Por Bianca Oliveira
1. Introduction
Remote access trojans (RATs) are a type of malware that allows the target to be controlled remotely. The list of known RATs is quite extensive, but there are new threats emerging all the time. However, it’s not uncommon to see old RATs that are still active, such as Gh0st RAT, a remote administration tool aimed at Windows environments, created in 2008 by a Chinese group called C. Rufus Security Team.
Since the publication of its source code in 2008, Gh0st RAT has been used as the basis for the production of several variants, which have been used in campaigns against entities from many sectors, mainly government, telecommunications, finance, education and health.
2. Characteristics and functionalities
2.1 Infection
The infection chain begins with sending phishing emails (T1566.001) containing a malicious file attachment which, when executed, infects the target’s machine with Gh0st RAT.
The infection process involves four components, namely a malicious DLL, a binary to be executed at kernel level, a dropper and a Windows application responsible for interacting with the attacker’s remote infrastructure through which the Gh0st RAT operator controls compromised hosts.
The DLL is installed on the target as a Windows service and contains the malware’s toolkit. When started, the service registers the infected machine with the command and control server and waits for instructions from the adversaries.
The DLL is configured and installed by the dropper, which prepares the compromised host to run the Gh0st RAT. The installation is done using the DLL Side-Loading technique (T1574.002), so that a legitimate executable is exploited to operate as a dropper, loading the malicious DLL.
The dropper also installs the kernel-level binary, which is executed at system startup and which resets the SSDT (System Service Dispatch Table), a table containing the addresses of the kernel functions running on Windows. The threat manipulates the SSDT to allow the execution of code with kernel privileges.
2.2 Communication
One of the main characteristics of the Gh0st RAT is present in its communication between the compromised host and the command and control server, considering that the header of the packet exchanged between them always begins with a 5-byte “magic word”, which in its default configuration is “Gh0st”. It’s also standard for malware to compress the packet payload using the zlib library.
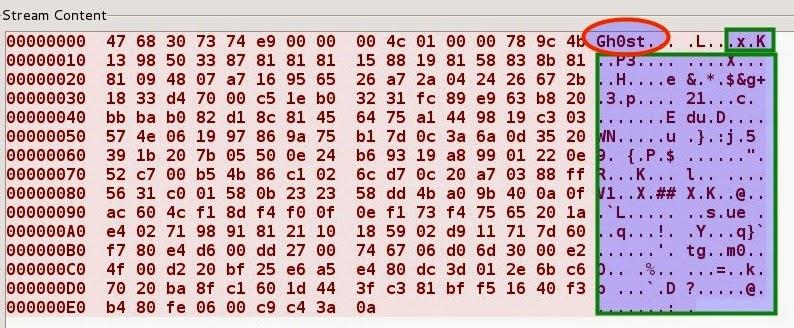
Some of the RAT’s functions include:
Controlling the compromised machine.
Remote file download.
Real-time keylogging (T1056.001)
Webcam access and microphone recording (T1125 and T1123).
The malware has also been observed establishing shells for remote command execution (T1059.003), clearing event logs (T1070.001), creating services to establish persistence (T1543) and encrypting TCP communications to avoid detection (T1573.001).
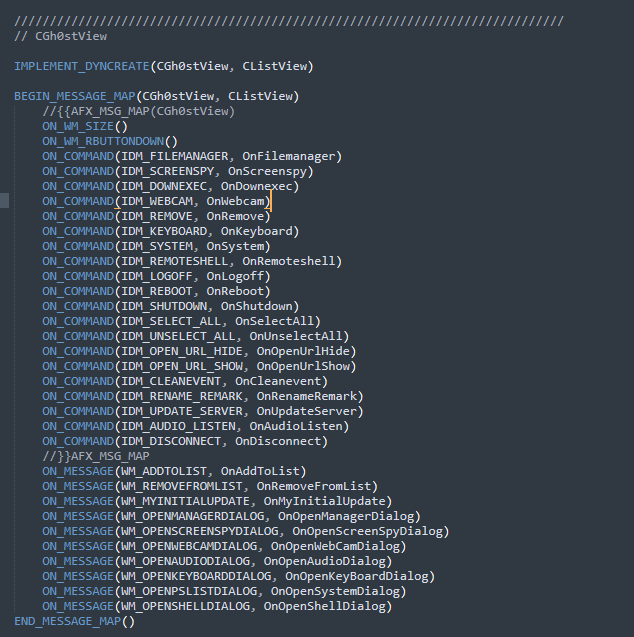
3. Campaigns
The first documented use of Gh0st RAT on a large scale took place in 2009, in a spying campaign known as GhostNet against Tibetans in exile in various countries.
