Introduction
According to the white paper released by Hewlett-Packard’s Intelligence and Security Operations Consulting Services Division in May 2013, the still-developing fifth-generation Security Operations Center (SOC) is highly marked by the use of analytics and big data, a methodology based on threat intelligence and information sharing, in addition to a behavioral approach to human adversaries. Obviously, in the face of the huge volume of analysis, sending and receiving threat intelligence data to the information security community, it becomes essential that organizations establish and adopt not only well-defined controls, processes and policies associated with information security in productive environments but mainly that the best IT governance practices are adopted in both internal and external environments.
Given the high complexity of current threats and their rapid evolution and adaptation to evade controls and defenses, organizations have been forced to deal with the exponential growth of budgets dedicated to security and with a challenging job market regarding the qualification of security analysts, so that ensuring better and more efficient protection barriers, in alignment with cost containment and without the need to acquire new and expensive systems, is one of the paradigms of the current organizations’ management regarding information security.
Adding to the difficulties mentioned above, the need for distance and the restriction of dislocation imposed to contain the health crisis caused by the pandemic of COVID-19 has substantially increased the cyber threat surface existing in organizations, originated by the acceleration of digital transformation in these companies, since communication and remote work infrastructures have been established, as well as the fact that physical processes have become digital, literally overnight. As a result, news about security incidents and cyber-attacks contemplating service interruptions, exfiltration of sensitive data and hijacking of entire systems in private companies and public agencies in developed and underdeveloped countries, and new forms of defrauding the general public through electronic means have been flooding the news around the world. This was evidenced during the meeting of the G7, the group of the seven largest economies in the world, which met between June 11 and 13, 2021, in Cornwall, England, and which for the first time brought among its discussion agendas the so-called cybercrimes, as well as their effects on world economies and concerns at the military level.
It is therefore in this context that Managed Detection and Response (MDR) service providers supply organizations with highly skilled analysts, state-of-the-art security tools and up-to-date global databases, which would be way out of reach for a corporation’s internal SOC; however, it’s also in the same context of service offerings and high budgets in an economic and investment downturn that there’s a need to demonstrate value to management and contractors, as well as justify the motivation to continue funding and investing in SOC and MDR Services.
MDR Services consist of outsourced incident detection and response management services applied to the protection of assets and data that are vulnerable and even exposed to threats beyond regular security controls. In addition to providing better threat detection and response conditions, MDR services provide threat intelligence to internal security teams, reducing the time to detect threats and consequently improving SOC performance metrics. Aside from operational work, the benefits of MDR services also include analytical and compliance consulting to provide comprehensive reporting to stakeholders and record retention across a wide range of applicable regulations and standards.
In turn, the report “The Definition of SOC-cess?” by the SANS Institute Security Operations Center issued in the year of 2018 shows that in general, there’s only a limited satisfaction with the performance and capabilities of SOCs and lack of a clear vision about excellence or path to excellence in the activities performed. Furthermore, in all the surveys conducted by the institute and documented in the report, it was identified that among the main barriers to improvement in SOC performance and effectiveness, there are problems related to performance metrics. Out of those who responded to the surveys, only 54% stated that they collect metrics and that most of the metrics collected are strictly quantitative data with no relevance to demonstrating effectiveness or business impact. This issue appears alongside the lack of qualified staff and insufficient automation and orchestration, as well as poor integration between tools and processes and playbooks as the main factors hindering the performance improvement of SOC activities.
From this, the constant conflict is characterized in which cybersecurity program managers complain about not receiving adequate resources for security operations, while CEO’s and CIO’s argue that security programs require increasing investments, and it’s never possible to define how much will be enough or how well previous investments were made from a business perspective.
According to COBIT 2019, an international set of best practices in IT governance and management published by ISACA (Information Systems Audit and Control Association), “stakeholder value creation (i.e., realizing benefits at optimal resource cost while optimizing risk) is often driven by a high degree of digitization into new business models, efficient processes, successful innovation, etc.” (ISACA, 2018, p.11 ), in this context, it is understood to perceive benefits as creating value for the organization through IT, maintaining and increasing value derived from existing IT investments, and eliminating initiatives and assets that aren’t creating sufficient value, by optimal resource cost, ensuring that adequate resources are available to execute the strategic plan and sufficient, appropriate and effective resources will be provided, applying this understanding to people in addition to hardware and software, and finally, risk optimization is taken as the reduction of IT-related business risks, i.e. events that could potentially impact the business, thus risk management focuses on preserving value.
