Researchers from Tempest’s Threat Intelligence team have detected a new phishing campaign targeting Facebook users in Brazil and Mexico. In the campaign, sponsored ads offered discount coupons for a large fast-food chain in order to spread a malware which, according to the research, is divided into three modules: a file capture and credential theft module, a malicious extension to Google Chrome and a Remote Administration Tool (RAT), used for screen overlay to commit bank fraud.
Next, we’ll look at the details and methods used in this campaign.
Campaign Analysis
Phishing
In the scam, which would have made more than 10,000 victims, a sponsored ad (link imagem 1) offers discounts on products. To get discounts, one has to click a link to a website where the coupons are. The website is a malicious page containing a series of seemingly official coupons. On the page, the victim is prompted to click a button to supposedly download the coupons. By clicking the button, a compressed file (containing two files, with the extensions .msi and .exe) is downloaded to the victim’s computer.

By running the .msi file (through msiexec.exe — Windows Installer Component) a Visual Basic script (VBScript) is triggered, which, in turn, will trigger the following actions:
- Download other script files;
- Download and unzip a file containing the malicious extension for Google Chrome;
- Modify Chrome shortcuts from scripts to run the malicious extension;
- Start the RAT infection process.
VBScripts execution and RAT installation
The first VBScript (contained in the .msi extension file) runs a sequence of obfuscated codes, culminating in the download of a new VBScript on the computer. In all, six distinct routines were identified in the process. It is speculated that this is done in order to hinder the work of analysis and also as a method of evasion from antivirus programs.
The new VBScript downloads the .zip file containing the malicious Chrome extension and the commands that modify the browser shortcuts on the victim’s computer. These commands will cause the browser to load the malicious extension at runtime, which guarantees its persistence in Chrome even if it is removed by the victim.
Concomitantly, the computer is infected by the Overlay RAT; however, this infection will only be performed if the language configured on the computer is Portuguese, and if it is not a virtual machine (VM).
Post infection and data theft
After completing the entire infection process, the malware searches the entire operating system for user and password data from email and FTP clients. If identified, this data is obfuscated and sent to a C&C server.
Several C&C servers were identified by the research. Through them, researchers found data that included email client contact lists, Gmail contact lists, HTML pages, email credentials (usernames and passwords), and password lists with apparent origin at the Google Password Manager — later it was possible to confirm that cookie data and Google Chrome’s “LoginData” (SQLite database that saves all user and password information saved in the browser) were in the campaign target. It is noteworthy that “LoginData” data is encrypted, but the author of the malware was able to decrypt it, transforming it into clear text.
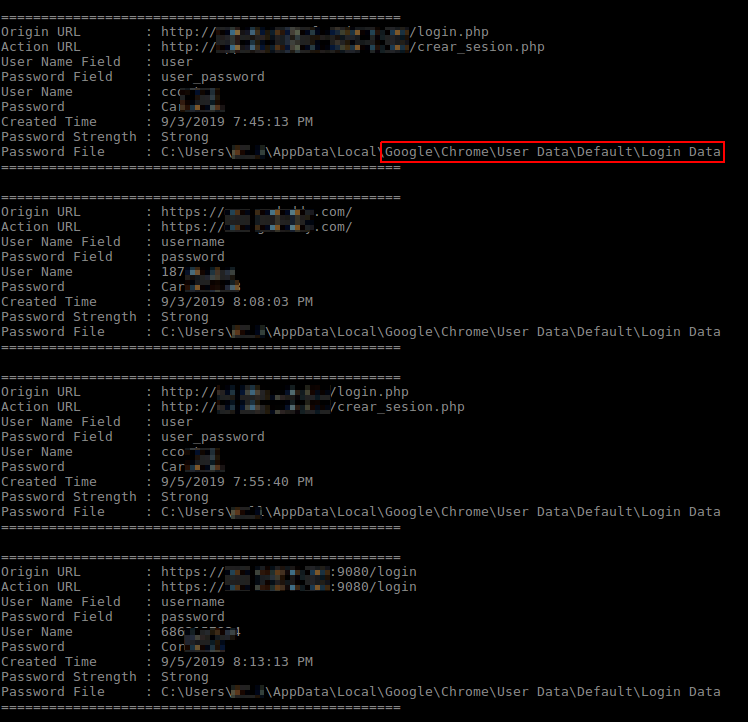
Researchers have identified that each type of captured data is cataloged and separated into files containing identification codes. So far the following codes have been identified:
* HJ — LoginData Chrome *
* HK — Contact List (emails only) *
* HY — Errors reading Chrome database *
Malware analysis made it possible to verify the existence of a mathematical pattern in the obfuscation processes involved in sending data to the C2 server. This way, researchers were able to create a script to unscramble all information captured and sent by the artifact.
