In our monitoring we see little being created from scratch in everyday cybercrime. Generally speaking, most of what we find are adaptations of crimes, techniques and tools already used previously. This is no different with IoT botnets.
Since the Mirai botnet’s source code was made available on the Internet (October 2016), several variants have appeared, with little or no modification to the original code. Depending on the variant, what changes is the infection method, which, in some cases, focuses on devices that use standard passwords and on others that exploit vulnerabilities which allow for remote code execution; in a few other cases, multiple methods of infection are used.
From this stage, the operation is very similar in almost all variants. They all use access (obtained through a standard credential or exploiting a vulnerability) to download a payload that is typically a Shell script.
The use of the shell script language appears to be purposeful. These botnets exhibit a very worm-like behavior and, after infection, they scan the Internet for new IoT devices to infect. There is no control over which device will be infected or what architecture this device uses, so a simple way to make code work in any architecture is to use shell script because, despite the differences, these devices always use Linux as the operating system. which supports the shell language by standard.
Once the malware identifies the target’s architecture and forces it to download and execute the corresponding binary, that device becomes part of the botnet and begins performing the actions defined by its administrator. Whether it is DDoS attacks or the search for new victims.
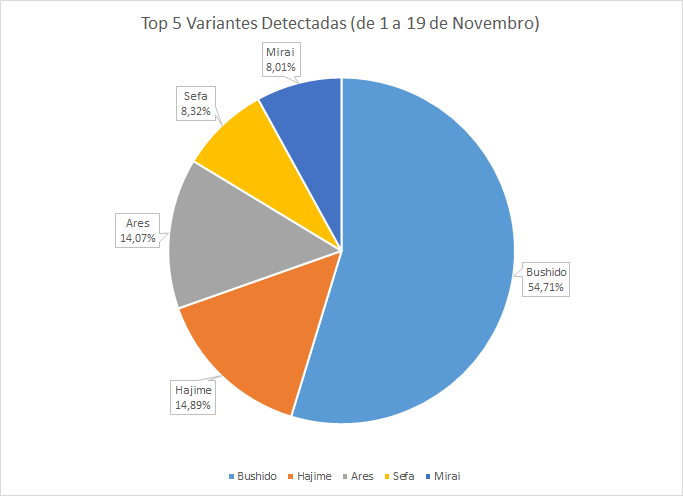
This month, more than half of the attempted invasions of our honeypots were made by the Bushido variant, followed by Hajime, Ares, and Sefa. The Bushido variant was identified by the Fortinet company in an 26 October publication, according to which this variant would be used in DDoS rental services.
This infection process occurs either through bruteforce in the Telnet service or by exploiting remote code execution vulnerabilities on routers.
The passwords used in the bruteforce process originate from lists of factory default passwords or are defined by Internet providers.
When access is obtained, a wget command is executed to download the payload on the web server 176 [.] 32 [.] 33 [.] 123. In this case, the author does not care to verify the architecture of the device and downloads executables compiled for various architectures.
Once executed, the binary establishes connection with the same server from which the previous files were downloaded (176 [.] 32 [.] 33 [.] 123) on port 3265 without the need for authentication, and receives an initial command “BIGEPS ON” to start the search for other vulnerable devices. We detected the “BIGEPS OFF” message in some cases, which indicates that the attacker can determine when the devices should start the search for other victims. After infected, the device waits for commands to initiate DDoS attacks.
During our monitoring, it was possible to identify at least 70 UDP and STD attacks (1024 bytes random payload) being triggered by this variant, but none of them targeted Brazilian companies or IP addresses.
By analyzing its binary, it was possible to identify that, in addition to bruteforce, this variant attempts to exploit at least three vulnerabilities in largely used routers: Dasan GPON routers, Huawei HG532 and Eircom D-1000. This is a small amount of exploited vulnerabilities when compared to other variants — we have already seen some variants using more than 10 different vulnerabilities for the infection process.
The trend is that the number of exploited vulnerabilities and the number of infections will only increase as Internet operators continue to distribute standard password devices to their subscribers, and the firmware update process still depends on user interaction.
We recommend that home users constantly check for updates to their devices and that companies always check the status of their routers in order to identify as quickly as possible if there has been any compromise in the device.