According to ISO/IEC 38500, it is appropriate for leaders, in order to be able to govern IT, to adopt the “assess-direct-monitor” cycle (ABNT, 2009, p7-8 apud TCU, 2014, p.13).
The COBIT 2019, in which the governance and management objectives are divided into five domains, presents with EDM domain – Evaluate, Direct and Monitor in which good practices are developed so that the governing body can evaluate the strategic options available, direct the organization by strategic objectives and monitor the achievement of the strategic plan.
Governance and Management Framework
COBIT is an acronym for “Control Objectives for Information and Related Technologies” it’s an international collection of best practices in IT governance and management, published by ISACA (Information Systems Audit and Control Association), whose methodology is aimed at aligning IT governance and management practices with business objectives. The 2019 version is the sixth version of the framework, whose working group activities were carried out between the years 2017 and 2018 and replaces COBIT 5, the previous version released in 2012.
It is important to make clear that COBIT makes a sharp distinction between governance and management since the subjects comprehend different activities within the organization and within the subject of IT governance, as well as each demands different frameworks and meet specific requirements; the focus of this article is on governance practices.
According to COBIT 2019, governance ensures that stakeholder interests, conditions, and options are assessed for the determination of balanced strategic objectives aligned with the business environment and operational direction is set through prioritization and context-based decision-making, and finally, performance and compliance are monitored against the previously agreed direction and objectives.
Management activities, on the other hand, are focused on planning, implementing, executing and monitoring the activities in the focus areas, in alignment with the direction defined by the governing body, to achieve the company’s business goals.
Given the importance of IT in the scope of risk management in organizations, the last three decades have seen the development of a new field of study and development of best practices called Enterprise Governance of Information and Technology (EGIT), as an integral part of corporate governance. The activities and practices incorporated in it aim at the definition and implementation of processes, structures and relational mechanisms to generate the alignment of the governing bodies and their business purposes with their responsibilities in supporting IT activities and creating value to the business from investments in technology.
Principles of the governance system
COBIT 2019 was built according to two sets of guiding principles, those being principles for a governance system and principles for a governance framework.
The six principles for a governance system defined by COBIT 2019 are:
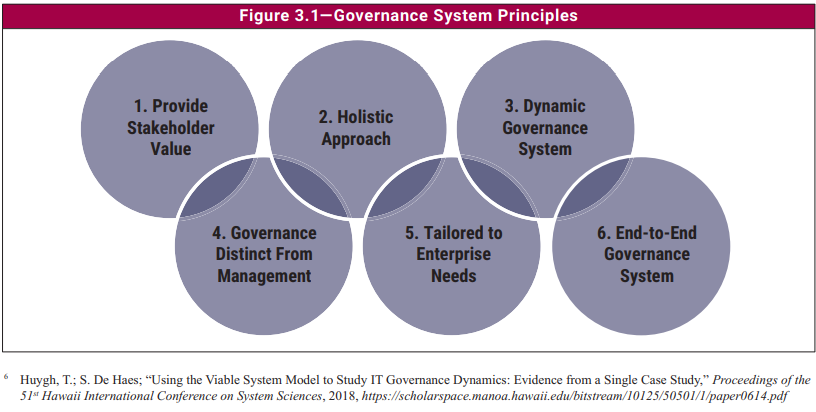
- Every company needs a governance system to meet the needs of the stakeholders and generate value from the use of IT. Value reflects a balance between benefits, risks, and resources, and companies need an actionable strategy and governance system to realize that value.
- A governance system for IT is built from a series of components that can be of different types and work together in a holistic way.
- A governance system should be dynamic. This means that every time one or more of the design factors are changed (e.g. a change in strategy or technology), the impact of these changes on the EGIT system must be considered. A dynamic view of EGIT will lead to a viable and future-proof EGIT system.
- A governance system must clearly distinguish between governance and management activities and structures.
- A governance system should be tailored to the needs of the company, using a set of design factors as parameters to customize and prioritize the components of the governance system.
- A governance system should span the organization from end to end, focusing not just on the IT function but on all technology and information processing that the company puts in place to achieve its goals, regardless of where the processing is located in the organization.
