DoS attacks have become a constant problem for many companies around the world. According to the HIPPA Journal[1], in 2021 there were around 9.84 million DDoS attacks; an increase of 14% compared to 2019. A report presented by Dell[2] predicts that between 2018 and 2023 the number of DDoS attacks will double. The main sectors affected in 2021 were finance, health, education and government.
As well as having to deal with the loss of important services and the resulting damage, many companies have suffered from a new type of attacker, Ransom DDoS, or RDDoS. After a successful DDoS attack, the attackers threaten the affected company with further attacks if an amount is not paid. According to a report by Cloudflare[3], 1 in 5 attacks carried out in the second quarter of 2022 was accompanied by an extortion letter.
The aim of this article is to explain how DoS attacks work and suggest defense mechanisms and actions to mitigate them.
1. DoS and DDoS
DoS stands for Denial of Service, while DDoS stands for Distributed Denial of Service. Both represent attacks with the aim of causing a service to become unavailable, however DDoS is used for attacks with multiple origins while DoS means an attack generated from a single computer. In many literatures, this term is used interchangeably. From now on, in this article we will only use the term DDoS to refer to all types of attacks.
1.1 Motivation
A DDoS attack can have the following motivations:
- Smokescreen – Many attacks are carried out to keep the target’s cybersecurity team busy while the attackers make attempts to break into the environment.
- Extortion – After carrying out a brief DDoS attack, the attacking group threatens to carry out further attacks if a sum of money in cryptocurrency is not paid by the target.
- Competition – A company can fund a DDoS attack against a competitor in order to harm them, for example, taking down a retailer’s website during a massive sales campaign such as Black Friday.
- Ideological/Military – Opposing groups or nations use DDoS attacks to damage their opponent’s services and communications. This can be seen recently in Russia’s war against Ukraine, and in the actions of the Anonymous group during the “Arab Spring”.
- Revenge – Ex-employees can use DDoS attacks to damage the company they worked for out of a sense of discontent.
1.2 BOTNET
BOTNETs are a collection of computers infected with command and control programs, allowing attackers to send remote commands arbitrarily. These devices are usually contaminated through malicious links and the exploitation of vulnerabilities. It’s very common for BOTNETs to be used in DDoS attacks to generate a large volume of traffic during an attack.
1.3 Types of DDoS attacks
DDOS attacks are commonly divided into 3 categories:
- Volumetric;
- Protocol;
- Application layer.
1.3.1 Volumetric
Volumetric attacks aim to overload the target’s network and processing capacity through a high volume of traffic. This category of attacks is measured in bits per second.
Below are some examples of this type of attack:
HTTP flood
The HTTP flood attack aims to generate several requests with GET or POST methods to a web server in order to exhaust the target’s bandwidth. This attack is usually carried out via a BOTNET with thousands of computers initiating connections. Since this attack is very similar to an ordinary user’s access, it’s difficult to detect.
UDP flood
A UDP flood attack is carried out by sending a huge number of UDP packets to a server. The aim is to exploit the way a server normally responds to UDP packets:
- upon receiving a UDP packet, the server will check whether there is any program listening on the specified port
- if there is no program using that port, the server will respond with an ICMP packet to inform the sender that the destination port is not operational.
By receiving this many packets, the server can become overloaded and stop responding to new requests, preventing legitimate traffic from being processed. It’s also possible that the firewall, which protects the server, becomes unable to process the load of requests from a UDP flood attack, and as a result is impacted.
ICMP flood
ICMP flood attacks occur in a similar way to the UDP flood attack: a huge amount of traffic will be sent to the target to consume bandwidth and computing resources, abusing the ICMP protocol’s reply feature. Upon receiving an ICMP request (echo-request), a server will respond with another ICMP packet (echo-reply).
IPSEC flood
The IPSEC protocol is widely used in VPN connections to establish a secure connection between devices over an unsecured network.
IPSEC flood attacks send a large number of IPSEC IKE requests to a VPN server via port 500, forcing it to respond to all requests. Each response will consume the server’s processing resources until it runs out, thus causing the service to crash.
