Threat Intelligence Team
The strong growth of Brazilian e-commerce, marked by a business evolution rate of more than 70% in 2020, results from a change in the behavior of people and organizations faced with the needs of the current pandemic. This change also brought an evolution in the tactics and techniques used by criminals operating in the mode of Phishing-as-a-Service (PHaaS). In this article, we present the main SPAM tools and services used in the dissemination of malicious links, especially those of fake online stores, which were observed in chats and private groups, as well as the old tactics that are still popular in Brazilian cybercrime, outlining an overview of the infrastructure used by criminals to reach as many victims as possible efficiently.
Overview about fake stores
A fake store is way more than a website with a similar design to the original e-commerce. It’s a web application intended for hosting fake pages that copy the brand of major Brazilian retailers. In this business model, some criminals develop and commercialize these structures and those who buy or rent them, which can be a set of fake pages or a single page linked to a specific brand.
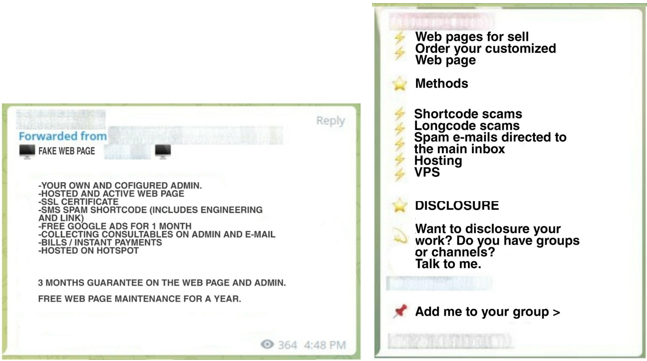
In 2018, Tempest’s Threat Intelligence team uncovered the workings of an entire PHaaS operation targeting the marketing of fake stores. The campaign aimed to collect credit card and personal information from victims and profit from bill payments. This research revealed one of the first infrastructure models to offer fraudsters a range of support services, such as resources to communicate with victims until the bill is paid.
In this regard, what differentiates a fake store from a regular phishing store is that they do not limit themselves to collecting personal data and credentials. Criminals also provide bills from purchases with similar value to those made in authentic stores, making victims pay for real products or services they will enjoy. These bills can also work in digital bank accounts created and used by criminals as an “straw man account” – that is, registered with someone else’s information – to receive payments.
As expected, the success of this kind of scam is directly linked to the criminal’s ability to create similar content to the original websites. Because of this, the registered domain must appeal to the victim’s curiosity with social engineering techniques linked mainly to seasonality, like commemorative dates such as Mother’s Day or Black Friday, for example. Another technique approach is the traditional typographic similarity to the original domains using methods such as cybersquatting and typosquatting.
SPAM Services and Tools
To get the fake content to its targets, criminals rely on specific SPAM dissemination tools and services to boost their malicious campaigns. This infrastructure is often easily accessible and low cost, as we’ll demonstrate below.
Texting
One of the primary means that, despite being old, is still widely used to reach many users is sending SPAM texts via Short Message Service (SMS) or email. This type of service uses various social engineering techniques to attract the attention of victims, including fake fraud prevention alerts.
Shortcode and long code numbers
In the context of smishing (SMS phishing), one of the main recommendations against this type of approach is to check the sender’s number, since specific systems, like those legitimate marketing campaigns, usually use services that automate the triggering of messages and use a shortcode pattern with five or six digits. However, the packages’ offer with a limited amount of shortcode SMS can be easily found on the Internet, so the criminals have also started using this type of service, aiming to increase the credulity of campaigns.
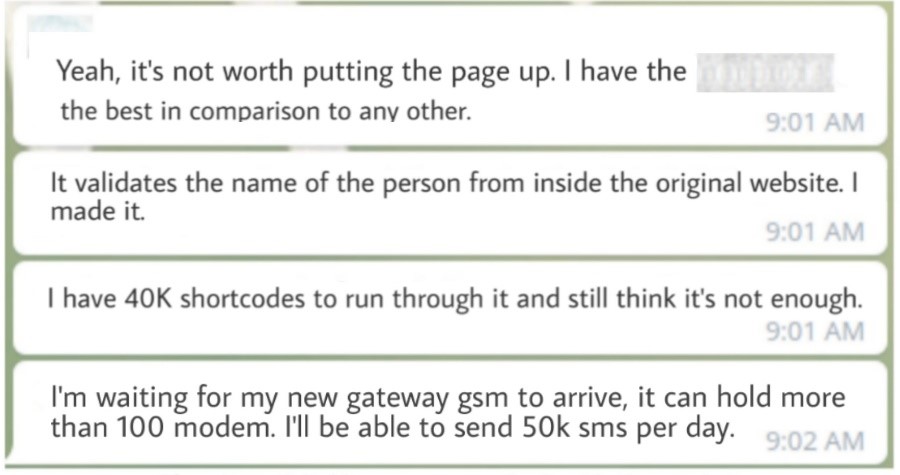
In a private chat group focused on fake stores, we identified conversations about the criminal use of shortcodes, including a video showing the work of a bulk-sending script developed by one of the group members. The tool uses the API of a legitimate SMS marketing service to trigger messages.
