Criminals have intensified a kind of attack on large organizations’s networks in which they spend weeks selecting and extracting sensitive information and disseminating ransomware on all eligible computers, exposing the data of companies that do not pay the ransom on time.
Incidents of this type have been classified by the industry as “double extortion” attacks, as they can be summed up in the combination of two conducts linked to extortion: the one that threatens victims with having their data leaked, and the one that makes access to the data unavailable by using ransomware. To conduct the attack, offenders do not rely on unprecedented or impossible prevention methods. However, double extortion differs from automated attacks.
Attackers rely on the use of varied techniques, selected according to each target condition, to invade the business environment, to move around the network in search of systems with critical information, to steal gigabytes of data and to activate ransomware.
To succeed, the initiative depends on known problems often addressed by cybersecurity experts, such as remote connection abuse, configuration failures, phishing and known vulnerabilities.
According to recent studies, at least 15 ransomware has been identified in these attacks, which may indicate a relevant number of actors or active groups and whose modus operandi has already attracted imitators.
This is a serious problem, which strategy we will try to explain in this article.
Intrusion
Criminals generally take advantage of four relevant weaknesses to get initial access to the target company.
RDP
There is a preference for using RDP (Microsoft Remote Desktop) due to its popularity, as there are more than 4 million of these servers exposed to the Internet. Another condition that attracts criminals is the common neglect that people have with their password protection.
There are marketplaces where criminals rent or sell RDP server access credentials to companies of various sizes.
For less than $10 it is possible to buy access to their network, browse their computers and, depending on their configuration, exploit the connections that the company may have with their clients and service providers, stealing data and installing malware along the way.
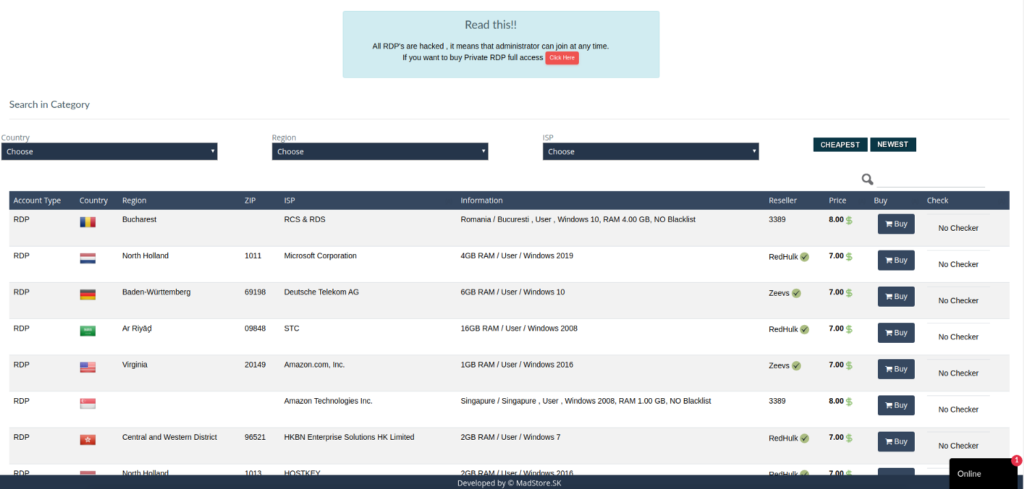
Renting or selling access credentials has become a business because of mistakes that people often repeat, such as setting weak passwords, not changing them from time to time and reusing them on multiple systems.
Testing several possible passwords (a brute force attack) is something that happens frequently and makes it possible to get weak passwords, but it takes time. Criminals are really happy when a database leak with access credentials occurs, which often happens. With such a database, it is possible to test these passwords on various systems, including corporate servers. In other words, a leaked password for any service on the Internet can be the gateway to a critical server in your company. This is because people often use the same password in several systems.