The three principles for a governance framework are:
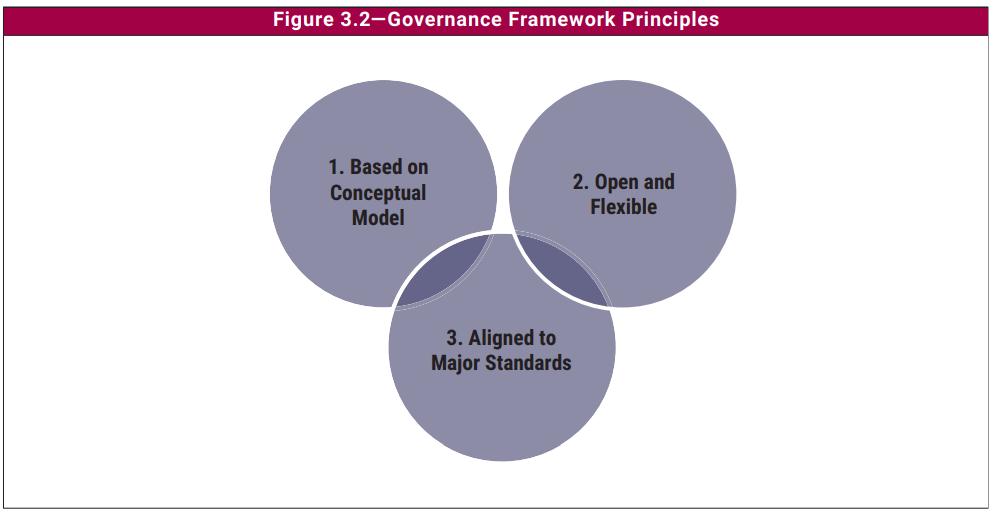
- A governance framework should be based on a conceptual model, identifying key components and relationships between components to maximize consistency and enable automation.
- A governance framework should be open and flexible. It should allow the addition of new content and the ability to address new problems in the most flexible manner while maintaining integrity and consistency.
- A governance framework should be aligned with relevant core standards, frameworks, and regulations.
(Source: COBIT 2019 Framework: Introduction and Methodology. COBIT Working Group. ISACA, p. 18. 2018.)
Domains and design factors of an EGIT
COBIT 2019 divides its model of IT governance and management objectives and processes into five domains. Governance objectives and processes are grouped into the EDM domain; under this domain, the governing body evaluates strategic options, directs senior management on the chosen strategic options, and monitors the realization of the strategy.
The remaining four domains cover management objectives and processes, which are: APO – Align, Plan and Organize BAI – Build, Acquire and Implement, DSS – Deliver, Service and Support and MEA – Monitor, Evaluate and Assess; the four domains won’t be discussed in this article as they are domains related to management activities and therefore aren’t the focus of this piece as already explained.
For each governance or management objective, COBIT 2019 establishes the components that need to be established, scaled, sustained, and satisfied in order to achieve the completion and achievement of each objective, and they are:
- Processes;
- Organizational structures;
- Information flows and items;
- People, skills and competencies;
- Policies and procedures;
- Culture, ethics, and behavior;
- Services, infrastructure, and applications.
It is also important to reflect that each governance or management objective and the process is virtually applicable to an unlimited number of focus areas, which makes COBIT an open framework and that, as explained in the principles of a governance system, the governance system should be adapted to the needs of the enterprise.
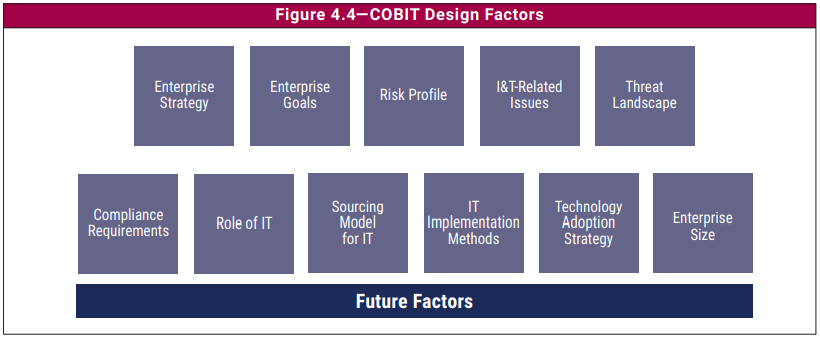
Also, on the needs of context adaptation, not only the governance system itself but also the design methodology of the governance system, its objectives and processes must be adapted to the business context and the reality of the organization. The entire governance system must, thus, be formatted in a customized way in each focal area, and regarding the adaptability of the governance system, it’s of critical importance to consider the impacts of the design factors that can influence the formatting of the system. Design factors that impact the establishment of a governance system include any combination of the following:
- Business strategy: companies can have different strategies. Organizations usually have a primary strategy and, at most, a secondary strategy.