Reflection Amplification
Reflection amplification attacks are carried out by sending packets with a falsified source IP to various services on the Internet. The source IP in these packets will contain the IP of the target. By sending these requests, Internet services will respond to the target’s IP, thus consuming its bandwidth. As a result, depending on the scale of the attack, there may not be enough bandwidth to respond to legitimate traffic.
1.3.2 Protocol
Protocol attacks aim to abuse weaknesses in protocols commonly used on the Internet. This category of attack is measured in packets per second.
SYN flood
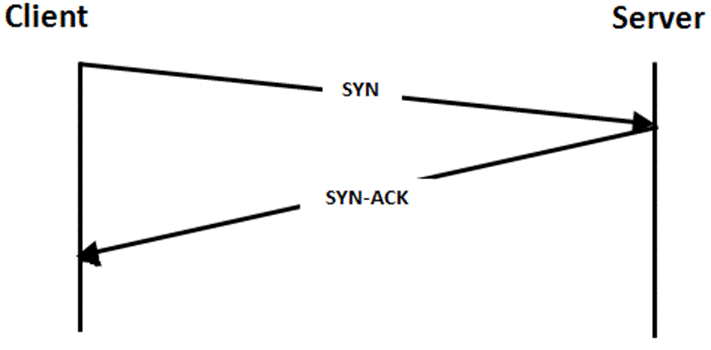
The SYN flood attack exploits a weakness in the TCP protocol’s three-way handshake. Normally, when it’s executed, the client sends a SYN packet, the server replies with a SYN/ACK packet and waits for a final ACK packet from the client before it can start sending data. The image below shows this process:
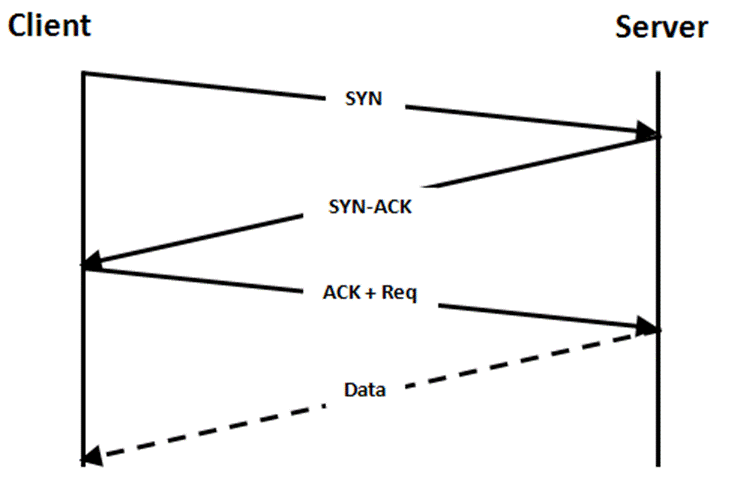
In a SYN flood attack, several SYN requests are sent, but the client does not respond with an ACK packet. As a result, the server waits for this packet and keeps the characteristics of this connection in a table until the timeout for this connection attempt is reached. With the accumulation of this type of request, the firewall’s connection table will be exhausted before the connection timeout is reached, making it impossible for legitimate connections to be established, as well as causing a large consumption of resources. The image below demonstrates this process:
Fragmented packet
To explain fragmented packet attacks, it’s important to understand how packet fragmentation works in the IP protocol.
Each network operating on the Internet has a maximum packet size that it can process. This limit is called the maximum transmission unit (MTU). When a packet needs to travel over a network where the MTU is smaller than the size of the packet, it will need to be fragmented, i.e. divided into smaller parts.
An analogy for this process is the transportation of a large closet in a home. It will first have to be disassembled into smaller parts so that it can pass through the door, then it will be transported to its destination where reassembly will take place.
There are two types of fragmentation attack:
- UDP and ICMP: oversized UDP or ICMP packets are sent (usually with MTU greater than 1500). In this situation, the server ends up reserving resources for packets that can never be reassembled, until it reaches a point where the server can no longer process legitimate packets.
- TCP: The target of these attacks is the packet reassembly mechanisms, which cause packets to overlap when they are reassembled. There are operating systems that cannot cope with this situation and start operating in an undesirable way, often resulting in a blue screen. Examples of vulnerable systems are Windows Vista and Windows 7.