Configuration Failures
Imagine a large company where several projects are managed at the same time. In the middle of one of these projects, a web developer installs the ngrok on his computer, a small software for legitimate use, used mainly to show the progress of the website creation to external approvers. Although apparently harmless, what this software does is to generate an externally accessible URL, converting the user’s desktop into a web server, without the protections needed by a server exposed to the Internet.
The case is merely illustrative, as there are several ways to introduce vulnerabilities in a network, but what this hypothetical developer did was create a Shadow IT, that is, install technology without approval from the areas responsible for assessing its risks.
A variation of this scenario is when, for example, a financial area hires a specific cloud service without the responsibility for managing its components (database, operating system, etc.) being formally negotiated. What often happens is that the vendor installs the operating system and creates a database with standard configuration, usually insecure, exposed to the Internet, and then fills it with sensitive information. Many of the recent data leaks that have gained prominence in the media are an aftermath of similar stories.
These are two cases that happen frequently and become breaches that can be easily found by cybercriminals, as in the case of RDP servers.
Phishing
Much has been said about the prevalence of phishing attacks, so it is not necessary to be repetitive about the subject in this article.
However, it is worth saying that some double extortion attacks that we analyzed and that used this attack vector were based on phishing with malicious Microsoft Office documents.
It is essential to train teams about phishing scams, especially addressing targeted attacks as well.
Known Vulnerabilities
A Microsoft study of recent attacks also identified the abuse of five vulnerabilities known as gateways for attackers.
- CVE-2019–19781 — Affecting Citrix ADC, Citrix Gateway, Citrix SD-WAN WANOP, NetScaler ADC and NetScaler Gateway products. Fixed from January 19 to 24, 2020
- CVE-2019–11510 — Affecting Pulse Connect Secure and Pulse Policy Secure products. Fixed on April 24, 2019.
- CVE-2019–0604— Affecting Microsoft SharePoint Enterprise Server 2016, Microsoft SharePoint Foundation 2010, Microsoft SharePoint Foundation 2013, Microsoft SharePoint Server 2010, Microsoft SharePoint Server 2013, and Microsoft SharePoint Server 2019 products. Fixed on February 12, 2019.
- CVE-2020–0688 — Affecting Microsoft Exchange Server 2010, Microsoft Exchange Server 2013, Microsoft Exchange Server 2016, and Microsoft Exchange Server 2019 products. Fixed on February 11, 2020.
- CVE-2020–10189 — Affecting Zoho ManageEngine Desktop Central product. Fixed January 20, 2020.
Another recurring problem that was identified in the same research is the use of unsupported systems, such as Windows Server 2003 and Windows Server 2008.
Lateral movement
If attackers have used these four primary ways to invade the victims’ environment (RDP, phishing, configuration failures, and vulnerabilities), when it comes to moving around the affected network, there is a plethora of tactics and tools available. We have chosen here to address three of them, often pointed out in recent studies.
The first one is Mimikatz, a tool that allows for obtaining access credentials for Windows so that an attacker with limited permissions on a computer can use it to elevate their privileges, even taking control of the main servers on the network. Mimikatz has had its use documented in the criminal activity of, at least, 28 cybercriminals groups with different interests.
Another widely used component, which was also identified in double extortion incidents, is a legitimate tool, developed by Microsoft, called PsExec, which allows the remote execution of programs. This has also been documented in 21 campaigns of known groups.
Also common is the use of Cobalt Strike, a legitimate software, which license is sold from $3500.00, but “cracked” versions are negotiated in the underground. According to its vendor it is used for “software for Adversary Simulations and Red Team Operations”. If Mimikatz and PsExec are considered as single purpose mechanisms, Cobalt Strike is a toolbox, through which 39 attack techniques are used by 8 documented groups in cybercrime.
As soon as attackers take control of the network computers, they start the phase of collecting passwords and other important information, as well as activating persistence mechanisms. Ransomware can also be installed at this time, but kept in dormant mode.