- Business goals that support the business strategy: business strategy is realized by achieving (a set of) company goals. These goals are defined in the COBIT framework, which is structured along with the balanced scorecard (BSC).
- Company risk profile and current IT issues: the risk profile identifies the type of IT-related risk to which the company is currently exposed and indicates which risk areas are exceeding baselines.
- IT-related demands: a related method for an IT risk assessment for the company is to consider which risks have materialized.
- Threat surface: classification of the threat surface under which the company operates.
- Compliance requirements: categorization and classification of the compliance requirements to which the company is subject.
- Function of IT: classification of the function of IT for the company.
- Sourcing model for IT: classification of sourcing model that the company adopts.
- Implementation methods for IT: classification of methodologies that the company adopts.
- Technology adoption strategy: classification of technology adoption strategy that the company adopts.
- Size of the company: identification of the size of the company.
(Source: COBIT 2019 Framework: Introduction and Methodology. COBIT working group. ISACA, p. 23-27. 2018.)
Relevance of the EDM domain of EGIT regarding the MDR services context
As a governance system domain applied in the MDR service provider context, analyzing and articulating the requirements for EGIT aligned with the organization’s governance approach are the focuses of the governance objective determined by the Ensured Governance Framework Setting and Maintenance (EDM01). IT-related decisions in this domain are made in line with the company’s strategies and objectives, and the desired value generation is idealized. This requires ensuring that EGIT processes are supervised effectively and transparently, and then compliance with legal, contractual and regulatory requirements is confirmed in the domain.
It is necessary to put in place and maintain governance components with clarity of authority and responsibility so that the mission and goals of the company are achieved.
This governance objective is aimed at demonstrating the realization of business benefits from the investments made in IT and the service portfolio, as well as demonstrating compliance and support for the business with external laws and regulations. Business objectives that need to be aligned on this topic are managing the digital transformation processes, optimizing the functionality of internal processes, and compliance with laws and regulations.
The following could be metrics applicable to the context of aligning EGIT with the organization’s governance:
- Number of regulatory non-compliance issues that cause public comment or negative publicity;
- Number of regulatory non-compliance issues related to contractual agreements with business partners;
- Levels of the board and executive management satisfaction with business process resources
- Levels of customer satisfaction with service delivery capability
- Number of programs on time and within budget
- Percentage of stakeholders satisfied with program delivery;
- Percentage of business transformation programs with regular status updates reported.
In the context of MDR services, where customers typically make high and ongoing financial investments, the second governance objective in the Evaluate, Direct and Monitor domain, and perhaps the primary one, is concerned with generating demonstrations and evidencing the delivery of benefits related to threat detection and response capabilities.
Ensured Benefits Delivery (EBD) applies to ensuring, on the part of stakeholders and governing body, that the optimal investments are made available for IT initiatives, services, and assets, as well as returning to investors a reliable and accurate picture of the costs and likely benefits so that they can have business needs met effectively and efficiently.
At this point, it may seem deceptively trivial to say that investments need to be applied effectively and efficiently; however, it’s essential to understand that both MDR vendors and MDR contractors are faced with a highly changeable threat landscape in which tactics, techniques, and procedures (TTPs) are transformed and refined by threat actors on a daily basis, and malware is created and distributed with unprecedented signature capabilities and functionality.
To further enhance the scenario faced, one of the main frameworks applied to the cybersecurity market, Mitre Attack, undergoes community reviews to update the database of validated TTPs every semester and is currently in its tenth version, which was published on October 21, 2021. This is evidence, therefore, of the extremely fast mutation and transformation of threats, which can only be mitigated by the constant implementation of defenses in the environments to be protected. It becomes necessary, then, for the stakeholders to establish a balance between investments in new technologies and devices and their application in an in-depth defense strategy, prioritizing and evaluating the needs according to the risk analyses applicable to the organization and the costs resulting from the defense strategy adopted. In other words, this is the moment when the decision is made on the financial viability of the defined strategy or of an appropriate mix of investments based on cost, alignment with the defense strategy, the type of benefit to the organization’s portfolio programs, and the level of risk and expected return on investment (ROI) throughout the economic life cycle, in the face of possible losses that may result from a security incident or exploitation.
