Story by Carlos Cabral, originaly published in August 2016 on the previous version of the Tempest Blog
The use of Exploit Kits is not new. The first campaign that used an EK — sold for 20 US dollars — was spotted a decade ago and it used code that exploited a ‘0-day’ vulnerability in Internet Explorer.
These days this type of tool has an even greater impact with the increase of malvertising attacks, since these cyber offensives have the potential to reach a very large audience and require a component that exploits users’ browsers to deliver and execute additional malicious code. That is essentially the way EK operates.
Next is shown the operation of Neutrino Exploit Kit, which was analysed by researcher Luis Rocha in an attack campaign in which this EK was used to infect computers with the CryptoWall ransomware. All activities described next are performed in a few seconds.
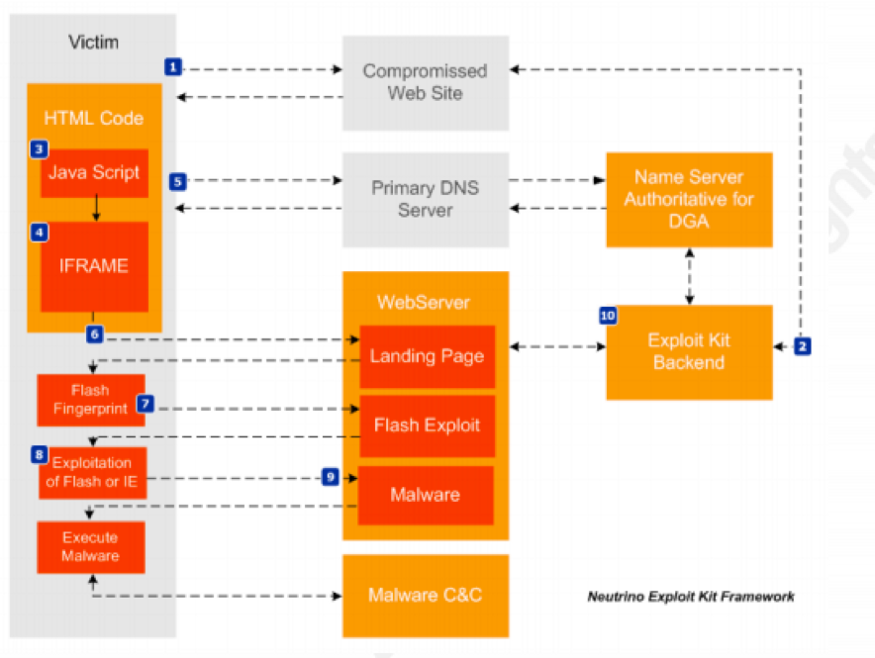
1. User reaches the compromised web server. This can happen through malvertising, phishing or watering hole attacks;
2. Web server redirects the connection to a backend server under the attacker’s control. This server hosts a JavaScript code that is designed to do several checks before calling the exploit kit. Some of these checks look at operating system information, geolocation, etc. The backend servers are also updated periodically with new URLs dynamically generated pointing to locations where the EK and malware can be reached;
3. Browser processes and decodes the JavaScript code. If the victim’s computer has the desired specification, the EK stores a cookie and creates an IFrame42;
4. At this moment the IFrame calls an URL and the Exploit Kit is executed;
5. The EK is stored in servers with several URLs and all calls that come from the IFrame are dynamically generated using DGA;
6. The EK executes an HTML page that starts the Flash Player application on victim’s machine. If the computer doesn’t have the Flash applications, the EK indicates the way to install it;
7. The browser then downloads and decrypts a malicious Shockwave Flash file (SWF);
8. The Flash Player runs the malicious SWF file that exploits vulnerabilities in Internet Explorer and Adobe Flash. Through the exploitation of these vulnerabilities, it is possible to access the victim’s filesystem;
9. Finally, EK runs a shellcode that downloads, decrypts and executes the malware. Here the victim’s computer is infected.
In general, the activity of Exploit Kits follows the steps above. The variations are the vulnerabilities which are exploited or the techniques used to hide the way to the malware.
Although Neutrino has robust protection features, such as the random domain generation and encryption of its components, it performs many functions that depend on disk storage, which leaves footprints. This limitation was solved with the development of Exploit Kits operating entirely in memory, as HanJuan and Angler.
Threat Outlook
Today Angler is the most used EK, responsible for 60% of all Exploit Kits traffic in the first quarter of 2016, according to Proofpoint.
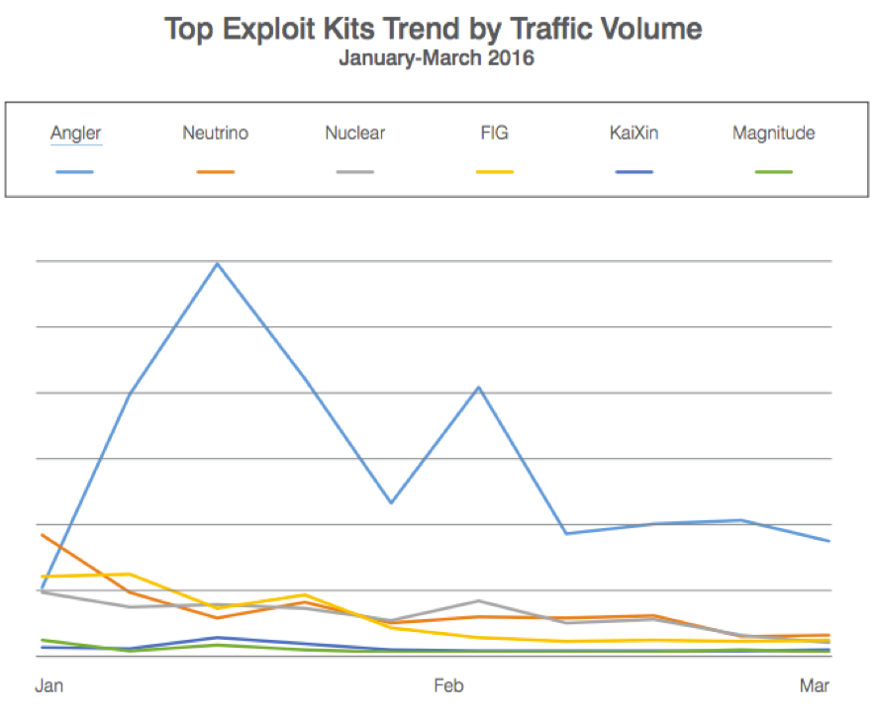
Exploit Kits are threats that have become more popular, especially because they can be used in various types of attack and are very common in malvertising campaigns. During the last months there have been significant attacks on popular sites like the celebrities’ news ‘Perez Hilton’, the websites of affiliates of CBS News KMOV and WBTV and EMOL, the most accessed Chilean news website. All these attacks used Angler EK.
In a study conducted by Talos, they verified the activity of 60,000 distinct IP addresses in a day connecting to a server with Angler EK. That was part of a malvertising attack against an adult site.
Keeping systems updated is essential to combat EKs because it depends on vulnerabilities in the operating system, browser or plug-ins to work. However, this so old recommendation is still neglected by many users. In a study conducted by Duo Security with 2 million devices, the company could prove that a quarter of all Windows devices were outdated, as well as 60% of all installations of Flash and 72% of all Java.
Cybercrime adapts quickly. However, combining awareness programs with basic activities, such as keeping systems up to date, can help address this problem.
