In a routine analysis, Tempest’s Threat Intelligence team found a platform that sells artifacts for phishing attacks and, after investigation, uncovered the operation of a Brazilian fraud campaign.
Known as Phishing-as-a-Service (PHaaS), this activity relies on platforms that sell fake e-commerce (fake stores) ready for use. Fake stores are websites that have a similar design and similar URLs as large e-commerce retailers. The creators of these artifacts usually copy screens from well-known e-commerces, however, behind these copies, the platform is the same.
This means that the infrastructure found by the researchers has run several fake stores with the purpose of collecting victims’ personal data and profiting from the payment of “boletos” — a kind of paper bill that operates only in Brazil which is based on documents containing a bar code and a numerical code in a format that is recognized by all Brazilian banks.
Frauds related to the use of fake stores are not new in Brazil, but the point that attracted researchers’ attention in this specific operation was that the platform offers resources for fraudster’s communication with victims and that this mechanism was used until the moment that the boleto was paid.
Two-Stage Attack
In this type of operation, once the platform is activated, the fraudsters advertise the fake stores in several digital channels (Phishing e-mails, sponsored ads, social networking posts, etc.) in order to persuade the victim to buy products — usually offered at a value far below the common price. The profit is obtained when the victim pays for the product, which will never be delivered, via boleto.
One of the analyzed fake stores is similar to a well-known Brazilian e-commerce; on it, a smartphone that costs 1,189 Brazilian Reais is offered for 499.
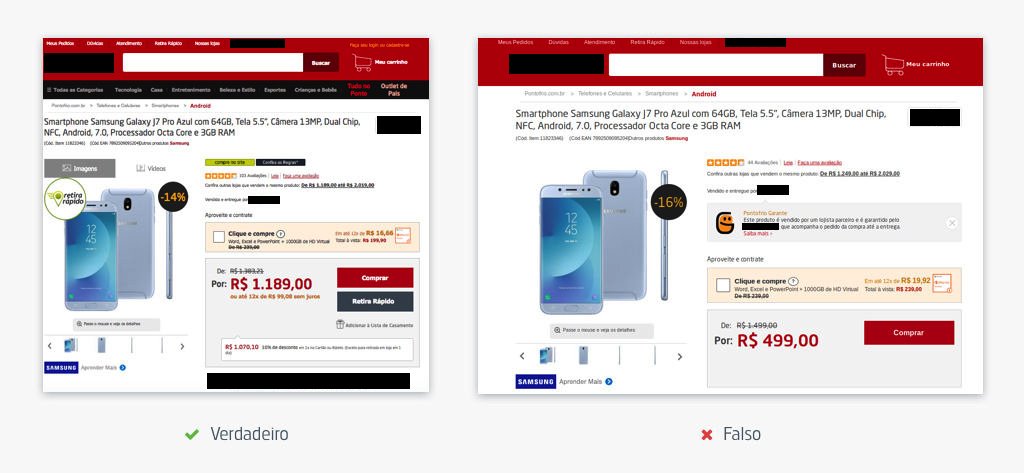
The operation identified by Tempest has a similar behavior as that of a traditional fake store; however, in this case, the fraudsters add another stage to the scam, with a “customer service” sending messages to the victim until the boletos is paid. The communication between fraudsters and victims is made by WhatsApp and involves messages such as “successful purchase” and “order booked”, as well as alerts in case the victim does not pay the boleto.
Researchers simulated a purchase and noted that the buyer’s signup screen requires a phone number associated with a WhatsApp account, which will then be used as the main communication channel between victims and the fake call center.
