Tempest’s Consulting Team, has detected a vulnerability in Trend Micro Password Manager. It enables a privilege escalation that grants NT AUTHORITY_SYSTEM (user who has full local privilege) to whomever exploits it through a Hijacking DLL.
In the following text, we will briefly present some basic concepts on the subject, as well as the demonstration of this vulnerability in Trend Micro Password Manager
DLL (Dynamic Link Library)
According to Microsoft’s documentation, a Dynamic Link Library is a binary module that has a set of functions and data that can be used by other binary modules — that is, a set of functions and data that can be used by another DLL or an executable.
A feature of DLL functions is that they do not inherit the permissions set in the Access Control List (ACL) of the uploaded files when they are imported. However, they usually inherit the permissions of the process that imported them.
The import of a DLL can be performed through the functions LoadLibrary() and LoadLibraryEx(). If the absolute file path is not provided, Windows will by default use the natural resource of the DLL search order find the unloaded module. This search order is performed in the following directories, consecutively:
1. The directory from which the application was loaded;
2. The system directory;
3. The 16-bit system directory;
4. The Windows directory;
5. The current working directory (CWD);
6. The directories that appear listed in the PATH environment variable.
However, there are several ways to change the search order of a DLL. Microsoft’s documentation, Load Library Safely, can be found for more details on the topic.
The fact is that if the loading of a DLL is implemented insecurely, an attacker can take advantage of the search order to perform an attack known as Hijacking DLL. To do this, the attacker just inserts a malicious DLL with the same name as the one requested, in a previous directory in the search order.
Trend Micro Password Manager
Trend Micro Password Manager is a software that can be installed together with Trend Micro Maximum Security.
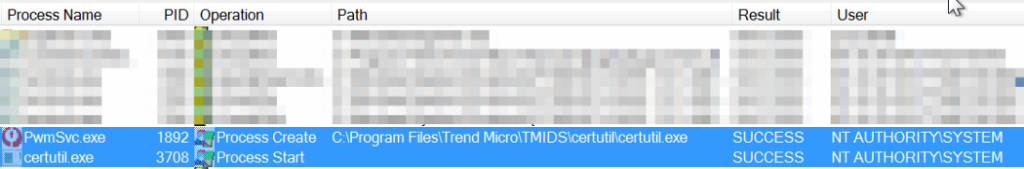
During an analysis of the operations performed during the start-up of the operating system, it was possible to detect that the Trend Micro Password Manager Central Control Service, through its main process PwmSvc.exe, is responsible for creating a new process called certutil.exe, which aims to manipulate Firefox browser certificates. The following image illustrates the creation of this process:
Right after this creation, certutil.exe inherits the privileged user permissions and tries to load several DLLs, among them, the nssckbi.dll located inside the Firefox browser profile folder:
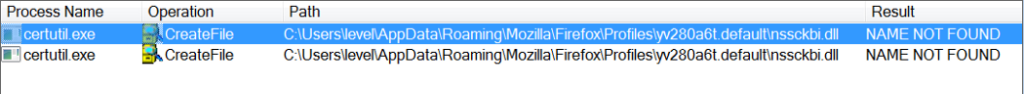
The security problem of this import performed by the certutil.exe process focuses precisely on the excessive permissions of the directory, considering that it is inside the profile folder of the user in use (C:Users\usertest). To test whether the process would actually import a DLL into the indicated directory, even if it is not signed, a DLL was designed to write the author of the action — user name — to a text file. As can be seen in the image below, the DLL has high privilege on the machine:
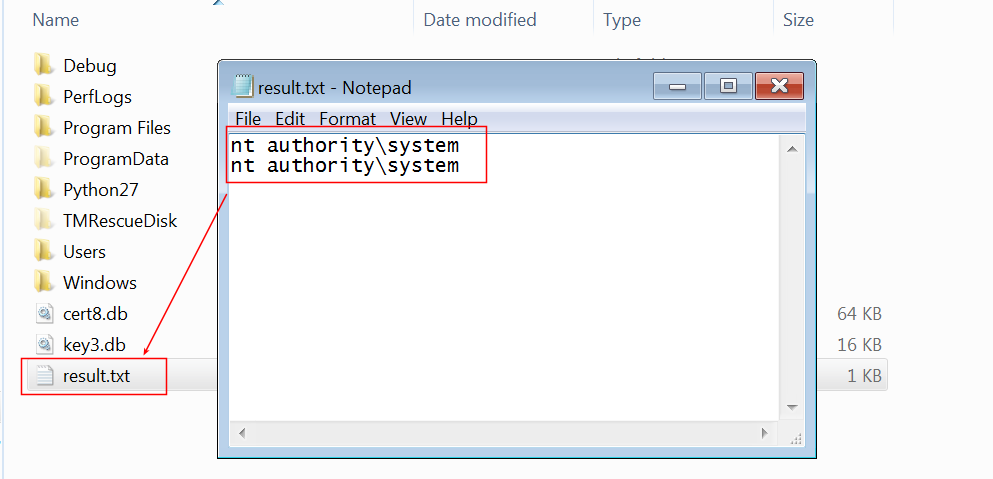
Thus, one can conclude the existence of two vulnerabilities through the actions described above:
1) The DLL was being imported from an improper location;
2) The signature verification was not being performed.
When contacted, Trend Micro claimed that the vulnerability in question was present in the NSS tools module of the Firefox browser. Firefox, on the other hand, replied that it did not recommend the commercial use of its browser; stating that it was a test tool. However, after a more refined analysis, Trend Micro not only accepted the vulnerability, correcting it, but also generated a thank you note and a CVE assignment. In addition, more recently, the company released another note, where it reports the change in the Common Vulnerability Scoring System — CVSS severity assignment. The vulnerability in question had been considered by them to be of medium severity, but ended up being recognized as of high severity.
