. . .
Story by Carlos Cabral, originaly published in August 2016 on the previous version of the Tempest Blog
Check Point Software published in early July a report containing the details of the infrastructure behind the HummingBad malware, which was discovered in February 201622. According to the study, the malware, which affects Android devices, had been built by Yingmob Interaction (微赢 互动) company to defraud the digital advertising industry in campaigns that generated revenues of up to $ 300,000 per month.
The HummingBad is one among the various activities that continually harm the digital advertising industry. When compared to other activities in the same market, digital advertising is the most promising one, with a profitability that seeks to overcome advertising revenues on TV in 2016. However, this is also a market where many clients hang suspicious when considering the most basic relationship between sellers and buyers: delivering what has been paid for.
It is estimated that over fifty percent of all legitimate advertising campaigns will never be seen by humans, only by ‘bots’. This scenario, according to Keith Weed (chief marketing officer of Unilever), is “a time bomb” that will make the entire industry lose credibility.
In fact, publishers are already suffering with lack of credibility, not because of fraud, but because more and more users are annoyed by the interference of advertising and, consequently, they navigate using adblockers. It is speculated that the adblockers tend to reap $ 12 billion predicted for the industry by 2020. It is not just to avoid the annoyance caused by advertising, but also to apply security, because these tools are being seen as another layer of protection against Malvertising attacks.
The issue escalated to the point that some developers created tools, like Antiblock.org, to circumvent AdBlocking solutions; and others have proposed to draw up an additional layer to AdBlocker for fighting against these tools; therefore becoming an ‘anti-anti-AdBlocker’.
The digital advertising industry is now a complex ecosystem that encompasses companies and tools performing various functions in an automated process of buying and selling human time attention.
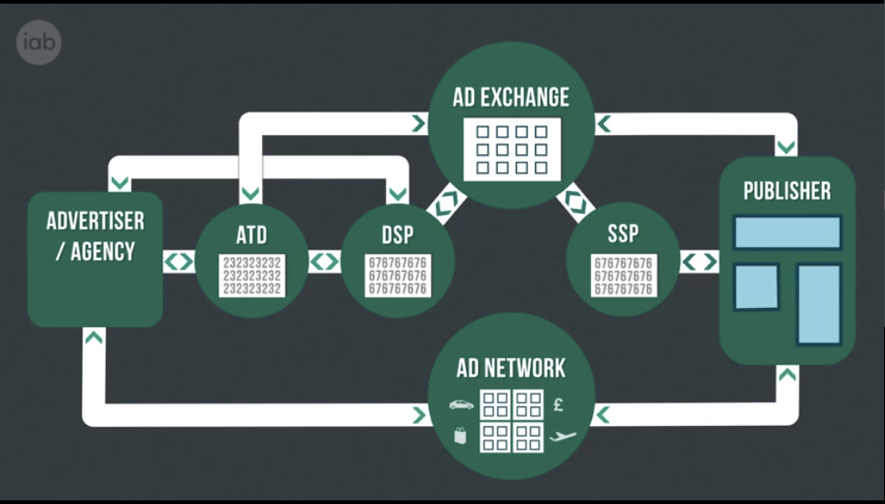
In this article, we discuss three scenarios for the execution of fraud. In fact, these are three ways to see the problem and it should not be construed as borderline.
It is possible that the fraudsters use tactics of one scenario in another one. It’s like looking for a school of fish: it keeps moving, adapts to water conditions and the presence of predators.
Control the Traffic
The first strategy involves the use of malicious Traffic Brokers, which can be contracted by both legitimate and malicious publishers, and which are attracted by the high volume of qualified traffic. In this attack, the access volume actually increases. However, the traffic does not have human origin; it is formed by botnets controlled by the broker.
Malwares such as HummingBad are very important for this strategy. Its primary method of infection is to disguise itself as a new version of QVOD video player, which used to offer adult videos and was discontinued in April 2014, amid a police investigation against Nora company, which had developed the player.
Anxious for new versions of the app, users install the malware, which has two stages of infection: the first is a rootkit that exploits multiple vulnerabilities in the operating system and takes control of the equipment. If the first module does not work, the second component sends a system update message to the user, waiting for him to press OK and grant system-level permissions, which allow access to several functions of the device, such as storage in specific folders.