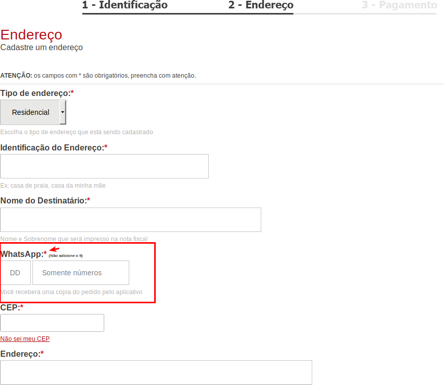
During the payment process, the site allows users to choose a credit card as a payment method and even offers the option to enter the payment card data, however, in this campaign, fraudsters are interested in payments via boletos because it is a fast way for scam monetization, so the card data is sold or used in other frauds. To encourage the victim to use the boletos as a payment method, fraudsters also use WhatsApp, as shown in the image below.

At the end of the “purchase”, the victim is redirected to a screen that informs the order number and the boleto payment code. Confirmation of purchase and payment information are also sent by WhatsApp.
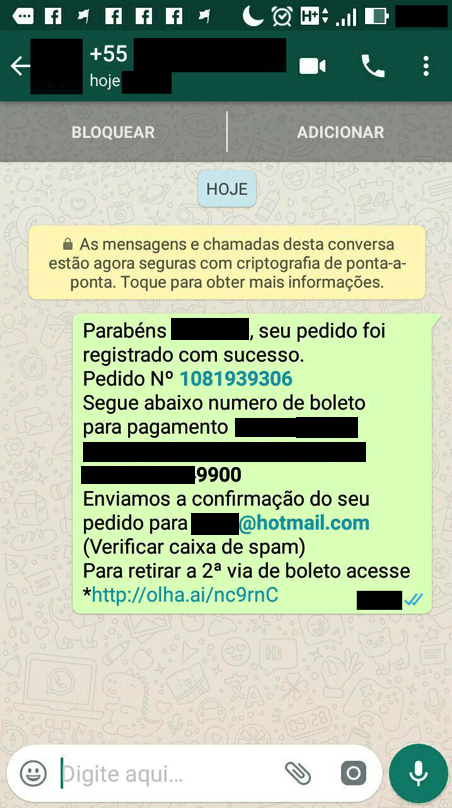
In addition to the confirmation message, the fraudsters send alerts informing the victim that the payment was not received.

To complete the service, after the payment of the boletos, the fraudsters send a confirmation message.

The PHaaS management panel
By deepening the investigation, it was possible to interact with the administrative interface of PHaaS that used the http://aquisempretemoferta[.]com domain. There were several options on the home screen, such as “Gerenciar Boletos” (Manage boletos), “Produtos” (Products), “Tools”, among others. This screen also brings the option used to interact with the victims via Whatsapp.
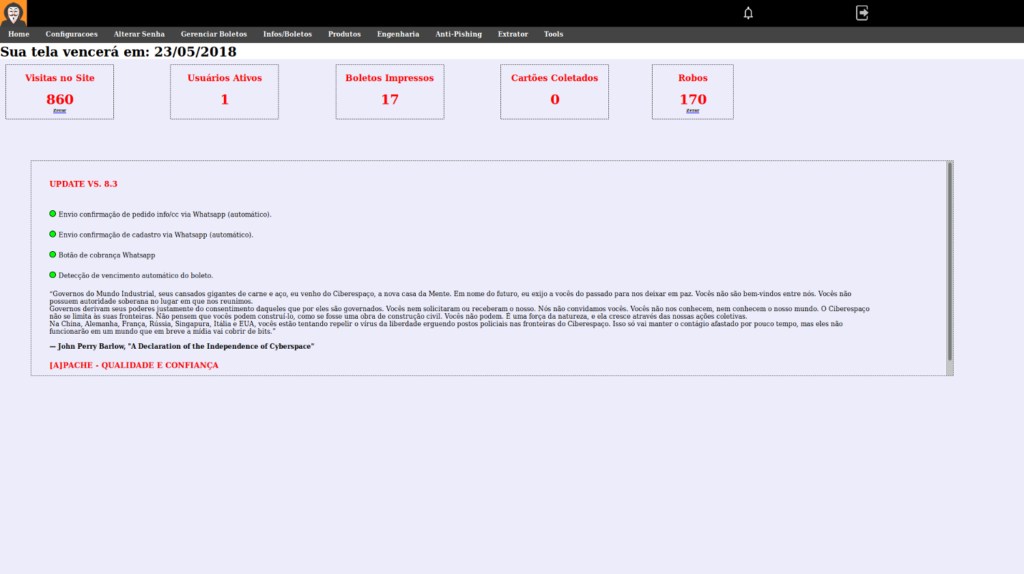
In the “boletos” menu it is possible to register boletos for each product.