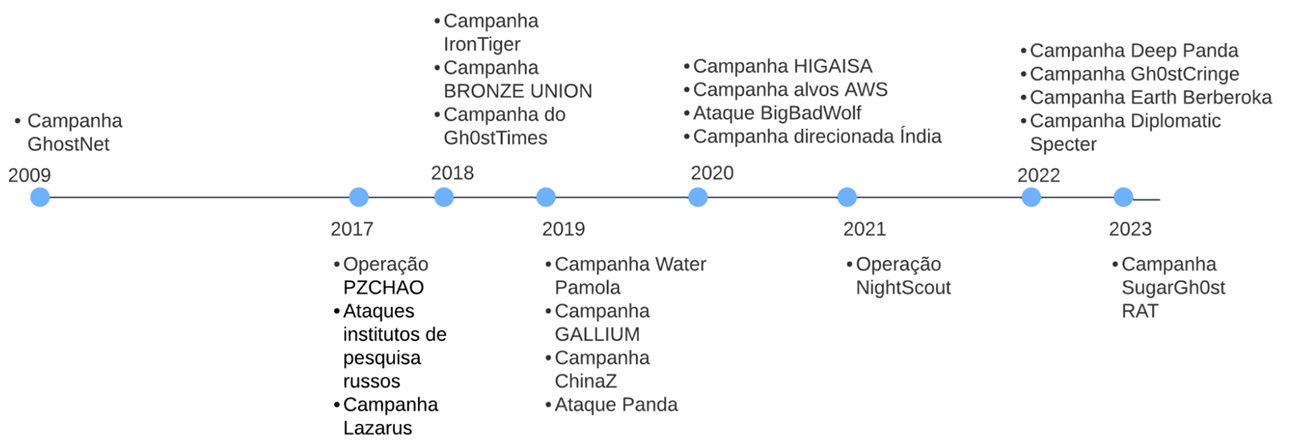
After this period, the malware was observed in isolated attacks and was seen again in large-scale attacks in 2017, such as the Operation PZCHAO led by the IronTiger group and the series of attacks targeting Russian research institutes, in which a variant of Gh0st RAT called “BackDoor.Farfli.130” was used.
Also in 2017, Proofpoint researchers identified the use of a Gh0st RAT variant in a campaign by the Lazarus group, which was used to spread the PowerRatankba backdoor. This was the first documented use of this RAT by North Korean threat agents, since until then the malware had only been observed in use by Chinese attackers.
In March 2018, the IronTiger group was again seen using a variant of the malware, this time in a campaign aimed at stealing cryptocurrencies. In the same year, another variant of RAT was used by the BRONZE UNION gang and a variant called Gh0stTimes was employed by the BlackTech group against Japanese organizations.
In 2019, two campaigns involving variants of the Gh0st RAT were identified. The first, dubbed Water Pamola, targeted e-commerces in countries in Europe, Asia and Oceania, spreading the Gh0stCringe variant. The second, conducted by the GALLIUM group, targeted telecommunications providers to distribute the QuarkBandit.
Also in 2019, two other campaigns were documented, these disseminating Gh0st RAT variants which have some differences when compared to the original Gh0st RAT code, but which were not given a distinct name by the researchers who documented them. The first of these was conducted by the ChinaZ group, known for launching DDoS attacks against Windows and Linux systems, while the second operation was conducted by the Panda threat agent resulting in the theft of thousands of dollars in cryptocurrencies.
In early 2020, the HIGAISA group spread an unnamed variant of the Gh0st RAT via phishing messages with a theme related to the COVID-19 pandemic. In March of the same year, Sophos researchers identified the infection of servers hosted on AWS with variants of the malware, which had versions for Windows and Linux systems. Also in 2020, two variants of the malware were identified, one of which was called BigBadWolf and the other, although unnamed, was used in attacks against institutions in the banking, health and agribusiness sectors in India.