When started, the malware contacts the command and control server, downloads other components and begins to display advertisements in various applications, forcing users to click in ‘close’, which generates clicks with financial feedback to fraudster.
There is also a similar version of this malware for Apple devices (iOS). An extensive report, produced by Palo Alto Networks, shows that the malware, called YiSpecter, also presented itself as a new version of QVOD, but diversified the method of infection, using popular Chinese platforms to promote mobile applications, social networks and web pages, which are promoted to the top of search engines by malicious SEO (Search Engine Optimization) techniques.
According to Check Point, both malwares were developed by YingMob Interaction , a company based in the province of Chonaaina, China, which sells advertising services for mobile devices. Among other features, the two malwares share certificates and, more importantly, the C&C addresses. This demonstrates the existence of a formal business whose operation is based on malware.
Botnets play an important role in directing requests. However, there is another way to control the traffic in order to defraud the digital advertising industry without having to develop and maintain malware. This tactic, though, requires power over the network — the power of an Internet Service Provider (ISP).
The Israeli researchers Gabi Nakibly, Jaime Schcolnik and Yossi Rubin detected that a part of China’s Internet traffic is redirected to malicious recipients. When starting a HTTP connection, it is the nature of TCP protocol to consider the first packet of the request and discard others with the same function, in order to avoid redundancies that may cause disturbances in connection.
What Nakibly, Schcolnik and Rubin could prove is that the common HTTP requests that came to China Telecom and China Unicom ISPs had the first packet replaced by another one, smaller in size than the traditional packet. Being smaller, it was quickly transmitted to the next hop of the communication chain.
The injected packet contained JavaScript code that redirected the connection to a destination that was different from the original request. In other words, the user’s device was requesting content on the Internet and was redirected to another. Among the recipients of this traffic are malware hosts, but most of the volume had the intention to push users to advertising.
Through what was reported in the media, it is not possible to determine whether the Chinese ISPs were redirecting traffic to profit from advertising or whether businesses were attacked by other groups who used assets from their infrastructure.
According to the authors of the study, the best way to mitigate this attack is by forcing the use of HTTPS for all connections.
Fake Publisher
In this scenario, fraudsters eliminate dependence on publishers creating farms with any type of content, usually republished from other vehicles in violation of copyright laws.
The next step they take is generating traffic to these farms through bots in order to make them seem, for the Ad Exchange, like sites that are very popular and have qualified audience. This raises the Publisher qualification in the Ad Network and attracts advertisers.
In some cases, the Ad Exchange can identify and block these farms, but, according to Christopher Heine, on Adweek, the fraudster is still paid for the traffic generated and payments can remain active for up to 90 days. So when they are removed from the network, fraudsters create other farms with other addresses and the cycle begins again.
Hide and multiply
Another very common fraud is to hide ads in order to accumulate a lot of them. Overlapping them or publishing on the bottom of the page in unreadable size of 1 pixel by 1 pixel.
Outlook
Some experts compare the digital advertising industry to the stock market, and this is because the assets are sold and bought automatically in an ecosystem with several companies and interdependent solutions. The comparison is correct. However, from the perspective of controls against fraud, this industry is more similar to the pre-1929 stocks market crash, with regulations that emerged only years later, in 1934.
However, the regulation of this market would not be the solution to all problems, and that is because the industry is global and decentralized, which would require a major effort to establish a legitimated institution and standards by the market.
According to Michael Tiffany, CEO of White Ops, the best way to fight fraud is by changing the way in which the fraudster is paid and by finding ways to fingerprint the human traffic. According to him, the available initiatives are weak and something really effective to seriously mitigate the problem has yet to emerge.
The best thing to do at the moment is having all honest entities of the industry meet to renegotiate their modus operandi.
There is no doubt that the situation is a time bomb, as the CMO of Unilever said. Bad for publishers, who suffer from unfair competition from fraudsters; to the audience, which is at the mercy of Malvertising attacks or other threats of electronic crime; and for advertisers, who witness their investment disappear in distant globe provinces in the hands of organised cyber crime.
