My name is Gabrielle. I am a student in the 8th period of Computer Science at the Catholic University of Pernambuco, and, in this article, I share some of my experience as an intern at Tempest and the results of a project I developed from Burp as part of my internship program.
But, first, “how did I get to Tempest?”.
At first, it was never in my plans to work for a security company. In 2018 I heard about an internship opportunity in the engineering area at Tempest, a company I already knew through some colleagues who worked there. I had a first interview, but I wasn’t very excited. In fact, I had already gone through an internship as a support and, in another company, as a developer in a project. I imagined that, after this project, I would be allocated as a developer definitely; unfortunately, I was allocated as an analyst, which discouraged me and led me to look for other ways.
Around this time, I had two new opportunities, one at CESAR and one at Tempest’s consulting team, through the recommendation of a friend who worked there. After an interview, in which I was approved, I opted for Tempest.
A little shy, I came to the company to work with pentest — something I had no knowledge of — but I was very welcomed. I think it’s nice to also point out that I was the first woman in the consulting team, which only contributed to my shyness, because we know that women still suffer prejudice when they decide to work with technology. But Tempest was different (I actually felt that it would be different from conversations with colleagues who worked there).
I went through a series of trainings and started the internship, which was divided into 3 phases: in the first one, we went through web security training and were allocated as shadow analysts of one analyst of this team. In the second phase, we went through a mobile security training and became a shadow of a team analyst. Finally, in the third phase, we developed a research project that involved the development of a plugin for Burp Suite. The following are some results of this project.
