. . .
Story by Maria Carolina, originaly published in December 2016 on the previous version of the Tempest Blog
Tempest Security Intelligence has created a unique methodology for running large-scale cyber war games exercises, which we call CYBERDRILL TM.
Tempest’s war games methodology incorporates best practices from international sources such as ENISA and MITRE, as well as our own proprietary experience in running scenario-driven exercises. Tempest has accumulated extensive experience in using the CYBERDRILL methodology in running cyber exercises for companies in the financial services and media sector, as well as major international events like the Rio 2016 Olympics.
This blog post is the first in a series on cyber war games, and will provide an overview of what cyber exercises are and how they work.
Cyber exercises Overview
Cyber exercises, also known as cyber war games, are scenario-based training exercises that test the preparedness of an organization’s cyber security processes, technologies and procedures, and the overall ability to cope with and recover from a hostile cyber attack. The results and lessons allow organizations to identify weaknesses, improve their security measures and level of preparedness.
The case for cyber exercises
In recent years, cyber exercises are being increasingly used by forward-looking organizations at the corporate, regional and national levels as an effective measure to improve overall security posture and increase resiliency. They serve as realistic training exercises for the teams responsible for providing security, bringing an effective and realistic assessment of security detection and response processes, procedures, decision-making and communications during a critical security incident or crisis.
Some of the major drivers behind the effectiveness of “war gaming” an organization’s security posture include:
Communication and articulation
Critical cyber security events can have deep business impacts, which require coordination, communication and decision-making between technical and executive teams. Depending on the nature of the event, this extends to articulatio n with other institutions like police, media, etc. Cyber exercises are an effective way to simulate realistic scenarios, test and rehearse reactions, and align priorities between different teams in a controlled environment. All of this increases the effectiveness of the reaction when a critical incident happens for real.
Threat-based simulation
There is now ample information on the motivations, goals and technical capabilities of cyber threats. Cyber exercises use this type of threat intelligence to simulate realistic scenarios taking into account the way the threat operates, guaranteeing the relevance and applicability of the exercise. This is critical in modern IT security environments, which are complex and multi-faceted, composed by different types of security tools. In many cases individual testing of each security control provides only a partial and optimistic view; once a red team performs a realistic threat-based penetration, weaknesses in how security tools function together, and in how they integrate and correlate information become apparent.
Team readiness and rehearsal
When an organization is hit with a critical cyber security event, time is of the utmost importance. The only way to ensure a timely response and containment is to have a heavily rehearsed set of response procedures, along with a security team that has been trained to act under stress before. Cyber exercises provide that opportunity in a realistic and controlled environment, ensuring that any problems with response procedures get identified and fixed before being actually used in a real event.
Cyber exercises at the country and regional level are being regularly executed by many high-profile organizations, including the following:
• NATO Cooperative Cyber Defence Centre of Excellence — Locked Shields Exercise: https://ccdcoe.org/event/cyber-defence-exercises.html
• ENISA Cyber Europe Exercise: https://www.enisa.europa.eu/activities/Resilience-and-CIIP/cyber-crisis-cooperation/cce/cyber-europe
• US and EU joint Cyber Atlantic Exercise: https://www.enisa.europa.eu/activities/Resilience-and-CIIP/cyber-crisis-cooperation/cce/cyber-atlantic
• Poland Cyber-EXE Polska: https://www.cyberexepolska.pl/
How cyber exercises work
There is now a wealth of information and practical experience on the most effective ways to perform cyber exercises . In general, three major areas need attention: (a) the objectives and scenarios to be tested; (b) the choice of type of cyber exercise; and (c) the composition of the teams which will participate in the exercise.
Objectives and scenarios
The starting point for a cyber exercise is to have clear view of the objectives of the exercise: what needs to be tested, what needs to be trained.
Common objectives for cyber exercises may include:
• Test effectiveness of incident response processes and procedures;
• Test effectiveness of communication with partners and authorities;
• Test decision-making chain during crisis;
• Evaluate reactivity and behavior of key actors under pressure;
• Test reaction to public events and media handling;
• Evaluate alert trigging and information exchange procedures.