Malicious Chrome Extension
The malicious Chrome extension is able to capture and modify data from any site accessed by the browser. Its specific feature, however, is to modify payment slips identified in the browser tabs.
Once the extension identifies a payment slip on a page, it captures and sends it to a C2 where it is modified, and sent back via POST. All this data, both in the request and in the response, is obfuscated.
RAT module
The final module of the malware is a Remote Acces Trojan which is able to perform page overlays for four Brazilian banks.
A DLL (which is imported as soon as the malware is run at operating system startup) has been identified by the researchers as containing the screens used in the overlay process.
IOCs
URLs
mcdonalds[.]promoscupom[.]ml
contadorrebol4-com[.]umbler[.]net
areavip[.]tk
areavip[.]tv
mcdonalds[.]promoscupom[.]cf
www[.]tu-cupon[.]com
tucupon[.]tk
Servers
51.75.95.179
40.121.5.174
18.229.131.184
mexico003[.]ml
mexico003[.]tk
mex002[.]tk
mex002[.]gq
mex002[.]ga
iquksjpablukduwt1[.]tk
fkkavtwfilvpkl2[.]ml
vvcniayccmr3[.]ga
rinlircavgcronx4[.]cf
elbkbbmdmrrg5[.]gq
mqrflkgxinxdgr6[.]tk
yyxfkpffhvo7[.]ml
tjcpccfddsxbr8[.]ga
oupypirjyrqgtlgt9[.]cf
qnpkocplwiyyjaid10[.]gq
yerhqyfrtcyruj11[.]tk
ygwompuaqdfr1[.].ml
qhenujpqooidc13[.]ga
lfxfmphkmal14[.]cf
eaisoxmsvntyvgvk15[.]gq
ukjbwwxifxdutc16[.]tk
skefjkokgpiatfn1[.]ml
yiwmbfddtxltb18[.]ga
rocgjkixhhpiajn19[.]cf
kpsifdyjhkufct20[.]gq
udgetbnvebfhp21[.]tk
rdxabyfohrdh22[.]ml
ovbmiebdqduws23[.]ga
qcotohinmciilh24[.]cf
wcxfejvmdsani25[.]gq
edbxublfkvatmww26[.]tk
psublaugrwdehpih27[.]ml
mibjdulwddkq28[.]ga
bmcmontgtqobq29[.]cf
wdxmkoqgqoh30[.]gq
mmttmiubtvmhok31[.]tk
ntmludavsamydq32[.]ml
sxpaavkkbbyjpdow33[.]ga
xjnkmyprutswjjd34[.]cf
nmrxhhfphiwpd35[.]gq
jvqhflyubweqan36[.]tk
txbnciwpqudbqprp37[.]ml
jhpbostqvxmy38[.]ga
uvwgoaeniuiuf39[.]cf
cbubhrbodjn40[.]gq
wgybeleosem41[.]tk
grvtxkisbyn42[.]ml
qdohpefsnxg43[.]ga
cuuoisoopdebh44[.]cf
uleqbpbnpmjlk45[.]gq
cityrnlotdcnhy46[.]tk
ubhxmjmesiv47[.]ml
velsqnhnbicn48[.]ga
dootdcuydwuiwi49[.]cf
shedxlgaekhiu50[.]gq
ecpmkbfqfhfctl51[.]tk
diaduodhiuh52[.]ml
tlvsgwudxbxpfaww53[.]ga
buauanotgpnwvqdd54[.]cf
tsmpbqpyyrxvb55[.]gq
jjshxdmaalgbtxhd56[.]tk
jpfpbtxqsieryj57[.]ml