In January 2021, another variant of the Gh0st RAT was distributed in the NightScout operation, aimed at compromising the NoxPlayer emulator update mechanism for users in Asia.
The following year, in March, Fortinet researchers detected a campaign by the Deep Panda group exploiting the Log4Shell vulnerability in VMware Horizon servers to spread a Gh0st RAT variant called MILESTONE. Also in March, ASEC identified a campaign with this threat targeting MS-SQL servers to deploy the Gh0stCringe variant.
In April 2022, the Earth Berberoka group conducted attacks against gambling websites, distributing another Gh0st RAT variant. At the end of 2022, an operation dubbed Diplomatic Specter targeted political entities in the Middle East, Africa and Asia through two variants of the malware, called TunnelSpecter and SweetSpecter.
In 2023, a malware variant called SugarGh0st RAT was employed in campaigns targeting the Ministry of Foreign Affairs of Uzbekistan and also individuals in South Korea.
4. Main variants
Although the original Gh0st RAT has well-defined characteristics, such as the magic word in the header or the compression of packet data with the zlib library, it’s still notable that there are a number of variants, which retain most of the standard features but make changes, such as adding and/or removing features.
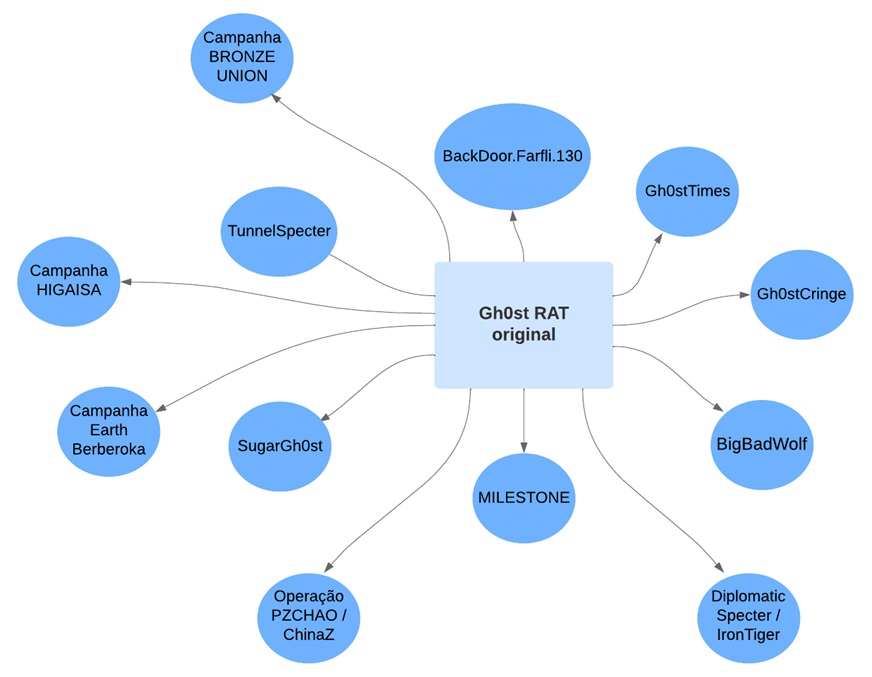
Among the differences between the variants, we can mention the one used by the BRONZE UNION group, which randomized the standard Gh0st RAT header to obscure network traffic, and also the version distributed by the HIGAISA gang, which compressed the packet data with the LZO library instead of zlib.
There are also variants that have been added, such as the one used in the Earth Berberoka campaign, which contained a destructive feature that replaces the Master Boot Record (MBR) to display a message.
4.1 Other features of the variants
BackDoor.Farfli.130: has fewer features compared to the original Gh0st RAT, but is capable of obtaining information about the system.
Gh0stTimes: maintains most of the typical features of Gh0st RAT, modifying only the format of the packet used in communication and also includes two new commands related to operating with files.
Gh0stCringe: much of its source code is identical to that of the original RAT. However, it has exclusive commands and also changes the “magic word” in the header of its packages from “Gh0st” to “xy”.
BigBadWolf: is made up of portions of the Gh0st RAT source code, but with exclusive binaries and also includes changes to callbacks in an attempt to avoid identifying communications that are characteristic of the Gh0st RAT.