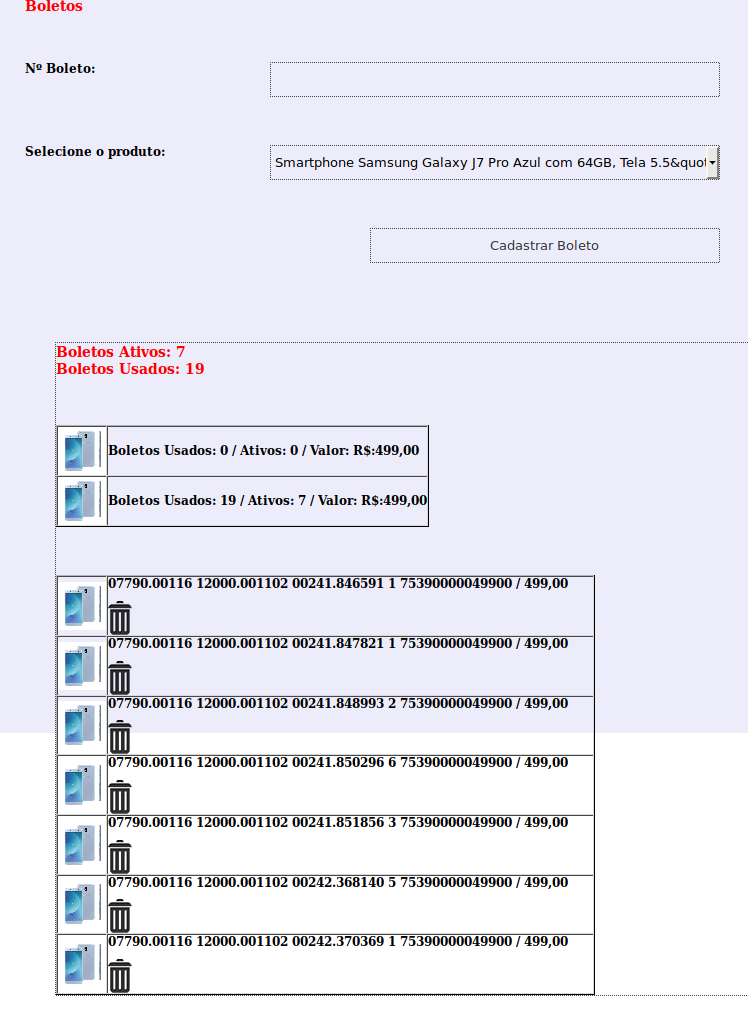
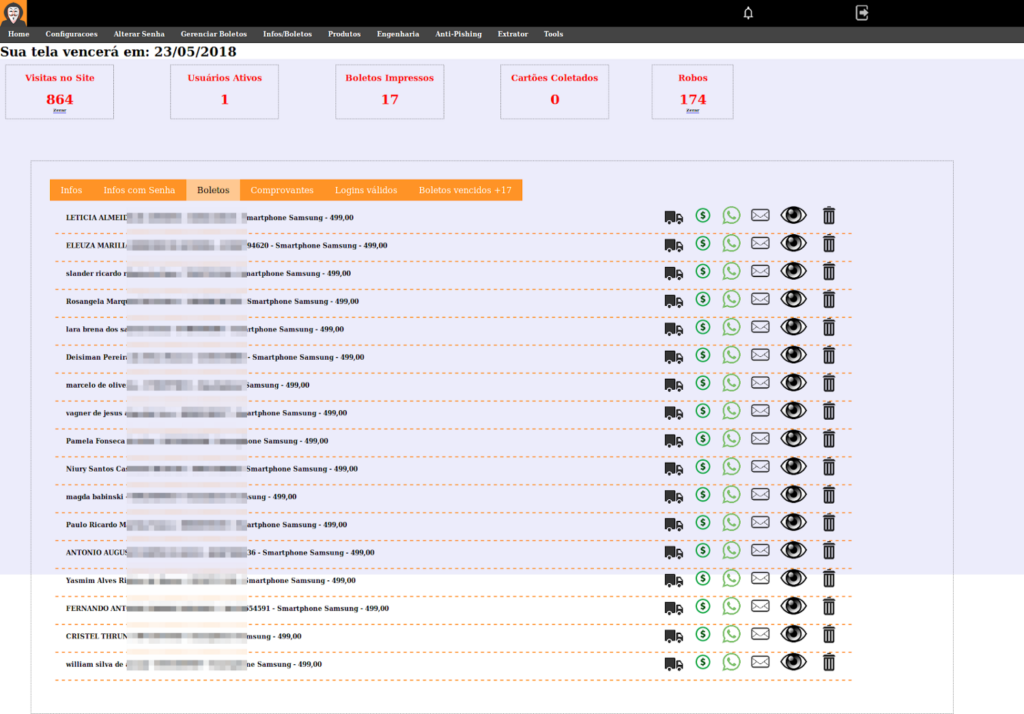
In the “Infos / Boletos” menu, it is possible to see all victims who submitted their data to the fake store. It is through this screen that the fraudsters send all messages.
Fraudster Support Services
At the time of the research there was a fraudster support service operating in the domain “http://protecaodeclientes[.]com”, which validated its clients by means of a serial number that the fraudsters received when subscribing to the service. Upon being validated, the fraudster has access to several tools that were available at the following addresses:
● http://protecaodeclientes[.]com/ferramentas/Geradores[.]rar
● http://protecaodeclientes[.]com/ferramentas/MudaData[.]rar
● http://protecaodeclientes[.]com/ferramentas/SpamMail[.]rar
● http://protecaodeclientes[.]com/ferramentas/Mac[.]rar
Besides these features, this service also provided the web interfaces of the fake stores. In one of its directories (\download), it was possible to find one of the stores in a zip file whose name is the MD5 hash value of the store’s name. Following this logic, the researchers found more files linked to renowned Brazilian e-commerces.
The service also provided data of money mules to be used in frauds. This information was available at: http://protecaodeclientes[.]com/account.
Protection against PHaaS
The use of social media as a channel of customer service is an already established reality in companies of the most varied sizes. It meets a growing demand for speed in communicating and solving problems between consumers and businesses. However, where there are communication channels — especially those where it is difficult to confirm the identity of the parties — there are opportunities for fraudsters.
It is always important for consumers to be suspicious of prices far below the market, since criminals abuse people who are thrilled with unusual offers. A good measure is to communicate with the store through other channels to check if the offer is valid. It is also always important to carefully check the address of websites where any financial transaction will take place or where sensitive information will be sent. Fraudsters commonly link copies of the original pages to addresses that are slightly similar to the original one, in an attempt to deceive inattentive victims.
In addition, it is worth it to suspect beforehand any customer service contacts via instant messaging if the e-commerce does not mention this practice on its website.
For retailers, it is important to evaluate threat intelligence services, which analyze threats on several electronic channels and can act as a differential in fraud prevention. Another relevant measure is training employees against phishing attacks. They can become propagators of best practices among their social circles and this also reverts in a measure against fraud.
IoCs
http://aquisempretemoferta[.]com