Persistence
Maintaining access after the computer is restarted is one of the goals of any cybercriminal. To ensure it, there is a set of techniques often seen in various attacks, including double extortion:
- User creation — the criminal simply creates a user with administrator privileges on the computer or domain and expects that this user will not be identified and removed by the victim’s administrators.
- Scheduled tasks — the attacker creates tasks in the operating system scheduler to activate malware from time to time.
- GPO changes — the attacker creates or changes group directives present in Microsoft Active Directory to start some task or activate malware from time to time.
- Registry Changes — the attacker modifies the Windows registry to start some task or activate malware from time to time.
- Shadow IT — the attacker installs legitimate applications that allow external access, that run some malware or task from time to time, and expects the administrator not to identify and delete the software.
Ransomware and Data Leak
Among the attacks studied, 15 different ransomwares were identified. All of them with documentation about its operation and encryption available on the Internet.
There is not necessarily a fidelity between the criminals and the tools they use, so it’s not possible, through the list below, to state that there are 15 gangs operating, because the choice of ransomware can be determined by other factors, such as the environment condition and ransomware prices, in the case of rent in Ransomware as a Service market. Additionally, and because of the aforementioned conditions, the list below can become bigger or smaller with time.
- Clop — with documentation catalogued since February 2019, but linked to an active group since 2014.
- DoppelPaymer — first documented in July last year.
- Maze — was one of the first to adopt the double extortion modus operandi.
- Nephilim — active recently, at least since early March. But much of its code comes from Nemty.
- Nemty — ransomware first documented about a year ago, originally sold as a service, but recently its developers decided to operate in private mode only. Possibly because of the larger gains linked to the pandemic.
- RagnarLocker — another recently identified ransomware. It was used in early April against a Portuguese energy company which ransom was set at approximately 10 million dollars.
- REvil (Sodinokibi) — a widely studied threat in the last 12 months. Earlier this year one of its operators was identified by independent researchers.
- Sekhmet — little has been published about this threat that might offer some information that differentiates it from the others.
- Snatch — ransomware that forces the reboot of the computer and acts in safe mode, a situation of greater fragility.
- RobbinHood — a threat that was highlighted in February by exploiting a legitimate driver signed with the certificate of a Taiwanese company.
- PonyFinal — Java-based ransomware that uses PowerShell scripts to enable mshta.exe — a legitimate Microsoft component — that starts a reverse shell.
- Paradise — ransomware that has existed since 2017 and which use is sold as a service.
- MedusaLocker — according to Microsoft, this threat has been installed on computers previously infected with Trickbot.
- LockBit — a threat that, according to Sophos, has undergone recent improvements, which have placed it at a similar level of severity to REvil or Maze.
- Netwalker (Mailto) — originally documented in May last year, this threat has been used frequently in attacks on healthcare facilities.
As soon as the ransomware is activated on as many computers as possible, users are surprised by a message that, in most cases, requests a contact with the authors via email to negotiate payment.