Reverse Tabnabbing
The idea of creating another extension for Burp came up in one of the editions of “Na Beira do Rio” — “By the Riverside”…, which are weekly meetings where Tempest’s technical professionals present their projects and research. In this issue, a colleague from the Engineering team brought up a vulnerability related to flaws in the web application development process. This vulnerability offers the potential for Reverse Tabnabbing attacks, in which a Y page could be rewriting an X source page to, for example, replace it with a phishing page. This is possible by creating an HTML link containing the target =“_ blank” attribute, without this attribute being accompanied by another attribute (rel = ”noopener”). In these cases, using the window.opener property, it is possible from the landing page to have partial access to the page from which it was created.
For illustration purposes — what follows is not really an issue on Twitter, it’s just an example — imagine that a user is browsing a news profile on Twitter. At some point, the user clicks on a news link to read the full story, and that link opens a new tab.
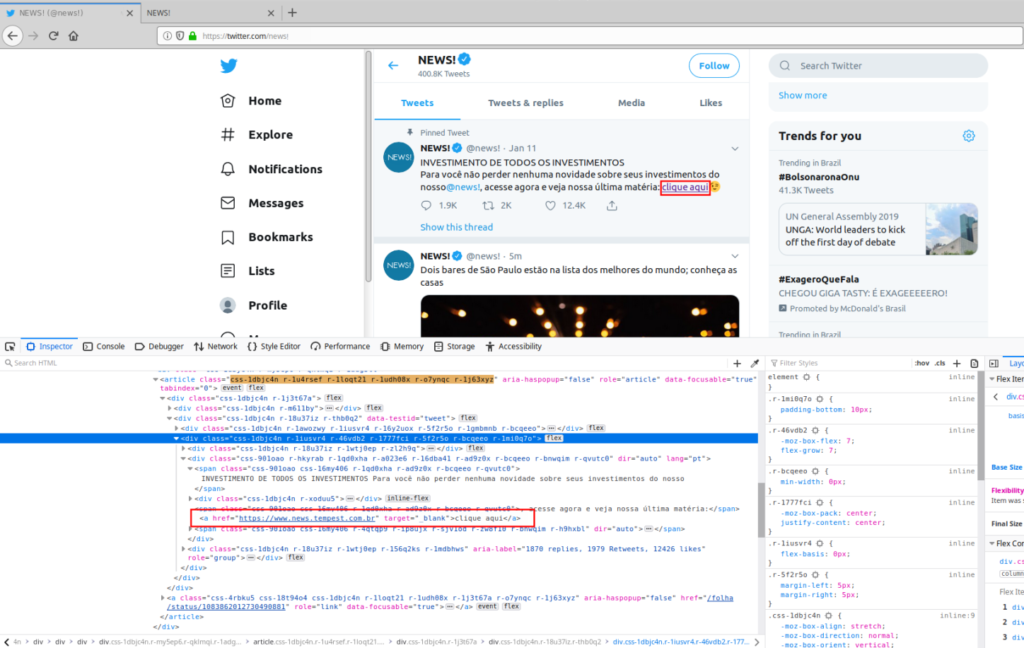
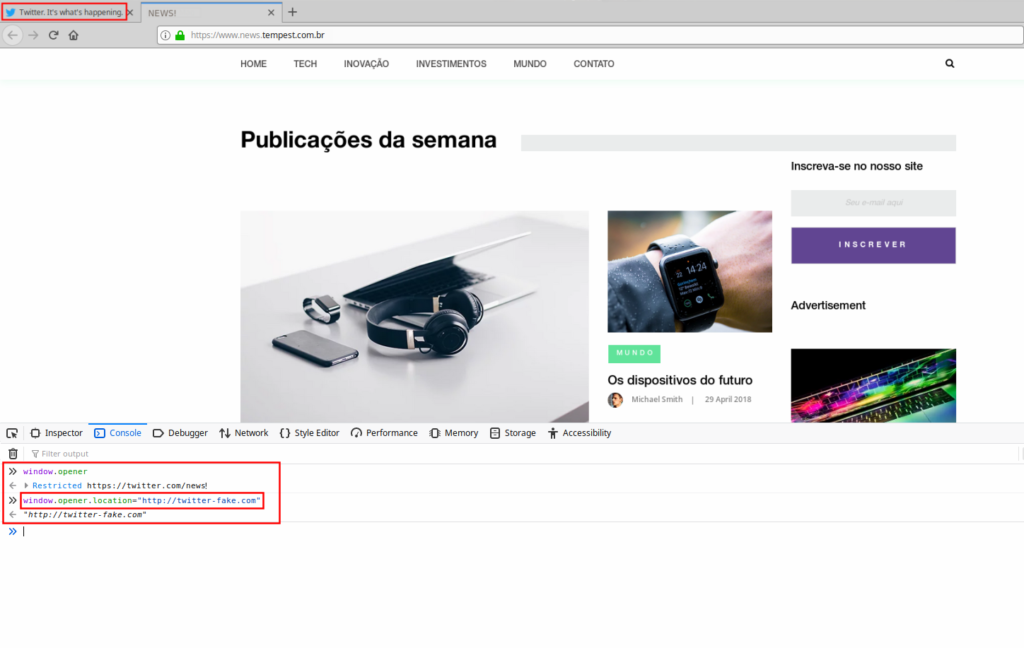
While the user is on the site reading the news, the page runs the script embedded in its page (window.opener.location = “http://twitter-fake.com”), after that, in the original tab, a fake Twitter-like webpage is displayed. This fake page prompts for login, justifying that the user has been logged out for some reason, and the user, without much thought, enters their credentials and submits the form.
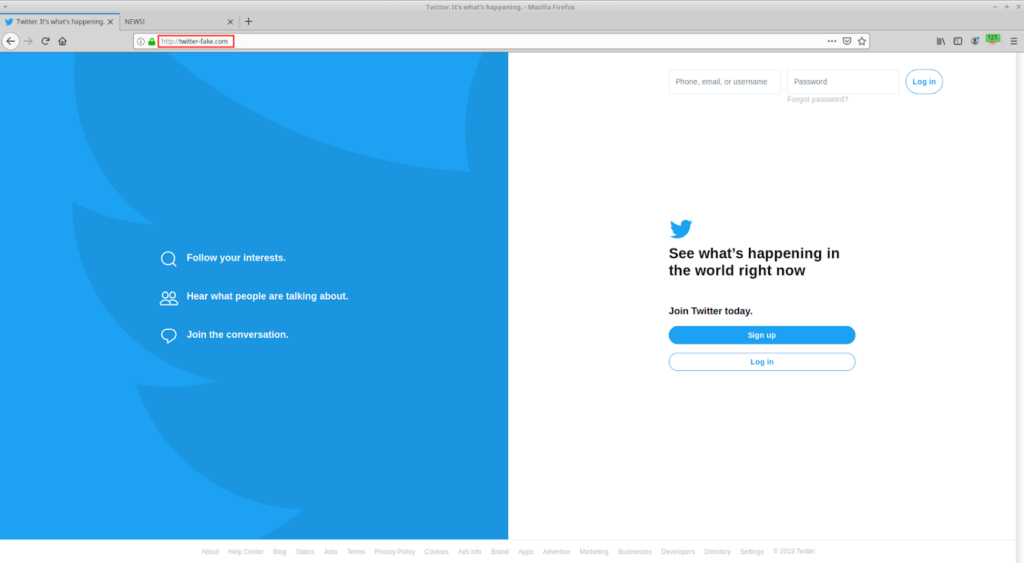
With this, the user ends up sending their credentials to the attacker, who can immediately log in with the captured credentials and do what they want.
Developing a Burp plugin to detect Reverse Tabnabbing
From this vulnerability, I had the idea of creating a Burp extension that could identify the existence of HTML tags that contain the target =“_blank” attribute but do not contain the rel =”noopener” attribute.