IOCs:
MD5
897d330bfbeeb1d3895671e7655d4178 arm5.bushido
769bf57c9c80a99d70970c1febec5b75 arm6.bushido
d3939e1c8a2d5e4ddcb30f1e210c3932 arm7.bushido
9d06e242ab16394cbcc500b8478dda5c arm.bushido
b135774fb6fa86ad0d079d1f537a704c m68k.bushido
5633362701d9844b6db0e04946381fb9 mips.bushido
b7c7a3fd4d47ab394f997469ddcb17ee mpsl.bushido
47d8c10c09f91256e4ee1211d23e7bcf ppc.bushido
c8e8a4764217e241a73ae83ecc90ba71 sh4.bushido
69bb1cc9b2bf1b93d0cb2c7fcbca1e3e spc.bushido
c9e095989082e98cec9747307af45fb3 x86.bushido
SHA256
cab78b922e7f2826f47890b1407170fda47e851839636a2654372d55d20c9c1c arm5.bushido
29863377f7e06cb27e63e4263f97ee28661f2df239f383ea297ad531cb37d00b arm6.bushido
0f000dc18bfa638563a0555a9213b0c01ef69148f1beb08edad16810ce78ad3d arm7.bushido
8bfb2e91a06ef535fa31f9dbaa3939a449a48f433a03e72436a57e0828a11c56 arm.bushido
77c20f7d2ee0b018e00c3fdc9ff5a89994c592967b1f3d9cbb4021c265746e60 m68k.bushido
518d220dd2bf8335fabfba3fb2247e090710138a4be1276024de287fb35dc130 mips.bushido
d7ab74282b013c44d4dfff81fcb5aeb8a5d704b3ce29a1cde4b78481f73b7258 mpsl.bushido
045a4880ff8b039746655d16ace9004fd712219321c566326b3a77c7458e0722 ppc.bushido
4e67a530441859416277648678b535e50a60de4703121c0a544a5e88e4a64efd sh4.bushido
4ef7e2e1adb6712a83560e3f36a3731ac6fd2183aa8b6d9caa91c08ca81d64c8 spc.bushido
407262063c442c1f2cd8af0ef7b417cba5e33beb486b3a839193ecf0569ccb74 x86.bushido
Payload and C2
176.32.33.123
Infected Devices
1.196.90.161
1.221.173.189
101.94.217.154
103.217.89.216
109.167.78.50
109.59.179.228
110.132.207.76
112.116.175.78
113.234.166.95
114.224.87.162
116.107.33.100
117.139.112.194
14.205.200.146
155.4.216.36
171.241.128.177
177.188.142.1
178.46.11.34
178.46.28.177
178.46.42.244
178.47.109.250
178.47.121.244
178.47.178.217
178.47.179.164
178.94.255.180
180.64.39.213
181.22.226.49
182.113.127.188
185.180.233.241
188.16.18.219
188.16.38.208
188.18.131.35
188.18.140.202
188.18.143.252
188.18.159.200
188.18.180.0
188.18.181.98
188.18.191.13
188.18.200.233
188.19.139.107
188.19.233.197
203.207.56.142
212.220.110.2
216.195.242.58
219.77.206.108
220.172.230.183
222.142.70.151
222.91.219.113
24.207.67.221
27.79.147.214
27.79.173.229
31.162.101.239
31.162.103.57
31.162.157.150
31.162.83.65
31.163.38.55
31.163.48.204
31.163.88.70
37.79.57.4
37.79.57.92
37.79.97.208
46.183.122.120
46.200.189.6
5.140.252.152
5.140.33.171
5.141.78.113
67.85.196.69
76.169.77.243
76.228.198.37
80.229.183.147
81.230.96.43
83.209.251.104
84.95.45.177
85.54.229.40
89.27.168.50
90.151.135.255
90.224.194.247
91.205.197.12
93.107.28.70
94.50.156.95
94.51.118.247
95.134.201.27
Logins and passwords used in this campaign
adm:(no password)
admin:(no password)
admin:1111
admin:1234
admin:2601hx
admin:QwestM0dem
admin:admin
admin:admin1234
admin:adminadmin
admin:cat1029
admin:changeme
admin:conexant
admin:default
admin:dvr2580222
admin:extendnet
admin:ho4uku6at
admin:ironport
admin:meinsm
admin:microbusiness
admin:nCwMnJVGag
admin:pass
admin:password
admin:root
admin:smcadmin
admin:true
admin:zhongxing
bin:(no password)
daemon:(no password)
daemon:daemon
default:(no password)
default:OxhlwSG8
default:S2fGqNFs
default:antslq
default:default
default:lJwpbo6
guest:(no password)
guest:1111
guest:12345
guest:guest
guest:password
root:(no password)
root:1001chin
root:1111
root:123456
root:20080826
root:54321
root:5up
root:88888888
root:ROOT500
root:Zte521
root:abc123
root:admin
root:ahetzip8
root:anko
root:ascend
root:blender
root:cat1029
root:changeme
root:default
root:iDirect
root:inflection
root:ipcam_rt5350
root:ivdev
root:juantech
root:jvbzd
root:klv123
root:pass
root:password
root:root
root:svgodie
root:t0talc0ntr0l4!
root:vizxv
root:zhongxing
root:zlxx.
root:zsun1188
service:ipdongle
smcadmin:(no password)
support:support
ubnt:ubnt
user:changeme
user:password
user:user
vstarcam2015:20150602
www2:9311
www:9311
