Por Cleiton Pinheiro e Leonardo Carvalho
Criminals are using web advertising features present on social network sites and search engines to create targeted low cost phishing campaigns against specific targets. The discovery is the result of research being conducted at El Pescador since 2016.
Web Advertising, also known as online advertising is a “form of marketing that uses the internet to deliver marketing campaigns to consumers.” It is a powerful resource for its relatively low cost (when compared to other traditional marketing techniques) and for allowing market segmentation in a reasonably simple way. Attentive to these characteristics, groups of fraudsters saw an opportunity to disseminate their malware on a large scale, delivering them through campaigns targeted at interests, age, countries, and other demographics.
Use of Facebook’s advertisement tool in phishing campaigns
Last August we detected a targeted attack using Facebook’s advertisement tool. The attack is distinguished by the sophisticated combination of techniques used, among which are typosquatting, page creation, creation of advertising campaigns and filtering of targets by interest.
The attack began with the creation of two fake pages simulating the fanpages of two Brazilian media outlets — the Folha de S. Paulo and O Globo newspapers.
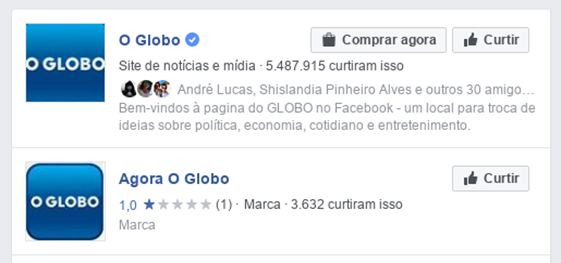
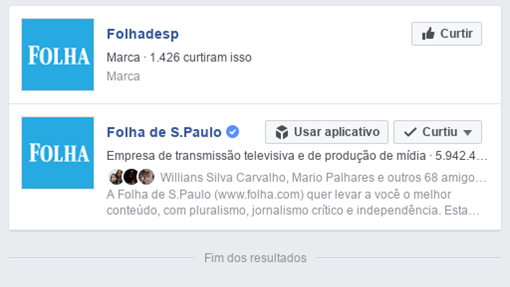
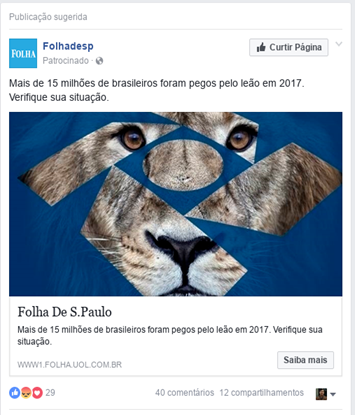
After creating the pages, the attacker worked out the posts that would be used in the campaigns. The texts imply that the reader will find information about income tax inspection.

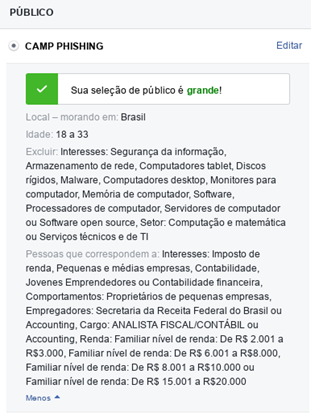
The agent went on to create the campaign. In it, filters were used to reach targets with specific interests in order to select the target audience — in the case found the terms “Receita Federal” (IRS), “Imposto de Renda” (Income Tax), “Declaração Imposto” (Tax Declaration) and “Malha Fina” (Income Tax Verification) were used. Figures 4 and 5 show how Facebook’s campaign creation tool allows not only to accuretely target specific audiences, but also to exclude from the campaign profiles that would be better able to detect them, such as people with an interest in information security and IT services.
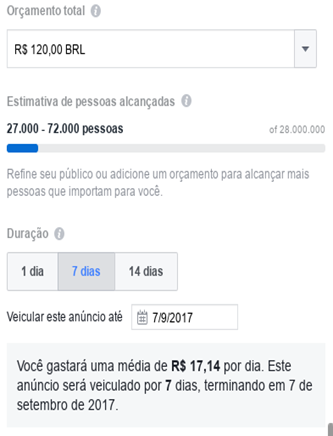
It should also be noted that, unlike phishing campaigns that use e-mail, the technique of advertising depends on a much lower investment — in the example, the cost of the campaign was just above R$ 17 per day (approximately £4, or US$ 5.3). In addition, the attacker will not be affected by anti-spam tools and can freely change the URL of infection, even during the spread of the campaign.
Infection
According to the study, the sponsored links contained shortened URLs in services such as bit.ly and goo.gl. After clicking the link the victim is directed to a page which, in turn, redirects to a Google Drive URL, from which a compressed (.zip) malicious file is downloaded; the malware is installed after the victim extracts and executes the file — in 2016 we published an article in the El Pescador blog denouncing the use of Facebook servers in phishing campaigns. We estimate that in this case, the use of Google’s servers (Google Drive) happened for the same reasons: reduce the possibility of detection by firewalls and anti-virus programs and further reduce attack costs.
The malware found is a .vbs extension file. Malwares that use this extension have as main characteristic the attempt of establishing a reverse connection with command and control (C & C) servers. Once connected to the infected computer, the criminal is able to perform operations such as privilege escalation, software scanning and installed applications, and scanning of connected devices such as pendrives — which can be infected in order to spread the malware on other computers. But it was found that the attacker does not perform these functions immediately after installation, preferring to maintain a persistent connection.
Campaigns using Google AdWords have also been identified. Other networks can be used
The study also identified the use of AdWords campaigns designed for the same purpose and using similar techniques.
AdWords is an advertising service that represents Google’s primary revenue stream — in 2011 it was responsible for 96% of the nearly $ 38 billion that the company earned. Through the service, using keywords and public filters, companies can make their products or services appear prominently in search engines or any partner site of the service.
Like happens on Facebook, criminals are using the service as a filter to deliver malware to specific audiences.
Although it has not yet been verified, the use of paid campaigns services of other social networks for the dissemination of phishing is not ruled out.
Recomendations
According to eMarketer Inc.’s Worldwide Social Network Users survey, more than 2.4 billion people already use social networks around the world. By 2017, a third of the world’s population will log in at least once a month on any of the existing social networks. The numbers attest to the relevance of the study, and the importance of taking some care.
1. Beware of sponsored links on social networks as well as on e-mails and search sites, especially those that use URL shortcuts
2. Be wary of very advantageous promotions or pages you’ve never liked that are appearing on your timeline
3. Do not download or open files from unknown sources
How to report suspicious pages on Facebook
1. Access the page you want to report
2. Click below the cover page photo
3. Select Report Page
4. Select the option that best describes the problem and follow the on-screen instructions.
5. If you can not access the page you want to report, consider asking a friend to report it.
How to report a post on Facebook
1. Click the top right of the publication
2. Click Report post or Report photo
3. Select the option that best describes the problem and follow the on-screen instructions.
Learn more: https://www.facebook.com/help/181495968648557/