Burp Suite is a software developed in Java, by the company PortSwigger (widely used in Tempest consulting team projects), and its main function is to be used as a proxy for the security testing of web applications. The software also includes a number of useful components, such as Burp Repeater (which handles and resends requests to the server), Burp Intruder (which allows some tests to be automated) and Burp Scanner (which scans applications and automatically finds some vulnerabilities), among other tools. In addition, it is also possible to access a number of extensions developed by users of the tool in an area called “BApp Store”. These extensions allow Burp to further enhance its functionality.
Studying the creation of a Burp extension, I found out that the documentation from PortSwigger itself (Burp developer) is sparse; fortunately, however, I was able to find several code examples on GitHub that were crucial for development. Initially I chose to use the Java language as this is the tool’s native language, but for convenience (and familiarity on my part), I decided to switch to Python.
Among the difficulties I encountered, the biggest ones are related to getting the content I would need to analyse from the getResponse object.
The point is that the return format of this object is of type bytearray, and I would need to convert it to string in order to make the necessary filters for the plugin to work. Various means of conversion were tested, and, after relentless searching GitHubs, forums, and documentation, a colleague pointed me to a method called Python’s dir() itself, which returns all the attributes of an object. With that, I was able to use the attribute of Burp’s own interface, which does the conversion to string.
Then the development went smoothly and in about 2 weeks (including the difficulties) I was able to finalize the first version of the Discovering Reverse Tabnabbing plugin, which allows (from the Burp Scanner component) to detect HTML tags that are in vulnerable situation,as I pointed out earlier. Upon performing this detection, the plugin will automatically create an issue in Burp that allows for analysing which parts have this vulnerability, as follows:
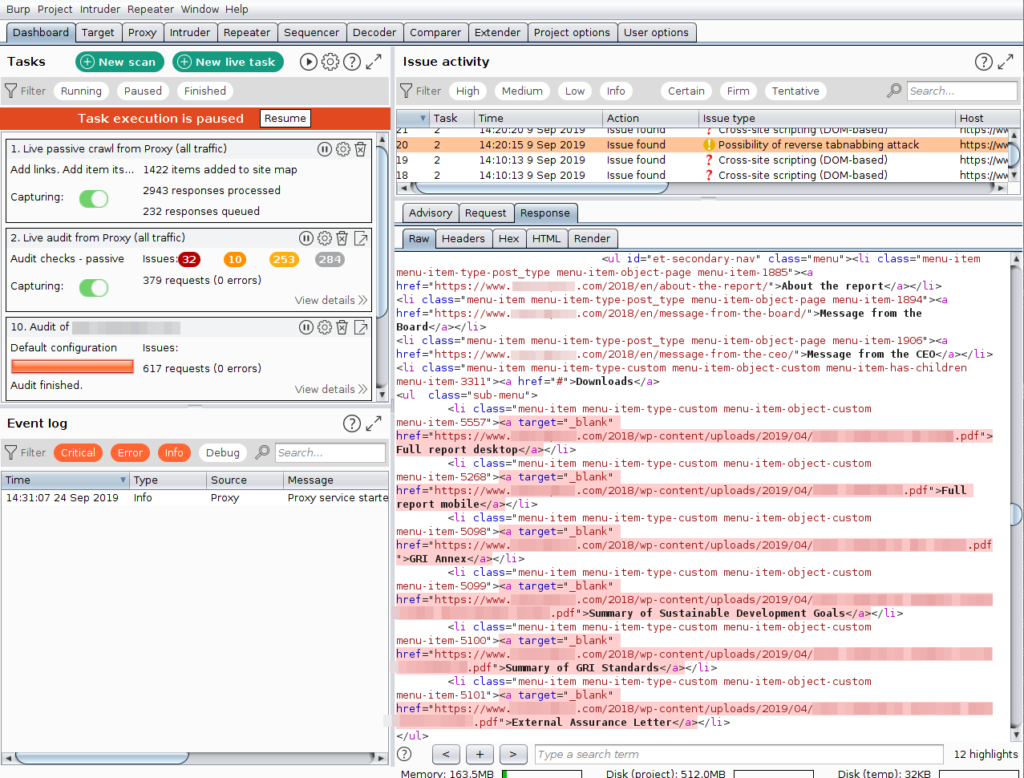
The plugin is available on my GitHub and, to start using it, it is necessary to:
1. Download the “Standalone jar” version of Jython (https://www.jython.org/download);
2. Open the Burp Suite tool;
3. Go to the “Extender> Options” tab;
4. In Python Environment select the Jython file, which was downloaded in step 1;
5. After that, go to “Extender> Extensions” and click * Add *;
6. Under “Extension Details -> Extension type” select Python and under “Extension Details -> Extension file” select the discoveringRT.py file that is available on GitHub (https://github.com/GabsJahBless/discovering-reversetabnabbing)