Key points for evaluation and monitoring in this governance objective are:
- Percentage of IT-enabled investments that claimed to generate benefits achieved or exceeded for the business;
- Percentage of IT services for which the expected and stated benefits in service level agreements are realized;
- Distribution of the mix of investments applied;
- Verification of value realized against investments made over the economic life cycle;
- Percentage of IT investments traceable to business strategy;
- Percentage of IT initiatives in the overall portfolio where value is managed across the full life cycle;
- Percentage of IT initiatives using value management principles and practices.
One of the main concerns in the growing threat context is the certainty that the defense strategy and measures adopted is adequately dimensioned to the business risks and its tolerances, being certain that an inadequate defense strategy will almost always be much more costly than necessary; however, it’s important to reflect that when it comes to measures and strategies that guarantee the security of the organization’s critical assets, an undersized strategy certainly results in exposed critical assets, but an oversized strategy doesn’t guarantee any extra coverage, so a defense-in-depth strategy must be adequately sized.
Ensured Risk Optimization (EDM03), in this context, is focused on ensuring that corporate risks and their tolerances are understood, communicated, identified, and managed throughout the organization. IT-related risks cannot exceed limits and tolerances, possible impacts to business value are identified, and the potential for compliance failures are minimized.
Some pertinent questions in IT risk management are:
- What percentage of IT assets exceed business risk tolerances?
- What percent of enterprise projects consider IT risks?
- What percent of critical risks have been effectively mitigated?
- What percent of risk mitigation activities performed within plan?
If answered, the above questions can provide very effective and clear evidence that the business risk management and mitigation strategy is being carried out properly and is effectively delivering value to the business, as well as justifying the investments made by stakeholders in MDR services.
Some metrics applicable to the context of aligning EGIT with the organization’s risk management are:
- Number of interruptions to customer service or business processes causing significant incidents;
- Cost of incidents to the business;
- Number of lost processing hours due to unplanned service interruptions;
- Percentage of complaints due to unavailability of services;
- Frequency of risk profile updates;
- Number of significant IT-related incidents that were not identified in a risk assessment
- Number of confidentiality, availability or integrity incidents causing financial loss, business interruption or public embarrassment.
It is important to emphasize that threat detection, and incident response are the primary benefits delivered by MDR services, and therefore avoiding loss of value, business interruption, or public embarrassment are the basic targets of this type of service. In this regard, it’s also vital to direct the establishment of risk management practices to provide reasonable assurance that IT risk management practices are appropriate and that the actual IT risk doesn’t exceed the tolerated risk.
At this point, assessing and monitoring the maturity level of the SOC is a very effective way to highlight the benefits provided by hiring specialized MDR services. Currently, the security market adopts some referential frameworks for assessing the maturity of organizations in terms of security; among the most used are Mitre Attack, Detteck, React, and SOC CMM frameworks. The constant performance of assessments allows stakeholders to have visibility on the maturity levels of business, services, technology, visibility, detection, response, processes, and people, and therefore it’s important to identify the percentage of critical business processes and services covered by risk assessments. Once you see what can be assessed, in addition to the assessment of their capabilities, you understand which processes and services aren’t even visible in the assessments.
As quoted in the report “The Definition of SOC-cess? “from the SANS Institute Security Operations Center, the lack of qualified staff and lack of automation and orchestration, as well as lack of integration between tools and processes and playbooks, is one of the main obstacles to improving the performance of SOC activities, given this perception, it’s clear that the availability of financial resources is not enough for the SOC to be effective, but when it comes to MDR services, it’s clear that the triad of resources related to IT processes, people and technology (PPT) must be adequate and sufficient and available to support the objectives, and be effectively in alignment with cost optimization.
Ensured Resource Optimization (EDM04) practices are aimed at providing assurance that the necessary resources are gathered so that realization of benefits and also visibility into future changes are achieved.
Since one of the main propositions of MDR services is to provide resources and high-level analysts to generate better detection and response conditions, it’s useful for the governance system to be able to assess:
- Amount of programs on time and on budget and generating revenue and market share;
- Quantity of products and services that generate competitive advantage;
- How satisfied are you with the capability and maturity of the processes?
- What is the percentage of reuse of the business architecture or its components?
- Number of deviations and exceptions;
- Level of stakeholder feedback on resource optimization
- Number of benefits (e.g., cost savings) achieved through optimal resource utilization;
- Number of resource management performance targets achieved
- Percentage of projects and programs with medium or high-risk status due to resource management issues
- Percentage of projects with adequate resource allocations.