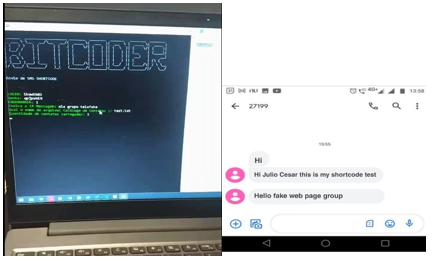
Image: Tempest
The difference in using shortcode SMS instead of long code is the possibility of sending unlimited SMS per second. With the long code, it is only possible to send a single message simultaneously. Another difference in the use of long code is the representation based on numbers consisting of 9 to 11 digits, the standard format of a traditional phone line, which can easily make the victim suspicious.
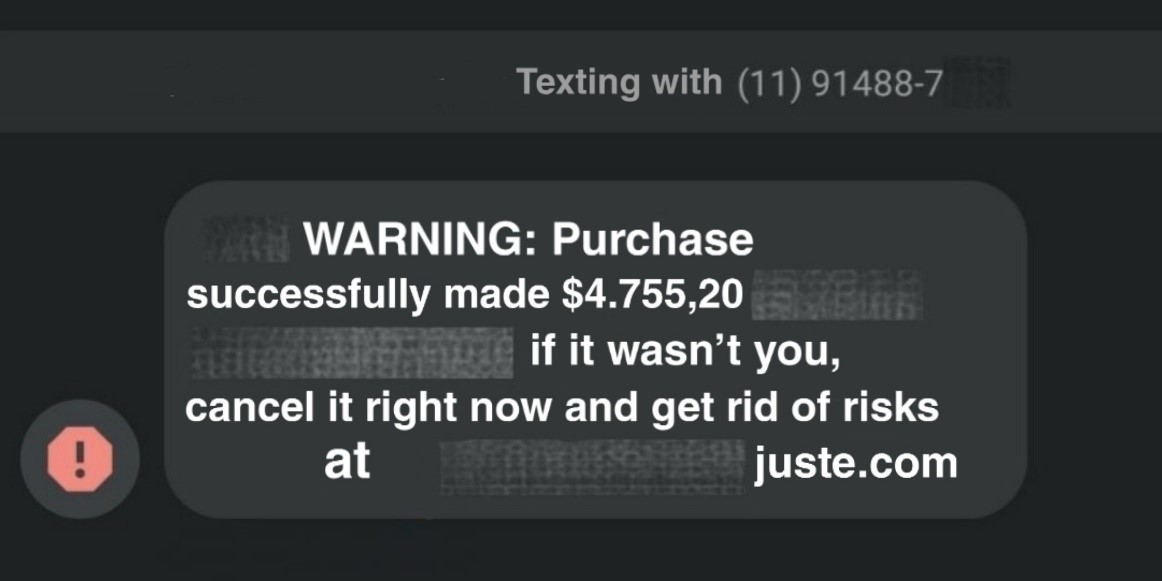
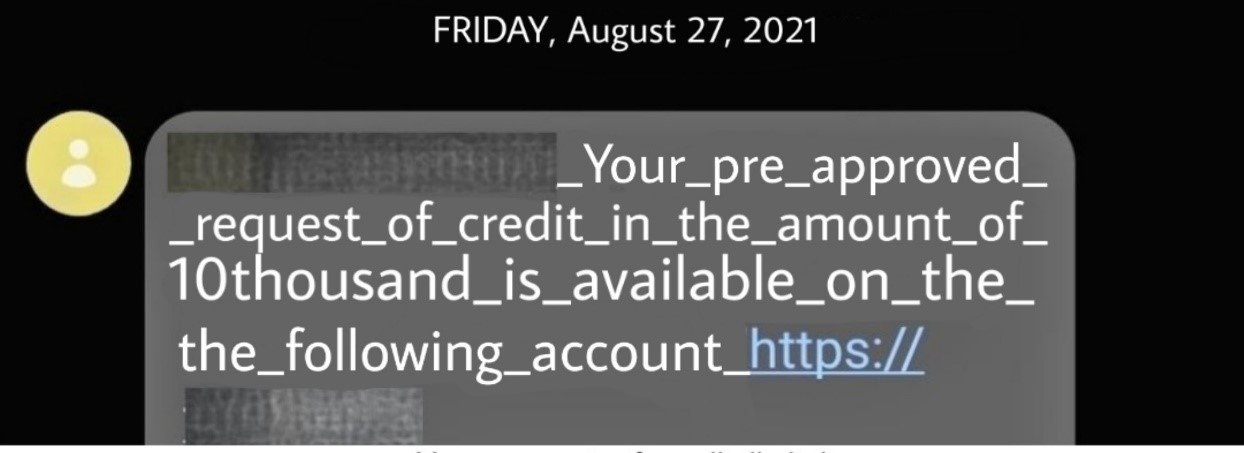
In these texts, it’s also possible to identify the use of characters or punctuation marks such as “_” or “.” to replace the space between words. According to research released by Kaspersky in early 2021, this technique is used to prevent malicious messages from being detected by carrier blocking filters.
SIM card trap
Another mechanism used in fraud groups is the SIM card trap, a kind of “farm” of connected modems that send a significant amount of SMS messages. To set up this infrastructure, criminals buy several prepaid SIM cards with unlimited SMS sending support. The messages are sent to a pre-defined list of numbers with the help of text message management software, such as SMS Caster. To work correctly, the user must configure the sender’s number, which can be in short or long code format.


Scripts
The most common techniques used to send phishing emails are already widespread in the security community. However, criminals are always seeking to diversify these techniques to go through detection systems, an example being the scanning of weaknesses in the Simple Mail Transfer Protocol (SMTP), which allow, among other things, the manipulation of the sender field in the email header. Despite implementing protection measures to avoid these openings on security, there are script-based tools whose primary function is to bypass anti-SPAM mechanisms and allow the mass sending of malicious messages.