The next step after choosing the major objectives for an exercise is to build an exercise scenario which will allow those objectives to be met. The scenario should describe the situation that the teams participating will work with. It is key that the scenario is realistic enough that the team will engage effectively with the exercise.
Common scenarios for cyber exercises, could include:
• Hacktivist attack with information theft and publication of sensitive email and documents on the Internet;
• Denial of service on corporate networks and disruption of internet-facing services;
• Compromise and leakage of sensitive data from corporate databases;
• Compromise of corporate systems and e-commerce;
• Cyber-fraud and financial loss.
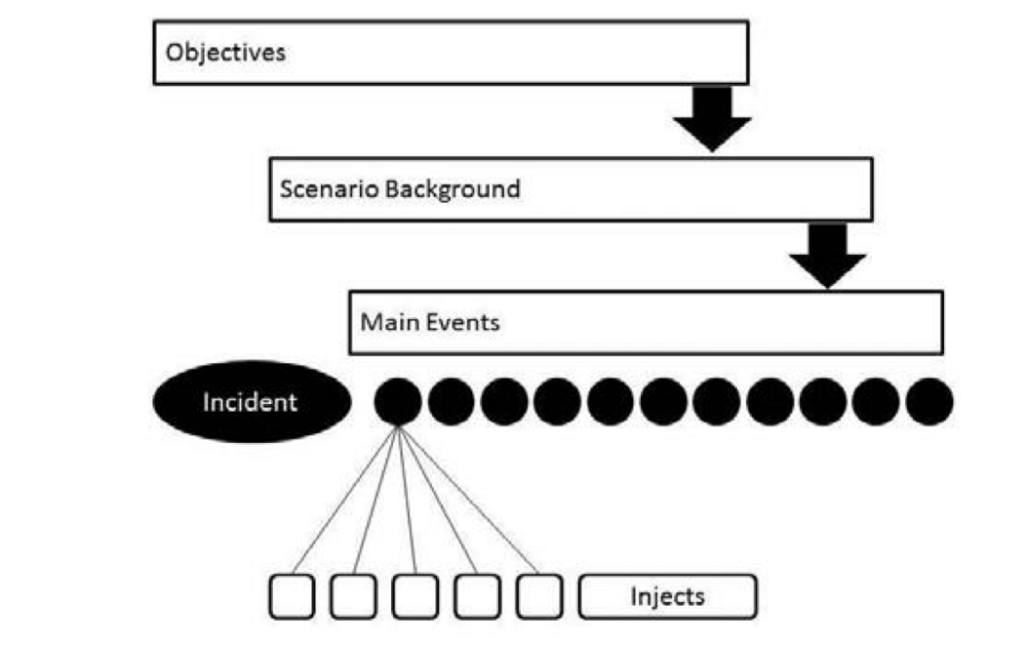
After one or more scenarios for the exercise are chosen, the next step is to choose a ‘storyline’, or list of events that will take place during the exercise. The terminology is that each event is ‘injected’ by the organizing team into the exercise. Each event must then be reacted to by the teams being trained during the exercise, and the result of what each team does is then evaluated according to the objectives of the test. In this way, the exercise organizers can create realistic situations, learn how the team operates under these situations, and extract intelligence and lessons of how to increase effectiveness.
Common storyline events for a scenario based on hacktivist attacks targeting sensitive information could include:
• Spear phishing emails reach user who clicks on infected attachment;
• Malware persistence and C&C established;
• Lateral movement and compromise of AD server;
• Download large amounts of data from Sharepoint and Exchange;
• Leaked data on Torrent sites;
• Media coverage and reaction;
The flow between all of these components can be described visually in the following way :
Types of cyber exercise
Different types of cyber exercise can be trained, with increasing levels of complexity and technical/operational realism. The choice of which type of exercise to perform should take into account the goals and maturity level of the team that will be trained.
In general, there are three types of cyber exercise: table-top exercises, hybrid exercises and ‘live’ exercises. Table-top exercises are the least complex to prepare, while ‘live’ exercises are the most complex.
Table-top exercises: In this type of exercise, participants work through a scenario and steps to respond to it. Events and injects are scripted by exercise planners and delivered through email, phone, or web to the exercise participants as the scenario unfolds. These exercises do not require any type of technical setup to prepare, simplying logistics.