Finally, given the external nature of MDR services, it’s necessary to make sure that internal and external stakeholders are identified and engaged and that the measurement and reporting of program performance and compliance is transparent, with stakeholders approving the targets and metrics and the necessary corrective actions. Ensured Stakeholder Engagement (EDM05) aims to act to ensure that the parties involved support the strategy adopted and the roadmap determined by the SOC consulting, remembering that in addition to providing better threat detection and response conditions, Managed Detection and Response services offer threat intelligence and analytical and compliance consulting to provide strategic information to stakeholders. Therefore, it’s vital to understand that in the context of MDR services, the strategic information generated and made available is considered a product and generates a lot of value to the service, as well as tools, employees and security measures, which are often more visible and tangible to customers, since they subsidize decision making and highlight the intelligence work acquired.
Establishing communication with stakeholders is then the basis for proper reporting flow and are established to increase consulting performance by identifying areas for improvement and confirming that EGIT objectives and strategies are aligned with business strategy and governance.
Required in this governance objective is:
- Identify all relevant IT stakeholders within and outside the organization;
- Maintain agreed communication principles, including communication formats and channels for stakeholder acceptance and report approval;
- Determine whether the requirements of different stakeholders are met and assess stakeholder engagement levels;
- Survey key stakeholders’ satisfaction regarding transparency, understanding, and accuracy of information generated
- Determine the degree of satisfaction of the board and executive management with information made available for decision making
- Number of incidents caused by incorrect business decisions based on inaccurate information;
- Timeliness of management information;
- Aligning data openness with data governance best practices.
Conclusion
The context of Managed Detection and Response service delivery offers customers a multitude of benefits, from better resources, tools and people to threat intelligence. However, it’s conclusive that all these benefits need to be demonstrated at strategic and tactical levels to customers, far beyond the operational demonstrations typical of today’s SOCs.
It’s already clear and evident the concern of SOC’s in generating operational indicators such as MTTD (Mean Time To Detect), indicator of time to detect a security event, or MTTR (Mean Time To Response), indicator of response time to a security incident, among many others such as SLA’s, quantification of monitored devices, quantity and classification of events, however, according to the report of the SANS Institute Security Operations Center, the quantitative metrics generated have little or no relevance to the business.
As stated by David Flater, a computer scientist in the Software and Systems Division at NIST (National Institute of Standards and Technology) in the article Bad Security Metrics, quantitative security metrics “are numerous and in high demand” and often generate misleading scaling because results can be presented in ways that lead readers to make inferences that are erroneous or false.
In this sense, the governance practices of COBIT 2019, especially those in the EDM domain, provide effective direction for information and technology governance to fulfill its role and ensure that the interests, conditions, and options of stakeholders internal and external to the organization are assessed, provide input for determining strategic objectives through prioritization and context-based decision making, and finally, that performance and compliance are monitored against the direction and objectives previously agreed upon.
If fifth-generation SOCs are still developing and increasingly adopting the use of analytics and big data, threat intelligence-based methodology, and information sharing, i.e., adopting more and more a context-informed response posture, technology and information governance cannot follow a different path.
The understanding by Managed Detection and Response service providers that the information generated by EGIT is as valuable as a SIEM opens up new business possibilities for the development of new products and services and will add a new layer of customer value to the current scope of MDR services.
REFERENCES
5G/SOC: SOC Generations HP ESP Security Intelligence and Operations Consulting Services. Business White Paper. HP ESP Security Intelligence and Operations Consulting Services. Hewlett-Packard, 2013.
BRZEZINSKI, Robert. Vision or Visibility?. Industry News. ISACA, 2020.
COBIT 2019 Framework: Governance and Management Objectives. ISACA, 2018.
COBIT 2019 Framework: Introduction and Methodology. ISACA, 2018.
CROWLEY, Christopher; PESCATORE, John. The Definition of SOC-cess?-SANS 2018 Security Operations Center Survey. SANS Institute Reading Room, 2018.
ELUE, Emeka. Effective Capability and Maturity Assessment Using COBIT 2019. Industry News. ISACA, 2020.
FLATER, David. Bad Security Metrics. Department of Cybersecurity. Institute of Electrical and Electronics Engineers, 2018.
FRISKEN, John. Leveraging COBIT to Implement Information Security. Industry News. ISACA, 2015.