MILESTONE: has the standard features of the original malware, but also has its own commands, in addition to modifying original commands and also not compressing its communication with the attacker’s server, which would usually be done via the zlib library.
SugarGh0st RAT: the header of this variant’s network packets is now 8 bytes instead of 5 bytes, and it also has new features such as custom commands and the ability to search for Open Database Connectivity (ODBC) registry keys.
Tunnel Specter: maintains part of the original RAT code, but includes its own features, such as the implementation of encryption and data extraction using the DNS tunneling technique.
5. Conclusion
Despite having been created 15 years ago, Gh0st RAT is still one of the most relevant remote access Trojans on the cyber scene, being used in campaigns that range from spreading ransomware to including compromised devices in large botnets.
Measuring the impact of malware can be challenging, considering that there are several variants, especially since its code has become public and can be used by any threat operator.
In addition, the infection process includes techniques to avoid detection and make it easier to install the malware, such as the Side-Loading DLL (T1574.002), which may be a feature related to the preference of attackers to continue using Gh0st RAT.
References
A PEEK INTO BRONZE UNION’S TOLLBOX. Secureworks. Available at: <https://www.secureworks.com/research/a-peek-into-bronze-unions-toolbox> Accessed on: June 20, 2024.
APT Group Planted Backdoors Targeting High Profile Networks in Central Asia. Avast. May 14, 2020. Available at: <https://decoded.avast.io/luigicamastra/apt-group-planted-backdoors-targeting-high-profile-networks-in-central-asia/> Accessed on: July 9, 2024.
ChinaZ Revelations: Revealing ChinaZ Relationships with other Chinese Threat Actor Groups. INTEZER. January 7, 2019. Available at: <https://intezer.com/blog/research/chinaz-relations/> Accessed on: May 1, 2024.
Cloud Snooper Attack Bypasses AWS Security Measures. Sophos. March 2020. Available at: <https://news.sophos.com/en-us/2020/02/25/cloud-snooper/> Accessed on: July 9, 2024.
COVID-19 and New Year greetings: an investigation into the tools and methods used by the Higaisa group. PTSecurity. June 4, 2020. Available at: <https://www.ptsecurity.com/ww-en/analytics/pt-esc-threat-intelligence/covid-19-and-new-year-greetings-the-higaisa-group/> Accessed on: July 8, 2024.
Cryptocurrency miners aren’t dead yet: Documenting the voracious but simple “Panda”. Cisco Talos. September 17, 2019. Available at: <https://blog.talosintelligence.com/panda-evolution/> Accessed on: 9 jul 2024.
Decoding network data from a Gh0st RAT variant. NCC Group. Apryl 17, 2018. Available at: <https://research.nccgroup.com/2018/04/17/decoding-network-data-from-a-gh0st-rat-variant/> Accessed on: July 29, 2024.
Deep-dive: The DarkHotel APT. Bushido Token Threat Intel. June 14, 2020. Available at: <https://blog.bushidotoken.net/2020/06/deep-dive-darkhotel-apt.html> Accessed on: July 8, 2024.
Digitally Signed Malware Targeting Gaming Companies. BlackBerry. October 18, 2016. Available at: <https://blogs.blackberry.com/en/2016/10/digitally-signed-malware-targeting-gaming-companies> Accessed on: July 11, 2024.
GALLIUM: Targeting global telecom. Microsoft. December 19, 2019. Available at: <https://www.microsoft.com/en-us/security/blog/2019/12/12/gallium-targeting-global-telecom/> Accessed on: July 9, 2024.
Gh0st RAT Part 2: Packet Structure and Defense Measures. INFOSEC Institute. February 19, 2015. Available at: <https://www.infosecinstitute.com/resources/malware-analysis/gh0st-rat-part-2-packet-structure-defense-measures/> Accessed on: July 17, 2024.
Gh0st RAT: Complete malware analysis – Part 1. INFOSEC Institute. February 11, 2015. Available at: <https://www.infosecinstitute.com/resources/malware-analysis/gh0st-rat-complete-malware-analysis-part-1/> Accessed on: July 17, 2024.