hbudtuxmkofi58[.]ga
mrqrdrbhhpwexn59[.]cf
clmbkxslunmkwyy60[.]gq
mthhpdinkqtskio61[.]tk
wpftxqsaeryj62[.]ml
Files
Filename: Binary.fgak8ktkkyo7q3xl5.vbs
MD5: fc9b0cfc56dfe1de05e17e907555ae22
Sha1: 3b7aa37129c6fcb91a5e9b6141589e0da5c88a4f
Sha256: 344f88b12b3d0cb8649a58428cd7e9d8ca37ac380a92e7673fabee724d23fc44
Filename: Cupom_MJ738J3JS.msi
MD5: 25eb88342a0492fc342b1b0d12925e96
Sha1: 3662723aff984bf76e306b8eb9be6418bd02f666
Sha256: 1525be6d2587acc232832241c14ee154579c89a1bbd0ea138a12bd0ab54c6ef3
Filename: Cupom_MJ738J3JS.zip
MD5: 49b6625ae11c6d6579ed358acd51adcb
Sha1: c4daeaeca119b5f56a0bfbb2232967f7c40ad006
Sha256: a1c2810a98789cee93d2b306c863d24f0cb47d85b37e1a8b2491e9a62f6063a8
Filename: fvcgTL.zip
MD5: a376e397d3d24c053b304efe12bef22b
Sha1: aada56c5de0618e7da8bfeb632f1fc0f68eb84f0
Sha256: 9dbc72a8ab9549812ff38fe12336d16fa10c614c3eb26df613e9a71376b82216
Filename: ky419.zip
MD5: 913673c19cb73cab4ebe9b156cc3a943
Sha1: 4b68ed8670293607b793895cf00acaaadff11ae8
Sha256: a839e7f5cdfd75eeb0147ccb44e251e320bf52b698080433bee02cac272a8888
Filename: MImpZ.vbs
MD5: c6b0a821f0c2656f2f8903b82bcef1c5
Sha1: 35e5689728d1a1dbb6974c8b67782ac4e1299d5b
Sha256: 638be4d5a470fb8581e0eceee1999ce2b972f16042b5c76d9bd01f104eaf205a
Filename: OgawC142.zip
MD5: b2099d3b4ee91b93e007349e6b773273
Sha1: 8e9b00025ae466bf95848f36784132d8d0cd56ab
Sha256: a34b0e5de20abfa64e520f8df6dd61c4b7f417cf24c57ca4130a6725238d6478
Filename: oois7yl1w.zip
MD5: d120778ef82f5432216fc931be3c4ba7
Sha1: 514e05b08616086205cdd83267d674d421a7d033
Sha256: 30c6c25555a0573690d60334141cb7339be91de16a547f8f288b407032da2929
Filename: pk6pf2x6s4a1xn.zip
MD5: 2ea13aa1eb17dc9baa3ed175cdfaa15b
Sha1: 847a111a87af203f4ad75cfeff01875d4a761323
Sha256: b001ff0c904fc2506bfb56269060570c442888dd84a56b8ca874d7ed41a1d1b4
Filename: at2/at23.js
Md5: 9f0fa7cc3f6d3c3b5d5136613cfee4a9
Sha1: 0b7221a3845a66ab3a7f35c4f6475fd0743119f0
Sha256: 528ca8e0f620d2899255158661d065b9612e1783e0e20f0b8411dce430726d7f
Filename: at2/at24.js
Md5: 572f1c06b8004d560d8817570584112a
Sha1: 61cde2b9c0d663c34f994de81020ea1841ac5433
Sha256: e0612e763841eda3f75690a457f952e43fdb2bce3d9bcac09177f1de62faede3
Filename: at2/eventPage.js
Md5: d41d8cd98f00b204e9800998ecf8427e
Sha1: da39a3ee5e6b4b0d3255bfef95601890afd80709
