangulation
The action involves three parties: the fraudster, the unsuspecting legitimate buyer, and the legitimate store. An online store is set up by the fraudster on a legitimate platform offering products in high demand at extremely low prices. The store collects payment for the items it sells.
The fraudulent shopkeeper uses stolen card data and names collected from orders in his “real” store to buy products from the legitimate store and send them to customers.
-
Mallory
Mallory, a character often used in cryptography explanations, represents an active attacker in a communication. He can and wants to actively intervene in the communication to forge messages or alter data.
In this method, fraudsters create orders in which the billing and shipping correspond to the address linked to the credit card. The goal is to intercept the package in one of the following ways: by contacting the sender to redirect the package to an address where they can receive the fraudulent assets, or there are cases where the fraudster lives near the billing address of the cardholder. He then waits for the delivery and offers to sign for the package because the owner is not available.
-
Identity impersonation
Fraudsters assume the identity of someone else, then create credit cards in the victim’s name and make the purchases. Even though this may seem more difficult to occur, it’s actually a modality that has been growing a lot, following the constant waves of data leaks.
-
Card test
A scam that tests information acquired, via the deep web, from a credit card. Fraudsters give preference to sites that reveal a different answer for each type of decline. For example, when a card is declined due to an incorrect expiration date, a different answer is provided. In this way, fraudsters know that they only need to find the expiration date. This is usually done in a more automated way, and transaction attempts happen quickly and with a low value, as the focus here is on validating the card and not receiving the product. It can occur in conjunction with account takeover, using accounts that are already “established” on the platforms, so as not to draw suspicion.
-
Self fraud
Very recurrent on platforms. In self fraud an online buyer makes a purchase and, in a short time, issues a chargeback claiming that his credit card was stolen. The return of the money usually occurs after the items have already been delivered.
-
Family fraud
In this case the fraudster can be a son, wife, cousin or someone in the family. It usually occurs when the victim leaves the cards in an easily accessible place. The fraudster, without the victim realizing it, takes a picture of it so that he or she can use it for future purchases without the victim’s consent.
-
Account Enumeration
This one is quite similar to the card test and the ATO, only this time the “inputs” acquired are the accounts (user + password). The goal of this type of fraud is to use the acquired/leaked data to locate accounts on other platforms, targeting users who reuse passwords. The fraudsters, by automated means, begin to perform login attempts on several platforms, tabulating the positive and negative returns, and may market or use them.
-
Symmetry
The fraudsters create stores on the platforms and advertise products that they do not own. After that, they create buyer registrations and in possession of stolen cards they start shopping in their stores. Since they do the whole procedure of “sending” the product and receiving it, they end up collecting almost the entire value of these non-existent products, paying only the platform fees, making money laundering easier.
-
Disposable registration
Fraudsters register non-existent people, taking advantage of the lack of onboarding verification. With a registration made, they can practice several types of fraud already mentioned above, for instance: they can use this registration in the card test (6), Symmetry (10), Mallory (4), Card fraud (1).
-
Fake proof of payment
The fraudster places the order on the site, doesn’t pay, contacts the seller and informs that he has already made the payment and attaches a fake proof of payment to the conversation. Parallel to this, the seller receives an e-mail, also fake and very similar to the e-commerce layout, informing that the payment of order X was successfully completed and that they should send the product to the buyer.
Triad of Fraud Prevention
Have you ever heard the phrase “there is no fraud in my e-commerce” or even “my business is too small, fraudsters are interested in the “big fish”? Unfortunately, these are statements that can lead to a huge loss. As we’ve already seen, there are several types of fraud. So, whenever possible, we should ask ourselves: Are we really not being defrauded, or are we looking properly?
Detection is a fundamental part of the risk mitigation process; it’s from this stage that it will be possible to identify the types of perpetrators and the vulnerabilities present in your platform.
Learning will be essential to record the behavior of fraudsters and understand their modus operandi, thus facilitating detection and providing inputs for prevention. Understanding your user profile is fundamental to make life easier for the good user and more difficult for the bad user (fraudster), improving the experience and increasing security. This is extremely important to avoid friction.
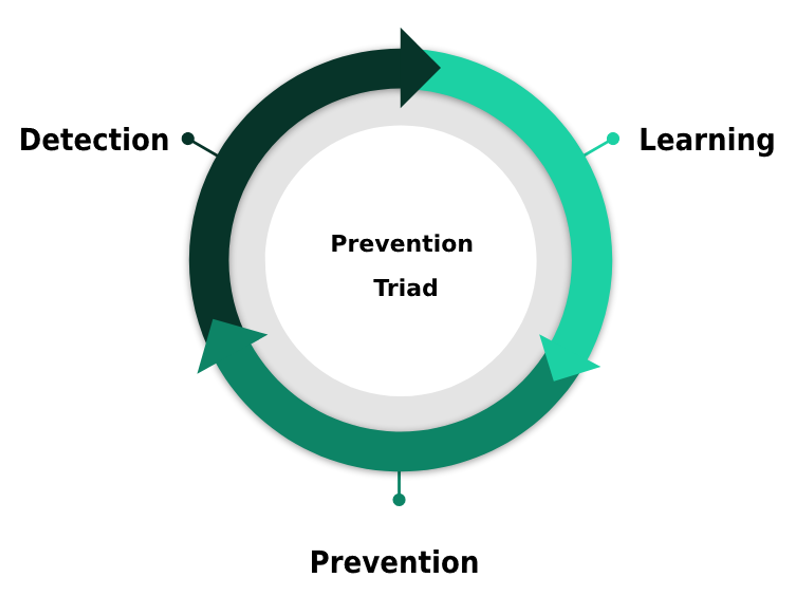
The image on the side illustrates how the fraud prevention triad works.
After detecting the threats and learning from it, it’s time for prevention. This is when the strategies that will be used to minimize the impacts and make the fraudsters’ action as difficult as possible will be defined.
Therefore, looking at the anomalous behaviors (detection), recording them (learning) and starting to define the strategies that will be used to combat the attack vectors, is a great way to start to get a good result in the prevention process.
Do you want to know how to apply the fraud prevention triad to mitigate these 12 profiles? Click here to download the complete E-book.
https://conteudo.allowme.cloud/e-book_fraudes-nos-e-commerces-visao-brasil
References
EBIT | Nielsen. [S. l.], 30 nov. 2022. Available at: www.ebit.com.br. Acessed: 30 nov. 2022.
KONDUTO | BoaVista. [S. l.], 30 nov. 2022. Available at: blog.konduto.com.br. Acessed: 30 nov. 2022.