Packet fragmentation is necessary because each network on the Internet has a certain size of packet that it can process.
1.3.3 Application layer
This category of attack seeks to exploit vulnerabilities in the functioning of application layer protocols. Not all application layer attacks generate large volumes of data, but that doesn’t make them any less effective.
Low and slow
Attacks of this type aim to create extremely slow connections to exposed web servers on the Internet. The aim is to occupy the server with several active slow connections to prevent legitimate users from using the services.
This type of attack is difficult to detect, as it doesn’t generate large volumes of data and can go unnoticed. Attackers can use both GET and POST methods to generate these requests.
Large Payload POST
This type of attack takes advantage of a web server’s XML message parsing mechanism. Using the HTTP POST method, an attacker will create complex requests so that the server uses a large amount of memory to parse the message. In addition to complex messages, variations of this attack include excessively large headers and message bodies.
Bellow is an example of a complex request attack:
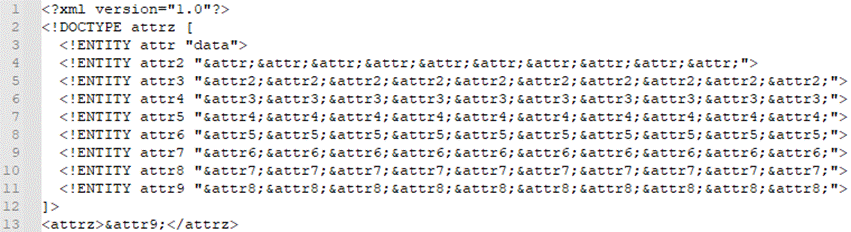
This message contains a root element called attrz, as well as several entities. The first of these entities contains the text “data”. The attr2 element expands the attr element 10 times. The attr3 element expands the attr2 element 10 times, and so on up to the value9 element. This way, when the message parser has finished expanding the entities, that 1KB block will actually be several GBs. With just a few messages like this, a web server can easily be overloaded.
Now we have an example of a large header attack:
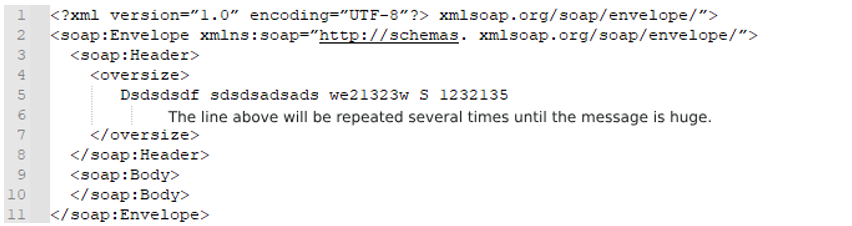
An attacker can create a message where the header is a few MBs long and then use a small BOTNET to send that message to the target. Through this approach, the server can be overloaded with several GBs of data, preventing legitimate traffic from being processed.
Unlike other types of DDoS attack, Large Payload POST does not require a large number of computers to execute. It’s also difficult to detect because it doesn’t have a recognizable pattern.
Mimicked User Browsing
This type of attack is carried out via a BOTNET. In this case, the computers will simulate legitimate users accessing a website. The aim is to cause a large consumption of resources on the target so that it is taken down, or at least to prevent and hinder legitimate users from using the service. This is another attack that is difficult to detect, given the fact that it simulates the actions of legitimate users.
DNS flood
The aim of a DNS flood attack is to exhaust the resources of a DNS server through a large number of DNS requests. In this type of attack, an attacker uses a botnet to bombard a DNS server with malformed packets. This will generate a high consumption of processing, memory and bandwidth.
In this situation, the DNS server won’t be able to handle requests from legitimate users, and the domains linked to that server will become inaccessible.
2. Anti-DDoS mitigations: Learning How to Defend Yourself
Due to the large number of different types of DDoS attacks, there are also different solutions suitable for each situation. Below, we’ve divided the different defense options between on-premise and cloud environments.
2.1 On-premises
Scrubbing center
Scrubbing center is a DDoS mitigation service in the cloud. It’s capable of capturing and filtering traffic destined for a hostname or IP address block, delivering to its destination only traffic that is considered legitimate.