One of the tools is the SMTP cracker, a script that uses credentials from legitimate email sending services to trigger malicious messages. Consequently, the victim receives phishing without it being classified as malicious, being delivered to the promotion or social mailbox.
The SMTP cracker is just one of many SPAM automation scripts that can be purchased on the Internet. There are specialized websites that provide these mechanisms with multiple functionalities and methods of dissemination, including techniques that aim to prevent malicious emails from being directed to the SPAM box, such as sending from numerous locations, reusing the visual identity of the original companies, and using random words in the sender’s name and email address field.
Third-party services
Another approach used by criminals is bulk delivery services based on the clandestine routing of messages via international routes, known as pirated SMS. Although there’s no apparent control over the traffic of sending and receiving messages, some companies provide this type of service at low cost, sending thousands of messages from different places, attempting to fool the anti-fraud systems of phone operators.
Selling courses and sponsored links
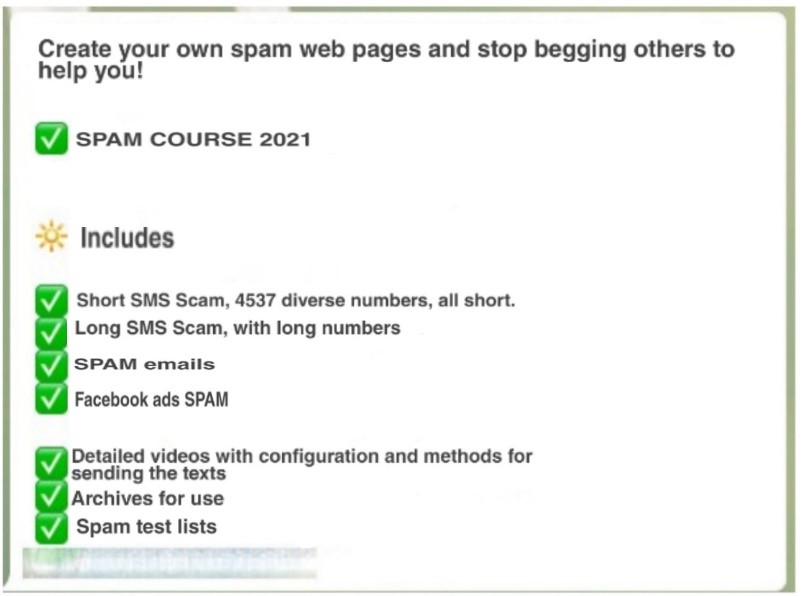
In addition to the marketing of SPAM tools and services, it’s also possible to identify the sale of courses for beginners’ criminals in some chats, as in the following example. The ad is about a “SPAM course” whose topics include using Facebook Ads service to disseminate malicious campaigns through advertisements on social networks.
