Tempest security analyst Silton Santos recently discovered a vulnerability in Trend Micro Premium Security, Maximum Security, Internet Security and Antivirus + Security in its Windows versions; the flaw is related to a poor implementation of the CreateProcess function that is triggered by the execution of the PC Health Checkup functionality and may, if exploited, lead to elevated privileges.
Responsible for creating new processes, the CreateProcess function is represented by the following code:
BOOL CreateProcessA(
LPCSTR lpApplicationName,
LPSTR lpCommandLine,
LPSECURITY_ATTRIBUTES lpProcessAttributes,
LPSECURITY_ATTRIBUTES lpThreadAttributes,
BOOL bInheritHandles,
DWORD dwCreationFlags,
LPVOID lpEnvironment,
LPCSTR lpCurrentDirectory,
LPSTARTUPINFOA lpStartupInfo,
LPPROCESS_INFORMATION lpProcessInformation
);
To implement this function, one of the required parameters is lpApplicationName, which provides the name or path of the module to be executed; however, according to Microsoft documentation “if the value you enter in this parameter contains spaces, you must use quotation marks (“) to indicate where the file name ends and the arguments for its execution begins”.
This means that, when creating a hypothetical process, a directory C:\Program Files\Directory abc\Directory def \example.exe would be interpreted in the following order until a valid executable is found.
• C:\Program.exe
• C:\Program Files\Diretorio.exe
• C:\Program Files\Diretorio abc\Diretorio.exe
• C:\Program Files\Diretorio abc\Diretorio def\exemplo.exe
This recursion is due to the lack of quotation marks (“) in the path defined in that parameter, which will lead the operating system to try to define the beginning of the path of the file to be executed and what the arguments of this file are. This is also what happens when running the PC Health Checkup tool, which is feature for all the aforementioned softwares.
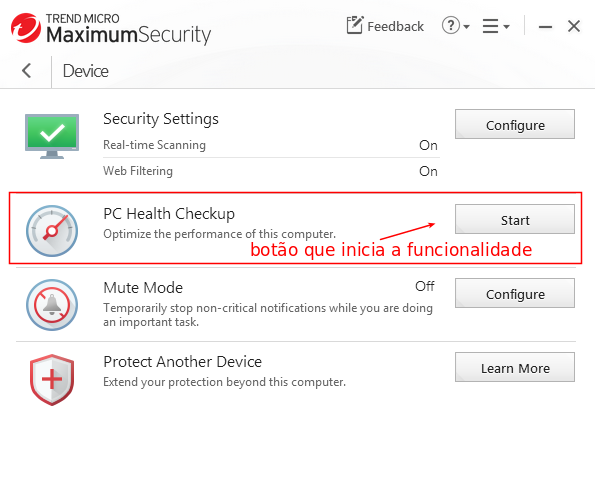
When running the tool, the coreServiceShell process attempts to load the PwmConsole executable recursively. In image 01 we see that the coreServiceShell tries to execute, C:\Program.exe and C:\Program Files\Trend.exe before running C:\Program Files\Trend\\TMIDS\PwmConsole.exe. Also relevant to notice is that these execution attempts are performed by an NT AUTHORITY\SYSTEM user process.
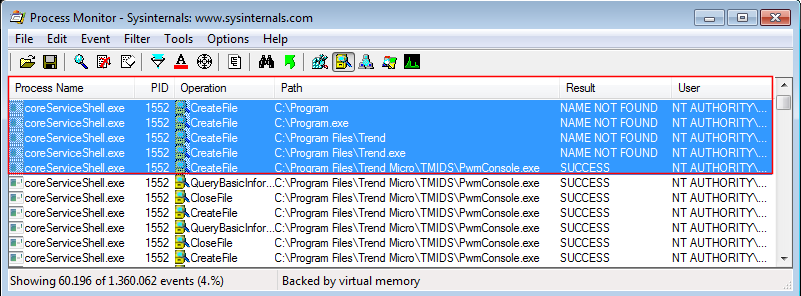
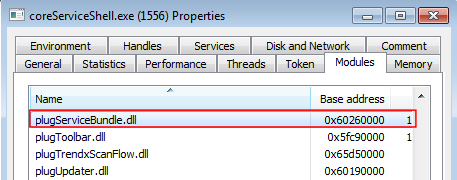
Parallel to this operation, the DLL plugServiceBundle is loaded by coreServiceShell (Image 02); among its functions is the CreateProcessW (Image 03).