Through a scrubbing center, it’s possible to defend against volumetric and protocol attacks, without having to invest significant amounts in infrastructure. In addition, it allows you to mitigate attacks aimed at the company’s IP addressing infrastructure, which is not possible with other protection services, such as a CDN. It’s important to note that when this type of service is activated, there will be an increase in latency between the client and the application protected by the service, as traffic will be diverted and filtered.
It’s possible to activate the scrubbing center service on a 24×7 or on-demand basis. This way you can only use it when under attack.
There are certain requirements for protecting IP address blocks, such as having a public block of 256 IP addresses and routers capable of creating a BGP tunnel. As such, this type of service is not viable for all types of company. Another feature of this service is that it doesn’t perform SSL inspection and is therefore unable to protect against service layer attacks.
DDoS appliance
An anti-DDoS appliance is a piece of equipment specially designed to mitigate DDoS attacks. Its hardware is designed to handle a high level of connections and traffic. It performs SSL interception, i.e. it is capable of decrypting packets and reading their contents, provided it has the appropriate certificate, so it can act to defend against protocol attacks. It is usually sold with different packet processing and bandwidth capacities.
Unlike scrubbing centers, the implementation of a DDoS appliance is much simpler and has fewer requirements. A major advantage of this equipment is the possibility of creating specific defense rules, whereas in scrubbing centers and CDNs, these options are more limited.
CDN
CDN is short for Content Delivery Network. It’s a cloud service used to deliver the content of a web application’s static pages to users based on their geographical location. CDN services are highly capable of mitigating the three types of DDoS attacks, but they only protect hostnames and have no ability to mitigate attacks aimed directly at the IP addresses hosting an application, which is particularly worrying for applications hosted in on-premise environments. Furthermore, a CDN is only capable of protecting web applications; other types of application must be protected by other means.
It’s common for CDNs to only offer DDoS protection against volumetric and protocol attacks by default. On the other hand, additional fees are charged for protection against application layer attacks.
WAF
A WAF (Web Application Firewall) is responsible for protecting and mitigating threats targeting web applications. This includes threats such as SQL Injection, Cross-Site Scripting (XSS), file inclusion, as well as application-layer DDoS attacks.
It’s common for a WAF to be available as a feature in a conventional firewall. This is a useful option, especially when there is no CDN and/or anti-DDoS appliance protecting a web application.
Hardening de firewall
Hardening a firewall to increase its resistance to DDoS attacks is good practice. The most advanced firewalls have various configurations that can be applied to detect, mitigate and withstand these types of attacks, but it’s important to bear in mind that they weren’t developed to defend against large-scale DDoS attacks, and in these cases, they can’t be used as the only line of defense.
Various DDoS protection configurations can cause unwanted effects such as false positives, high resource consumption and slow access to applications. You need to understand how each protection works and the possible impacts of activating them.
The most common protection configurations include increasing buffers, reducing TCP connection timeouts and optimizing the packet discard process.
Summary of application layers
To create a DDoS defense strategy, it’s important to understand what each element of your defense is capable of. Below is a brief summary of these elements and their application.
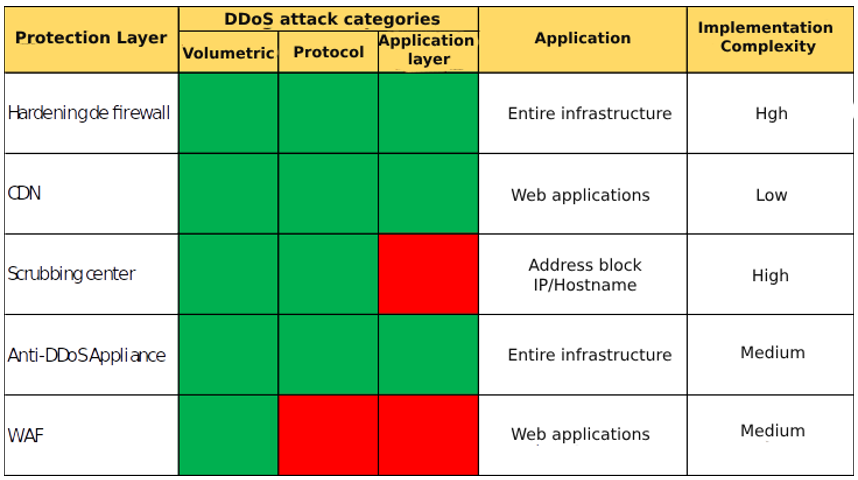
As described above, it’s important to note that different elements work in different ways and have different defense capabilities. For example, an anti-DDoS appliance is capable of mitigating all 3 types of DDoS attacks, but it’s not as effective in volumetric attacks as a scrubbing center or CDN.