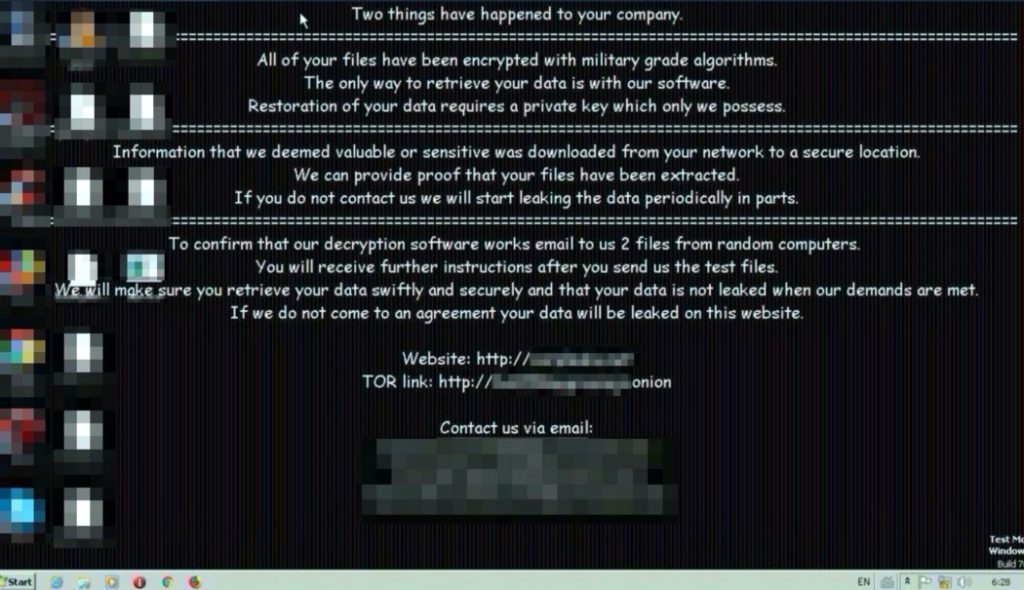
In the attackers’ note there is also the statement that the data collected will be leaked if no agreement is reached. This has been the case for some companies which information is being bundled into packages of up to 20GB and published on various websites both on the Internet and the dark web.
Recruitment
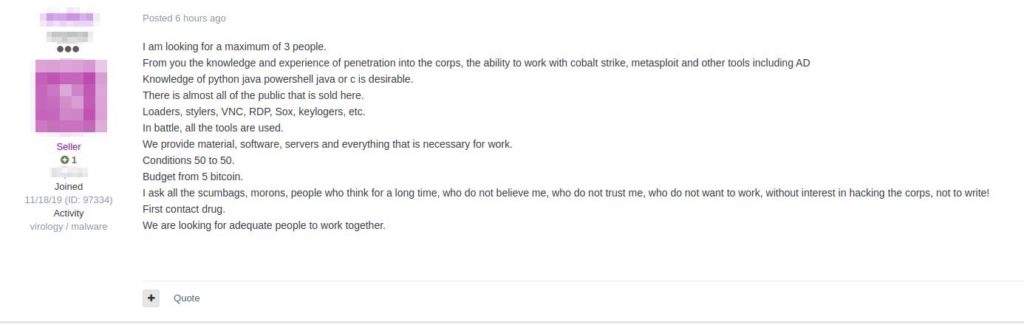
Regardless of how many or which actors are behind these attacks, it is possible to say that the incidents are attracting the attention of many people in the underground, so that imitators are acting to conduct similar operations.
We have witnessed the increase in the recruitment of people with the necessary knowledge for a job such as double extortion in various channels, which suggests an increasing trend in attacks with this modus operandi.
Remediation
One common recommendation that many experts make to those who suffer attacks with ransomware is that you should not pay the ransom and need to have up to date backups. This is because, however painful the period of rebuilding the environment may be, in backups there would be salvation, and no one who backed up computers properly would need to contribute with criminals, who may not return access to the data.
Unfortunately, this recommendation does not meet the double extortion scenario because attackers spend enough time in the victim’s network to double the impact: making the environment unavailable (including backups) and leaking sensitive data.
The beauty of cryptography lies in the mathematics of its conception, which has no value judgment, being used for good or evil. If ransomware is well done, the mathematics itself shows the impossibility to beat it in time. In other words, the problem is serious (and has become too broad) for us to repeat standard recommendations.
People with technical experience are all the time looking for ways to beat threats like this and, at this moment, there are a lot of good people working on it, like the No More Ransom project professionals. However, what I can say to companies that have succumbed to attacks like these is that, from the moment that the ransom note appeared on computers, their problem is no longer something that should be treated only from a technical perspective, but that also demands experience in negotiation.