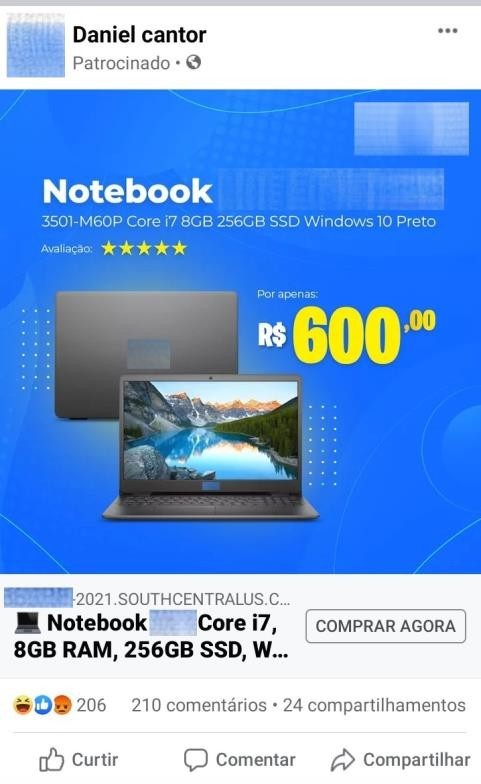
The improper use of sponsored links has been tracked since 2018. Criminals create fake accounts on Facebook and Instagram using famous retailers’ brands and hire the boosting service to advertise fake store products. Another well-known approach is to compromise third-party accounts that already have the ad service contracted.
Final considerations
In 2018, in our first research on platforms that sell fake online stores, we demystified how an entire Phishing-as-a-Service operation works. Some of the main changes identified between the old and current fake store scenarios are related to the anti-analysis techniques that criminals have employed in these infrastructures, such as encrypting essential functions in the source code, sending collected information straight to the database, and hiding directory and links based on random strings. Another significant change is the adaptation to instant payments methods. There are now fields for registering this type of payment key in the control panel to receive the money for fake products.
The use of social media as a customer service channel was intensified due to the current pandemic, which opened a space for criminals, as we demonstrated in our research on the scam known as Impostor Attendant. With this in mind, consumers need to be aware of the official channels and be wary of crazy promotions or products sold at a price far below the market. To succeed in their campaigns, criminals will always appeal to our curiosity and desire to make purchases at a better price.
The monitoring and takedown activities of our Threat Intelligence team are strong allies in the fight against phishing campaigns, especially those related to fake stores.
Recommendations
For users:
- Be careful with messages that appeal to urgency as “Limited offer”, “Special promotion,” or “Product for a limited time”, because it is common for criminals to use these words to make the victim curious.
- Be careful with messages that have links or attachments, especially those with spelling errors. Also, inspect the spelling of these
- Do not send personal information through SMS, email, or forms without being sure of the organization’s legitimacy because serious companies will hardly make this kind of request from these
- Be wary of messages that begin with a generic address, such as “Mr.”, “Ms.” or “Dear”, or those that use the destination email instead of the user’s name, such as “Good morning, [email protected]“
- Be suspicious of promotions or exaggerated information that makes polls and/or request sharing via WhatsApp to receive prizes. It is almost always a scam to collect data from
- Check legitimate channels of companies for the most appropriate means of contact. If they have apps or other products, check which links lead to safe
- When it comes to banks, it is recommended to be suspicious of messages received without prior request. It is not common for entities of this type to request actions and/or information from customers without contacting them
For businesses:
- Implement anti-spoofing solutions such as Domain-based Message Authentication, Reporting, and Conformance (DMARC), a standard for authentication designed to prevent email address
- Protect employees with anti-SPAM and anti-fraud solutions, including hiring malicious content monitoring and removal
- Promote training for employees and contractors to recognize the most common phishing
- Encourage security awareness campaigns for your customers on social media and other official means of
- Create exclusive channels to report when scams happen and implement a process for the proper handling of these