As with any cyber defense strategy, it’s recommended that it be thought out in depth, i.e. an attacker will have to go through several layers before they can reach their target.
Below is a representation of the topology with these layers applied.
2.2 Cloud
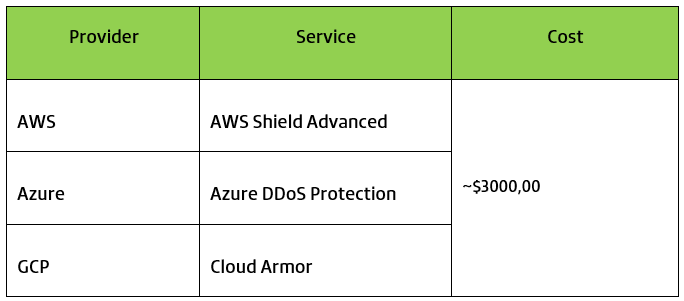
The defense strategy against DDoS attacks in the cloud is a little different from an on-premise environment. The largest cloud providers, such as AWS, Azure and GCP, natively provide robust protection against DDoS attacks targeting layers 3 and 4. This protection is automatic and requires no extra costs.
For protection against application layer attacks, the cloud providers mentioned above offer services with similar characteristics:
- the possibility of employing WAFs at a reduced cost;
- advanced monitoring of DDoS attacks;
- a team available 24×7 to deal with ongoing attacks;
- reimbursement of resource scaling expenses caused by DDoS attacks;
- centralized dashboards and reports on DDoS threats and attacks.
Below is a list of the names of the services offered by each provider:
Monitoring – On-premises and cloud
Regardless of where an application is hosted, proper monitoring to detect DDoS attacks is critical. It’s common for an attacker to carry out smaller attacks before receiving a large-scale DDoS attack in order to test their target’s defenses. This reconnaissance can take hours or days.
With proper monitoring, it’s possible to anticipate these attacks and strengthen your defenses. An example is an attack aimed at a particular application that has caused high resource consumption, but has not caused a denial of service. In this situation it’s possible to prepare the environment to scale resources to the application and also adjust the upper layers of protection to prevent the attack from reaching the application.
It’s recommended that monitoring be configured so that it’s possible to detect attacks based on signatures and behaviors.
Conclusion
Effective defense against DDoS attacks involves a combination of proactive and reactive measures. This includes implementing hardened firewalls, detection systems, and security mitigation services.
DDoS, which can help identify and filter malicious traffic before it reaches its final destination.
It is crucial that organizations are prepared to deal with DDoS attacks by developing detailed incident response plans and carrying out regular security testing to assess the effectiveness of their defenses.
Ultimately, protecting yourself against DDoS attacks requires a multifaceted and ongoing approach to cybersecurity. By adopting best security practices, be prepared to
responding to incidents and collaborating with others in the security community, organizations can significantly reduce the risk and impact of DDoS attacks on their operations.
References
2021 Saw Record Numbers of DDoS Attacks on the Healthcare Industry. Available at: <https://www.hipaajournal.com/2021-saw-record-numbers-of-ddos-attacks-on-the-healthcare-industry/>. Accessed on April 22, 2022.
CISCO. Cisco Annual Internet Report (2018–2023) White Paper. Available at: <https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.html>. Accessed on March 9, 2020.
YOACHIMIK, O. DDoS attack trends for 2022 Q2. Available at: <https://blog.cloudflare.com/ddos-attack-trends-for-2022-q2/>.Accessed on July 6, 2022.