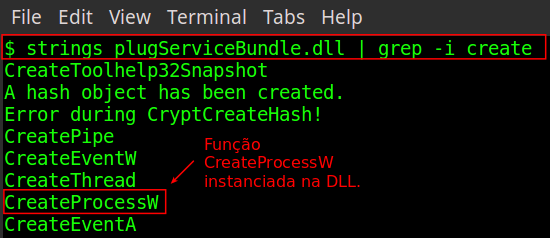
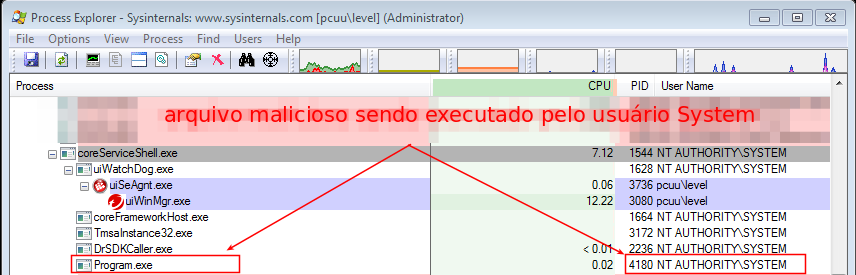
Assuming that an attacker has writing permission on C:\ or C:\ Program Files\, it could enter a malicious executable named Program.exe or Trend.exe and these would be executed by the coreServiceShell process, inheriting its NT AUTHORITY\SYSTEM user privileges.
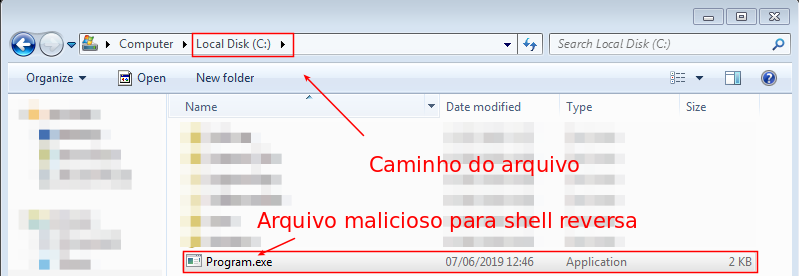
To prove the concept, a malicious executable was developed, which was later copied to the path C:\Program.exe, as shown in Image 04:
By running the PC Health Checkup tool (Image 05), a process is created with SYSTEM privilege (Image 06) with the execution of the malicious program.
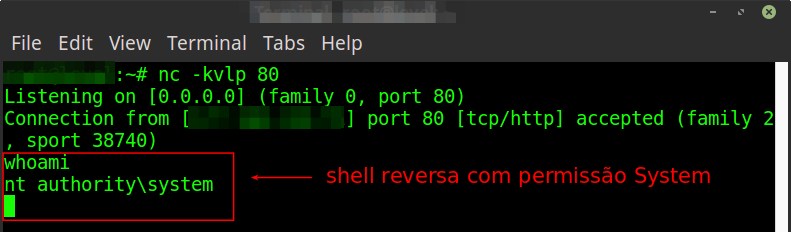
The success of the exploit can be verified from the external server waiting for the reverse shell, as shown in image 7.
The vulnerability was acknowledged and reported by Trend Micro through CVE-2019–14685. According to the security bulletin released on 14 August, patches have already been released and must be installed through the ActiveUpdate tool.
Report Timeline
- 24 Apr 2019 — Responsible Disclosure with Trend begins;
- 25 Apr 2019 — Trend has started analyzing the issue;
- 10 May 2019 — Trend requested more information about the PoC performed. Email was sent with the requested information;
- 22 May 2019 — Trend sent an update and requested a patch test;
- 27 May 2019 — The email was answered stating that the update had solved the problem;
- 28 May 2019 — Trend said thank you for the confirmation and warned that they were providing the public release and, upon finalization, would provide the CVE, release the public disclosure and insert the name in the Acknowledgment session on the Vulnerability Responses page;
- 04 Jun 2019 — Trend announced that the release was expected to be ready in July and, only after the release, the CVE would be provided;
- 31 Jul 2019 — Vendor reported that there was a public release and requested the validation of the patch again. An email was sent confirming the validation and requesting the CVE;
- 13 Aug 2019 — The CVE and the URL were reserved for security advisory (which was published on the next day [14/08]).