Technicians need to be involved in incident response and environmental recovery, but what you need most at a critical time like this is a skilled negotiator who can understand the extent of the problem and has the cold blood to deal with extortion.
This person should not necessarily have expertise in cryptography or operating systems, but needs to be a strategist with a good technical team to support him or her in considering the pros and cons of not paying the ransom or, unfortunately, negotiate its value.
Risk Reduction
Preventing double extortion attacks is something which costs are easier to measure and which, in most cases, involves doing what is often forgotten or not prioritised, but which is in any cybersecurity playbook. Talking about this over and over again is our job and, if it is helping people, we do not mind repeating these recommendations.
Monitor anomalies
Computers and other technology devices produce a multitude of signals about their behavior, some are recurrent and have to do with their normal use and others are unusual and can be considered as anomalies that need to be monitored and investigated.
Several were the examples of anomalies mentioned in this article, such as:
- User creation — in most companies this is usually done only through a formal request. Cases that escape this are suspect.
- Changes in user access — same situation as user creation, and, if a user’s access is changed so as to give them more privileges on the network without the proper formal request, it is very likely that an attack is taking place.
- GPO changes — this is a delicate activity and it is done by network administrators. Without a formal request, within a project or change management, this should be considered as suspicious.
- Changes in OS folder — from the moment the operating system is installed, some of its folders are only changed in case of software updates and scheduled maintenance. Different situations need to be considered as suspicious.
- Changes in the Windows registry — something similar to changes in operating system folders, changes in the registry outside of the schedule indicate suspicious activity.
- Task creation and execution — this is the kind of element that is not common on desktops and is usually documented on servers. Deviations need to be considered suspicious.
- Software installation — people without technical attribution should not be allowed to install software, but this is not the reality in many places. The activity, at the very least, needs to be strictly monitored.
- Bizarre Hours — some administrative activities, for example, only occur outside of working hours so as not to affect the business, others, if they happen on the weekend, are suspicious. It is up to the company to determine what is outside the standard for each action and fine-tune the monitoring at these times.
- Network anomalies — identifying what is an anomalous network behavior is something that requires study and monitoring by experts. However, the flow of large amounts of data to a limited set of external servers needs to be investigated.
All monitored activities will issue alerts that cannot be neglected, so it is important to be formally clear what the plans are for each type of alert: which ones require emergency investigation on a Sunday morning for example, and which ones can wait until the next business day.
Control your environment
Each company has its own priorities and a limited budget to deal with cybersecurity issues. It’s not easy to have to adapt plans in order to protect systems from every new thing that comes along. However, many criminals take advantage of the lack of control companies can have over their assets.
I apologize for being incisive, but it is not acceptable, for example, that there are technical conditions for anyone in a company to install software, make changes in the Windows registry, create users or grant administrative access to them. The same goes for the ability to set weak passwords that are never changed. This can (and should) be inhibited in the operating system configuration and exceptions need to be monitored.
Allowing everyone to have power over the computers and systems they use is the same as not controlling (and therefore not protecting) the corporate technology.
You can be the size of your suppliers
One thing that has become very important to cybersecurity is the data that your company exchanges with its suppliers. It is necessary to review what this data is and check the security of connectivity between companies, requiring the adequate cybersecurity controls and monitoring its application.
Review exposed computers
This is a topic that connects the issue of control over the environment with the protection of data in the suppliers. It is a sign of diligence to check from time to time whether all your systems that are exposed to the Internet really should be accessible and correct deviations.
Services such as Shodan and Censys are very useful for this, all you need to do is search for your network addresses or those of your suppliers.
Update Systems
Although it is difficult to prioritize the approval and installation of patches in the midst of several other activities that may compete with this in large companies, cybercrime has shown that there is no mercy with those who lag behind on this issue. Those who maintain obsolete and outdated systems become easy prey.
Insurance
The cyber incident insurance market has developed in several countries. Take some time to study the possibility of obtaining a service like this.