Gh0st RAT. MITRE ATT&CK. Available at: <https://attack.mitre.org/software/S0032/> Accessed on: June 11, 2024.
Gh0stCringe RAT Being Distributed to Vulnerable Database Servers. 16 Março 2022. Available at: <https://asec.ahnlab.com/en/32572/> Accessed on: 29 jun 2024.
Hunting and Decrypting Communications of Gh0st RAT in Memory. CYSINFO. Published in 2016. Available at: <https://cysinfo.com/hunting-and-decrypting-communications-of-gh0st-rat-in-memory/> Accessed on: July 17, 2024.
Malware Gh0stTimes Used by BlackTech. 04 Outubro 2021. Available at: <https://blogs.jpcert.or.jp/en/2021/10/gh0sttimes.html> Accessed on: June 29 2024.
New APT Group Earth Berberoka Targets Gambling Websites With Old and New Malware. TrendMicro. April 27, 2022. Available at: <https://www.trendmicro.com/pt_br/research/22/d/new-apt-group-earth-berberoka-targets-gambling-websites-with-old.html> Accessed on: June 22, 2024.
New Milestones for Deep Panda: Log4Shell and Digitally Signed Fire Chili Rootkits. March 30, 2022. Available at: <https://www.fortinet.com/blog/threat-research/deep-panda-log4shell-fire-chili-rootkits> Accessed on: June 29, 2024.
New SugarGh0st RAT targets Uzbekistan government and South Korea. Cisco Talos. November 30, 2023. Available at: <https://blog.talosintelligence.com/new-sugargh0st-rat/> Accessed on: June 21, 2024.
North Korea Bitten by Bitcoin Bug: Financially motivated campaigns reveal new dimension of the Lazarus Group. Proofpoint. December 19, 2017. Available at: <https://www.proofpoint.com/us/threat-insight/post/north-korea-bitten-bitcoin-bug-financially-motivated-campaigns-reveal-new> Accessed on: May 21, 2024.
Open-Source Gh0st RAT Still Haunting Inboxes 15 Years After Release. Cofense. April 24, 2023. Available at: <https://cofense.com/blog/open-source-gh0st-rat-still-haunting-inboxes-15-years-after-release/> Accessed on: May 21, 2024.
Operation Diplomatic Specter: An Active Chinese Cyberespionage Campaign Leverages Rare Tool Set to Target Governmental Entities in the Middle East, Africa and Asia. Palo Alto. 23 Maio 2024. Available at: <https://unit42.paloaltonetworks.com/operation-diplomatic-specter/> Accessed on: June 11, 2024.
Operation NightScout: Supply-chain attack targets online gaming in Asia. ESET. February 1, 2021. Available at: <https://www.welivesecurity.com/2021/02/01/operation-nightscout-supply-chain-attack-online-gaming-asia/> Accessed on: July 21, 2024.
Operation PZCHAO. Bitdefender. Available at: <https://www.bitdefender.com/blog/labs/operation-pzchao-a-possible-return-of-the-iron-tiger-apt/> Accessed on: July 5, 2024.
RAT used by Chinese cyberspies infiltrating Indian businesses. SEQRITE. December 18, 2020. Available at: <https://www.seqrite.com/blog/rat-used-by-chinese-cyberspies-infiltrating-indian-businesses/> Accessed on: July 11, 2024.
Study of targeted attacks on Russian research institutes. Dr.WEB. April 2, 2021. Available at: <https://st.drweb.com/static/new-www/news/2021/april/drweb_research_attacks_on_russian_research_institutes_en.pdf> Accessed on: May 21, 2024.
The many faces of Gh0st RAT. Norman ASA. 2012. Available at: <https://www.yumpu.com/en/document/view/11503105/the-many-faces-of-gh0st-rat-norman> Accessed on: July 10, 2024.
Tracking GhostNet. The SecDev Group. 29 Março 2019. Available at: <https://pt.scribd.com/document/625295908/TRACKING-GHOSTNET-www-amarbooks-com> Accessed on: July 11, 2024.
Water Pamola Attacked Online Shops Via Malicious Orders. 28 Abril 2021. Available at: <https://www.trendmicro.com/en_us/research/21/d/water-pamola-attacked-online-shops-via-malicious-orders.html> Accessed on: May 21, 2024.
