Researchers at security firm WhiteScope have released a report with the results of an extensive review of vulnerabilities found in different pacemaker models. The study, which involved seven devices with wireless communication systems developed by four different manufacturers, revealed the existence of more than 8,000 vulnerabilities in libraries developed by third parties potentially exploitable in cyber attacks.
To better understand these risks, it´s important to understand what are those devices and how they work.
What is a pacemaker?
Pacemakers are cardiac rhythm management systems (CRMs) that are used to treat arrhythmias through the emission of electrical impulses.
The models studied by WhiteScope are composed of four elements, namely:
- The pacemaker devices (which is implanted surgically in the patient)
- A programmer — a computer adapted to the evaluation and calibration function of the device
- A home monitoring system
- Support/update infrastructure
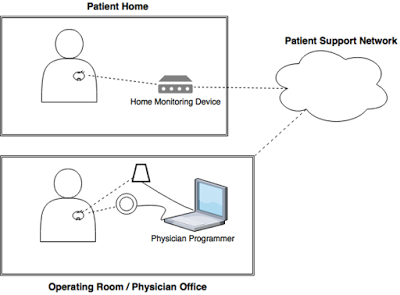
In one of the models studied — shown in the diagram — the implanted device sends data to the system installed in the patient’s residence via radiofrequency. This data is sent to the manufacturer’s cloud servers and then sent to the programmer — installed in the doctor’s office — where the necessary calibrations are periodically made in the pacemaker. The programmer communicates with the pacemaker using a magic wand that is placed over the region where the device was implanted.
What are the risks that threaten pacemakers?
The study shows that “despite efforts by the the Food and Drugs Administration (FDA) to streamline routine cyber security updates” all programmers reviewed have outdated software versions. The researchers identified in the equipments more than 300 libraries developed by third parties responsible for much of the more than 8000 vulnerabilities found that can be exploited in cyber attacks.
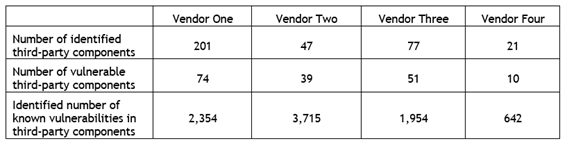
Other risk factors include:
- Patient data is stored unencrypted in programmers on hard drives and on removable devices such as SD cards.
- The programmers analyzed do not require any form of authentication (login or password) to access the control program
- Any programmer from a particular manufacturer can communicate with all pacemakers developed by the same company
- Some newer models of programmers can communicate with pacemakers over long distances using RF, dispensing the magic wand
Finally there is the fact that the researchers were able to perform the tests with equipment acquired on eBay, without any form of control by the manufacturers. “All manufacturers had devices available on the auction site. A programmer costs between $ 500 and $ 3000, a home monitoring system costs between $ 15 and $ 300 and pacemakers were found to be between $ 200 and $ 3,000. “
What is the number of pacemaker users in the UK and Brazil?
In Brazil, more than 240,000 surgeries were performed between implants and general maintenance between 1994 and 2014. A worldwide census of pacemakers and defibrillators conducted in 2009 accounted for 136 implants per million inhabitants in the country.
In the UK data from the 11th edition National Audit of Cardiac Rhythm Management Devices show England and Wales with a base of 600 implants per million and Northern Ireland with a base of 432 implants per million between 2015 and 2016.