Sha256: e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
Filename: at2/jquery-3.1.1.min.js
Md5: e071abda8fe61194711cfc2ab99fe104
Sha1: f647a6d37dc4ca055ced3cf64bbc1f490070acba
Sha256: 85556761a8800d14ced8fcd41a6b8b26bf012d44a318866c0d81a62092efd9bf
Filename: at2/manifest.json
Md5: e9fb6decb5b4569177b1ce166fb151d3
Sha1: 828fa1b2d3733846ea9c9cc195beb8be6d9756bb
Sha256: 6ce8d3306cf0b504de0571bfea3fabe08061379a01ef6fbaad3021243a7f35b0
Filename: OgawC142/eventPage.js
Md5: d41d8cd98f00b204e9800998ecf8427e
Sha1: da39a3ee5e6b4b0d3255bfef95601890afd80709
Sha256: e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855
Filename: OgawC142/GvpqXN.js
Md5: 37ff95b74df1c86dfff51650d39a3783
Sha1: a6b5528726c7ff3f4b55194baf19347e93e158de
Sha256: e52b8806a78db9f69d1c19e1b38ef4db133b3e42220bd49839d1c705b707c69b
Filename: OgawC142/jquery-3.1.1.min.js
Md5: e071abda8fe61194711cfc2ab99fe104
Sha1: f647a6d37dc4ca055ced3cf64bbc1f490070acba
Sha256: 85556761a8800d14ced8fcd41a6b8b26bf012d44a318866c0d81a62092efd9bf
Filename: OgawC142/manifest.json
Md5: 15a10b06da1d05afcf2abdee82c99a08
Sha1: 5f7b221485291ef49ded3a2fc1f54f4eb025d597
Sha256: 0e93f8ac443cfb3306eeb149d3881f8eebdafc7c669795e41b444d4c792d36d8
Filename: OgawC142/VnBeAv.js
Md5: b8a51bd551d1b4a2b88310e5d3a2a665
Sha1: e11a17b1f76ccc6db36896fb133e6db833215ad1
Sha256: ee311315b364dbed3ebdc539f272afc487943a8be4500aef26a1a25429517119
Filename: oois7yl1w/ecy.dll
Md5: 95b2f86dee18e2883ee1429ef2f1a734
Sha1: c957732b11181ab13dc27943ed5f2f65d047a4f8
Sha256: 0dbd022a78a38ca67ee56551d72e3c92c0f728943fef4ab76b65e1fc73837a56
Filename: oois7yl1w/hfyhbiu.dll
Md5: 8818909bfbc9d427a31fbd12c7a2157e
Sha1: 5b228f099b167a190c8fe280efcb47a9cae1fab9
Sha256: a857a813390b7d1e81ca9b1929c0b2031fd13bd8f7bb8444aea3ea3f5461be67
Filename: oois7yl1w/kqvwo1mhrg.dat
Md5: 1b949adf1316001a392e19416e073bc5
Sha1: c1726c441eea972f6f79f8c2aba1838fb9680d30
Sha256: 0213cbb44603c42667abdbd6300e9352201fbb0a71d11908495398fee9eb76c5
Filename: oois7yl1w/ky3ubl.dll
Md5: 061440d1c00a4d78cea1cbd1701afb5d
Sha1: a6303d49222490333ee6e7ecf721fa06218961b2
Sha256: 9622e80bec193c49038ff70e1db7a11592d4282a9f0089a03ce69889f839dd8f
Filename: oois7yl1w/lgfm2w8.dll
Md5: f3f571288cde445881102e385bf3471f
Sha1: d3222d7f6d97b0a8e144760151782e0721f18ded
Sha256: a6bd9fd8e9d1dba14334db442b7fd6bb06f58201db720a7aa006530f76fc26eb
Filename: oois7yl1w/libeay32.dll
Md5: de484d5dafe3c1208da6e24af40e0a97
Sha1: 3e27b636863fefd991c57e8f4657aded333292e1
Sha256: 007342c6b9b956f416f556b4bd6f1077e25bd077cc4f4ac136e3fccb803746e3
Filename: oois7yl1w/ltqd7iy4.dll
Md5: 3a44b86aadcce51f87e28aae98e58f16
Sha1: b08ff9dd23bf1d38db2fb04c1ecf8b0e4844c6bc
Sha256: 8c17300d9d05ffe05ced7cc35e62d7e86a9b7534386cf7bd6a9151cb321beb8e
Filename: oois7yl1w/o2gd3fq6hm.exe
Md5: c648901695e275c8f2ad04b687a68ce2
Sha1: 892503b20247b341cfd20dda5fdacfa41527a087
Sha256: 3fa4912eb43fc304652d7b01f118589259861e2d628fa7c86193e54d5f987670
Filename: oois7yl1w/ssleay32.dll
Md5: 284e004b654306f8db1a63cff0e73d91
Sha1: 7caa9d45c1a3e2a41f7771e30d97d86f67b96b1b
Sha256: 2d11228520402ef49443aadc5d0f02c9544a795a4afc89fb0434b3b81ebdd28c
Filename: oois7yl1w/t5wyfwne8b8k4.dll
Md5: cde01c58778c9a3b26f3e3f2689f6614
Sha1: 2009aa23f15ea6e8e0d11e439bc7e2469da77f84
Sha256: 24456d429b721a6ebed691de24473d38e1608a50ceb8e8b970263670cd2aa89a
Filename: oois7yl1w/winx86.dll
Md5: 87f9e5a6318ac1ec5ee05aa94a919d7a
Sha1: 7a9956e8de89603dba99772da29493d3fd0fe37d
Sha256: 7705b87603e0d772e1753441001fcf1ac2643ee41bf14a8177de2c056628665c
Filename: pk6pf2x6s4a1xn/alsirwny5.dll
Md5: 824cd16f3c5db6a8ad0f314a8dff0c2e
Sha1: 84a54737a6c7222f02726fe3cc8cc9efa1df2d51
Sha256: 2f373cb24511ca1a1035bc94d4da28329814b9c2573d16f2a06319933eab8447
Filename: pk6pf2x6s4a1xn/bxyhmkl.dll
Md5: 50ce27d2a396e14300a2524e2ec8b982
Sha1: fa23428ac04a14b18ae46b71bc4bcae2636e6f57
Sha256: 4afa84efec6dbe05804216dc5ff716e5eb0e7fe95fd29709b3e8e7821787b3ed
Filename: pk6pf2x6s4a1xn/lxpvcq.dll
Md5: 866d9af9277e7928830454f76b12539d
Sha1: cad44533d3c3996e56c6125caf465ea7809a7b31
Sha256: 6c79b4be1b63b349015404ba3ce25c4cecfa679374ec269623c8ce949c42b656
Filename: pk6pf2x6s4a1xn/rmkqemobm.exe
Md5: 85409467e4bbd807309bce052a86e8ad
Sha1: e21a5f1d1ba0b52b0ab4ac55a588af68f6f60f8a
Sha256: 384294ef6760f53b7b2c9c5ff79a0db96b5ae7ac9f8848d188a6959b1b4011e1
Filename: pk6pf2x6s4a1xn/xld.dll
Md5: 961d95d29acee4291dfdbbcb7851895c
Sha1: d33228b6c0ddf6c5b9bac69cb148e2b7ff9eb742
Sha256: a4377478ff1dd7e85516187b9cf09d514e2656349991e138ed957b8725b17938