Hybrid exercises: In this type of exercise, most of the events and injects are scripted by the exercise planners and delivered through email, phone or web to participants, along with some live technical attacks for demonstration purposes and as a means to increase realism.
‘Live’ exercises: In this type of exercise, the scenario incorporates full-blown live technical injects and attacks by a red team against a production or realistic test network defended by a blue team. These types of exercise are the most complex to prepare, since they require access to production environments and qualified teams on both sides (red team and blue team). On the other hand, they are also the most realistic.
Cyber exercise teams
After having established the exercise’s objectives, drawn up one or more realistic scenarios, and choosing which type of exercise is the most appropriate, the next step is to organize the different teams which will participate in the exercise.
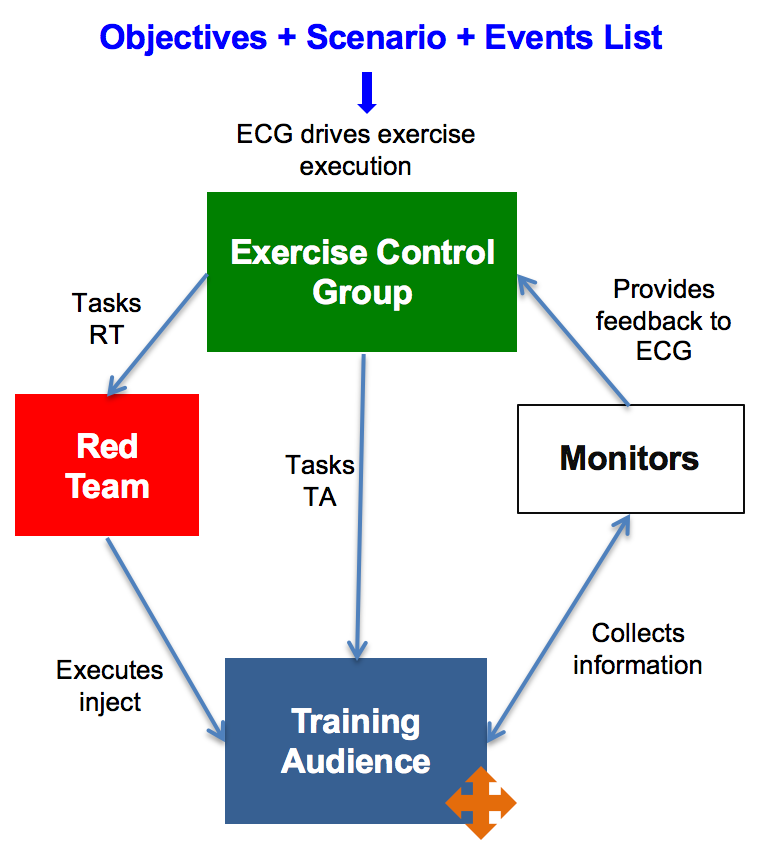
There are four major types of teams which participate in a cyber exercise: the exercise control group (green team); the training audience (blue team); the attackers (red team); and the monitors (white team).
Green team — exercise control group: this team coordinates and drives the execution of the exercise, and is responsible for the overall effectiveness of the project. As such, it is responsible for injecting scenario events in a way which tests the training audience, monitoring the outcomes and extracting information on what works and what doesn’t.
Red team — attackers: this team is tasked by the green team with specific storyline injects simulating cyber attack events, and delivers them to the training audience (blue team). On a ‘live’ exercise, this means executing the attacks directly; on a table-top exercise, this means just announcing what has taken place to the training audience.
Blue team — training audience: this is the team which is to be assessed and trained during the exercise, and is the team responsible for dealing with the events being injected in the exercise scenario. In a table-top exercise this could be as simple as stating how they would deal with a cyber event (execute a response procedure for example), while in a ‘live’ exercise this team would have to actually execute the procedures, detecting and responding to live attacks on production infrastructure. The training audience can even be composed of different organizations (eg., network security, police, media handling), to train each team in how to react to a given scenario.
White team — monitors: this team helps the green team, by staying ‘embedded’ within the red team and blue team, and is responsible for monitoring what actions are taken in each, documenting the outcomes, and providing feedback on these activities back to the green team.
The following chart describes the overall flow between each team: